Friendship bracelets are the most personal testaments to a good friend that you can make. Celebrate your friendship while creating a work of art that will last a very long time by weaving together this friendship bracelet with an "S" spiral.

In this tutorial, we learn how to draw a graffiti alphabet. If you aren't familiar with drawing graffiti, this is a very personal type of drawing that you can do anyway you would like. Make the letters close together, but give them wide arches so they look bold. When you write out the alphabet, you will color the space between them black, and then shade the inside of them. It may be hard to see exactly what the letters are, but that is the fun with graffiti. Make it completely unique to you a...

The best thing about going Gaga for Halloween is the variety of possibilities. Lady Gaga's wardrobe is vast and colorful: the Meat Dress, her trippy Anime Eyes, the scantily clad Caution Tape look, the Soda Can Hair Rollers, the light up Gothic Crown, the Cigarette Smoking Glasses, and, of course, the classic Hair Bow from Poker Face. It's my personal favorite, and the following illustration is easy to follow. If you don't feel like messing with your own hair and have a wig around the house, ...
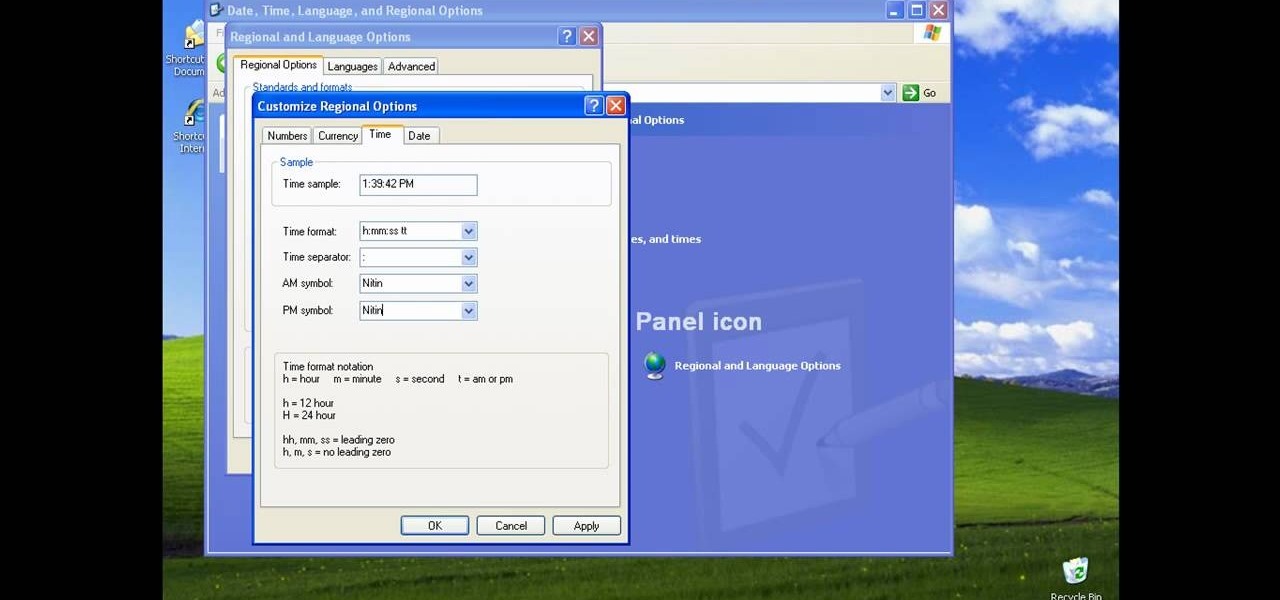
There could be multiple reasons why you would want to input a name in the Windows taskbar on your PC, like when dealing with a network of computers, to help identify workstations, or simply for a customized personal feel. With this tutorial, you'll see how easy it is to put your user name or computer name (or any other name) down in the taskbar, right besides the time in the bottom right.
Worried about a hard drive failure? Or a virus that destroys your operating system? Well, don't worry… Windows 7 lets you backup and restore your Windows 7 operating system and all of the files and folders you choose.

