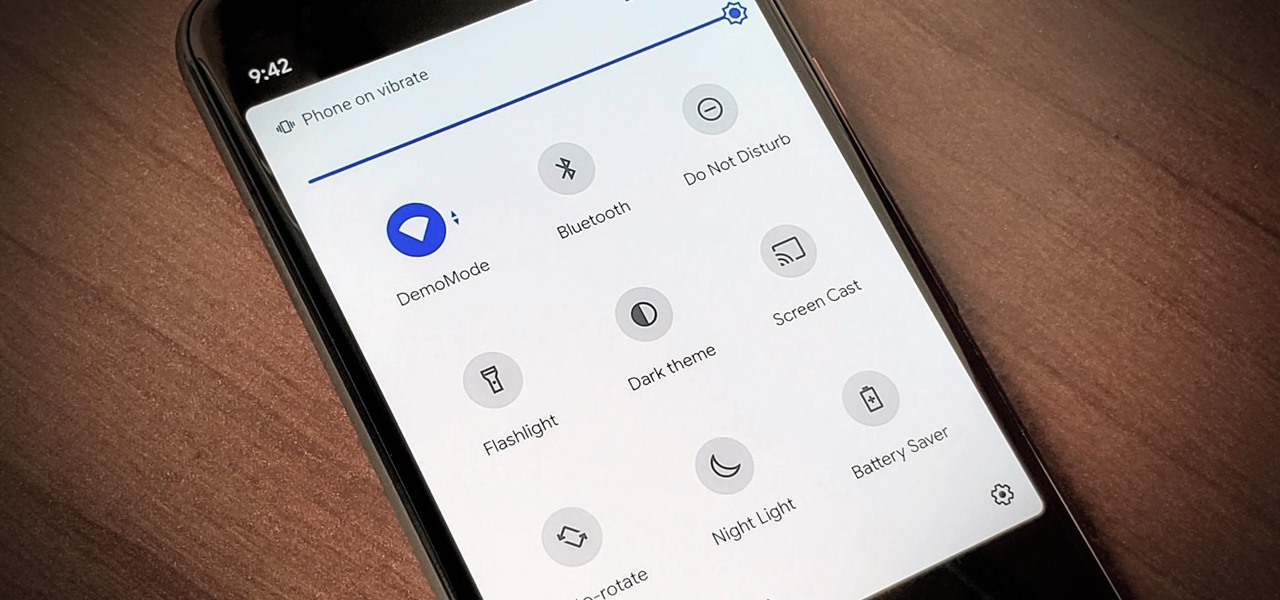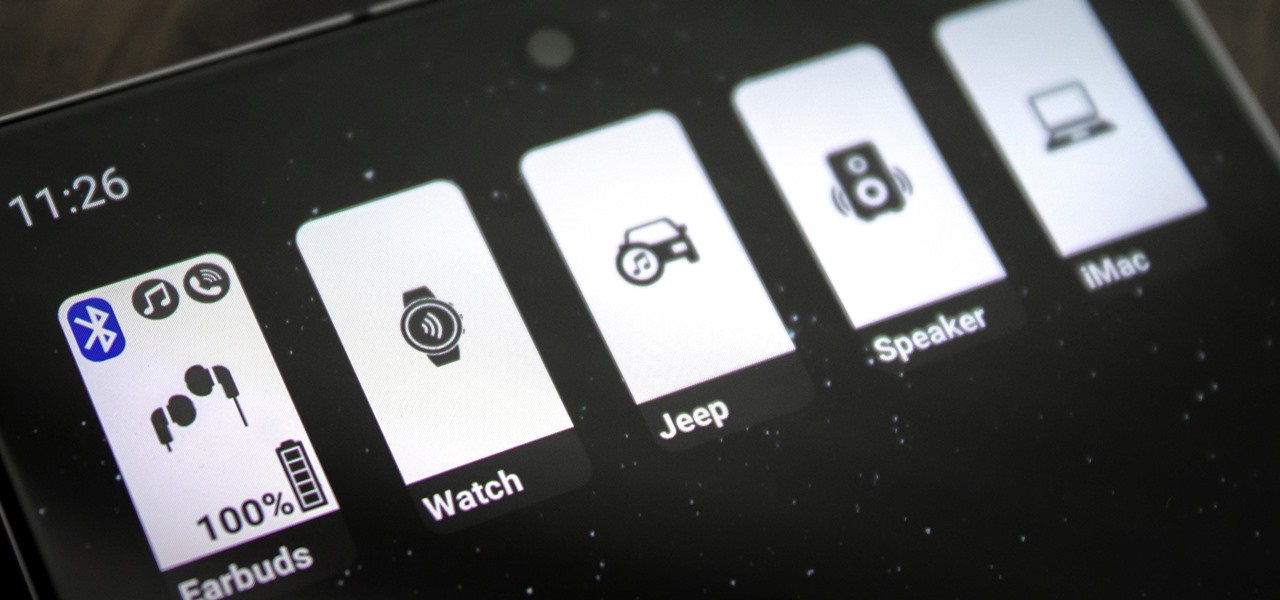
Back in Android 9, Google took away the expanding mini-menu for Bluetooth connections. The way it used to be, you could long-press the Bluetooth toggle in your Quick Settings, then the panel would turn into a fast-access menu for Bluetooth settings. It was a fairly minor feature, but dropping