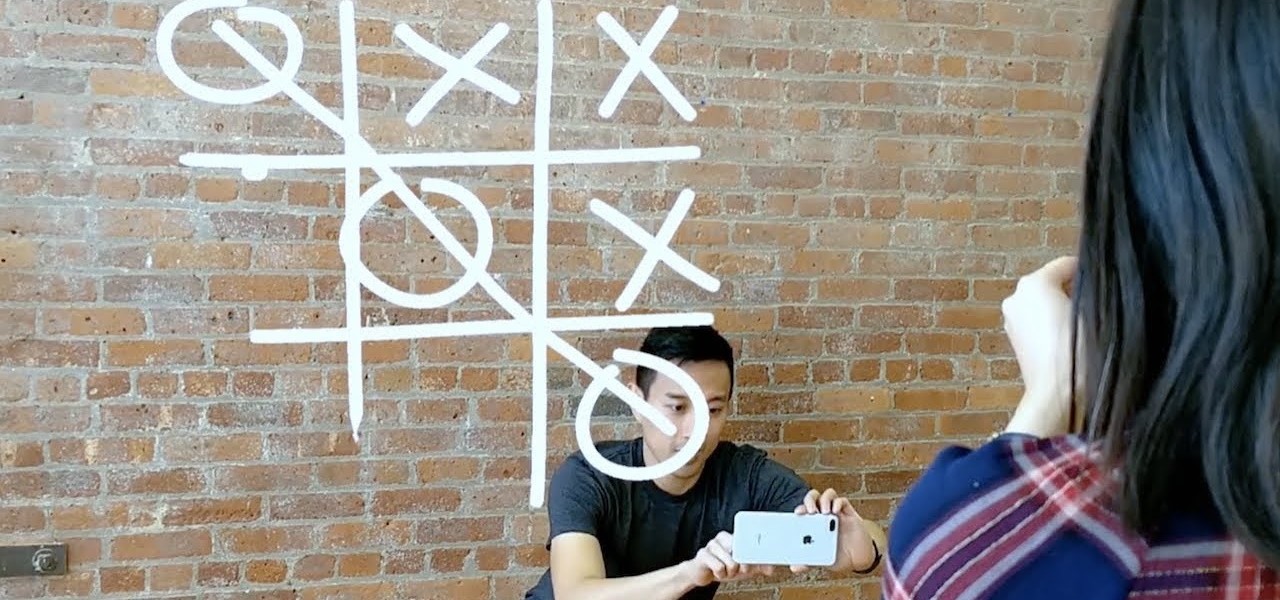Want to play "Viva la Vida" by Coldplay on baritone ukulele? Learn how with this video tab, which presents a complete breakdown of the song's component sections, chords and strumming & picking patterns. For all of the details, and to get started playing "Viva la Vida" on your own baritone uke, watch this free video ukulele lesson.

Want to play "Use Somebody" by Kings of Leon on baritone ukulele? Learn how with this video tab, which presents a complete breakdown of the song's component sections, chords and strumming & picking patterns. For all of the details, and to get started playing "Use Somebody" on your own baritone uke, watch this free video ukulele lesson.

Want to play "Hey, Soul Sister" by Train on baritone ukulele? Learn how with this video tab, which presents a complete breakdown of the song's component sections, chords and strumming & picking patterns. For all of the details, and to get started playing "Hey, Soul Sister" on your own baritone uke, watch this free video ukulele lesson.

Want to play "California Gurls" by Katy Perry on baritone ukulele? Learn how with this video tab, which presents a complete breakdown of the song's component sections, chords and strumming & picking patterns. For all of the details, and to get started playing "California Gurls" on your own baritone uke, watch this free video ukulele lesson.

Want to play "Wanted Dead or Alive" by Bon Jovi on baritone ukulele? Learn how with this video tab, which presents a complete breakdown of the song's component sections, chords and strumming & picking patterns. For all of the details, and to get started playing "Wanted Dead or Alive" on your own baritone uke, watch this free video ukulele lesson.

Want to play "Whistle for the Choir" by the Fratellis on baritone ukulele? Learn how with this video tab, which presents a complete breakdown of the song's component sections, chords and strumming & picking patterns. For all of the details, and to get started playing "Whistle for the Choir" on your own baritone uke, watch this free video ukulele lesson.

Want to play "When September Ends" by Green Day on baritone ukulele? Learn how with this video tab, which presents a complete breakdown of the song's component sections, chords and strumming & picking patterns. For all of the details, and to get started playing "When September Ends" by Green Day on your own baritone uke, watch this free video ukulele lesson.