You aren't just born with broad Stallone shoulders and arms, gentlemen. Of course we know you wish you never had to work to get those tight, chiseled arms and shoulders, but even the best of the best - that's right, including Stallone - have to work what their mama gave them to keep in shape.

Isometric exercises are strength training exercises that don't let the joint angle and muscle length contract during the movement. This means that the exercise is done in a static position with the muscular intensity coming from the weights and your own body.

Blind is a Limbo-like platformer on A10 Games where the player must platform through 2D environment that is largely concealed to them. This video will walk you through all of the game's 21 levels.

In this Outdoor Recreation video tutorial you will learn how to mount a fish finder on your kayak. There are many ways of doing this. All the methods work. It’s just a matter of personal choice where you want to mount it. Some boats are designed for a through hole transducer and have a space for it to mount it in a hole. Take a piece of foam, trace out the transducer and cut out the foam. Now open the front hatch of the boat and glue down the foam on the flat surface of the boat. Once that ...

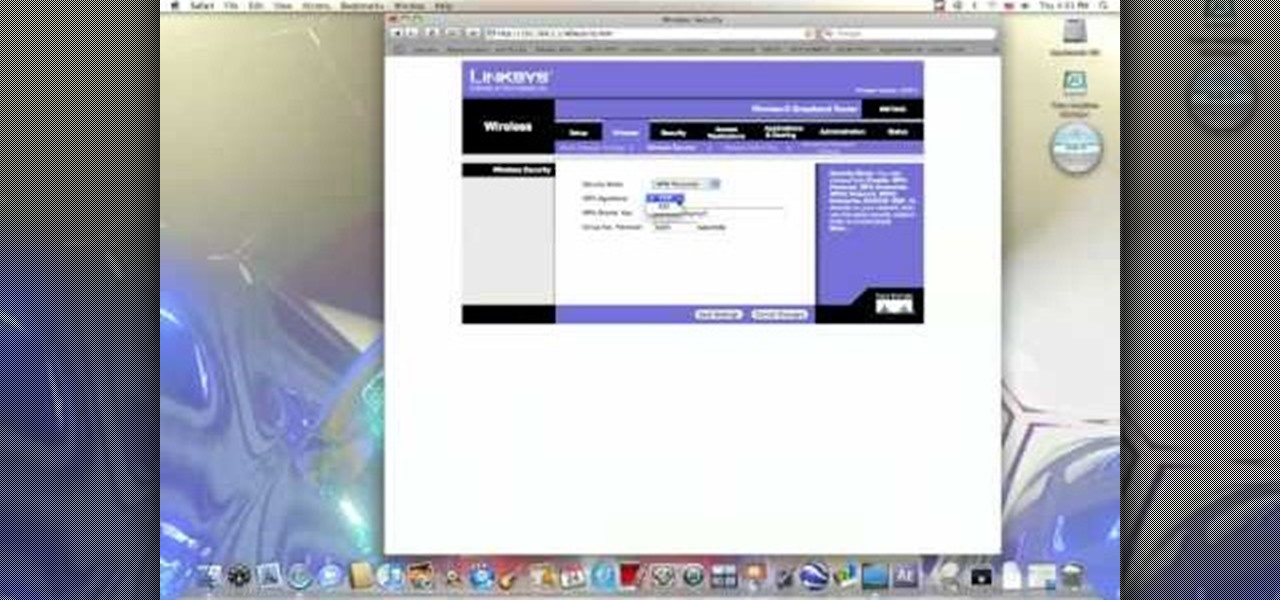
In this video from benjamoon we learn how to secure a linksys wifi network from a Mac. First type in your IP address in your browser bar which is 192.168.1.1 then press enter. If it asks for a password it is admin. Click on Wireless and here you can edit your name and who can access your wifi network. Under wireless security, go to WPA personal from the drop down menu. When you make your password, make it very challenging. He recommends just banging your hand against the keyboard, as long as ...