it has made it a lot harder to switch between your various Bluetooth accessories.
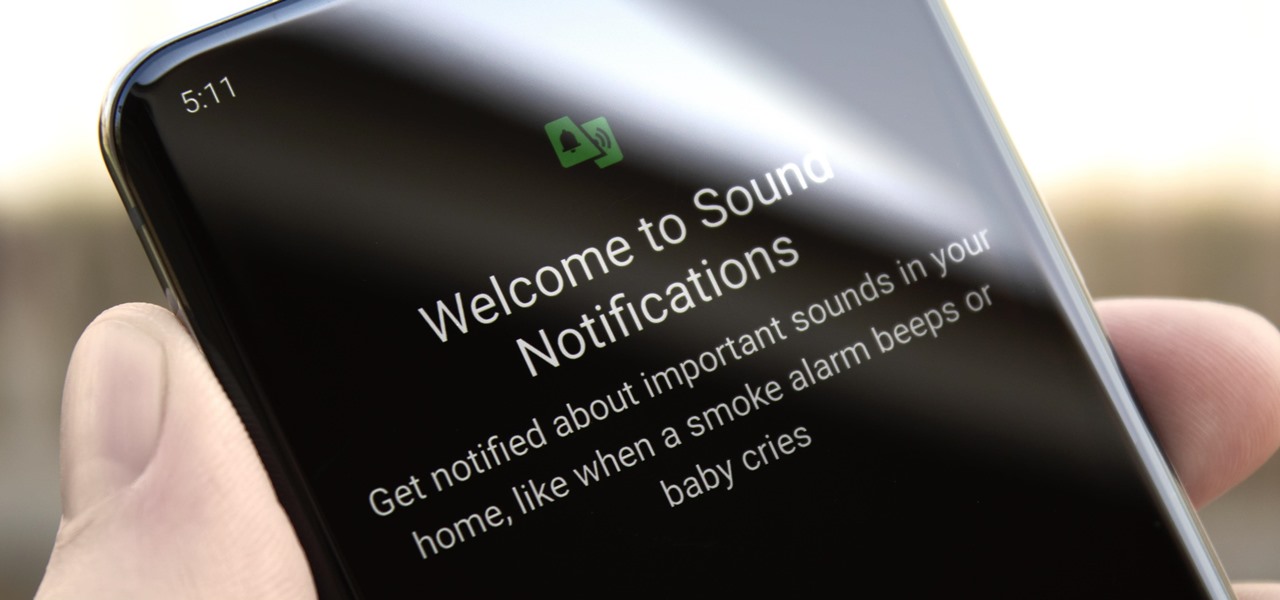
You don't have to be hearing impaired to appreciate one of Android's best audio accessibility features. This one can notify you when a baby is crying, a smoke alarm is going off, or when various nefarious sounds such as breaking glass are heard.

