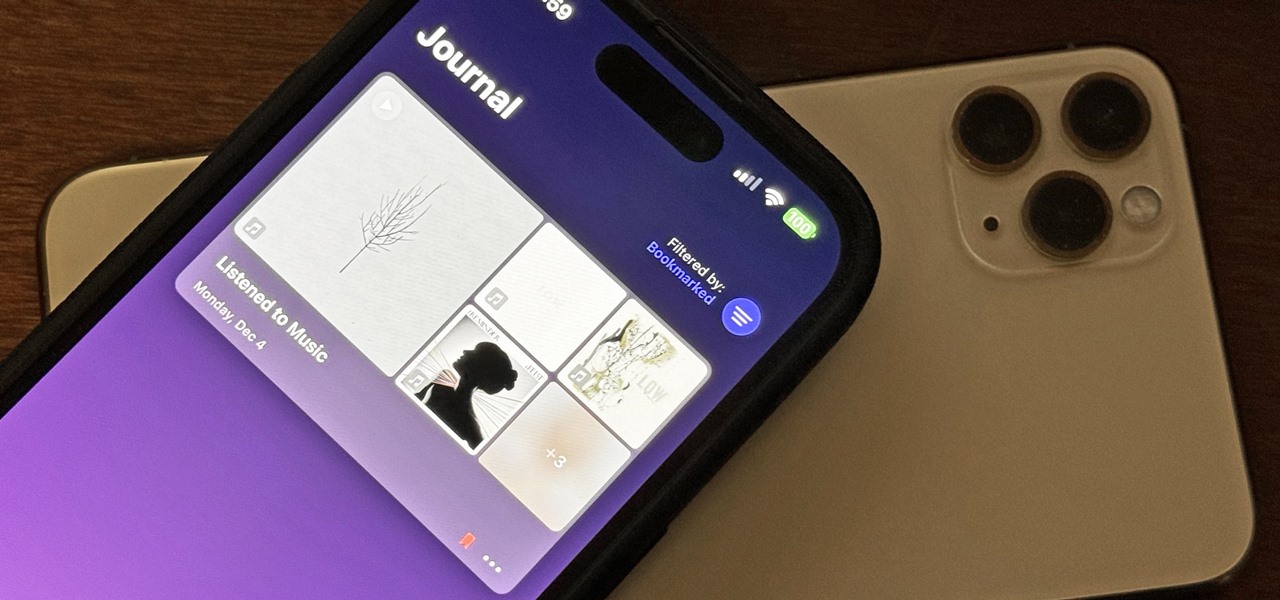
Perhaps the biggest new feature within Apple's iOS 17.2 update for iPhone is Journal, a new journaling app designed to help you take a moment to reflect each day using reflection prompts, recommendations via on-device intelligence, and suggestions for recent activities and events.

There are some important new features in the Photos app on iOS 17 and iPadOS 17 that will streamline editing, give your pets more recognition, help you learn about the world you've captured, and even add a bit of fun to your day. There are even a few hidden tricks that may surprise you.

Some apps look great with Dark Mode, and some do not. So when you have system-wide Dark Mode enabled on your iPhone and are using an app that only looks good in Light Mode, you'd normally have to turn the dark appearance off manually, then switch it back on when you leave. But there's a workaround that can automate the process for you.

While it doesn't come with any iPad models out of the box, the Apple Pencil is perhaps the best iPad accessory you can get. It's a powerful writing and drawing tool with an intuitive design and user-friendliness that makes it easy to take notes, draw sketches, mark up documents, and more. And there's a lot you can do with it — some of which you may not have noticed yet.

From time to time, you may need to locate the version and build number for a particular app on your iPhone or iPad, but it's not at all obvious where you can find the information. Well, there's more than one place to look on iOS 18 and iPadOS 18, but none are perfect solutions. Knowing each method will ensure you can always find any app's real version number.

Have you ever been locked out of your iPhone? Maybe you forgot your passcode. Or perhaps someone with access changed the passcode as a prank. Your iPhone's display could have even been damaged and unresponsive. Whatever the reason, there's an easy way to get back access to your iPhone the next time it happens.

