Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

So cute, so furry, and so chock full of parasites. While raccoons are fun to watch, they are neither friendly nor clean — and they can make you sick in more ways than one.

Just like your gastrointestinal tract, and the soil we walk on — a dust storm has a collection of bacteria, fungi, and viruses all its own called a "dust microbiome."
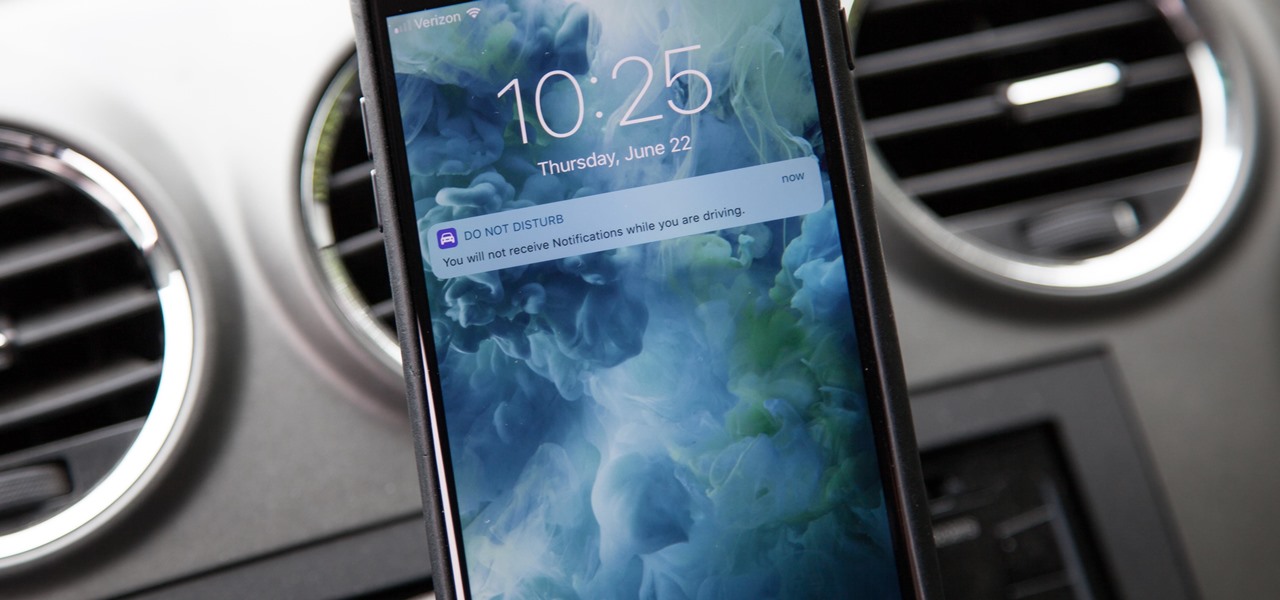
One of the most anticipated new Maps features in iOS 11 for iPhones is live and ready to keep you safe on the road. Right now, Do Not Disturb While Driving is opt-in, but if you missed Apple's on-screen prompt to enable it and want to turn it on, or if you accidentally enabled it but want it turned off, we're here to help.
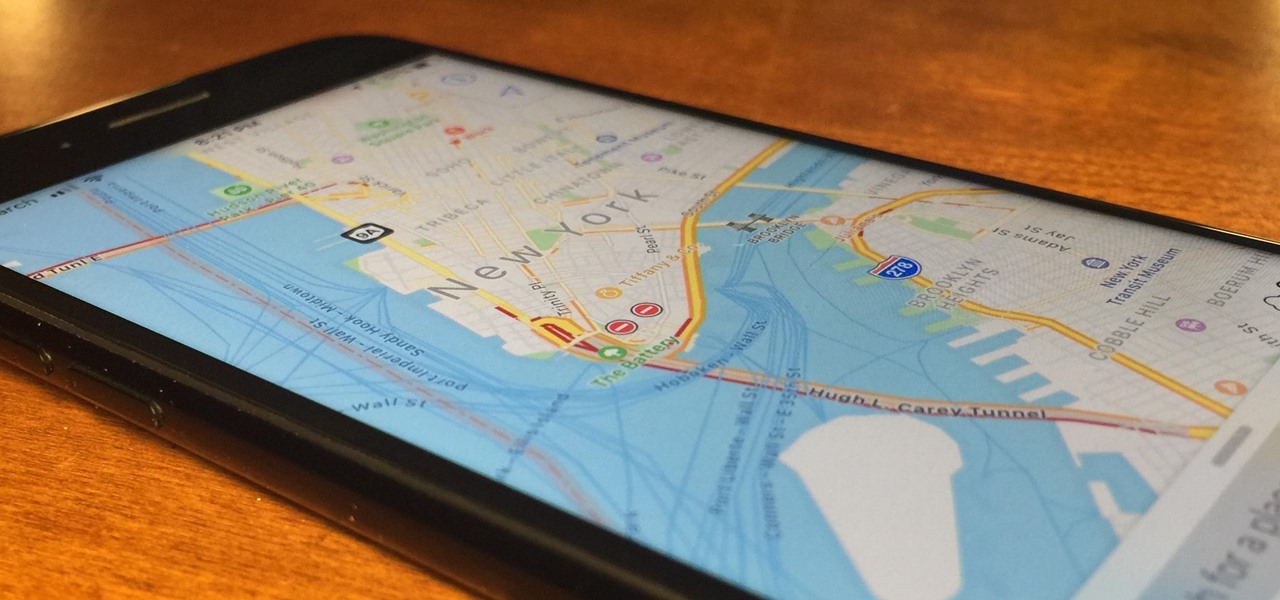
There are many impressive features in the new iOS 11 for iPhones, and the Maps app got a lot of love from Apple. This means it's finally about time you stop relying on Google Maps for all of your navigation needs, since Apple Maps is not only more accurate than it used to be, but it's way more helpful overall.