Progressive Web Apps hope to one day bridge the gap between websites and apps by giving the former more access to your phone's features, but they're not very common yet. In the meantime, you can take matters into your own hands with an app that uses your system WebView to render websites in a full-screen, borderless window with a few extra features — a lot like a native Android app.

Since iOS 11, a thumbnail preview appears on your iPhone whenever you take a screenshot. It's useful for access to quick sharing options and editing tools, but you can't disable the preview image. You can wait for it to disappear or swipe it off-screen, but that's as good as it gets — until now. In an iOS 14 update, there's an option to disable the screenshot preview — only you won't find it in Settings.
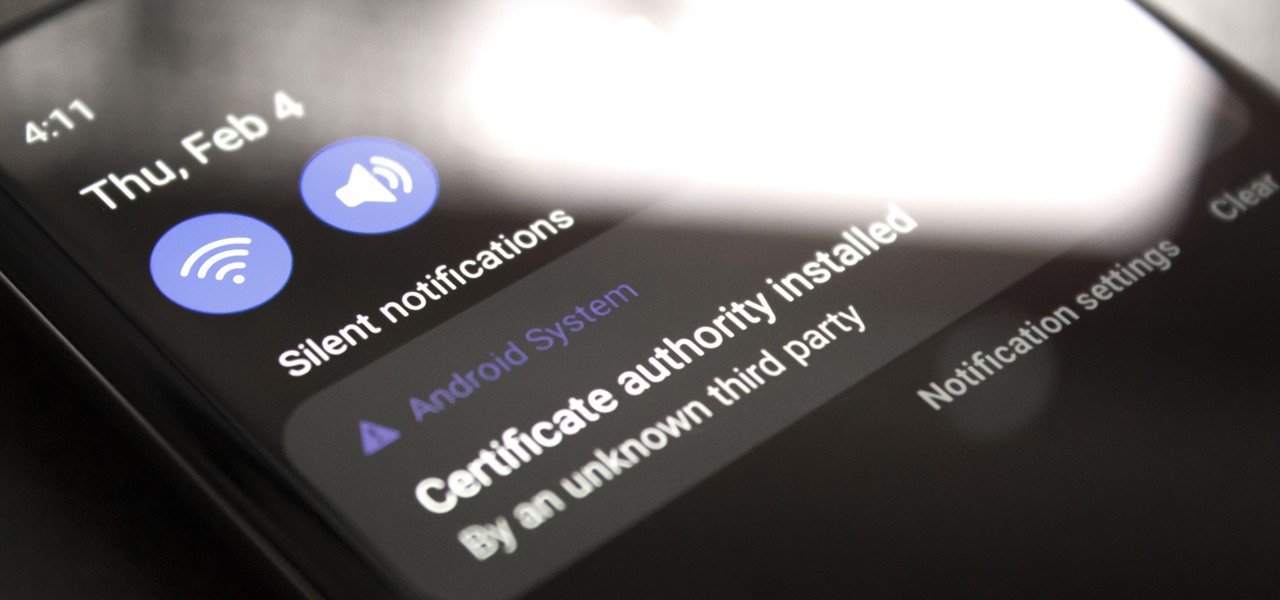
If you're using a VPN-based ad blocker with full HTTPS functionality on a Samsung phone, you'll get a notification informing you there's a third-party security certificate in use. No big deal, except it shows up every time you restart the phone. Samsung isn't alone in this type of annoyance, either.
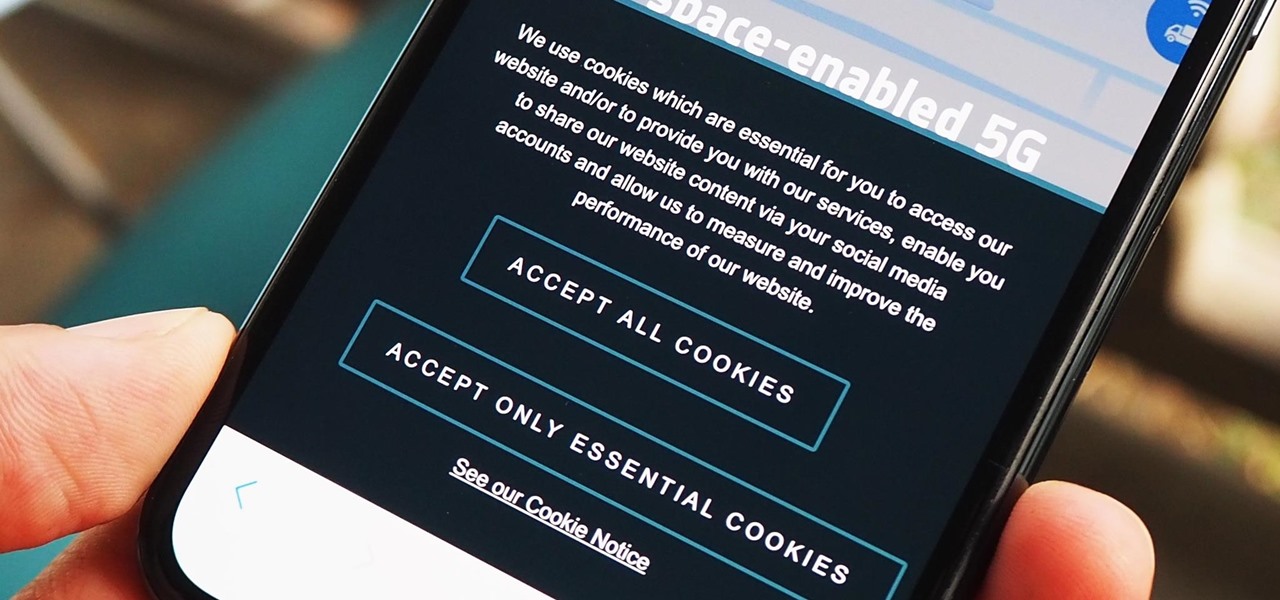
As a means to combat annoying and intrusive advertisements in Safari, Apple added native support for content blockers on the iPhone. Instead of being bombarded by notifications, banners, and pop-ups, content blockers prevent them from opening, which can also be said about those annoying cookie consent notices that many websites now have.