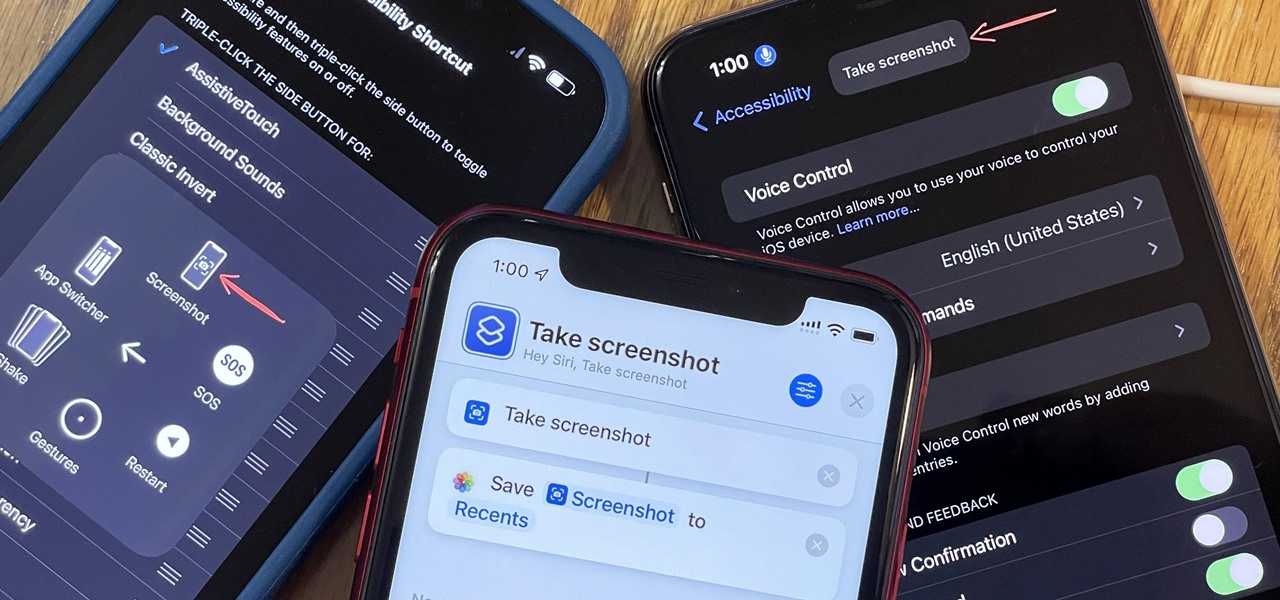
Using an iPhone isn't difficult, but it can be if you're using it for the first time, especially if you switched from an Android phone. That's primarily because of the massive difference in the user interface between the two operating systems. And when it comes to taking screenshots, you have more options than just using the hardware buttons.

