With thousands of people across the country protesting, you might be thinking about joining the march. But as is too often the case, law enforcement has been called to oversee the protests, and interactions aren't always peaceful or lawful.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

Whether you're calling the unemployment office, a popular radio contest, or any other phone line that gets super busy, having to recall the number manually is a pain. Whatever you do, however, don't punch in the same digits over again and again — our smartphones can help do it for us, saving our time (and sanity).

A stager is a small piece of software that's typically used by malware to hide what's happening in the early stages of infection and to download a larger payload later.
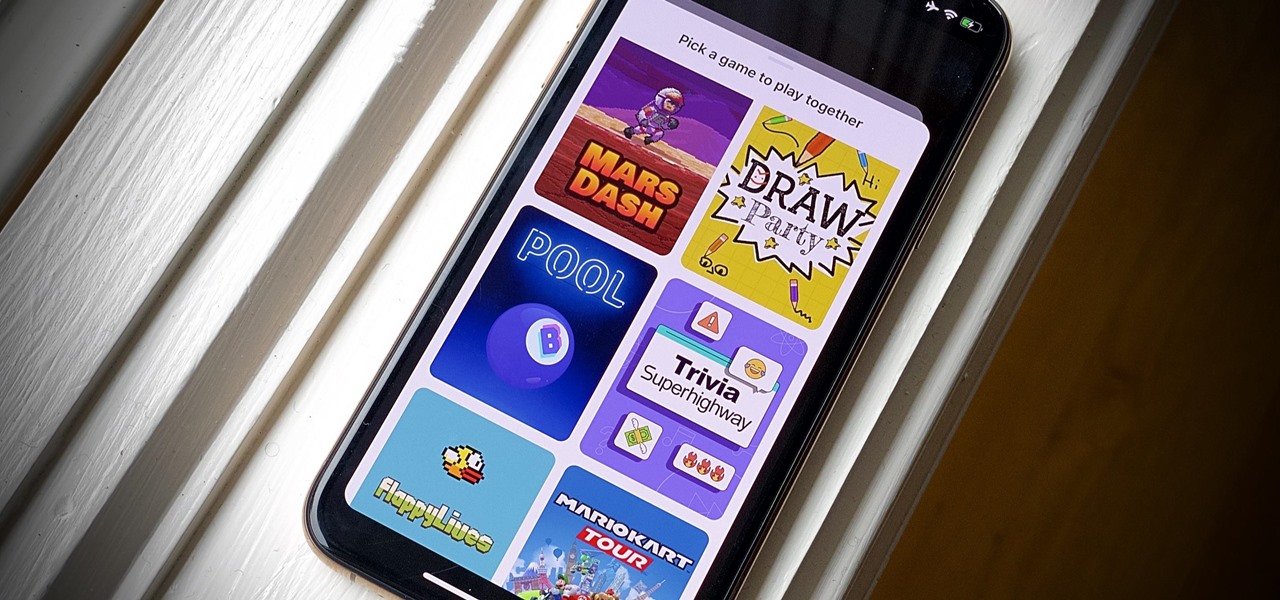
Even for those of us who enjoy spending time alone at home, at a certain point, it just gets boring. We all need social interaction, but with stay-at-home orders, that can be hard to come by. If you're feeling the itch to hang out with friends and have a good time, you should know there are plenty of free multiplayer games for iPhone and Android that will let you do just that — remotely.
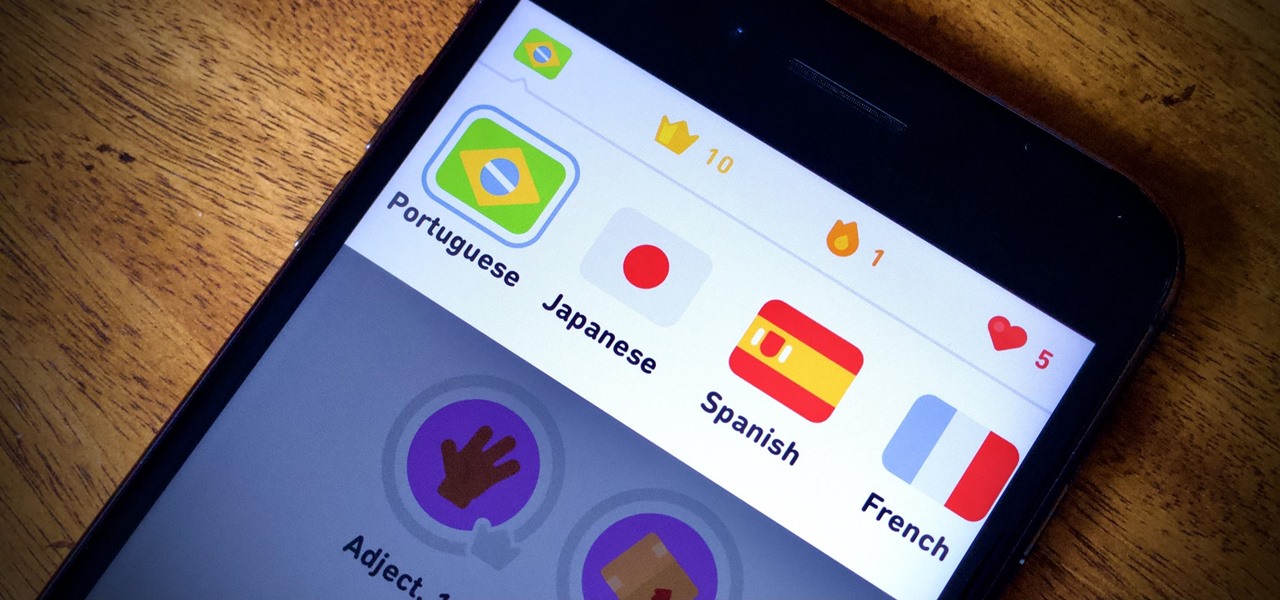
There's only so much Netflix and TikTok a person can take in quarantine before they've had enough. We've only just started our stay-at-home lifestyle, but already TV and movies are getting old. The COVID-19 lockdown doesn't just have to be a mindless watch party, so why not take the time to learn a new language?