Want to play "No Woman, No Cry" by Bob Marley on baritone ukulele? Learn how with this video tab, which presents a complete breakdown of the song's component sections, chords and strumming & picking patterns. For all of the details, and to get started playing Bob Marley's "No Woman, No Cry" on your own uke, watch this free video ukulele lesson.

Want to play "Sunday Bloody Sunday" by U2 on a baritone ukulele? Learn how with this video tab, which presents a complete breakdown of the song's component sections, chords and strumming & picking patterns. For all of the details, and to get started playing U2's "Sunday Bloody Sunday" on your own uke, watch this free video ukulele lesson.

Want to play minor jazz chords by on the ukulele? Learn how with this video tab from Glen Rose of Jazzy Ukulele. For all of the details, and to get started playing minor jazz chords on your own uke, watch this free video ukulele lesson.

With the reveal of Magic Leap's developer documentation last week, many questions have been answered—and several new ones have been raised as well. But since the Magic Leap One (ML1) isn't simply called the "Leap One," these are questions that the company probably has no interest (at least for now) in answering. Understandably, Magic Leap wants to keep some of the "magic" under wraps.

Want to play "I'm Yours" by Jason Mraz on baritone ukulele? Learn how with these video tabs, which present a complete breakdown of the song's component sections, chords, and strumming and picking patterns. For all of the details, and to get started playing "I'm Yours" on your own baritone uke, watch this free video ukulele lesson.

Hello guys, its been quite a while since my last post. (sorry for the lack of images)

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

In this tutorial, we learn how to get better at playing bass. To progress, you first need to practice with your bass! You need to not practice once a week, you need to practice regularly, no matter how busy you are. 30-45 minutes a day is adequate practice time to learn the bass properly. Next, you will need to be persistent, because it take commitment, even when you don't feel like practicing. If you let things slide, you can continue this process. Keep daily practice in your routine. Last, ...

Many of our members here at Null Byte are aspiring hackers looking to gain skills and credentials to enter the most-valued profession of the 21st century. Hackers are being hired by IT security firms, antivirus developers, national military and espionage organizations, private detectives, and many other organizations.

While we've seen Snapchat apply sky segmentation to AR content, the makers of the Blue Sky Paint app have applied similar capabilities to create and share airborne art.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

The only things that will get you into a good college is persistence, a will to learn, and of course… grades. If your grades are lacking that oomph they need to impress the schools and your parents, there's a few ways to aid in improving your scores. With a little effort and focus, your next report card will sport better grades.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

After publishing two batches of videos from its L.E.A.P. developer conference, Magic Leap has made the session on Seedling from Insomniac Games available to the public.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Hello Friends … My name is Suresh Senarathna and this is my first “How-To” post,

Hello Hackers! Welcome to my 2nd Post: This is a tutorial explaining how to hack android phones with Kali.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Samsung introduced a wave of seriously unique and innovative features on the Galaxy S4, including air gestures and weather sensors, but a lot of the features are actually just updated ones from the Galaxy S3. Unfortunately, one of those that returned was the dreaded increasing ringtone. In their increasing ringtone system, the ringtone will start off on a low volume and increase until it reaches your set volume. In theory, this is useful for not shocking the user with a sudden, blaring ringto...

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

The Windows 10 desktop and microphone can be livestreamed without using Remote Desktop Protocol (RDP) software and without opening any ports on the target computer. A hacker with low user privileges can monitor and exfiltrate a target's every move and private conversation in real time no matter where they are. Hackers are watching and listening, and there are few ways to protect yourself.

Kali Linux is established as the go-to operating system for penetration testing, but in its default configuration, it's less than ideal for regular desktop use. While in many scenarios, a live boot or virtual environment can resolve these issues, in some situations, a full installation is better. A few simple changes can be made to a Kali Linux desktop to make it safer to use in this environment.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

After improving hand-tracking and adding multi-user sharing features in the last Lumin OS update, Magic Leap has upped the ante yet again.

While Unity is already the leading 3D engine for augmented reality content in terms of volume, the announcement of Project MARS, a new augmented reality authoring tool, at Unite Berlin in June promised to expand AR development to a whole new audience of designers and other non-coders this fall.

Less than a week after debuting its AR Cloud platform in public with a multi-user installation of more than 100 participants, Ubiquity6 announced on Tuesday that it has closed a Series B round of funding totaling $27 million.

While mobile gaming, in the 10 years since the App Store launched, has matured to console-level quality, premium augmented reality games built with ARKit (or ARCore) have been scarce.

On the one year anniversary of the introduction of ARKit, Apple is planning to reveal major updates its augmented reality toolkit for mobile apps at its Worldwide Developers Conference in San Jose, California next week.