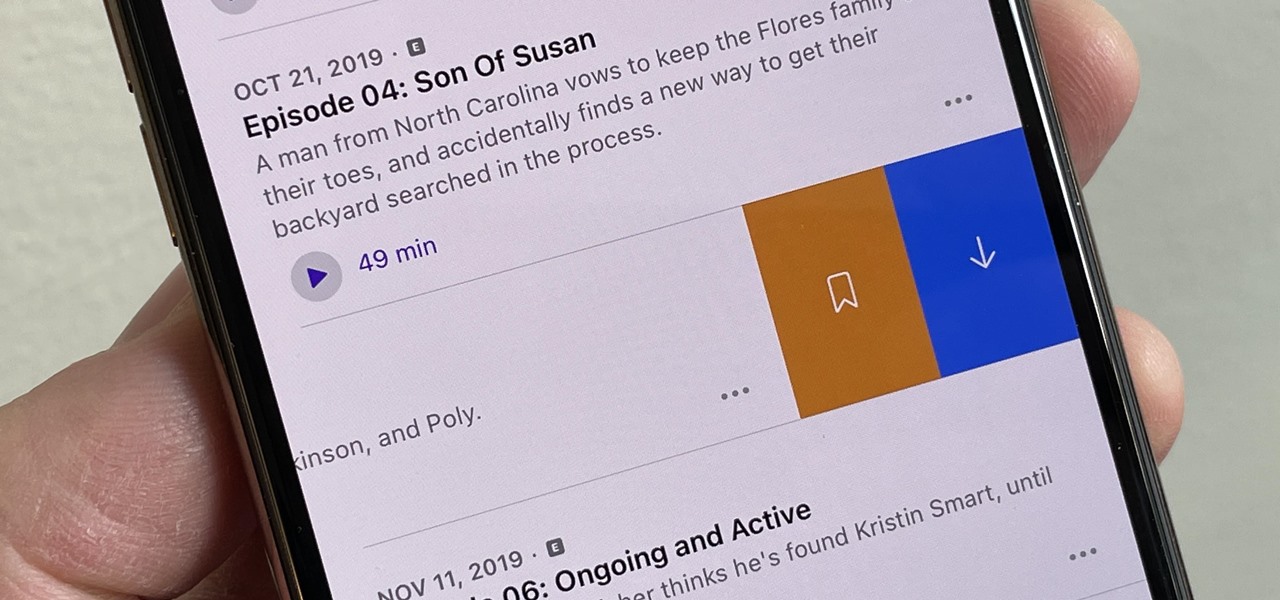
Spotify has caught up to Apple in monthly podcast listenership and is even forecast to surpass Apple soon, but Apple just made some serious changes to its Podcasts app for iOS and iPadOS that could keep Apple at the top.

When Microsoft unveiled Mesh a couple of weeks ago, the move revealed a major part of Microsoft's next steps toward dominating the augmented reality space, particularly with regard to enterprise customers.

Apple's latest update, iOS 14.2, is finally here. As the name implies, it's the second major update to hit iPhones since Apple released iOS 14 in the fall. The update brings at least 13 new features and changes to all compatible iPhones, including over 100 new emoji and eight new wallpapers.

For the first time, Apple has announced four new iPhone models at the same time. At the Oct. 13 web-only event, Apple revealed the iPhone 12, iPhone 12 mini, iPhone 12 Pro, and iPhone 12 Pro Max. This year, it made a phone for everyone. But when can you get your hands on one of these 2020 models?

The future of TikTok in the U.S. is all but certain. Microsoft, Walmart, or Oracle could save the day by buying the company, TikTok may win its lawsuit, or China's new restrictions could halt everything — but all could fail. Just like Vine before it, TikTok could be on its way out, only for opposite reasons. But will it matter if TikTok gets banned in the States? With the competition heating up, likely not.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.

Kali Linux has come a long way since its BackTrack days, and it's still widely considered the ultimate Linux distribution for penetration testing. The system has undergone quite the transformation since its old days and includes an updated look, improved performance, and some significant changes to how it's used.

Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

Network enumeration is one of the essential phases of an attack, but it can take a lot of time and effort depending on the size. We've all been spoiled by Nmap and similar tools, and while there is a learning curve involved, they are extremely useful. But there's also GoScan, a tool that builds upon Nmap, offering an automated way to enumerate networks and services quickly.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

Christmas is just one week before Jan. 1. That means a lot of New Year's resolutions filled with promises to better ourselves with increased productivity, focus, and work ethics — but getting started can be challenging. Give the people in your life a leg up this holiday season with these smartphone gifts to keep them on-task in 2020.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

One of the coolest aesthetic features of iMessage is its animated message effects. If you're like many users, you might even have discovered them by accident, where wishing your friend a "Happy Birthday!" or congratulating them on a promotion unexpectedly flooded your screen with balloons or confetti.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

