Maybe you decided to make your own pumpkin pureé because of all the buzz about canned pumpkin actually being squash (which, by the way, is a load of bull: it's made with ugly pumpkins, but pumpkins nonetheless). Or maybe you just wanted to be that person that proudly proclaims that they made everything from scratch for their Thanksgiving feast this year (ahem, me).

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

Black Mirror, Netflix's technology-horror anthology, never fails to provide thought-provoking entertainment centered around emerging and futuristic technologies, and the third season's second episode, "Playtest," delves deep into the worlds of mixed, augmented, and virtual reality. While designed to leave you haunted by the end, offering a more "evil" narrative than we'll likely see in our actual future, the episode explores possibilities that aren't as far off as one might think.

The 12.9-inch iPad Pro was released in stores on November 11, 2015, and a couple days later I went to an Apple Store and to check it out in person. I had mixed feelings about the tablet, but was intrigued overall—so much so that over the next few weeks, as I found myself hearing more and more about the device, a thought began to take hold in the back of my mind—I really want one. At the same time, I was hesitant about dropping roughly 10 Benjamins for a tablet!

Hello Guys, Today I have made a script for ddosing sites with VBScript! And I don't know how you guys do it, but I've made a script that refreshes the page in a chosen amout of milliseconds. And if you want it a number of times or if you want it to go on and on. And this is a script to run it on your botnet. But again I don't know if this works on your botnet too.

Counter-Strike is one of the most popular first-person shooters of all time, and deservedly so. What originally started out as a third-party Half-Life mod garnered such a cult following that Valve had to hire the developers and purchase the intellectual property to make it an official standalone release.

Now that smartphones have ensured that we're connected to the internet 24/7, online privacy has become more important than ever. With data-mining apps hoping to sell your information for targeted ads, and government agencies only one subpoena away from knowing every detail of your private life, encryption has become our last line of defense.

If you love quenching your thirst with an ice-cold glass of lemonade but aren't a fan of artificial powder mixes, then this hack is for you. When your next lemonade craving strikes, instead of reaching for a glorified Kool-Aid packet, get an instant sip of summer by using pre-made, frozen lemon cubes to create your favorite drink. And this recipe isn't just easy to make, it's perfect for any number of servings, from single to several, or even a pitcher, if necessary.

Chips are one of the most overpriced snacks on the market, and they're wildly unhealthy... even though they don't need to be.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Valentine's Day is upon us, and it's the perfect time to show those you love (or like) how you feel about them by making them a homemade sweet treat.

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.

Chestnuts are roasting on an open fire, which can only mean one thing: Christmas is nearly here. It's the time of year we're supposed to spend with family and friends, but usually we spend it stressing out over what to buy everyone on our list without going over budget, or shopping for decorations or holiday-friendly food items.

Welcome back, my novice hackers! More and more, the world is turning to and adopting the smartphone platform as the digital device of choice. People are not only using smartphones for voice communication, but also web services, email, SMS, chatting, social networking, photography, payment services, and so on.

So, you want to become anonymous? well let me give you everything I know (or at least most of it) to you.

In the digital age, maintaining your privacy is a never-ending battle. All sorts of companies and agencies have access to your data, and quite a few can eavesdrop on almost every method of modern communication.

By now, a mobile phone that isn't "smart" is about as hard to come by as a TV that isn't high definition. As a result, members of older generations who were previously reluctant to purchase a newfangled smartphone have no other choice but to cave into the more recent trends when their old device finally breaks down.

When it's time to get down to work, a clean, organized workstation is key to accomplishing tasks and being more productive. Or, so we thought.

There are over 1.6 million apps on the Google Play Store, which makes it the largest collection of mobile apps on the planet. However, a large portion of this total is occupied by apps with overlapping functions—think social media, news, weather, music players, and various other categories where developers compete against one another to garner the largest user base.

Many people deal with motion sickness on a daily basis, and if you're reading this, chances are you're one of them. Kinetosis can make your stomach roll, your entire body sweat, and make you feel fatigued and dizzy at even the slightest movement, whether it's related to carsickness, seasickness, or airsickness. And let's not forget the worst part—vomiting.
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

It's no secret that exercise is good for you, but you may be surprised to know that a good workout can actually boost your memory, too. They key to giving your body and your brain muscles a good workout is by adding more weight and pushing hard for an extra 20 minutes.