The world of augmented reality has seen a myriad of different products, from sensor-laden smartphones to robust holographic headsets, but Google Glass's failures nearly killed the middle ground.

Welcome back, my tenderfoot hackers! One key area on the minds of all hackers is how to evade security devices such as an intrusion detection system (IDS) or antivirus (AV) software. This is not an issue if you create your own zero-day exploit, or capture someone else's zero-day. However, if you are using someone else's exploit or payload, such as one from Metasploit or Exploit-DB, the security devices are likely to detect it and spoil all your fun.

Welcome back, my greenhorn hackers! One of the most important issues any hacker must address is how to get past security devices and remain undetected. These can include antivirus software, intrusion detection systems, firewalls, web application firewalls, and numerous others. As nearly all of these devices employ a signature-based detection scheme where they maintain a database of known exploits and payload signatures, the key is to either:
As a hacker or an aspiring one, You need to be careful and anonymous if your doing anything illegal. But you slipped up. Now someone is tracking you! Well luckily you read this post ahead of time and have a backup plan!

Welcome back, my budding hackers! This is the initial post of a new series on how to hack Facebook. It's important to note here that each hack I'll be covering is very specific. I have said it before, but I feel I need to repeat it again: there is NO SILVER BULLET that works under all circumstances. Obviously, the good folks at Facebook have taken precautions to make certain that their app is not hacked, but if we are creative, persistent, and ingenious, we can still get in.

There are a lot of manipulative people out there, but you don't have to let all of them push you around. It's time for the tables to turn.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

For over 20 years, a tiny but mighty tool has been used by hackers for a wide range of activities. Although well known in hacking circles, Netcat is virtually unknown outside. It's so simple, powerful, and useful that many people within the IT community refer to it as the "Swiss Army knife of hacking tools." We'll look at the capabilities of Netcat and how the aspiring hacker can use it.

Facebook just released its new "home on Android" last Friday, appropriately called Facebook Home. Taking a cue from Amazon's Kindle, Home serves as an "operating system" that runs over Android.

The herd of augmented reality cloud startups that emerged in 2018 have been hunted to near extinction, with Google-backed Ubiquity6 the latest to move from an independent entity to a wholly-owned asset.

In response to Apple's implementation of LiDAR sensors in iPad Pro and iPhone 12 Pro models, Google is looking to leverage the dual-camera setups in recent flagship devices as depth-sensing components.

