
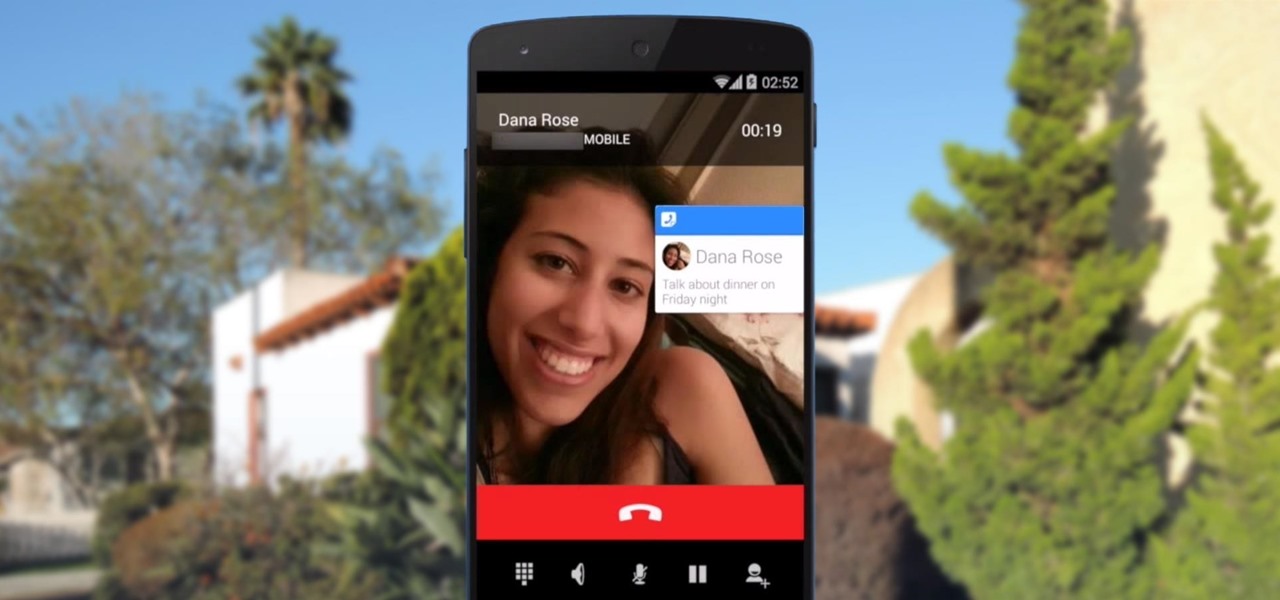
News: The Hollagram Selfie Booth Shows How Close We Are to Functional Holograms
Walking, talking, life-size holograms aren't just for staging Hatsune Miku concerts and reviving Tupac, Michael Jackson, and other fallen stars.


Walking, talking, life-size holograms aren't just for staging Hatsune Miku concerts and reviving Tupac, Michael Jackson, and other fallen stars.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.
Hello I have now asked for help a few times, so I figured I should contribute with what I can offer as of right now, which is many valuable sites if you need to look someone up.

Doxing is the act of finding one's personal information through research and discovery, with little to no information to start with. You may have seen doxing in the news, for instance when not so long ago, hacker team Anonymous doxed and reported thousands of twitter accounts related to ISIS. Doxing can be useful for finding the address of a coworker, or simply investigating people on the internet. The tutorial I will provide to you now will teach you the basics of doxing and how you can prot...

Christmas trees, once decorated and brightly lit, are the penultimate holiday decoration, but authentic pines lose their brilliance fast without any nourishment. Plus, they are major fire hazards without regular hydration. But watering one requires a lot of sliding around on the floor, and it can be hard to tell how much water is in the bowl beneath the dark, prickly branches. These five hacks can help!

I'm the type of person that rarely has an audible ringer enabled on my phone. Haptic feedback (vibration) is enough for me... most of the time. When my phone isn't in my pocket, I become the type of person who frequently misses calls and texts—and no one likes that person.
Every so often, we come across an app that makes us wonder "Why didn't someone think of this before?" This is definitely the case with developer Dor Sakal's latest offering, FloatNote.