Apple designed Find My Friends in 2012 as a means for better-connecting with friends and family. It's pretty useful for scenarios when you need to keep tabs at an amusement park or to get a live ETA when your buddy is coming to pick you up from the airport. You can even share your location with others so they can track your whereabouts as you go about your day.

Whether you are sending your phone in for repairs or finally selling it to upgrade to a new flagship, you are going to need to make sure all of your personal data is removed from your device.

Unruly customers. Crazy exes. Horrible bosses. When you need proof of insanity or just want it for your records, recording a phone call is a must. Problem is, it's not the easiest thing to do on an iPhone — but it's completely possible.

I like to think of myself as a pretty calm and even-keeled person. I rarely get angry or annoyed, and I don't even get peeved very frequently.

Your grater and microplane may look like single-purpose tools, but they're actually one of the most diverse appliances in your kitchen. Sure, everyone knows to use a grater on cheese and a microplane on citrus zest, but why stop there? Here are 10 things you may not have thought to grate:

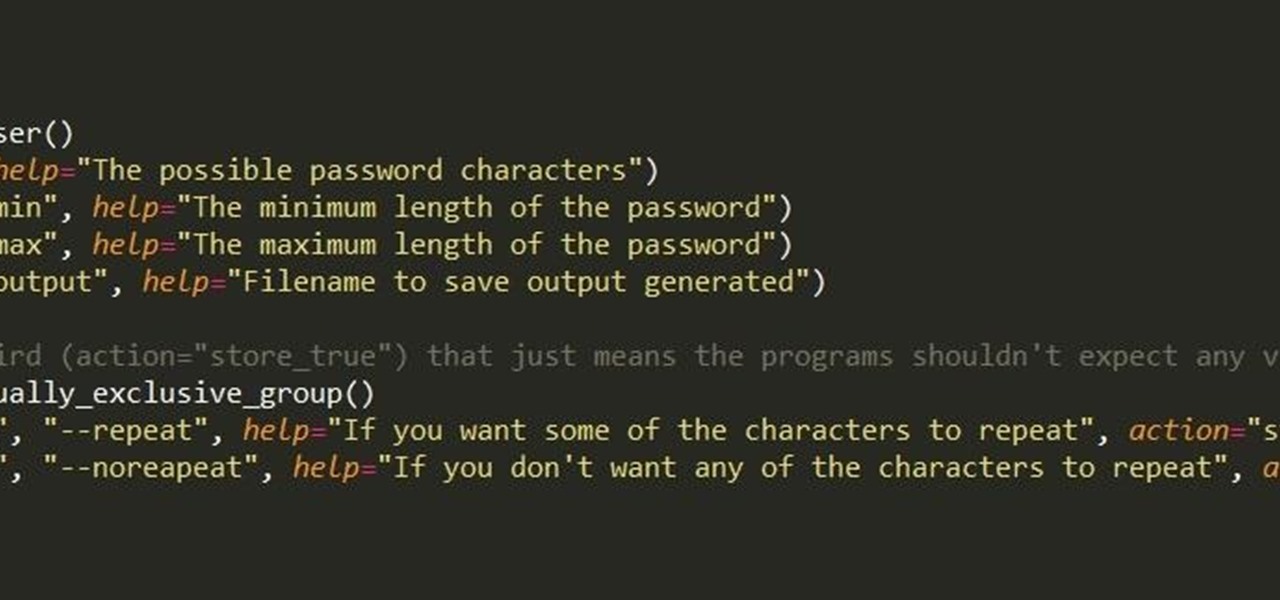
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

Few things in life are as relaxing and enjoyable as baking. When I'm having a bad day, I make cookies. When I'm stressed out, I bake a cake. When I have a free Sunday with nothing to do but listen to music and drink coffee, I bake a tart or a batch of cupcakes.