Apple's Gatekeeper security software for macOS (Mac OS X) is vulnerable to remote attacks up to version 10.14.5. An attacker that's anywhere in the world can exploit MacBooks and other Mac computers by sharing a single ZIP file.

With just a few taps, an Android phone can be weaponized into a covert hacking device capable of running tools such as Nmap, Nikto, and Netcat — all without rooting the device.

Over the years, Magic Leap's long-cultivated shroud of mystery led some onlookers to buy into the company's dream before even trying the device, while for others, the secrecy seems to have stoked the kind of resentment and overcorrecting critique usually reserved for the mighty Apple.

It's possible to stream a MacBook's entire computer screen without using Apple's Screen Sharing application and without opening any ports on the target device. A hacker with low user privileges on the backdoored Mac may be able to view a victim's every move in real time no matter where they are.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Tony Parisi, the global head of VR/AR at Unity Technologies, has been passionately working with virtual and immersive spaces for a long time. And while the internet world we live in now is very different than when Parisi was co-authoring VRML (Virtual Reality Modeling Language) — an early attempt at creating 3D environments that would work in a web browser — some of the questions that were assumed answered are being asked again.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

While the USB Rubber Ducky is well known by hackers as a tool for quick in-person keystroke injection attacks, one of the original uses for it was automation. In this guide, I'll be going the latter, explaining how we can use it to automate Wi-Fi handshake harvesting on the Raspberry Pi without using a screen or any other input.

If you don't want to dress up as a vampire, witch, werewolf, or zombie again this Halloween, step things up a notch and go viral. There have been a ton of funny memes and absurd news since last October, so the only hard part is settling on the right one for inspiration for your costume.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

Ironing is a serious chore: hot, unpleasant, and frustrating all in one, but necessary if you don't want to look like you crawled out of bed just before work. While you might only turn to your flatiron when faced with wrinkled clothing, this little appliance packs the power to tackle even greater challenges—and here are our 10 favorites.

We've already seen the visual changes that Android 5.0 Lollipop has brought to the table, but Google spent just as much time altering things under the hood. Awesome new functionality and hardware capabilities have been added left and right, and with the OS already out now, it's high time we had a look at some of these tweaks.

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

Some iOS and iPadOS apps offer alternative app icons you can switch between. Beyond that, you'd have to create aliases in the Shortcuts app to customize the look of the app icons on your Home Screen. But that would mean two icons for each app in the App Library. Now, in a new software update, Apple has given us a middle ground for Home Screen icon customization.

There's a lot you can customize on your iPhone's Lock Screen — wallpapers and photos, widgets, the display mode, notifications, and even the time's font and color. But there's another feature that lets you add custom text for whatever you want, whether it's an inspiring quote, a reminder, a warning to anyone who dares touch your iPhone, or even just your name.

If you scan the notification panel on your Samsung Galaxy smartphone daily, all those red circles with numbers that litter the apps on your home screen and app drawer can feel like persistent nagging and unnecessary clutter rather than friendly reminders to check your app alerts — but you can do something about it.