Whether you were exposed to the COVID-19 virus or just taking precautionary measures, self-quarantining is a tremendous disruption for anyone. Still, we all have to eat, pandemic or not. But unless you like eating canned food for two weeks, you're going to want to explore other options. That's why food delivery apps are going to be so necessary during such a hectic and uncertain time.

Congratulations, you've made it deep into the middle of flu season! If you're reading this, you're either a very smart preemptive sick day prepper, or already in the throes of fighting off a cold or flu situation.

If left unattended, a hacker with a USB Rubber Ducky and physical access to the computer can infiltrate even the most secure computer. Such attacks often go undetected without the use of a tool like USBRip, which can provide you with assurance that your device hasn't been compromised.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

Despite some of the biggest players in tech still lagging in terms of offering smartglasses options, there are nevertheless a number of smartglasses makers, including North and Vuzix, with consumer-grade smartglasses on the market right now.

While many people may use Bluetooth every day, the majority don't know how it works or that it can be hacked. Bluetooth hacking gives a clear window into the world of the target. Nearly every device has Bluetooth capabilities, and people store a great deal of personal info on their phones and tablets. Hack their Bluetooth connection, and you may be able to access all of that data.

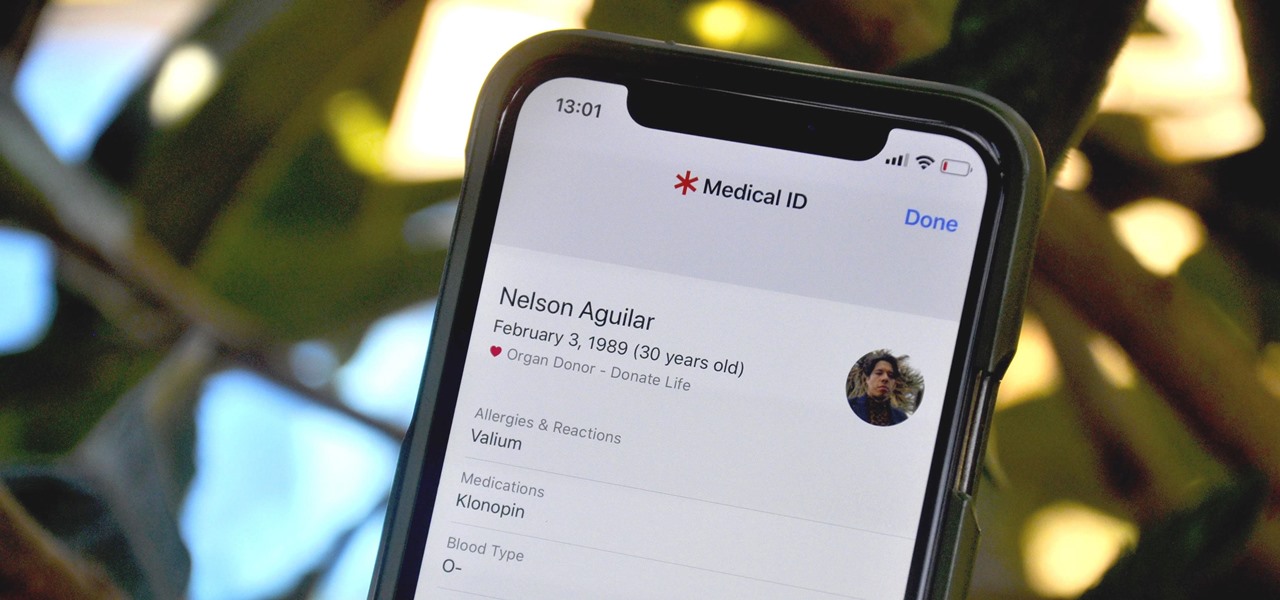
You can't predict the future, but you can prepare for it. On the off chance that you get hurt in a car accident, take a nasty tumble, fall down a cliff, have a seizure, or get struck by lightning, it's always good to carry up-to-date information about your health in case you can't speak for yourself. A physical medical ID wallet card or bracelet can provide the information, but so can your iPhone.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

While we just called the Apple Watch Series 5 the "best lifestyle assistant and fitness wearable you can get," it doesn't mean that it's the model you should get. Whether you're shopping for yourself or someone else and are on a tight budget, the Series 4 offers the majority of features that the Series 5 does at up to $300 less than the newer comparable models.

I've just recently hopped on the AirPods bandwagon, and I can't see myself ever going back to the wired EarPods that Apple includes with every iPhone. The only issue is that I paid full price, but you don't have to with 2019's Black Friday deals, some of which are happening right now.

The week in AR business news started out with a bang with two bombshell reports that cast a shadow on the AR industry as a whole.

After months of waiting, the iPhone 11 is here. At an event in Cupertino, Apple unveiled the iPhone 11, 11 Pro and 11 Pro max. You probably have a lot of questions after reviewing the specs sheet, including wanting to know more about the IP68 rating that all three phones have. We're here to clarify.

As excitement looms for Apple's annual parade of pomp and circumstance for its latest lineup of iPhones, some hidden hints in an internal build of iOS 13 has Apple enthusiasts salivating for what Cupertino is testing in the AR wearables realm.

If you've ever used the Find My iPhone and Find My Friends apps in iOS 12 and below, you may be surprised to hear that those apps have joined forces in iOS 13. Now, instead of two separate apps, they're combined into one convenient package. But what does that mean for you and your privacy and security?

Being an Android user and having friends who are in the Apple ecosystem does not need to be a pain. You can easily send high-quality videos to iPhone users, so don't feel handicapped without access to iMessage. Sending high-resolution videos to iOS users is easy with this fast video-sharing method.

Search engines index websites on the web so you can find them more efficiently, and the same is true for internet-connected devices. Shodan indexes devices like webcams, printers, and even industrial controls into one easy-to-search database, giving hackers access to vulnerable devices online across the globe. And you can search its database via its website or command-line library.

Unless you've been hiding under a (moon) rock for the past month, you already know that Saturday, July 20 is the 50th anniversary of NASA's Apollo 11 lunar landing.

