The iPhone X ushered in the Swiss Army Knife-like Side button, which can perform numerous functions, such as summoning Siri and opening Apple Pay through click gestures. This has carried over into the iPhone XS, XS Max, and iPhone XR, so if you've upgraded to one of these devices from a Home button-equipped iPhone, you'll have to learn how to shut down your new device.
Even if your default mobile browser is Google Chrome, you may not want Google to also be your search engine. Maybe you're not impressed with Google's search results all the time, maybe you want a more private search experience, or maybe you just don't want Google's hands over everything in your life. Whatever the case, it's easy to switch from Google to another default search engine.

Yo-yo's are not just for kids anymore. Check out this funky tutorial and learn how to yo-yo like a pro. You can do way more than just pull your yo-yo up and down, with a little practice you will soon be performing tricks and spinning your yo-yo all over the place!

Changing the drive letter is necessary for reassigning hard drives. This straightforward tutorial breaks down the steps for performing this simple computer-housekeeping task.

With 2 simple props and a bit of sleight of hand, you can be well on your way to performing an interesting card trick.

Choking is the mechanical (either by foreign object or compression) obstruction of outside air flowing into the lungs. Learn about choking, including emergency treatments like CPR, in this medical how-to video. Remaining calm and performing one of the procedures below could help someone who is choking.

Knee pain can quickly turn to a significant injury if ignored. Learn how to keep the knee pain at bay by performing these exercises and stretches with tips from an exercise therapist in this free health video series.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

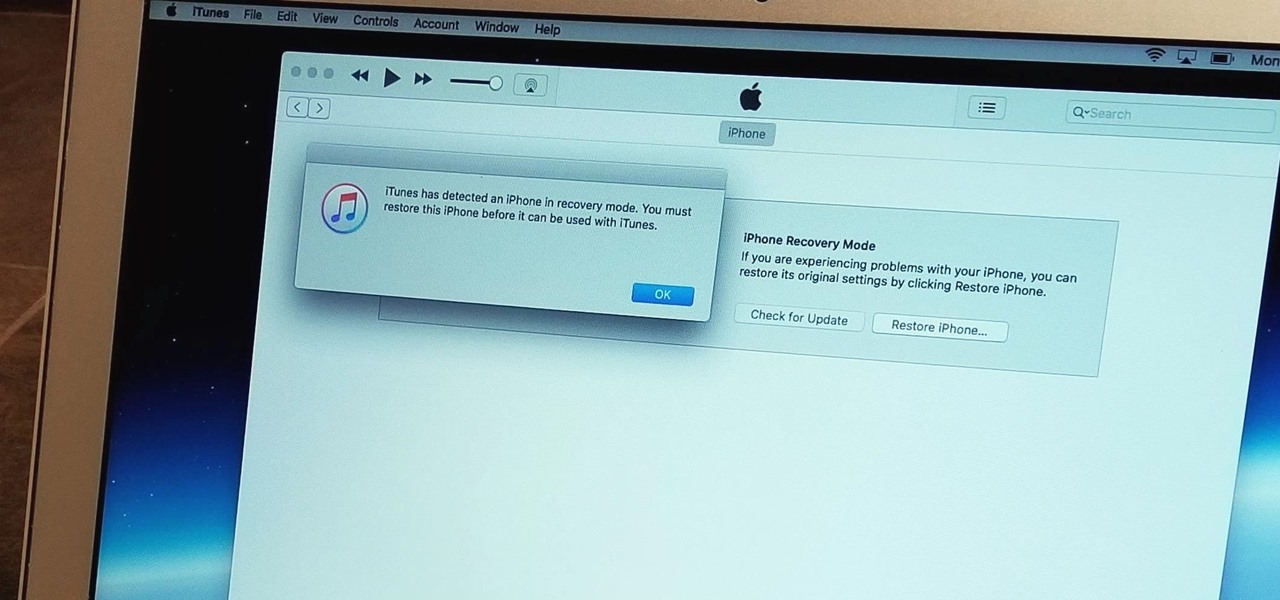
With the iPhone 8, 8 Plus, and the exclusive iPhone X, Apple has come full circle in transitioning its users away from the home button present since the first iPhone a decade ago. This gives us a window into Apple's design philosophy moving forward, but it also presents some new problems, especially when it comes to entering and exiting DFU mode in iTunes.