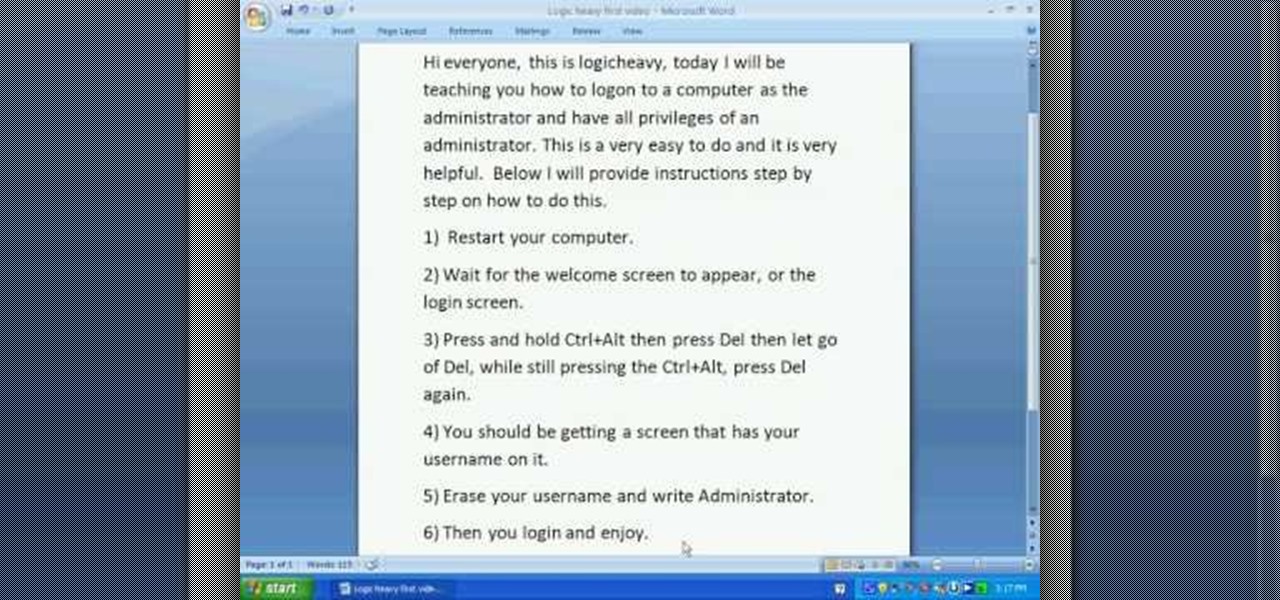
The video starts with a guy talking while we see a computer screen with instructions on how to log in as an administrator of your Windows XP Personal Computer.

A digital caliper is a good way to keep track of your body fat. With a caliper, you can measure body fat and keep track of your new diet or workout routine. This way, you will know the difference between muscle and fat, and not have to rely as much on the scale. A digital caliper is great in the sense that it is able to take an accurate reading in seconds, give you a clear output and beep when it is ready. A digital caliper can also be programmed with your personal gender and other informatio...

Gift baskets are a great way to celebrate the holidays and special occasions. They also are a great way for you to cheer a friend up and cure their blues. In this quick guide you will learn how to put together a kind and caring gift basket for someone recovering from illness.

In this video, you will learn how to grind and mix feed on a farm. Mixing feed allows farmers to buy feed ingredients in bulk, and prepare their own specialized blends, reducing costs. The farmers shown in this video use a Gel mixer, and they describe how theirs works, including a description and explanation of its parts and what they do. You will also learn about their own personal experiences with mixing feed on their farm with this mixer, as well as some tips based on this experience. The ...

Learn how to master tunes using Reason 4.0 software to get a more effective sound. The first step is to make sure the outputs are not in the red. If they are in the red, that means the sound is not that good, and you don't want to work with a bad mix. The next step is to add a McClass mastering suite to your mixer. As per the guide in this video, everything should be below 100 to 175 Hz mono. However, this is a personal preference and you should do what you feel is best for the sound of the m...

This video you shows how to send your pictures, videos, music and ring tones from your cell phone to your computer. The tutor asks you to find the pictures that you want to send to the computer, and then mail those pictures to your e-mail. We can then later open our computer and through the email download all the pictures and videos that we sent to ourselves. So in this way we can send all our personal stuff from the cell phone to computer without ever connecting the cell phone to the compute...

