YouTube is home to some of the most vile commenters on the internet—completely void of literacy, accuracy of facts, respect, and goodness in general. Known to many as the cesspool of the internet, the YouTube comment board can be a tough place for a person who's not accustomed to hostility on the web. "Tracking my cookies? They will never get my recipe!"

Unfortunately, there are plenty of situations where having a can of pepper spray could come in handy. Even worse, in most of those situations your state of mind isn't really conducive to remembering important details like the facial features of the person who's trying to mug you, which means the police will have a harder time catching the culprit.

Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.

Every group of friends has that one person who's always late. Luckily, I've never had to deal with that issue because all of my friends are always late. Never fashionably, either. I'm talking hours late. Oh, we're having lunch at noon? Nah, it's at 3 p.m. now.
With the use of Terminal, anyone can run multiple instances of the same application on a Mac. When you have multiple windows open in a web browser, the windows are all running under the same Process ID (PID). But, with multiple instances, each has its own unique PID. So why would you want to run multiple instances of the same app? There are several reasons a person may run clones of the same application, but the most popular would be so that the user could multitask. Some applications, like t...

I have never been the most artistic person in the world, but never overlook a great piece of work when I see one. With George Lucas selling the Star Wars franchise to Disney for more money than I could make in ten lifetimes, it's safe to say the franchise has a lot of fans.

When you're capturing video with a DSLR, not having some type of stabilization system can lead to some pretty awful and shaky scenes. Camera instability is not only painful to watch, but breaks the fourth wall. Once that the invisible barrier between filmmaker and audience is apparent, it may break down that magical relationship between the two.

Greeting cards. Everyone hates buying them, they're way overpriced, and the majority of them go right in the trash after they're opened. So why do we still buy them?

Over the past few years, indie game developers have gathered together to release their products in the widely popular Humble Indie Bundle, a collection that gamers can purchase for whatever price they want. It's a win-win for both. Developers get more exposure for their games, and customers get tons of games for whatever they could afford. Heck, charities even get a little piece of the pie.

As we approach the holiday (i.e. gift-giving) season, don't forget to make sure to include the usual notes in your gifts indicating that they can be returned. Otherwise, you'll just cause the recipients to save your gifts until they can be properly regifted onto some other ungrateful chump.

Feelings can get hurt on Twitter as fast as an update. Everything is fine and dandy because two people are mutually following each other, then out of nowhere, one person has unfollowed the other out for seemingly no reason. Twitter doesn't notify users when someone has unfollowed them, so there are millions of people out there who get used for their follow! Well, now you can find out who unfollows you on Twitter with these mobile apps.

The car is arguably one of the worst places to receive a text message. You know you can't resist looking, and when you do, your attention is no longer on driving, it's on reading the latest gossip or whatever. You take your eyes of the road for just a few seconds and you could get an expensive ticket, or even worse—an accident. But you can't just ignore that notification sound or vibration, can you? So, if you just have to know what it says right then and there, why not at least do it in a sa...

Remember TwtRoulette? TwtRoulette was an online app that turned you into a so-called Twitter spy, letting you peruse someone's own timeline feed exactly how they saw it themselves. So, if you wanted to see what tweets Ashton Kutcher was seeing in his home timeline from the 700+ people he follows, you could.

There are several ways to send pictures to others on your smartphone—picture message, email, Bluetooth, and even by bumping phones together. Now there's an even more unique way to transfer pictures from one Apple device to another—with sound. Chirp for iPad, iPhone, and iPod touch

Have a super secret spy communication you'd like to send out, but don't have the funds to hire your own trusted operatives to deliver the message? Then stick to what you're used to—email it. SafeGmail is a browser extension that allows you to send encrypted emails right through your regular Gmail account. While this may seem a bit unnecessary for most messages, encrypting your email can definitely be useful.

You can do a lot with water guns. Have trouble waking up? Make a water gun alarm clock that (almost) no one could sleep through. Prefer real ammo? Turn your water gun into an airsoft BB gun. And if you don't have one, you can even make your own.

Believe it or not, an ammo box can still be of use to you once its rounds are gone. You can use it for storage, as a toolbox, or possibly even as a Faraday cage. But if you want to use it as more than just a container, why not turn it into a portable set of speakers that you can take with you anywhere? The ammo can speaker pictured above was made by Instructables user Dustin White. He started with an empty .50 cal box, though you could probably even use thinner 5.56 or 7.62 mm cans. He remove...

If you haven't met a person that's broken a pair of headphones, you might need to get out more. No matter how expensive or cheap a pair of headphones are, the sound can get buggy, the wire can get cut, or the headphone jack itself can be broken or ripped off the cord. But instead of buying a new set of headphones or borrowing the ones from your cousin with the earwax problem, you can easily fix it yourself.

Steam is an online platform that lets you download and play over 2,000 video games, from first-person shooters to RPGs, as well as a pretty long list of indie games. You can play on your PC, Mac, mobile device, or even your television, and it has a community of over 40 million gamers. Prices are different depending on the type of game and how new/popular it is, but they're generally about the same as what you'd pay for an Xbox or PlayStation version. They also have a decent list of free games...

Whether you want to use it to keep your guests safe or just to see who's the most drunk, it's always fun to have your own breathalyzer at a party. We've seen DIY breathalyzers before, like this one by Craig Smith, but how about an Arduino breathalyzer?

Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading their minds are two totally different things. The first EEG headsets available to the public were used mostly in gaming and even in fashion, but in the last few years, they've gotten a little more sophisticated.