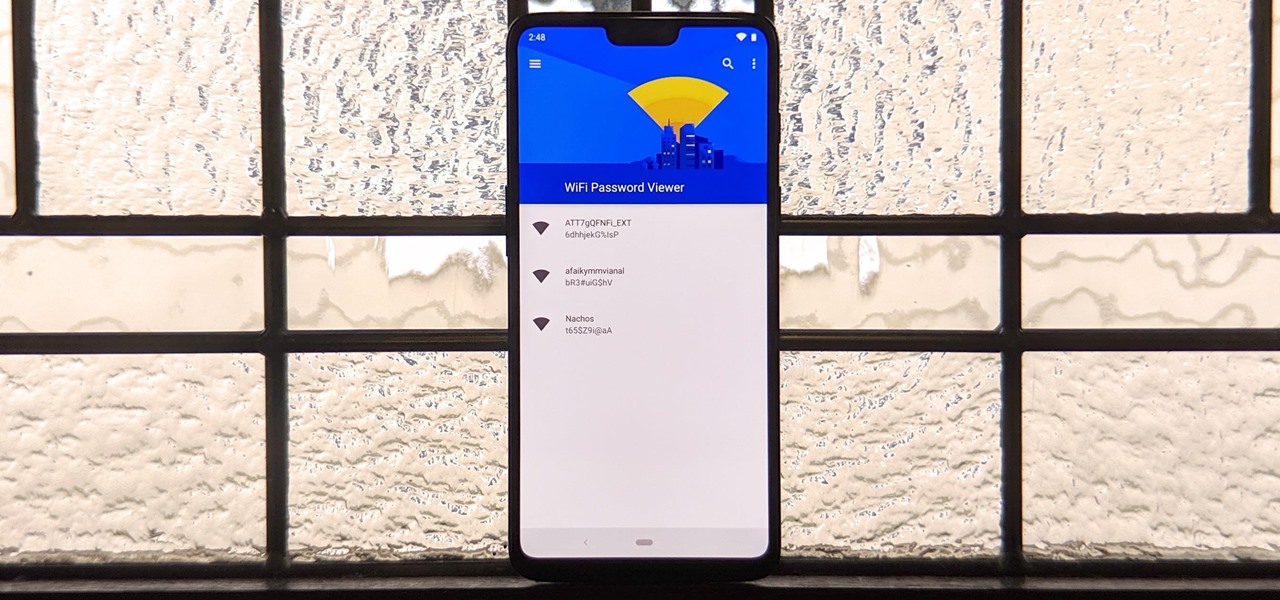
You've probably connected your Android device to dozens of Wi-Fi networks since you've had it, and your phone or tablet remembers each of them. Whether it's a hotspot at home, school, work, the gym, a coffee shop, a relative's apartment — or even from a friend's phone — each time you type in a Wi-Fi password, your Android device saves it for safekeeping and easy access later.

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

Need a unique gift idea for the techy person in your life? Look no further than that phone they always have in their hand. There are plenty of great accessories, apps, subscriptions, and other smartphone-related goodies that will improve their quality of life, and thoughtful gifts like that are always the best-received.

Ports allow network and internet-connected devices to interact using specified channels. While servers with dedicated IP addresses can connect directly to the internet and make ports publicly available, a system behind a router on a local network may not be open to the rest of the web. To overcome the issue, port forwarding can be used to make these devices publicly accessible.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

Apple's iOS 11 is finally here, and while they showed off several of the new features it brings to your iPhone, iPad, and iPod touch back at WWDC 2017, they've only just touched the surface of what iOS 11 has to offer. There are a lot of cool new (and sometimes secret) features to explore, so we've collected them all here for you.

Out of the more than 200 new features Apple included with iOS 13, perhaps none is more anticipated than system-wide dark mode. Finally, we no longer need to blind ourselves when responding to an iMessage late at night or checking Reminders to see the following day's tasks. But this benefit also applies to third-party apps, so long as they are updated accordingly.

The new iOS 14 for iPhone arrived Wednesday, Sept. 15, 2020, alongside iPadOS 14, and there are a lot of features to uncover. Improved widgets. Better home screen customization. Exciting Messages improvements. New abilities in Camera and Photos. There's so much here that it'll take months for you to learn everything by heart.