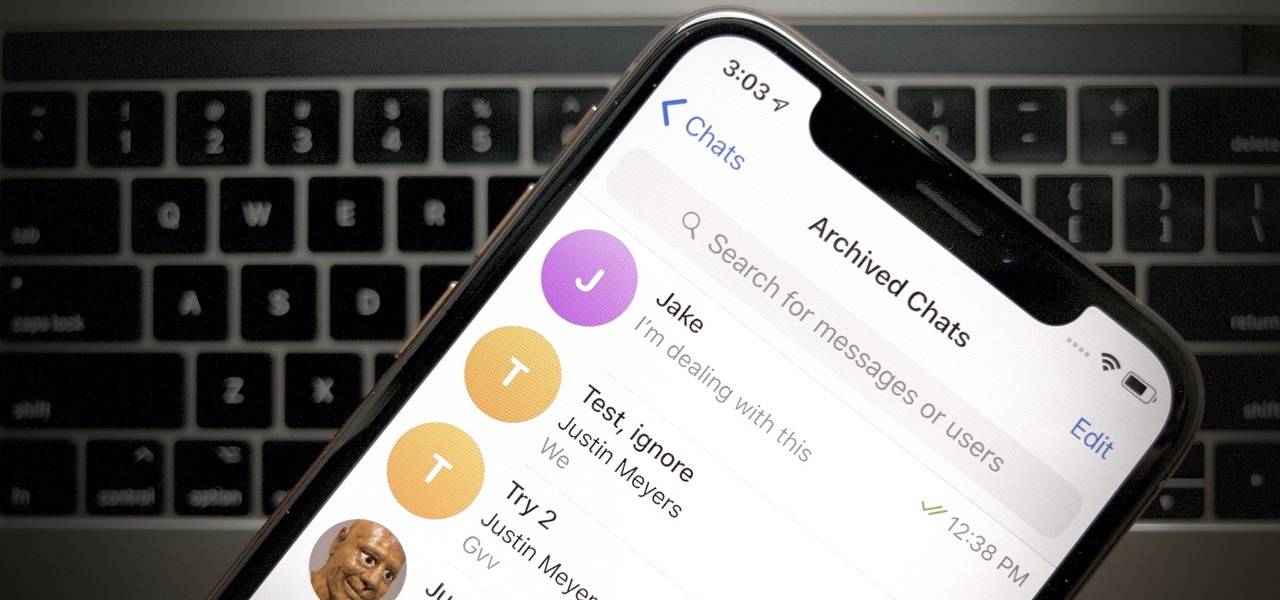
In Telegram — as with all instant-messaging apps — threads and conversations can pile up quickly. But you don't need to stare at all of your open chats on the main screen of the Android and iOS app. Instead, you can archive any conversation you like, keeping your main chats view relevant to your day-to-day communications without needing to delete any for good.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.

For all its faults, you can't say that Facebook hasn't been instrumental in connecting friends and family together, no matter where in the world everyone is. That's why one of its upcoming features — watching videos together with Facebook friends directly in Messenger — is so novel. It's just another example of the internet bridging gaps that couldn't be bridged just a short while ago.

For the first time, you can officially use a computer mouse with your iPhone, thanks to Apple's new Accessibility settings in iOS 13. It works for all types of Bluetooth mice, so if you have one, it'll already work. Plus, those with wireless receivers and even wired mice are supported by using a USB to Lightning adapter.

The next libSSH or OpenSSH exploit may be just around the corner. Keep your SSH service out of Shodan's database before hackers find new ways to bypass the password protecting the server.

Every model iPhone since the 6s has boasted a 12-megapixel rear camera. You can take some pretty spectacular, professional-looking photos with it, especially on devices that have more than one rear lens. But the file size of each photo can become a problem when sending as an iMessage, which can eat up data.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

In just a few weeks, on May 29, the annual AWE (Augmented World Expo) conference will take place once again in Silicon Valley (Santa Clara, California, to be exact).

Finland-based Rovio, one of the pioneers of mobile gaming, is now ready to break new ground in augmented reality with its Angry Birds franchise.

