In this web design tutorial we will show you how to protect yourself from losing your work just in case the program malfunctions, computer crashes or you accidentally forget to save document and so on. I highly recommend you utilize this Web Design Tutorial especially if you are working on large websites for clients.

In an increasingly mobile and globalized world, it’s not uncommon to lose touch with people we were once close with. Juggling between job demands, family responsibilities and our own personal needs, it’s often hard to put the time to keep all of our relationships going. Nevertheless, every now and then we get to reminiscing and feel the time has come for a reunion with people from the past.

Unless you're a business executive or movie star, most of us aren't afforded the luxury of having a personal assistant. Wouldn't it be nice to wake up in the morning and just have everything taken care of?

Admit it—at some point or another, you've wished that you had your own personal hovercraft. Don't worry, we've all been there. Well, a company called Aerofex wants to make a hovercraft that's way more than your standard leaf-blower-powered one, taking a queue from the swoop and speeder bikes from the Star Wars franchise, building their own sort of repulsorlift. This hover bike may not be quite as fast as the ones from Star Wars, but if the company has its way, it could be on sale by the end o...

If you use apps on your smartphone, chances are you have no idea what those apps are doing with your information. Just this year, there have been several scandals involving apps transmitting user data, like Path uploading users' entire address books onto its servers, HTC's Security Flaw, and Brewster exposing users' personal information (even Ashton Kutcher's). A new service called Mobilescope wants to make sure you always know where—and to whom—your data is going. Lots of apps copy your cont...

Get your numbering straight with Adobe's InDesign and this helpful tutorial, showing you what you need to know. It's essential when creating a project for yourself or a client, to get your numbering right the first time. There is no second chance. So, check out the steps and see how to turn this sometimes tricky task into a much easier one. InDesign offers a lot of options, and if you're going to master all it's tricks, watch this how-to to learn one of the most simple and essential tricks.

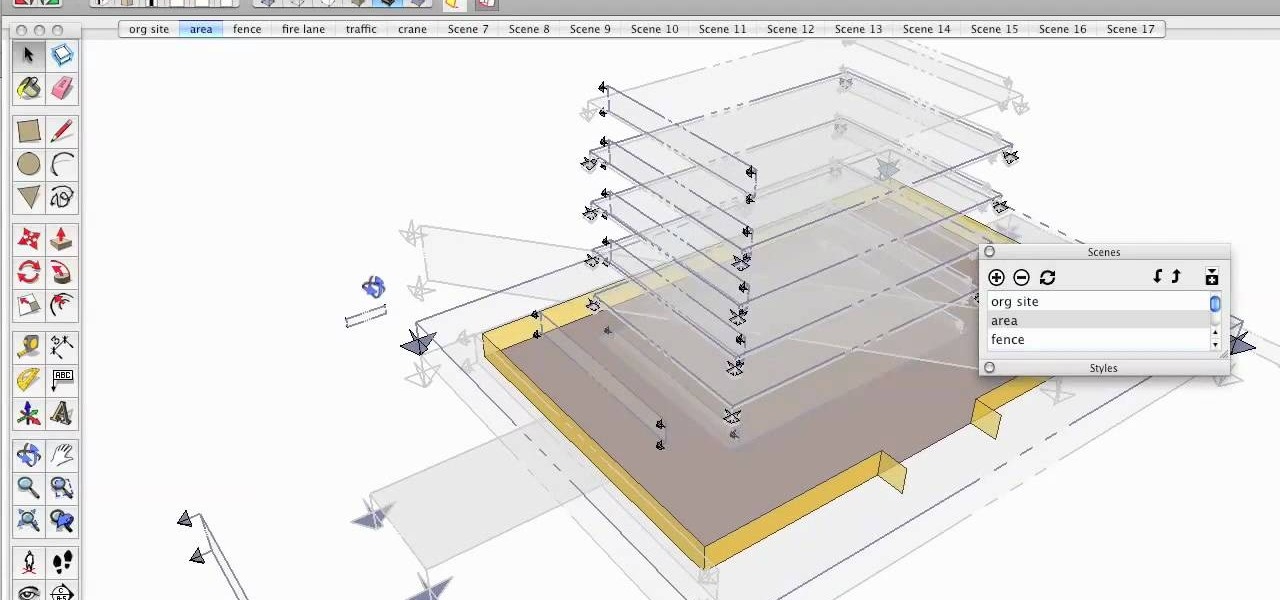
As you already know, Sketchup is a very cool program which allows you to design a myriad of things. But, did you know you can then animate those images? You can, and this tutorial will walk you through the steps to show you how. This is a very valuable thing to know if you're presenting something to a class, or client and want to show them the developmental stages of the project. So check out this video, get designing and put those pictures into motion!