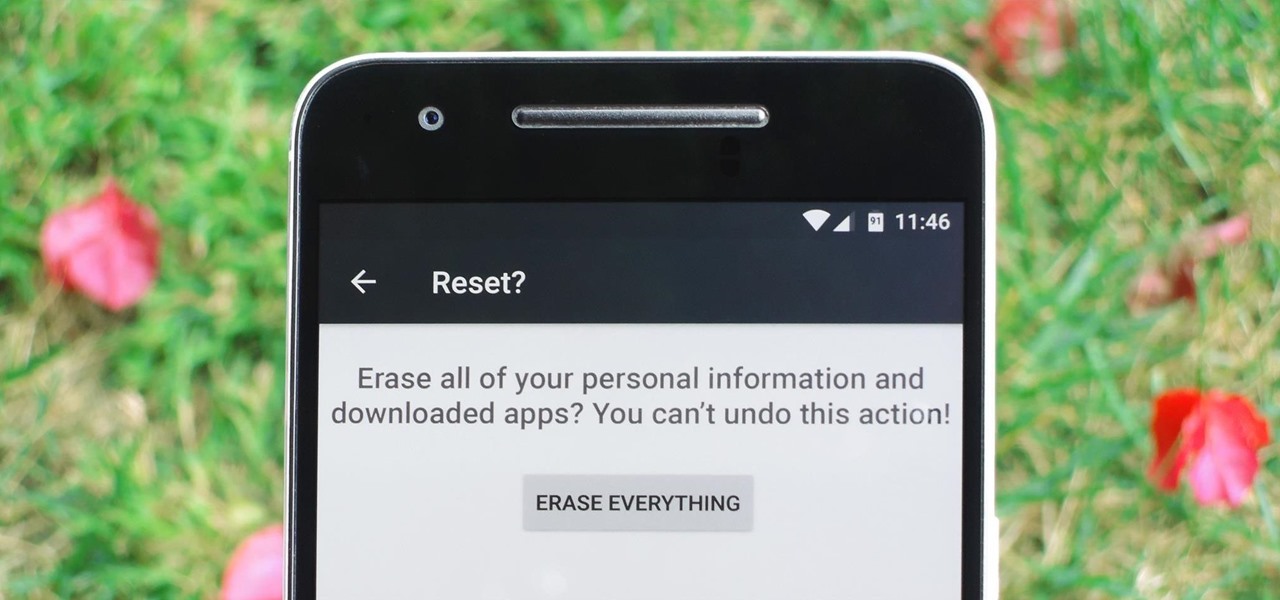
Whether you're performing a factory reset to get your device ready for sale or trade-in, or you're wiping your device in the hopes of fixing software issues, there's a right way and a wrong way to go about it. Sure, it seems like a simple task on the surface, but if you're not careful, you could end up wasting a lot of time or losing precious data.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

If you're ever worried about your bObsweep's well being, you can always do a home check-up test to make sure all of bOb's parts are in working shape. As long as bOb has some charge, you can diagnose any potential issues by following the video guide for performing bObsweep Standard's check up test.

In yoga, the half moon pose is a great standing pose that will help open the spine laterally and improve posture. Learn some tips for performing the standing half moon yoga pose from a professional yoga instructor in this free fitness video.

Let's be honest, nobody enjoys doing cardio — they tolerate it. That dreadful, loathsome feeling you experience when you're doing cardio workouts isn't unique to you, it's almost universal. Sure, it gets easier the more you do it, but there are some ways to make it better now.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

If you've ever seen one of those Samsung commercials from about a year back, you know that the Galaxy S series of phones come with a feature that allows you to do certain things by making gestures in front of your screen. They call this feature Air Gesture, and it enables you to perform certain functions without even touching your phone.