Admit it: you've been caught muttering to yourself under your breath in very public places. Maybe you've gotten stares while wandering the grocery store talking to yourself out loud. If you're like me, you might even talk yourself through various tasks, giving the atmosphere a little background noise.
Because of Android's massive array of supported smartphones that carry vastly different display sizes and resolutions, the operating system uses a value known as DPI to determine the size of icons and visual assets that will best suit a given screen.

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

I can certainly say that I don't like be ignored, and you're probably right there with me on that. Also, if you're like me, you don't like being blocked on an instant messenger, either. There's something about being shafted like that that can really cramp your style.

It always sounds like a good idea to throw a party... until the party gets there. Next thing you know, you're running around hiding anything breakable, and once everyone leaves, you're stuck cleaning up the mess. But the worst part is footing the bill for everything, and if you don't charge at the door, your chances of getting anyone to chip in are slim to none once the party starts.

When browsing the web, I enjoy my privacy. It's reassuring that I can peruse the internet without the worry of having my activity tracked back to me, allowing me to leave fun, anonymous comments when I get the urge to troll.

Step1. Determine the type of job you want. Make sure that you have a detailed and complete profile on ‘linkedin’. You must also have a number of connections. Then decide which job you are looking for and the typical functions and titles. Also choose which type of industry you would like to work in and also choose what locations. You also need to write down specific names of organizations that you want to work for and who are they.

Why waste your vacation dollars on pricey hotel rooms when there are cheaper – and sometimes free – alternatives? Watch this video to learn how to find cheap (or free) places to crash on vacation.

Learn how to mingle. If the idea of walking into a room full of strangers strikes fear into your heart… welcome to the club. But there are ways to overcome this common social phobia.

One of the most important things in a person's life is sleep (some of us don't get enough of it, and some of us get too much). Why not make it one of the most comfortable things, too? Having the right sleeping attire is great for comfort, especially when you make them custom yourself. See how to make pajama tank top in this video from GiannyL.

Sleep is one of the most important things in a person's life. So why not make it one of the most comfortable things, too? Having the right sleeping attire is great for comfort, especially when you make them custom yourself. See how to make pajama pants in this video from GiannyL.

Tower Blocks is a Facebook game that allows you to test your speed at building the tallest tower ever! Watch this video tutorial to learn how hack Tower Blocks on Facebook (09/02/09).

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.
In this software tutorial you will learn how to create an island terrain in Unity 3D game engine. PART 1 covers creating a new project and exploring the interface.

In today's world of social media, there's really only two powerhouses—Facebook and Twitter. And those of you with Twitter accounts know the power of a Tweet. Getting more followers means reaching more people, but the vast majority of Tweeters are following only a handful of Twitterers themselves. Do you ever wonder why them? What's so special about these selected followed users? Is it worth it to follow them, too? That's up to you, but if you're searching for more people to follow, then it's ...

Backpacks are handy for camping, hiking, school and travel, but they can be difficult to pack properly. In this tutorial, learn how to pack your bag so that its light and efficient.