If you think about it, your face is just another canvas, with makeup being the paint. You add highlights here to bring parts you want to emphasize forward, bronzer there to create fake shadows, and draw on patches of color (lips) or lines (eyes) to make things either pop or recess.

If you're a graphic designer, you've probably dealt with clients who sent you the wrong files, like JPG and BMP "source" files. You need to the EPS vector files, but they don't know what that is, and they don't care. They want that image or logo they sent you blown up to poster size for a billboard or something.

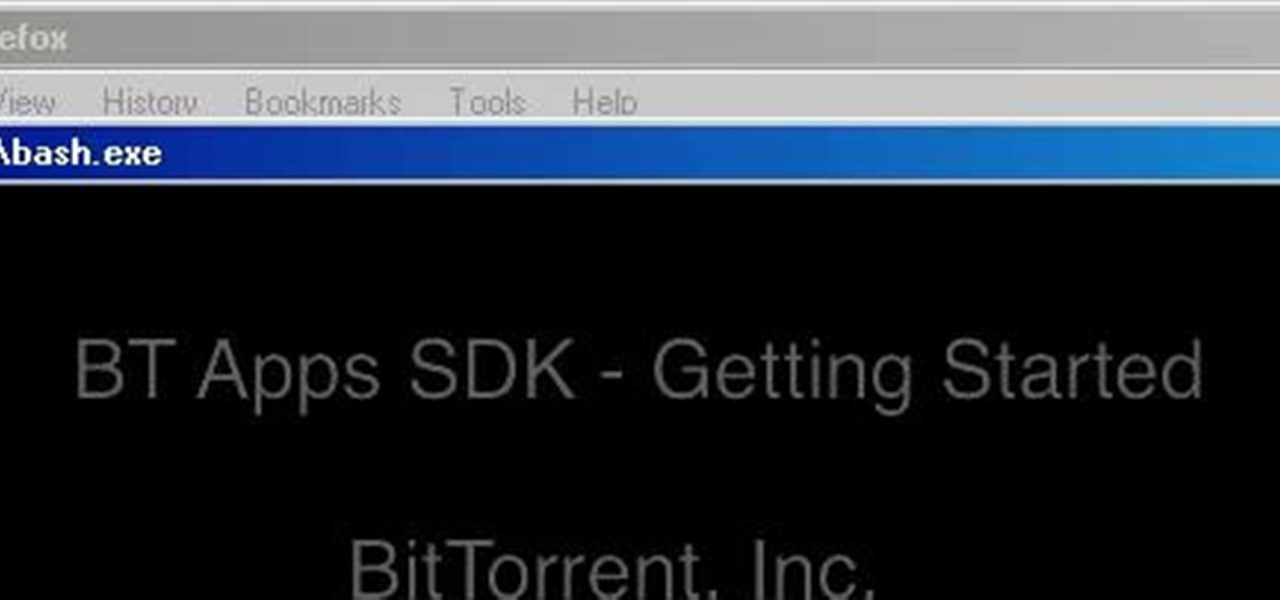
Today, BitTorrent Inc. released the SDK for uTorrent Apps, which will allow software developers from around the world to create Apps for uTorrent, the popular bittorrent client. This video will show you how to download the SDK, install it on your computer, make an app, view that app in a browser, and then package the app and view it within uTorrent without compromising uTorrent's famous lightness. This is a big day for bittorrent fans around the world; download the SDK and start making uTorre...

There are a couple of limitations that Microsoft put in to Windows 7 upgrades that can prevent users from upgrading and ultimately force them to do a clean install. First limitation is that they won't let you to upgrade Windows 7 if you run Windows 7 release candidate that was released earlier this year, which they won't let you to upgrade to a download Windows edition. If you are running Windows vista ultimate you cannot upgrade windows 7 professional. We have to buy an ultimate edition then...
When stories are told about people in need, the ones with happy endings include the details of someone that produced an action that caused the people in need to be better off than before. Do we have to wait for the identification of a need? Could we on purpose just plan to present products and services that cause our customers and client to see an improvement in their circumstances just because of the business interchange with an owner manager of purpose? The fair exchange of products or serv...