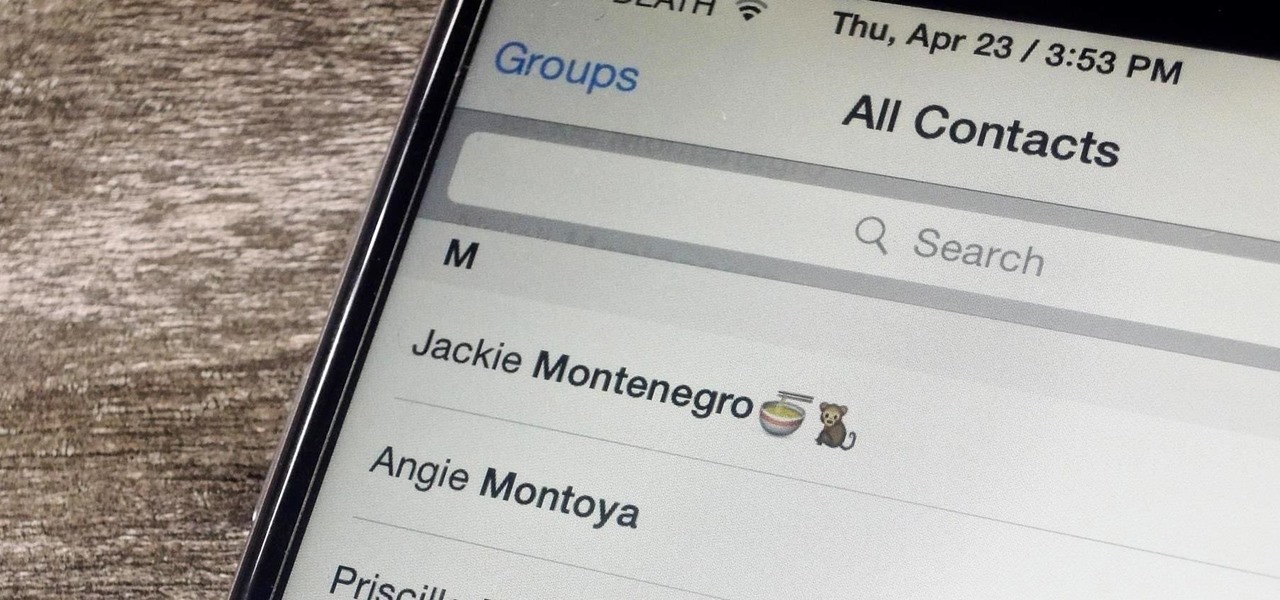
Organizing contacts is a bitch, especially on the iPhone. Some contacts will have multiple entries, you can only delete contacts one by one, and certain types of contacts can't be deleted at all. If that isn't enough to make you pull your hair out, then I don't know what will.

The gag reflex: it can interfere while in the dentist's chair, upon seeing another person throw up, or even just getting a whiff of a disgusting, stomach-twisting scent. Every time this reflex kicks in, it stops us immediately, inducing a choking, gagging, coughing fit.

Enough with zoodles (zucchini noodles), spaghetti squash, and carrot 'pasta' spirals. A well-prepared dish of zoodles with sauce is beautiful and tasty, but let's get real, it doesn't fill you up. If you use it as a meal replacement, then you'll be hungry about 30 minutes later.

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

There are so many cutesy pink, red, and heart-shaped desserts and drinks put out on Valentine's Day, but none of those really get you into a low-light mood. Instead, turn up the heat with one of these aphrodisiac cocktails for grown-ups.

The ability to make a meal for yourself used to be one of those life skills you had to learn or otherwise you would starve, but the rise of convenience foods, takeout, and other aspects of modern living have made it entirely possible to be a grown person and not know what to do in the kitchen.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

My years in the restaurant business have taught me many things. Some of those things are best left unsaid and other things require a PhD in vulgarity, but the one thing I learned that I keep coming back to night after night is that you do not have to spend a lot of money to drink excellent wine. This is especially true of champagne...I'm sorry, sparkling wines.

Being the bearer of bad news is unpleasant; there's nothing more uncomfortable than offering up a spoonful of negativity. Whether you're a supervisor who spends a lot of time interviewing and rejecting candidates, or simply someone who has to say "no" to a friend, it's never fun to break bad news. But sharing unpleasant words or feedback with another person can become less of a burden with a few simple steps.

If you struggle with deciding which wine you should buy for an intimate dinner, or the type of beer with the highest alcohol content that doesn't taste like tree bark, then check out some of these great alcohol-friendly apps to make better booze decisions.