Chris Brown's "Forever" is a sweet song about dancing with a girl on the dance floor forever - about meeting that perfect person that you click with right away. The choreography from the music video for the song is likewise perfectly on cue and smooth.
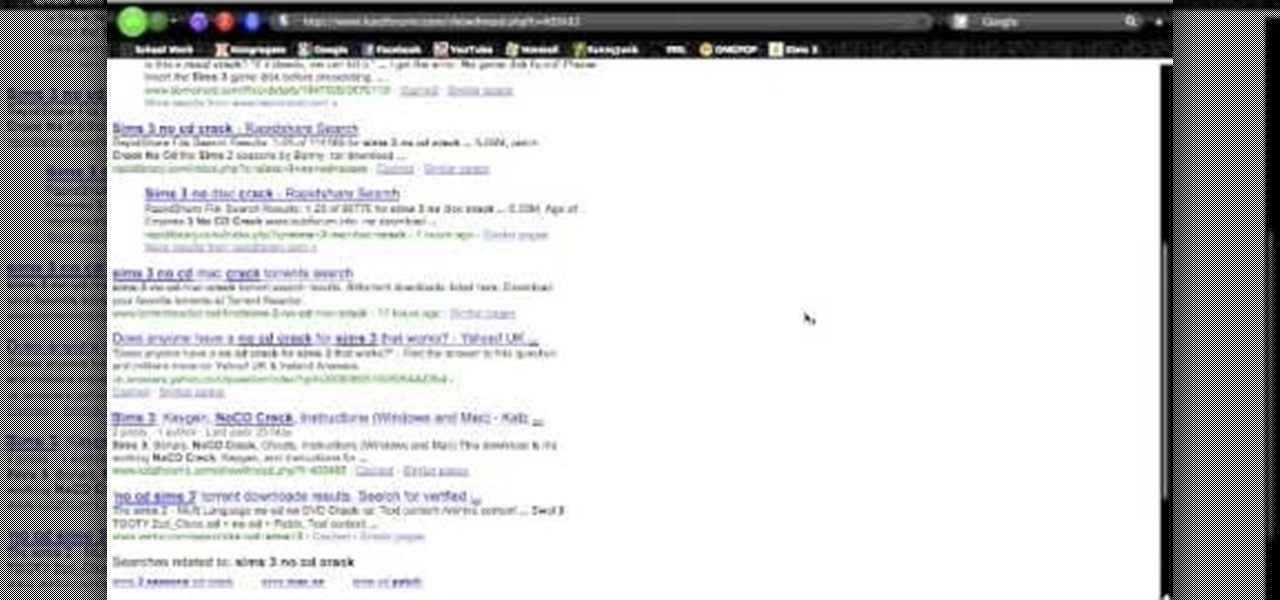
You'll need to have installed Sims 3 already, but this tutorial will show you how to get a special crack for your game that will let you play the game without needing the CD. Ideal if you have more than one person in your house who likes to play Sims 3!

The oxygen bubbler on your fish tank can really be annoying if left unchecked. The constant hum and vibrating can drive any sane person mad! But there's an easy way to silence it and bring you some peace, in this video you will learn how to silence your bubbler with a simple trick!

If you know someone who would appreciate being given a condom made out of yarn, you've come to the right place. This video will teach you how to knit a joke / prank condom that will make that special condom-loving person in your life very happy.

Appendicitis is one of the most painful and potentially dangerous maladies that can afflict a modern Western person, and recognizing the symptoms early is key to treating the disease and ending the pain. Watch this video for signs to looks for to tell if you or someone else is suffering from appendicitis. If they are, get them to the hospital now.
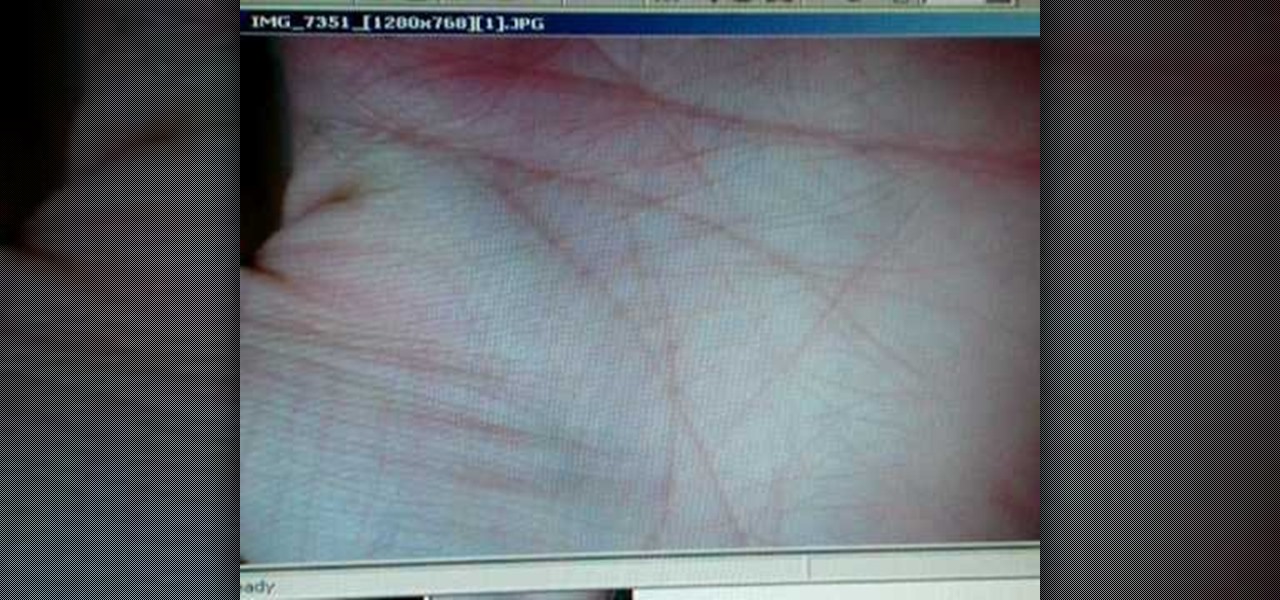
The left hand indicates what your subject has inherited from their family. Giving a reading on the left hand is different than the right, even for the same person. Peter John lays out a few palmistry principles if you want to give someone a palm reading on their left hand.