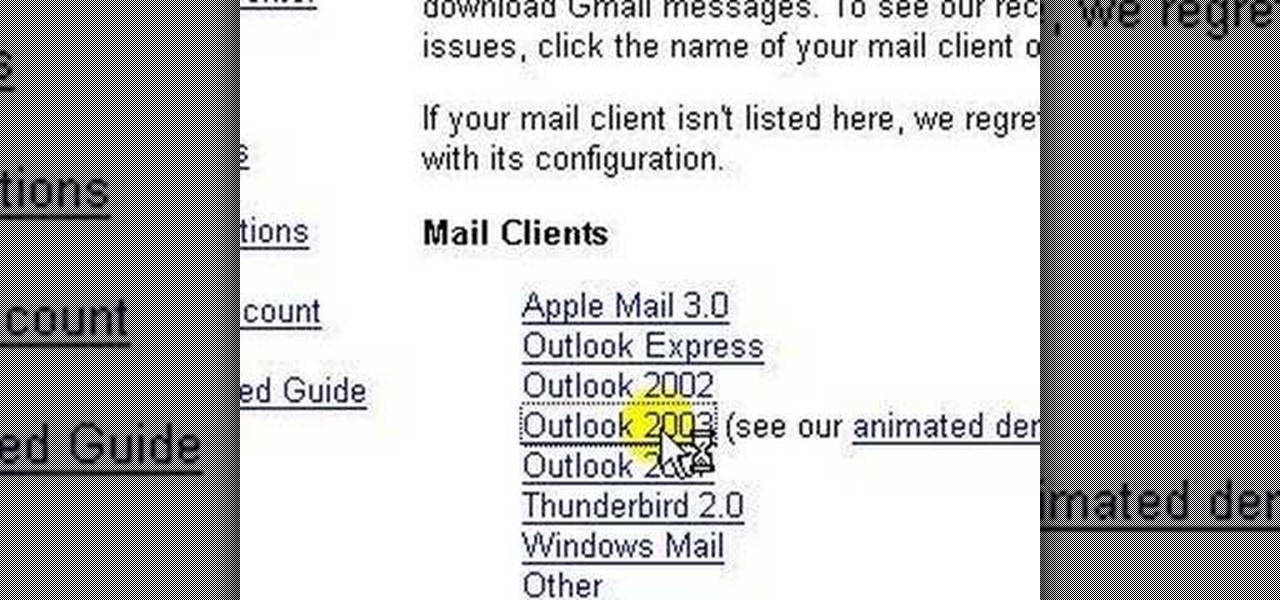
lakercoolman shows us how to set up our gmail account with this quick tutorial. Basically outlook express is a program that helps us to organize our email with added features such as contacts, to do lists and calender entries. Its an offline email client that allows us to work offline and also lets us set up exchange servers aswell. Ohter email servers such as hotmail and yahoo charge for thios service but the advantage of gmail is that IMAP or POP access is free. in ofer to set up, navigate ...

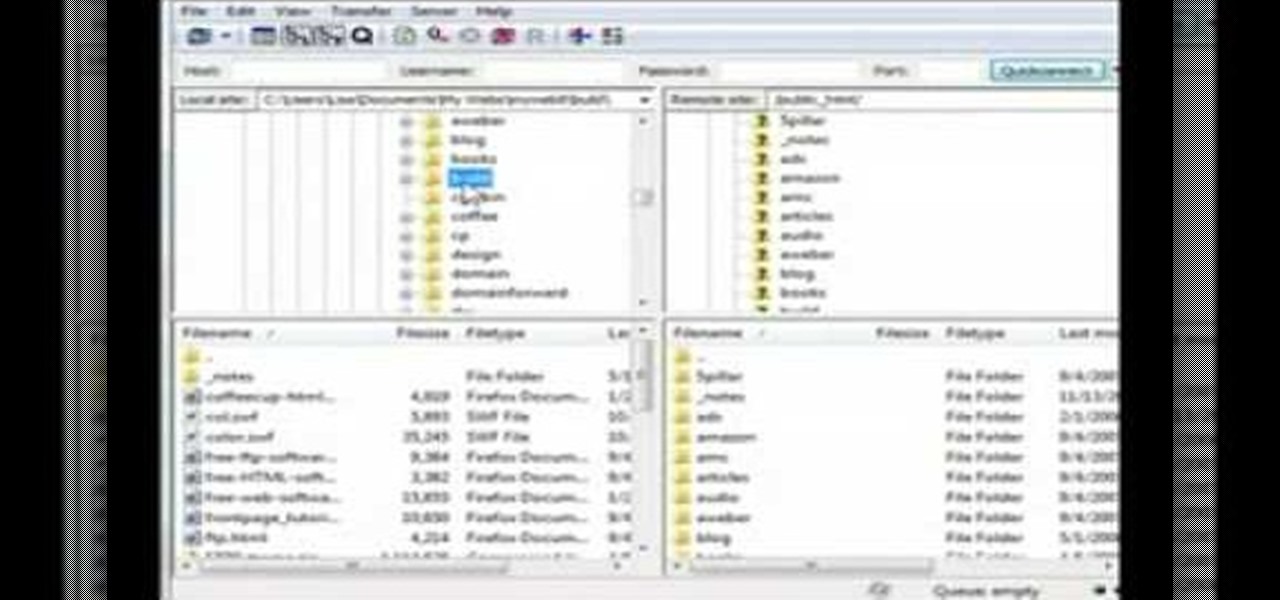
This video describes that how to use the file transfer protocol prgram. First we have to download filezilla to our computer. Go to google and download it first into the computer. There is a username and password to use the FTP. Open the filezilla and come to Host. There we have to type ourdomain.com or ftp.yourdomain.com. Next you have to enter the username and password. Next you have click quickconnect there. Then you will connect to your webserver. In filezilla there are four quadrants ther...

