When Kaci Hickox, a Doctors Without Borders nurse, returned to New Jersey from working with Ebola patients in West Africa in 2014, she was surprised by her reception. Instead of a quiet return to her home in Maine after four weeks on the front line of Ebola treatment, she was quarantined by the State of New Jersey in Newark. She later filed a lawsuit in U.S. District Court for violation of her civil rights, false imprisonment, and invasion of privacy.

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.

In this video, we learn how to prepare yourself for a major disaster. If you haven't planned ahead for storing water, you are going to be in big trouble. Your first option is to go purchase liters of water from the grocery store. The recommended quantity to store is 1 gallon per person per day. If you don't want to spend money at the store, you just need to fill up empty bottles with water from the tap and store these after cleaning. You can also fill the water in a large jug, just make sure ...

Fallout 3 is one of the first, if not the first, game to allow yourself to play your character when they are but a 1-year-old infant. The player is meant to be confined in a small area for this portion of the game, but need not be! This two-part video with instructions will show you how to escape the confines of your father's apartment and wander the games entire world map while still a baby! You will not be able to do many of the game's essential functions (you are a baby) but this is still ...

This video shows you a mind-reading card trick. This particular trick requires 8 cards: 4 kings and 4 queens. First, the subject is asked to memorize one of the 8 cards as they are laid out before the subject, face-side up. The cards are picked up and sorted in various ways and the subject is asked a series of questions. The questions are always asking whether the card the subject memorized is in a certain group that the trick performer presents. The card in question always is in the group th...

If done wrong, a backflip could be devastating. But if done right, a backflip just might make you the coolest person ever. This is a unique backflip tutorial that uses both video examples and instructional text. See how to do a backflip. Follow these steps, one by one, to see what you're doing wrong.

Watch this science video tutorial from Nurd Rage on how to get lithium metal from an Energizer battery. They show you how to get Lithium Metal from an Energizer Ultimate Lithium battery.

Here is a step by step tutorial for making a swimmable mermaid tail. Check out Video #2 for a demonstration of the tail in use!

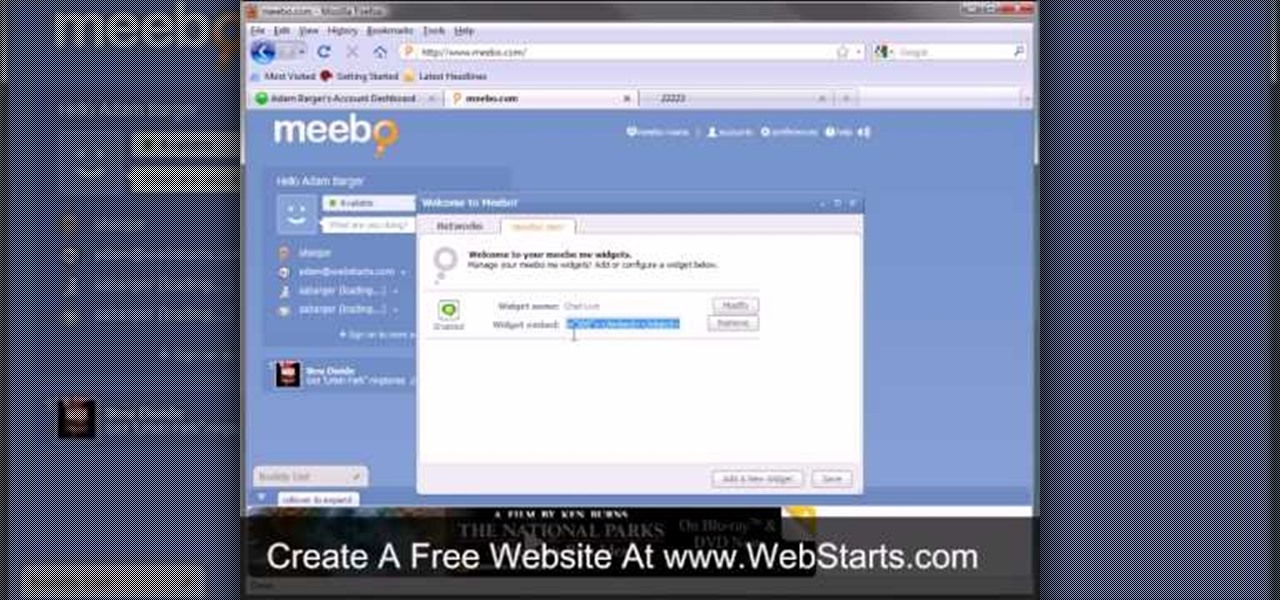
In this video, we learn how to add live chat to your website. First, go to the website Meebo and log into your account. Now, you will see the interface and the accounts you have associated with this client. There are several chat engines you can use through this interface. Once you have added all your chat clients, you can participate in the chats that occur on your website just from this one website. In order to add this widget to your website, go to preferences and choose the option for wid...

Already an impressive gaming machine, the Xbox 360 can be modified to play a wider variety of games. This instructional video demonstrates how to flash your Xbox 360 to play downloadable games from the Internet. This method only works on the Hitachi v0078fk drive and will void your warranty, but think of how cool it would be to pull this off.