Emo and scene hair, distinct for its haphazard appearing fringes and bangs over the face, is probably the least daunting hairstyle for one to style for themselves, to add a certain personal, and a bit more unconventional touch. In this video, our host explains that, mainly, it's about just doing what you want, and not caring too terribly much, but, if you like the way he's done it, he explains that what he did was cut the sides to create more points coming out across the cheek. Then, for the ...

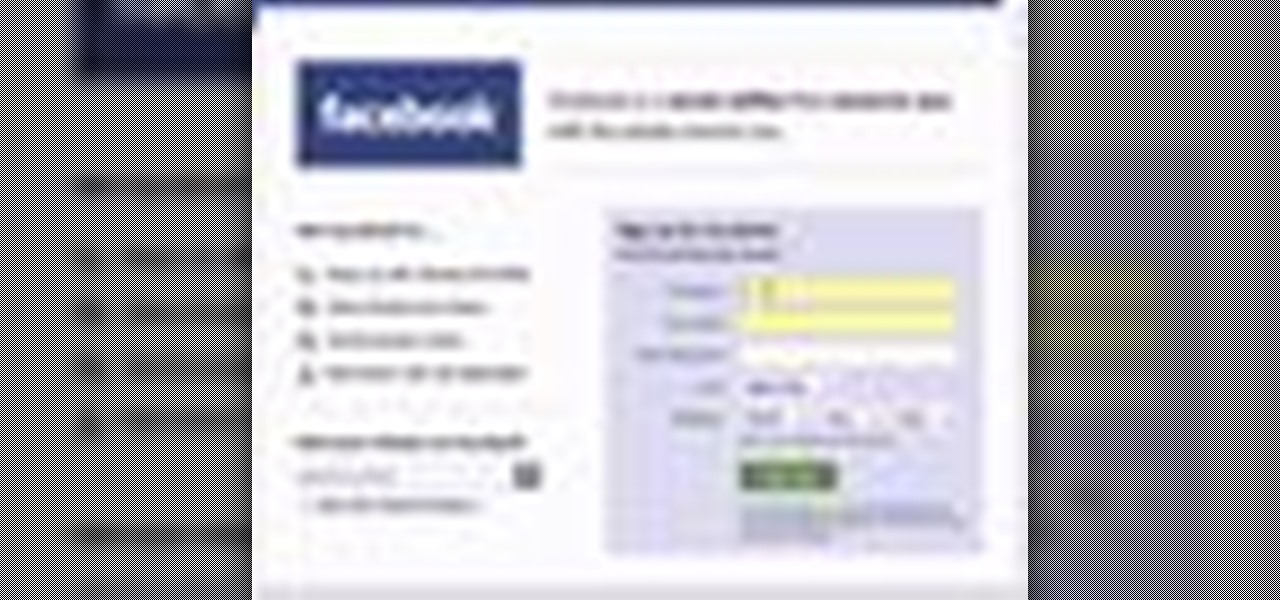
Start out by going to www.Facebook.com. From this page you will be able to create your own personal Facebook profile. Fill in your name, email, password, sex, and date of birth. Click 'Sign up' after you have filled in all of this information correctly.

Today, learn the basics of lock bumping. Lock bumping is a lock picking technique for opening a pin tumbler lock using a specially-crafted bump key. One bump key will work for all locks of the same type.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

Sometimes we don't have the time or money to go to a therapist to have them help us manage our stress. Using a shower to reduce stress is easy with these tips. Get advice on reducing and managing stress in the shower in this stress management how-to video.

Abdominal exercises such as kneeling ab crunches work out the abdominal muscles. Learn abdominal exercises in this free ab workout video series featuring a personal trainer.

What management style is best for you? Each situation can call on a different style. Learn about each style and when to use them from a communications and public speaking expert in the free instructional video series.

Check out this quick video tutorial on how to install Opera Mini 4 on the T-Mobile Shadow cell phone.

Carmen Lynne shows us how use personal numbers in numerology in this series of videos. Part 1 of 16 - How to Understand numerology personal numbers.