This video tutorial shows how to open a port for torrent downloading on your computer. Click Start menu, type cmd command in Search area. In cmd window type ipconfig and press Enter. Remember or write down your IP adress. Type exit and press Enter to close cmd window.

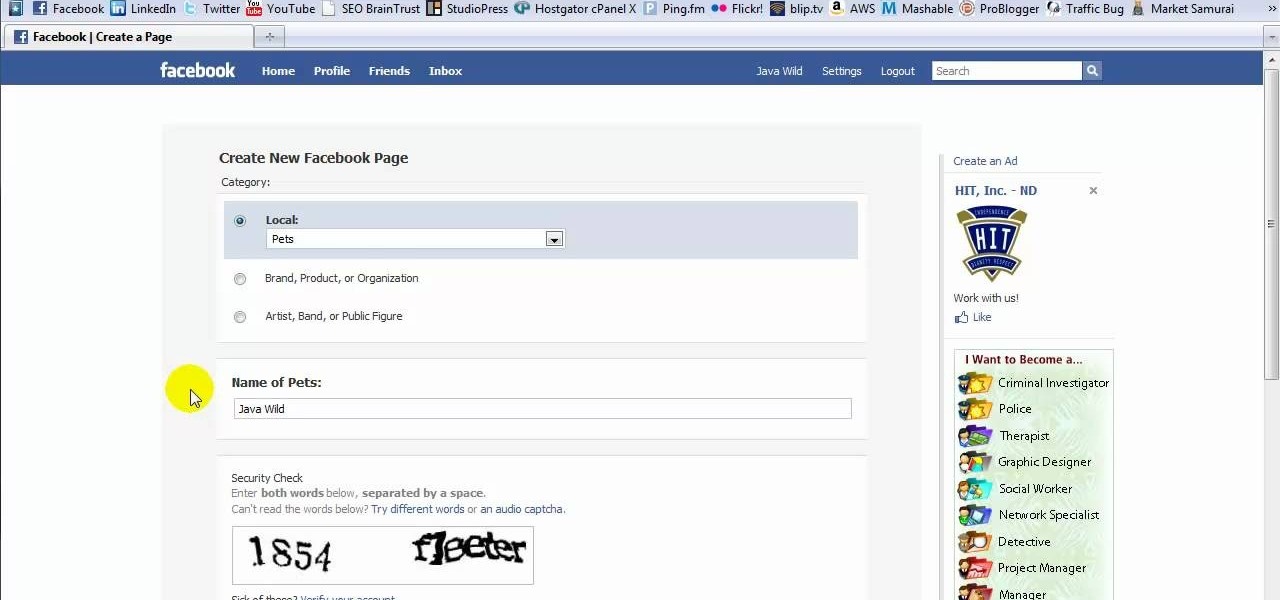
This tutorial is in response to mail to Facebook. Scott Wilde leads you through the process. You can start by creating a brand new profile page. In this case, Mr. Wilde created a profile page for his dog Java Wilde so he could have a fresh new page without having to alter his initial profile page. Fan pages are different than your base profile. Your base profile is not indexed, it is not public, it is private and limited to 5000 friends. A fan page is unlimited up to millions of fans and it c...

You're a busy, on-the-go professional, so you deserve an email client that keeps up with you. "Mail" on iPhone wasn't always the best option, but thanks to iOS 13, it feels like a completely different app. That said, there are plenty of alternatives that offer a different experience. Better yet, these apps are free. You won't need to spend a dime to try them out for yourself.