Android 11 has plenty of new features as you'd expect, including a fancy new embedded media player. Rather than a constant notification, your audio controls now get pushed up into the Quick Settings panel when playing music. However, to make way for this new media player functionality, your total number of quick settings tiles had to be cut from nine down to six.

Your Galaxy uses information from your SIM card to communicate with nearby towers and facilitate a connection. Which LTE bands you are assigned depends on a number of factors, including available bandwidth and your device's supported signals. But if speeds aren't great on your auto-selected tower, you can improve things by manually choosing a band.

So far, iOS 13's major point updates have all been pretty exciting for iPhone. We've seen iOS 13.1, 13.2, and 13.3 come and go, offering more than 60 new features and changes combined to that very first version of iOS 13. While iOS 13.3.1 was a minor update, its successor, iOS 13.4, is a return to form.

There are times when physically interacting with your iPhone is less than ideal, like when you're cooking or driving. Fortunately, iOS 13 has you covered regardless of the circumstance you may find yourself in. With the new Voice Control feature, you can control pretty much everything on your device without even touching it.

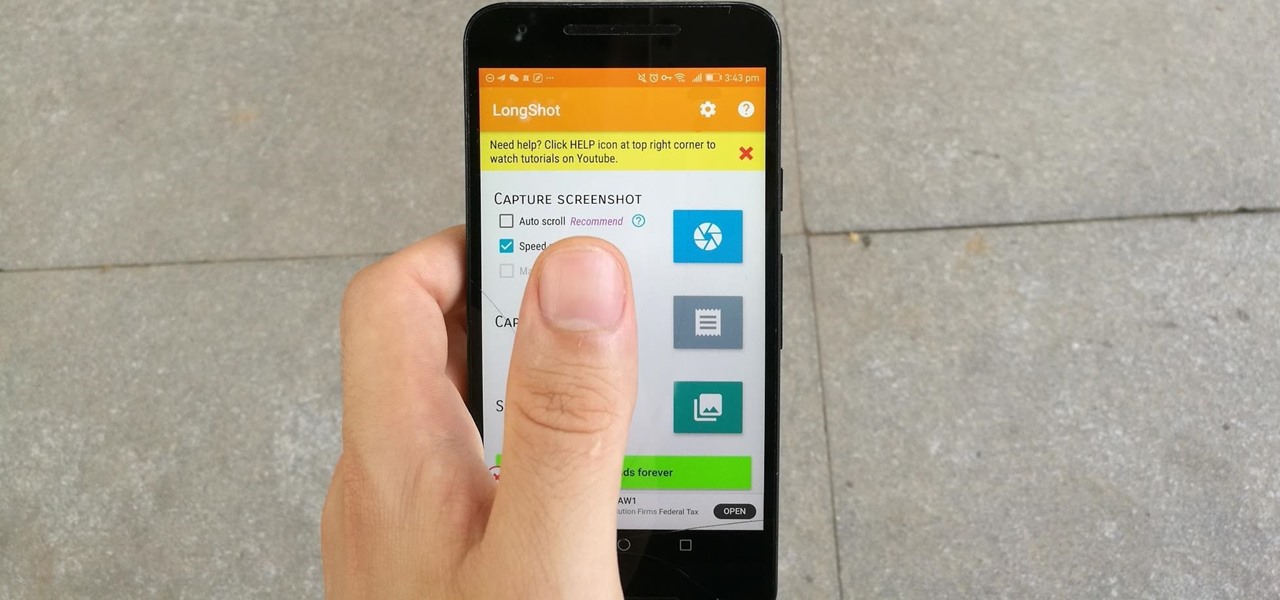
Some Android phones have had scrolling screenshots for years, but now that Apple added the feature to iOS 13 for iPhones, it should be standard on all phones. Thankfully, if your Android didn't come with the ability to take long, vertical screenshots, you can download an app that brings this feature to the masses.

The music and sound effects that play in the background of any videos you edit helps set the tone, so it's essential to get it right. Enlight Videoleap, an extremely powerful and popular mobile video editing tool for iOS, lets you quickly and easily add audio from your iPhone and the cloud, but things can still get a little confusing when you have a timeline full of clips.

If you want to get started sniffing Wi-Fi networks, you usually need to start with a wireless network adapter. But thanks to a Wi-Fi sniffing library written in Arduino and the ultra-cheap ESP8266 chip, you might not need one. For less than $10 in electronics, you can build a tiny Arduino Wi-Fi sniffer that saves Wireshark-compatible PCAP files and fits anywhere.

The tactic of brute-forcing a login, i.e., trying many passwords very quickly until the correct one is discovered, can be easy for services like SSH or Telnet. For something like a website login page, we must identify different elements of the page first. Thanks to a Python tool for brute-forcing websites called Hatch, this process has been simplified to the point that even a beginner can try it.

To hack a Wi-Fi network, you need your wireless card to support monitor mode and packet injection. Not all wireless cards can do this, but you can quickly test one you already own for compatibility, and you can verify that the chipset inside an adapter you're thinking of purchasing will work for Wi-Fi hacking.

The macOS 10.14 security update tried to make parts of the operating system difficult for hackers to access. Let's take a closer look at how its new feature works and what we can do to spoof the origin of an application attempting to access protected data.

Apple's latest mobile operating system for iPhones, iOS 12, was released to everyone Monday, Sept. 17, and it's the same exact build that developers and public beta testers received as the "golden master" on Sept. 12, the day of Apple's 2018 special event. Install it to start taking advantage of the 100+ features iOS 12 has to offer right now.