With stay-at-home orders for most of us in the US because of the new coronavirus, many of you are likely struggling to be productive and efficient when working from home. Unless you've worked from home before, it can be challenging to separate work from personal life throughout the "workday." But your iPhone can help make the transition easier and more successful.

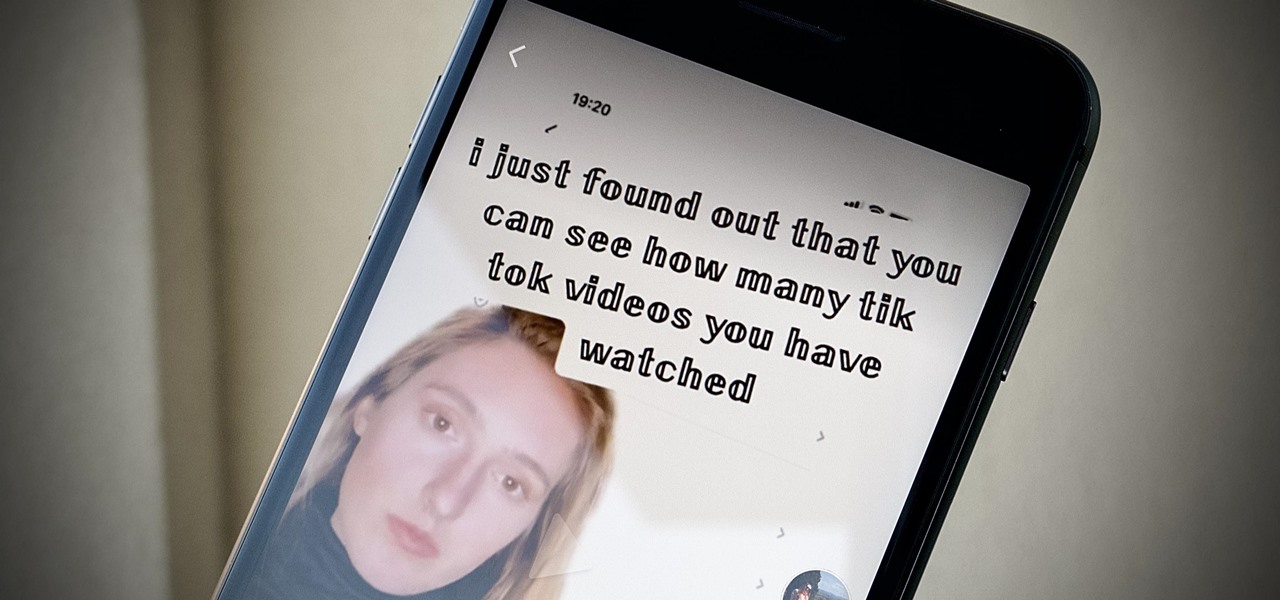
If you're as addicted to TikTok as much as I am, you probably heard about the app's alleged, hidden views counter, which can show you how many TikToks you've watched on your account. Most people who look at their counters are horrified to see that they've watched hundreds of millions of TikToks so far. Can that be right?

Over the years, TV has become more of a solo activity than ever before. It is exponentially more difficult to discuss the latest shows with friends since platforms like Netflix just release all episodes at once. Luckily, Snapchat makes it easy to keep your pals in the loop on what you're watching, so they can pick up the remote and do the same.