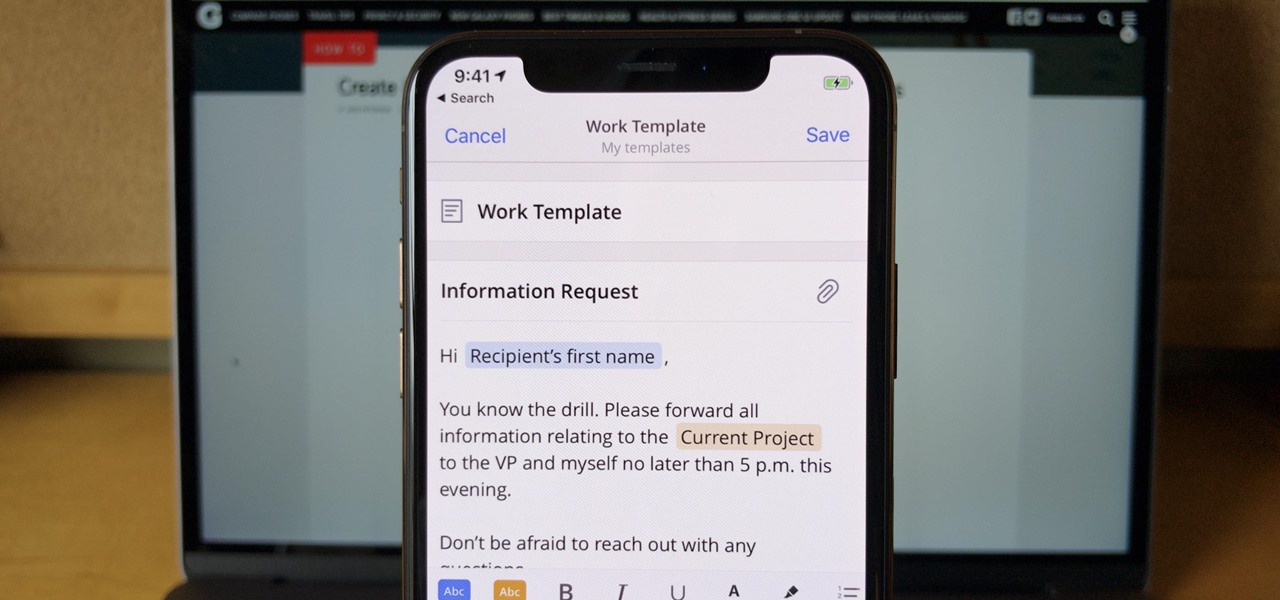
If you find yourself emailing the same email over and over again with just a few changes such as new addressees, or if you're constantly replying to messages with the same response, typing it out every time is, well, a waste of time. Spark, a third-party email client for mobile devices, takes all the work out of this — no matter which email account you need it for.

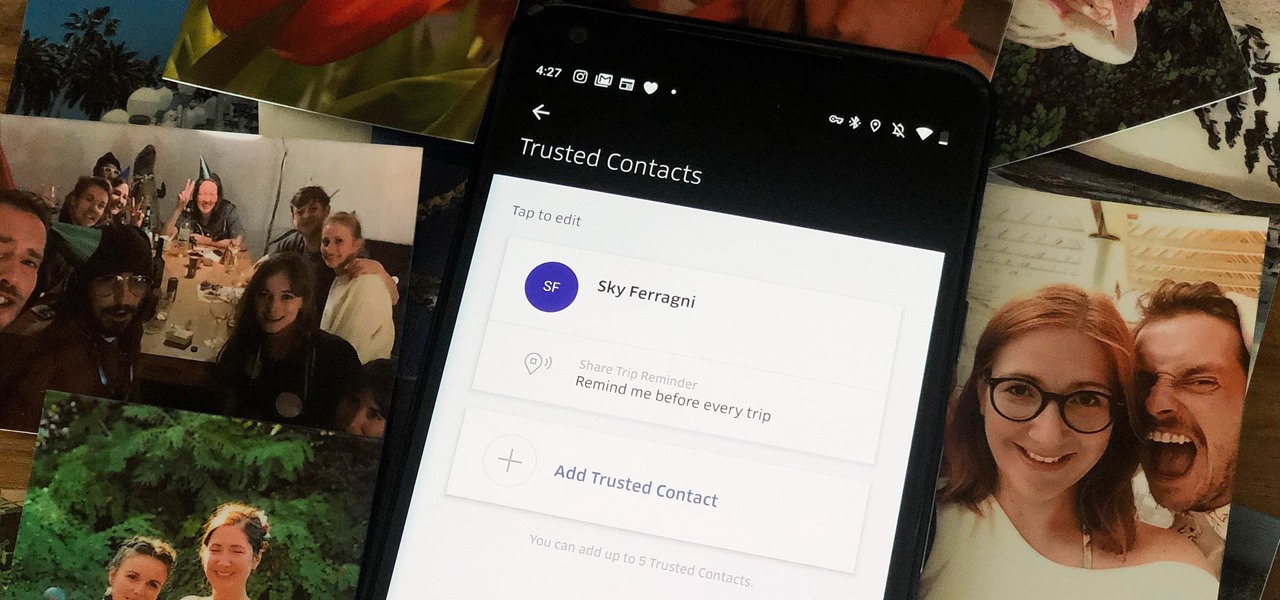
When you're riding in an Uber, on your way to meet family or friends, they may want to know where you are exactly to see how long until your arrival. On the other side of the coin, there may be times when you want to tell family or friends where you and your Uber car are without them asking, like when you're in a dangerous situation. Uber makes this easy, as long as you set it up first.