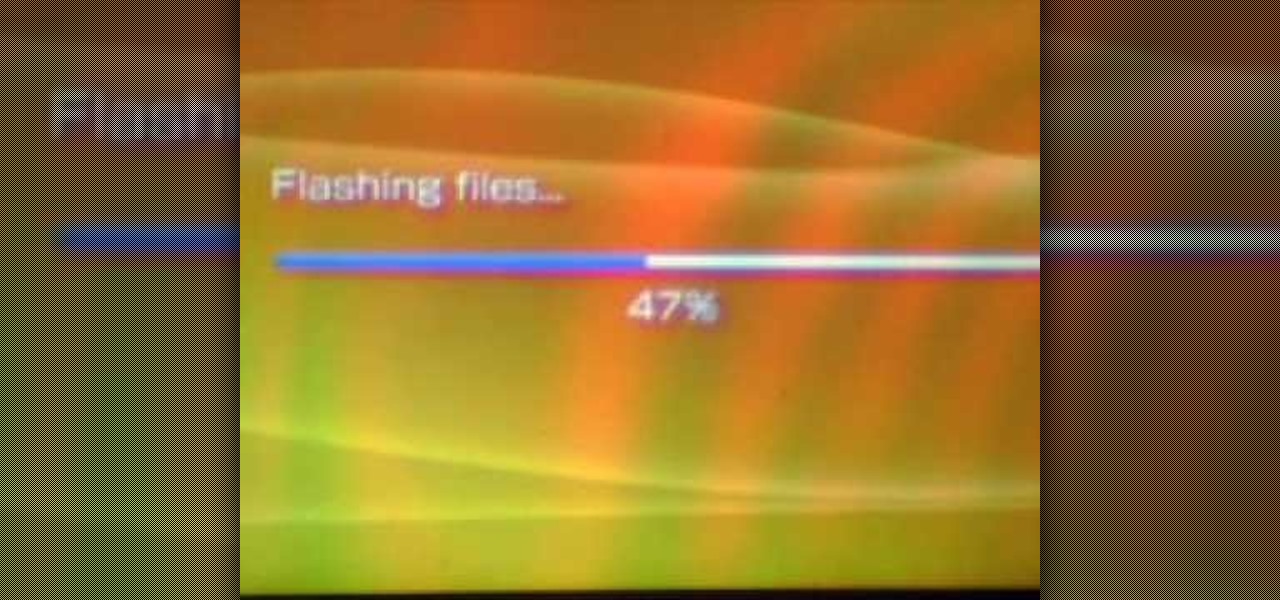
So your brand new PSP has been bricked, rendered useless and you have no clue what to do or perhaps your just stuck with a firmware update you hate and want to downgrade. No worries. In this tutorial, you'll be given the steps and tools you need to successfully unbrick/downgrade your PSP's firmware in a matter of minutes. So don't toss out your PSP or fumble around with a ineffective "upgrade" use this tutorial its easy!

Looking to create an additional, or perhaps even your first, email account but aren't quite sure what to do? In this how-to video, Digital Coordinator Hiwot will guide you, step by step, through the process of creating an account at Yahoo! Mail.

This tutorial is perfect for updating your website for that Halloween theme, or perhaps you just need a spiderweb. Whatever it's for, if you need to make a spiderweb in Flash, you'll want to watch this video.

What's the secret ingredient to these nails? Food. What?!?

Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to hack cash in Restaurant City (07/02/09).

So take a few moments and watch this instructional video series designed to help teach the basics of Hip Hop dance for beginners—or those of you who are already dancing fiends but perhaps unfamiliar with the variety of styles and moves under the umbrella term “Hip Hop.”

The Rubik's Twist, not quite the Rubik's Cube, but just as fun. If you don't this puzzle by the name Twist, perhaps you know it by its more familiar nickname, the Snake.

Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to hack the food quiz in Restaurant City with Cheat Engine (09/10/09).

Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to hack eating and cooking speed in Restaurant City with Cheat Engine (09/08/09).

Restaurant City is a Facebook game that allows you to create your own restaurant. Watch this video tutorial to learn how to hack Restaurant City with Cheat Engine (09/08/09).