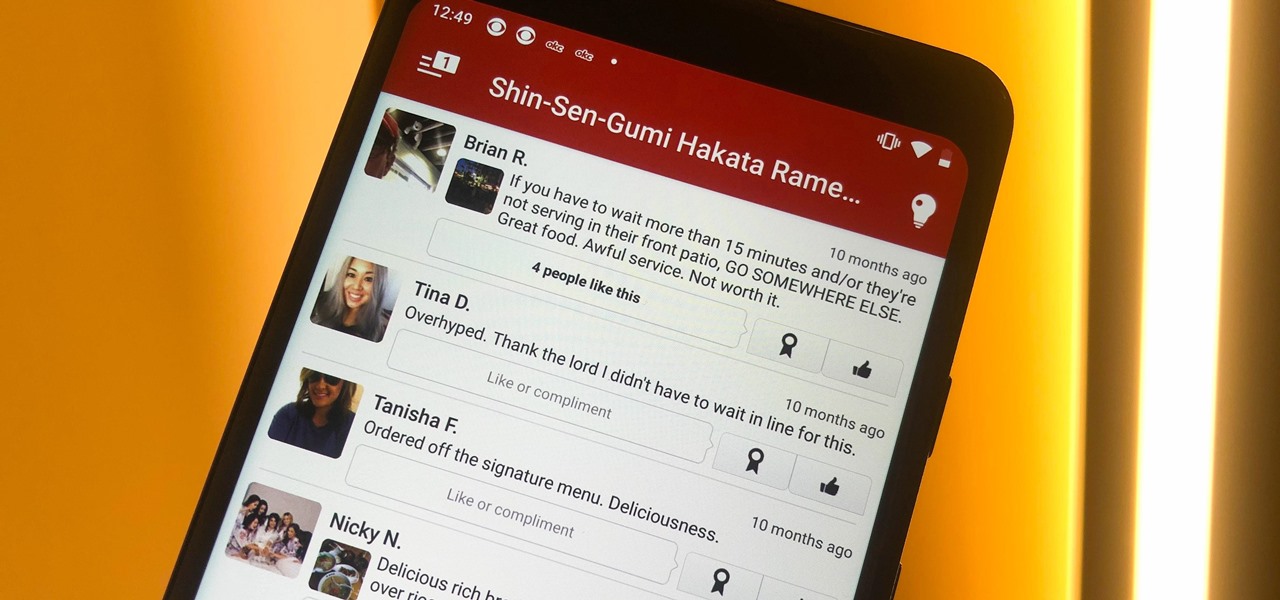
Yelp reviews are great for getting a feel for how a business operates, but they can't always be trusted, and they don't always get to the point fast enough. That's where "Tips" come in, and you can view and make them whether you're on an iPhone or Android phone.

Stumbling upon a specifically tailored advertisement on your iPhone can be a bit disconcerting. But that's what happens when you let advertisers track your data. Some of you may appreciate more relevant ads in apps, but the rest of you might consider it a straight-up privacy invasion.

Give an 18-month-old a shoe, check back 10 minutes later, and it's a very big maybe he will have it on his foot. But give him your smartphone, and in a mere five minutes, he can take 100 pictures of the carpet, send weird messages, and delete essential apps. Imagine what your child could do if they were able to harness this technical aptitude and put it to good use — and they can, with learning apps.

Thanks to recent reports, we now know third-party apps have a lot more access to our Gmail than we may have initially thought. In fact, these third-party apps have the ability to read our emails, not because these companies are necessarily shady, but because we agreed to it. Luckily, there's a way to view which apps have this access, as well as a way to boot those apps from your Gmail entirely.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

Ben & Jerry's addicts rejoice: Microsoft just won a patent for AR glasses that could help to combat overeating. Physical restraint is still needed to keep me away from that ice-creamy goodness, but a little virtual voice saying 'DON'T DO IT' could definitely help when the cravings come.

Responding to the emergence of Zika in the US, researchers investigated what type of repellent works best to reduce your odds of a mosquito bite from Aedes aegypti, the mosquito species that spreads the Zika virus.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

Welcome back, my novice hackers! In this series, we have been exploring how a forensic investigator can find evidence of illegal or illicit activity. Among other things, we have examined the registry and prefetch files for artifacts and have done some rudimentary forensic analysis. For those of you who are seeking career as a forensic investigator or security engineer, this can be invaluable training. For hackers, it might be life-saving.

When it comes to squeezing as much battery life as possible out of our smartphones, most people aim for software solutions, or ones that can otherwise be easily managed right from the touchscreen.

The release of the Nexus 5 marked the debut of the Google Now Launcher. Even with an integrated Google Now page on your home screen, the most talked-about feature was actually the always-listening functionality.

Merely fidgeting and shivering can burn calories, but now you can add trembling in fear to the list too. Just pop in a good horror movie and turn down the lights to burn off up to 200 calories. What would you rather do? Walk for over 30 minutes or watch a 90-minute scarefest?