Picture-in-picture mode on Chromebooks is almost identical to the one found on Android phones. Once activated, it transforms your video into a small window so you can do other things while watching. But the Chrome OS version is actually a bit better thanks to the addition of an Android 11 feature.

We all know how volatile the stock market is, especially during times of crisis. That does not mean that the market is impossible to gauge, however. Day traders are trained to read charts in order to recognize market trends and price patterns, giving them the insight they need to make their trades as profitable as possible.

The iPhone 11, 11 Pro, and 11 Pro Max are the most advanced flagships Apple has to offer, but that doesn't mean they're immune to occasional bugs. Anything from an app plagued with issues to a faulty software update still can cause your device to freeze up, so having the ability to force a restart can come in very handy.

iPhones aren't immune to occasional bugs. But starting with the iPhone X, performing a reboot to fix minor issues has gotten a little more tedious. Thankfully, iOS 13 has a hidden option that makes the process a whole lot simpler.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

With plans to compete with Niantic and other augmented reality game developers, game developer WarDucks has closed a $3.8 million funding round.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Apple released iOS 11.3 beta on Jan. 24 and the public stable release on March 29, and it didn't take us long to find plenty of cool new stuff. Aside from new Animoji, Health Records, and some upcoming changes related to the recent battery fiasco, most of the new features are about polish. One such feature we've found should make iPhone X users a little happier.

Architects are natural candidates to be early adopters of mixed reality. Their trade consists of not only designing buildings and spaces, but also presenting those designs to clients, who then decide that their vision is worth spending thousands (if not millions or billions) of dollars to build in reality.

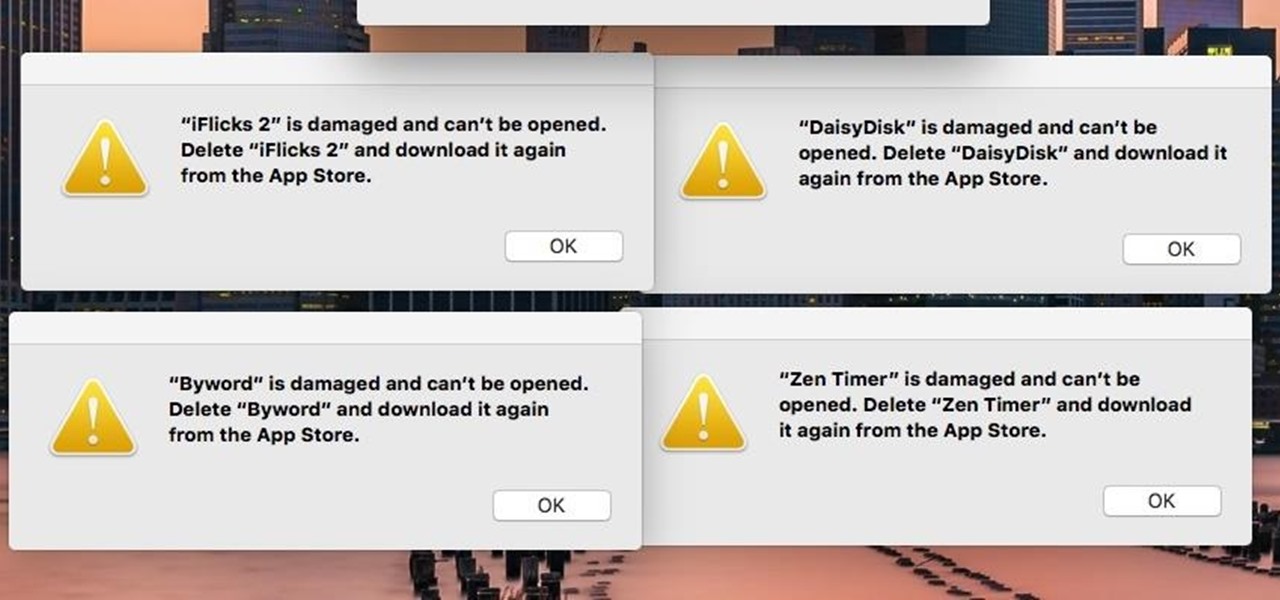
If you're seeing "damaged" apps on your Mac, you're not alone. A huge digital rights management blunder in Apple's Mac App Store on Wednesday, November 11th has rendered some apps unusable. When opening certain apps, the following message could be displayed:

While the Spotify interface isn't overly complicated or confusing, it's not exactly safe to use when behind the wheel. Thankfully, a new app from Navideck is here to make driving with a Spotify premium membership easier and safer for your daily commutes.