Hello! Today I would like to introduce a simple tiny braid - so called the small wrap up. I recommend it to every person who wants to prevent the hair from falling onto the face. It is suitable especially for the people who have long or medium sized hair and very delicate skin. And for all who just want to quickly bind together some hair.

As deeply as smartphones are integrated into our daily lives, it's no surprise that people are finding ways to use them to stay healthy. From detecting cancer and radiation to diagnosing STDs, phones have come a long way, baby.

What if you forgot your car keys and that keyless entry remote banded to them, how are you going to get in your car? Well, if you haven't forgotten your cell phone, too, you can call up someone who has access to that keyless remote, so you can unlock your car or truck via the wireless mobile phone! What?!?

Step1. Make sure you get your facts straight. Note down the dates, names, and numbers, what was said etc while talking over the phone. It is also essential that when you present your letter of complaint that it is chalked full of facts so that when it reaches a decision maker you may get justice properly. Do not write a novel that is 30 pages. Keep it short and write in bullets. Remember that they are interested in facts only.

One lesson on falconry in Sherwood forest. This is a third person falconry video that shows how to handle falcons with a glove.

Want to learn a valuable skill? Well, just watch this video tutorial to see how to cross one eye or speak with an echo.

If you're the sort of person who regularly engages in DIY projects around your home, one imagines you'll need to take a shower every now and again. In this tutorial, Danny Lipford will guide you through the process installing a ceramic soap dish in a shower stall.

This quick instructional claymation video reveals how to make a Mamshmam claymation clay person for a stop motion animation video. Follow these simple steps to create a Mamshmam claymation character: roll into a ball, pinch the top to create the head, push the middle to make the stomach, squish the sides to create arms, push down clay to finish legs, and smooth him out.

Accidents happen at work. When there is a minor wound victim, take charge and help support the injured person. This first aid how-to video shows you how to treat work related minor wounds. These first aid tips for work are sure to keep your employees healthy and happy.

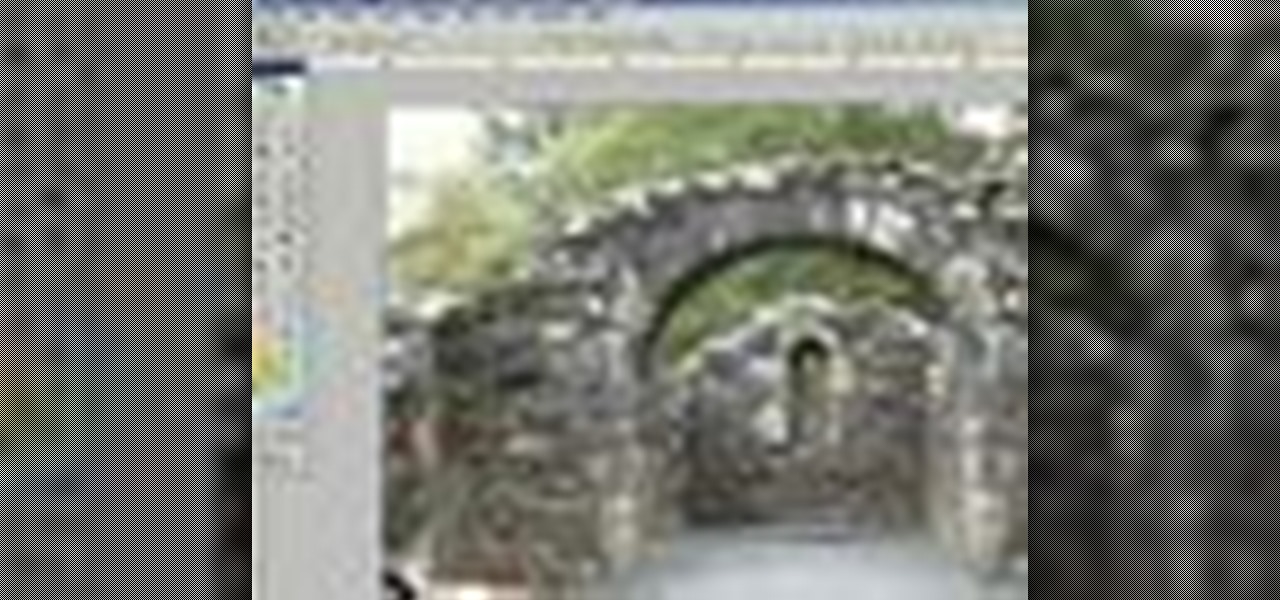
Learn how to cut the annoying tourist out of this stone arch photo by using textures that are already in the scene in Photoshop.

This video is a describing a day pack, with suggested items a person might carry with them on a day long hiking trip.

Spiderman demonstrates how to do the faced upside down card trick. The card you choose will be turned upside down. You turn the very bottom card upside down, make a person pick a card, flip the deck, get the card back, and flip the deck again.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.

Apple has packed a lot of new features into the iOS 13 update, and practically no core app has gone untouched. The Messages app, in particular, got plenty of love, including new ways to dress and use your Memojis.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Open-source intelligence researchers and hackers alike love social media for reconnaissance. Websites like Twitter offer vast, searchable databases updated in real time by millions of users, but it can be incredibly time-consuming to sift through manually. Thankfully, tools like Twint can crawl through years of Twitter data to dig up any information with a single terminal command.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

Analysis of photographs and social connections can be a huge component of social engineering. Understanding who a person is, as well as who they know, can establish links within a company. This information could be used by hackers to execute elaborate social engineering attacks.