This quick lesson helps a student of palmistry give an accurate reading for a subject who has a very long hand, especially if the heart line lies low on the palm. Learn the palmistry principles which indicate an analytical and mathematical person.

Finding someone in a burning car is a scary emergency. Learn how to safely extract a person from a car fire after an accident. You'll need to be able to pull them through the windows, and if an ABC extinguisher is nearby, you can use that to help fight the flames.

In this clip, you'll learn how to avoid offending the person you admire when flirting. As a general rule, when flirting with someone, it's important that you be confident and natural. But, if you're feeling nervy, there's little shame in doing a little prep work with silly videos like this one. For more information, and to get started using this tip for yourself, take a look.

Learn how to avoid being to forward or pushy when getting flirty with the person you fancy. As a general rule, when flirting with someone, it's important that you be confident and natural. But, if you're feeling nervy, there's little shame in doing a little prep work with silly videos like this one. For more information, and to get started using this tip for yourself, take a look.

Learn how to avoid coming on too strong when flirting with the person you fancy. As a general rule, when flirting with someone, it's important that you be confident and natural. But, if you're feeling nervy, there's little shame in doing a little prep work with silly videos like this one. For more information, and to get started using this tip for yourself, take a look.

When you smile, the whole world smiles with you. As a general rule, when flirting with someone, it's important that you be confident and natural. But, if you're feeling nervy, there's little shame in doing a little prep work with silly videos like this one. For more information, and to get started using this tip for yourself, take a look.

In this quick clip, you'll learn how to start a conversation with someone you fancy. As a general rule, when flirting with someone, it's important that you be confident and natural. But, if you're feeling nervy, there's little shame in doing a little prep work with silly videos like this one. For more information, and to get started using this tip for yourself, take a look.

In this clip, you'll learn how to monitor your posture and maintain positive body language when flirting with a person you fancy. As a general rule, when flirting with someone, it's important that you be confident and natural. But, if you're feeling nervy, there's little shame in doing a little prep work with silly videos like this one. For more information, and to get started using this tip for yourself, take a look.

The person in this video is teaching us how to make toys with the help of polymer clay. As you can see the video you can say that the person there is a girl. This lady is teaching to make a teapot to her daughter. Her hand is focusing the camera. First she makes a little ball with the help of polymer clay. Then she made few lines on that ball and press that ball slightly on the top. Then she takes another piece of clay and presses it but that one is too small. Then she use another on quit big...
For all you Facebook-addicts out there (or anybody else that needs to access blocked websites anywhere they want), this is a video that you will want to watch. In just a minute and thirty seconds, any ordinary person can learn how you can access any website they want anywhere they want, bypassing any blocks and firewalls that the network administrator has put up to stop users from getting to their desired website without using complex computer commands or other complicated methods.

If you are into lockpicking but don't have a ton of supplies, check out this video to learn how to lockpick with merely a bobby pin and a pen. With a bit of pressure you should be able to get all of the pins up and open the lock. If you don't get it as fast as the person in the video, keep at it. It may take longer depending on the lock!