In addition to the fingerprint scanner, the Samsung Galaxy S6 has all of the basic lock screen options that other Android phones have: swipe, pattern, PIN, and password. There also just happens to be a secret sixth option called "Direction lock" that protects the device with a series of customizable directional swipes—only it's hidden in an unsuspecting settings menu.

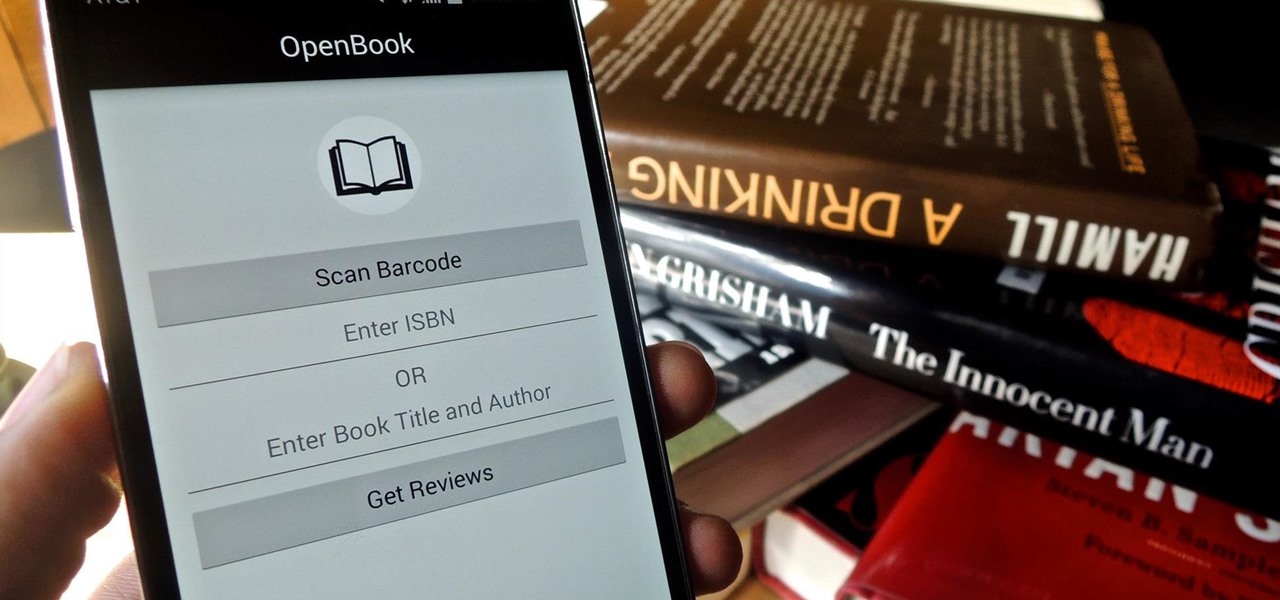
Purchasing an actual book from a brick-and-mortar store is becoming increasingly less common for people to do, but it hasn't completely gone out of style just yet. There's something about entering a bookstore and viewing all the potential great stories and epic tales just sitting on the shelves, waiting to be discovered.