This is a clever video that teaches you how to make a craft that is both fun to make, and also a useful item to have around the house- soap! This is from Living a Simple Life Blog and details how to make soap, just like the pioneers. To do this, you will need some equipment, a scale, scent, colorant, lard, lye, coconut oil, plastic containers to hold ingredients while you weigh them, a stainless steel pot, safety glasses, rubber gloves, a miter box, scraper, curing racks, a funnel and a plast...

If you've got a bobby pin and pair of handcuffs lying around, check out this video to learn how to modify your bobby pin to break into most locks. Using handcuffs, you can mold the tip of the bobby pin to allow the ability to open up things such as handcuffs and other locks.

The Paris-based technology conference Viva Technology, which hosted the likes of Apple's Tim Cook and Facebook's Mark Zuckerberg, is now over.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

Apple has several ways for you to communicate in the Messages app aside from texting — and that includes audio messages. You can send a voice recording via iMessage by long-pressing the microphone icon just right of the input field and speaking. However, by default, these audio messages self-destruct after two minutes, which isn't good if you want them archived.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

Smartphones and other Wi-Fi enabled devices send radio signals called probe frames to locate nearby wireless networks, which makes them easy to track by listening for their unique MAC address. To show how this kind of tracking works, we can program a NodeMCU in Arduino to sniff the air for packets from any device we want to track, turning on an LED when it's detected nearby.

Smartphones and laptops are constantly sending Wi-Fi radio signals, and many of these signals can be used to track us. In this guide, we'll program a cheap IoT device in Arduino to create hundreds of fake networks with common names; This will cause nearby devices to reveal their real trackable MAC address, and it can even let an attacker take over the phone's data connection with no warning.

In a previous tutorial, we were able to measure horizontal surfaces such as the ground, tables, etc., all using ARKit. With ARKit 1.5, we're now able to measure vertical surfaces like walls!

Hello, budding augmented reality developers! My name is Ambuj, and I'll be introducing all of you Next Reality readers to the world ARKit, as I'm developing an ARKit 101 series on using ARKit to create augmented reality apps for iPad and iPhone. My background is in software engineering, and I've been working on iOS apps for the past three years.

Whenever you attend or remotely watch a major Apple event, you're likely to see Phil Schiller, the company's senior vice president of worldwide marketing, unveiling a brand new product on stage. Outside of an official event, Schiller is the second most likely person (after Apple's CEO Tim Cook) you'll find delivering a rare tidbit of new Apple info or perspective to the public.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

A week into my internship, I experienced pretty serious back pain and slight difficulty breathing. I scheduled a doctor's appointment to make sure nothing was wrong, and I got a surprising diagnosis: bad posture.

Maine reported their first measles case in 20 years yesterday, June 27, in a press release from the Maine CDC. Many other people may have been exposed and could show signs of infection soon, with the potential for outbreak brewing. The last measles case in Maine was in 1997.

It's not always easy to get to the root of an infection outbreak. Epidemiologists study infected people, contacts, and carefully examine where the infections happened and when. In the case of a 2012 outbreak of pertussis — whooping cough — in Oregon, scientists just published an analysis of how vaccination status affected when a child became infected during the outbreak.

When you're taking a video in the Camera app on your iPhone, there's a little white shutter button in the corner that lets you take a still image while you're filming. Apple brought that same concept over to the FaceTime app in iOS 11, iOS 12, and higher, so you can take Live Photos of your friends during video chats.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

The culprit probably wasn't what doctors were expecting when a 57-year-old man in Hong Kong came to the hospital. The patient was admitted to the intensive care unit in critical condition. A clue to the cause of the infection would lie in the man's profession—he was a butcher.

At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

Hello people again, I wrote my last post about crypto about 10 months ago, now I will introduce something not fresh for the science, but fresh for the people who wants to learn. In my http://null-byte.wonderhowto.com/forum/cryptography-0161538/ post of crypto concepts, there is just basics, today we will see something that targets wide concepts like Symmetric crypto, Public Key Cryptography, Hashing, Keys etc...

Greetings my fellow aspiring hackers, It's still Christmas and we have a lot of things and hugs and kisses and ... to share ( you know the things that you do ). I have never done this before but I just felt to encourage you on the quest for knowledge, security and defence, skills and a whole lot more that comes out as a result of pursuing hacking. What we mean by hacking on this forum is White hat Hacking and OTW has great articles on it and I don't need to explain myself on that one.

Whether it's terrorism or brain-hungry zombies you're neutralizing, first-person shooters are an awesome way to immerse yourself within a new world and kill some time with your iPad or iPhone. And with so many games available in this genre, we wanted to show off ten of our absolute favorites.

Hello, hackers and engineers! Today we are going to dive a tiny bit deeper into the secrets of psychology, and how we can use them with hacking and social engineering attacks.

Look away from this screen and try to remember the sound of your childhood hero's voice. Did you do it? Do it again, and this time pay attention to your eyes.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

Are you interested in beginning research of your family's history? I began this journey about 3 or 4 years ago and here is what I found. I've done almost ALL of my research online, and gotten farther, faster and more comprehensively than anyone else who has researched my family the old fashioned ways. This is the kind of thing that technology is made for. Here's how to use it.

Wear your heart on your sleeve - literally - by crafting this origami heart pin. Show some love for Cupid's holiday by creasing and folding your way to origami perfection.

In this first aid video, learn the simple procedure of caring for burns and scalds, in sign language. It's specifically geared to helping the deaf and hearing impaired.