They say home is where the heart is. So, the opportunity to view the inner sanctum of Magic Leap is like gaining access to what makes the company tick, just as the fruits of its labor make it into select AT&T stores.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

We recently set out to find the best phones for people whose primary usage revolves around social media apps like Facebook and Instagram. Samsung, Apple, and Google were the three brands that made our top five, and while the latter only had one finalist, the two bigger OEMs had a pair of phones each. What struck us, however, was that Samsung's phones edged out Apple's not once, but twice.

Despite being at the helms of the RCS push, Google Fi has yet to support the new messaging protocol. It would've made too much sense if the Google-created MVNO was one of the first to support the feature Google's been pushing on other OEMs and carriers for years, but alas, they haven't. Well, better late than never — Google has finally announced support for RCS Universal Profile on Fi.

In late-2017, Instagram rolled out a feature that automatically saves your ephemeral Stories to a private archive. Before that, Stories disappeared into the ether after 24 hours, but not everyone was comfortable losing these precious photos and videos. If you post to Instagram Stories quite often, you can now easily access your history from your account — and you might not even know it.

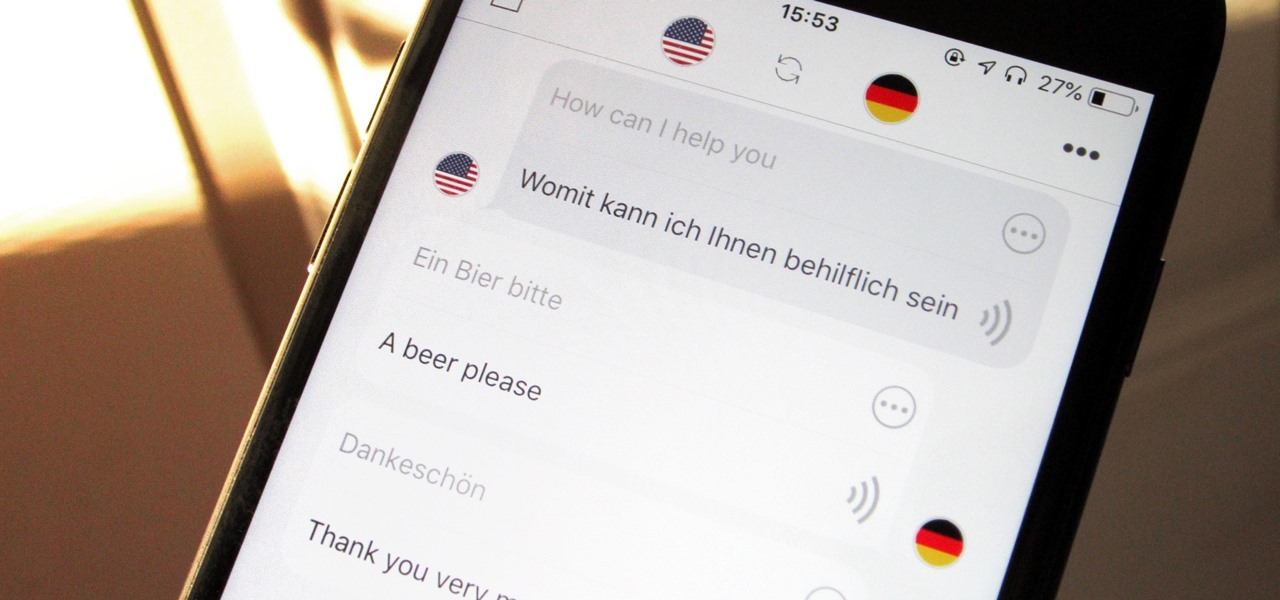
Nothing beats a human translator, but Google Translate and other software-based solutions have developed into decent alternatives for help with basic translations. Need an English word translated into German? No problem — but what if you need to have a conversation with someone who doesn't speak your language? Is Google Translate capable of doing that? The answer is not really.