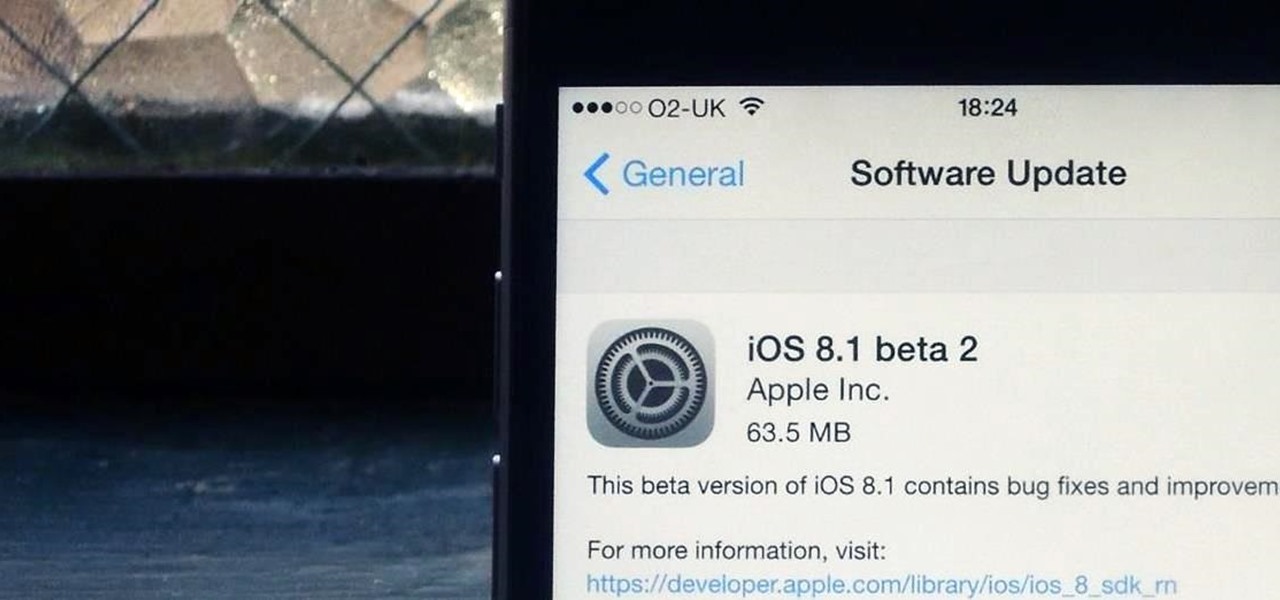
Shortly after Apple's iOS 8.0.1 update fiasco ruined many iPhone users' cellular reception (which was fixed with iOS 8.0.2), developers were treated to the first beta release of iOS 8.1, which will be the next big update for iPad, iPhone, and iPod touch.

Welcome back, my novice hackers! Reconnaissance is one of the most important preparatory steps to hacking. As I have emphasized many times before here on Null Byte, you must know the operating system, the ports, the services, the applications, and sometimes even the language of the target to be effective. If you haven't taken the time to gather this info, then you are likely wasting your time.

Since picking up your first crayon, chances are you've had a favorite, or dominant, hand. That hand gets you through the day, taking care of everything from writing to eating. If you've ever been forced to rely on your "wrong hand", you know how uncomfortable and unwieldy it feels.

Creating awesomely messy slops of DIY slime and curdled fake blood isn't something new—we even have guides on making Dr. Seuss-friendly Oobleck and the radioactive green ooze that created my childhood favorite Teenage Mutant Ninja Turtles (minus the radioactive part, of course).

The best chemistry experiments are those you can perform with items already laying around your house. With only some sugar, salt substitute and an instant cold pack, you can make your very own gunpowder! Being able to make homemade gunpowder without a trip to the store can be a lifesaver, no matter if it's just for testing out a Civil War-era musket, blowing up stubborn tree stumps, or preparing for battle when imperialists overrun your country.

When you look at the top corner of your phone, what do you see? Upon upgrading to Android 11 or iOS 14, you'll see either "5G," "5G+," or "5G E" if you're connected to the right network. But what exactly do these symbols mean? They indicate not only if you're using 5G, but also what type you're connected to.

When Apple removed the Home button from iPhone, it introduced a new way to install apps that caused confusion over what to "double click." Like most iOS changes, it didn't take long to get used to double-clicking the Side button. But for some, performing a double-click on the Side button isn't that easy.