Due to weaknesses in the way Wi-Fi works, it's extremely easy to disrupt most Wi-Fi networks using tools that forge deauthentication packets. The ease with which these common tools can jam networks is only matched by how simple they are to detect for anyone listening for them. We'll use Wireshark to discover a Wi-Fi attack in progress and determine which tool the attacker is using.

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

You may have heard of a signal jammer before, which usually refers to a device that blasts out a strong enough radio signal to drown out the reception of nearby devices like cell phones. Purpose-built jammer hardware is outright illegal in many countries. Still, Wi-Fi is vulnerable to several different jamming attacks that can be done with Kali Linux and a wireless network adapter.

Wi-Fi tools keep getting more and more accessible to beginners, and the LAZY script is a framework of serious penetration tools that can be explored easily from within it. This powerful and simple tool can be used for everything from installing new add-ons to grabbing a WPA handshake in a matter of seconds. Plus, it's easy to install, set up, and utilize.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

One of Android's most glaring weaknesses is its lack of an iMessage equivalent. That is, of course, until now. There's one app that will allow Android users to experience iMessage on their non-Apple phone, complete with end-to-end encryption, message effects, and group messaging.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

The dark web is an intimidating place for a newbie hacker, but it's a powerful tool once you've learned to navigate it safely. To help you out with that, this guide will cover some need-to-know information for traversing the dark corners of the internet while keeping your identity and data safe. (Hint: Using Tor is not enough.)

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

When WhatsApp first came out in 2010, it quickly gained notoriety as a great way to meet new people all over the world thanks to group chats, which allow multiple admins for each group that can all add participants from their own contacts lists.

If maintaining privacy is an ongoing battle, the front line is your smartphone. Apple included several new security features in iOS 10, but at the same time, some of the best new functionality comes with potential privacy trade-offs that everyone needs to understand.

Apple just announced the iPhone 6, and no matter whether you've been with Android for a few months or few years, there's a good chance you're enticed by the idea of switching over to the other side.

Taking a cue from Apple and its Health app for iOS, Google has created a central hub to collect health and fitness data on your Android device. With it, you can share and sync health and fitness data, such as steps, heart rate, water intake, sleep quality, and calories burned, between different apps and devices and use your favorite app to view all the information.

Google Voice has a hidden feature that lets you record any phone call you're participating in, and unlike other apps, it doesn't cost a dime.

Unless you have unlimited cellular data, you probably connect your iPhone to every Wi-Fi network you come across. It could be a local coffee shop, public library, or just a friend's place. Wherever it is, you'll need to ask for the access point's password if it's a secured network, and that can be a hassle if the place is busy or the owner forgets the credentials. Luckily, Apple has a solution for this problem.

The battery on your iPhone can go from 10% to completely dead in a matter of minutes, or at least it can feel that way. Apple does prepare you with an alert when you hit the 20% and 10% mark, but it's easy to forget to charge your iPhone before it dies even with those notifications. That's why you should also be notified when your battery's down to 5% remaining.

Nova Launcher can be customized to do just about anything, but that can get overwhelming. If you're mostly interested in getting a Pixel-like experience, you'd normally have to spend all day tweaking mundane settings like dock padding and drop shadow placement. Well, we've already done that for you.

Apple released the first public beta for iOS 14.5 on Thursday, Feb. 4. This update is proving to be the most significant in some time, offering new features and changes like support for PS5 DualSense and Xbox Series X controllers, the ability to unlock your iPhone using your Apple Watch, AirPlay 2 support for Fitness+, Reminders sorting and printing options, 5G support when using dual-SIM, and more.

Apple wants to support the advertising economy, but its primary focus of late has been user privacy and security. In Safari, cross-site tracking, which lets content providers track you across websites and apps to show you more targeted ads, is disabled by default. However, content providers can get around that using less privacy-invasive ad measurements, but you can stop that too in iOS 14.5.

Samsung and Google have done some amazing work together in the past, particularly with Android related projects. But after years of an inexplicable lack of interoperability, the primary smart home hardware divisions from both companies are finally on the same page — starting right now.