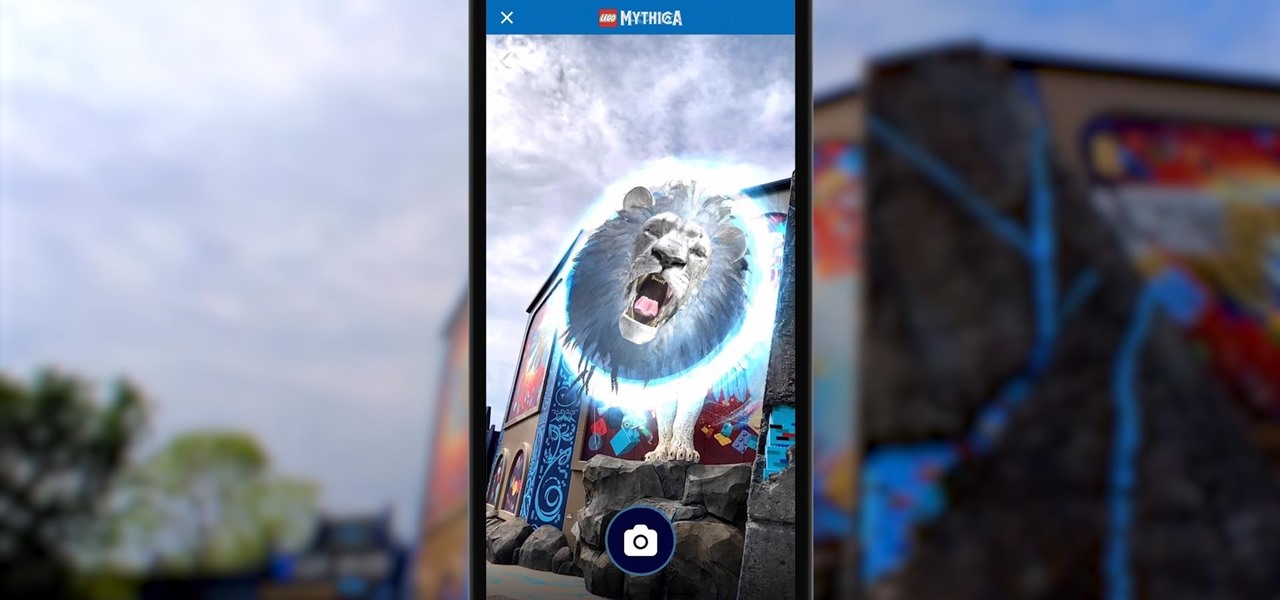
Few brands have been more enthusiastic about augmented reality than Lego, which has now expanded its AR experiences from toys to theme parks.

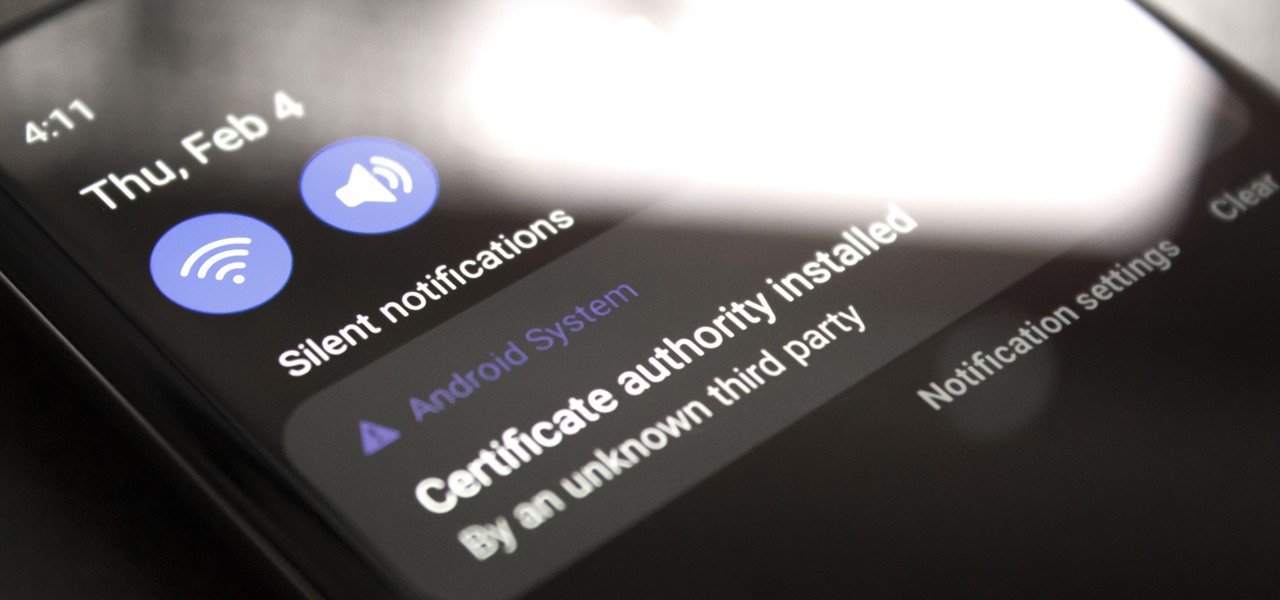
If you're using a VPN-based ad blocker with full HTTPS functionality on a Samsung phone, you'll get a notification informing you there's a third-party security certificate in use. No big deal, except it shows up every time you restart the phone. Samsung isn't alone in this type of annoyance, either.