In a way, Twitter is the town square of our era, where people can share and discuss ideas on a wide variety of topics. While the tech giant has its own app for Android, it's pretty bare-bones when it comes to features. This has paved the way for third-party clients that are rich with customization options.

After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

If you've read our list of the best email clients for iOS, you'll know Apple's Mail app doesn't cut it when it comes to third-party integration. If you want to use some of your favorite apps directly in your mail client's calendar, go with Outlook.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

Hello, fellow hackers. I'm sure we've all seen it somewhere: the undying question of "How do I hack the game so-and-so?" And the answer usually is, "Come back when you actually know how to hack!" But how does one even go about "hacking" a game? What could that even mean?

Remember portable MP3 players like the classic iPod? Seems like forever ago that they were all the rage, and I don't think I've seen a real one in the wild for a good 5 years now. These devices died out so quickly as a direct result of the onset of smartphones, which allow us to do everything that an MP3 player could do and then some.

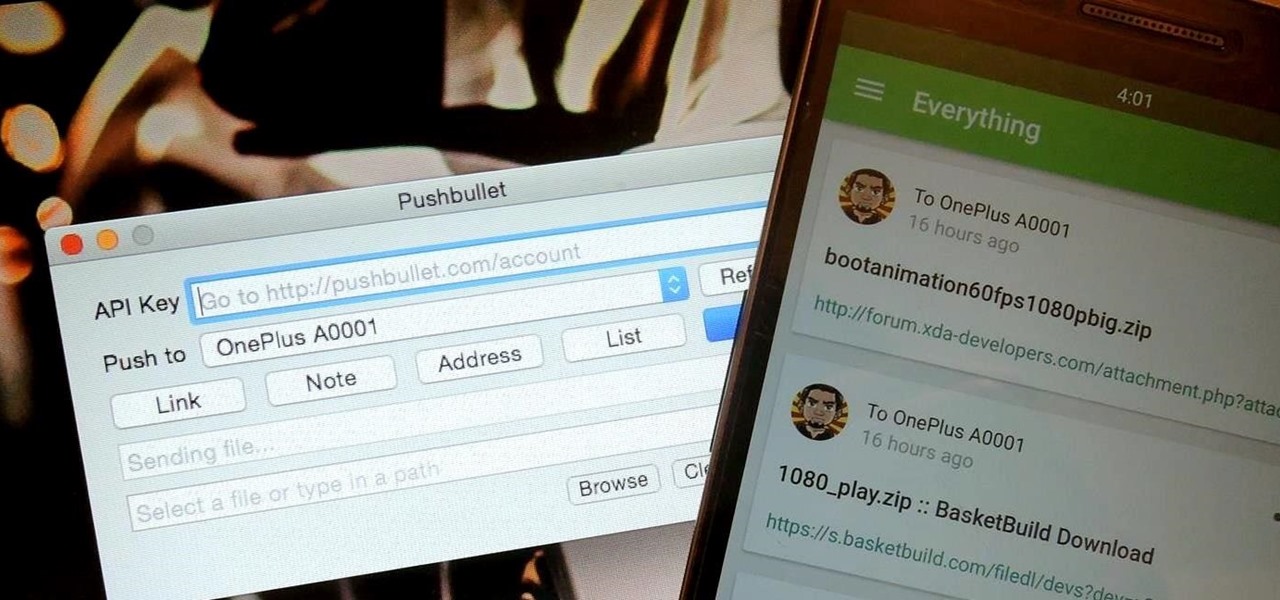
Before Continuity and Handoff were even announced, Pushbullet was already allowing users to quickly send notes, links, and photos between their devices with a few clicks.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

Welcome back, my budding hackers! We've spent a lot of time learning to compromise Windows systems, and we've successfully compromised them with Metasploit, cracked their passwords, and hacked their Wi-Fi. However, very little time was spent developing ways to extract the information from the system once inside.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.
In any project management career, there is no such thing as a person who knows everything for each project. Many times, those who got too much confident with their jobs fail because they were not able to make things clear before and during the project implementation.
I've noticed that a few people using the crypto-currency, Bitcoin are having issues importing private keys to their Bitcoin wallet. This is easy to do and doesn't require anything other than your Bitcoin client/daemon (as of ver0.6.0 ) and the command line.

What management style is best for you? Each situation can call on a different style. Learn about each style and when to use them from a communications and public speaking expert in the free instructional video series.

Carmen Lynne shows us how use personal numbers in numerology in this series of videos. Part 1 of 16 - How to Understand numerology personal numbers.

Friendship bracelets are the most personal testaments to a good friend that you can make. Celebrate your friendship while creating a work of art that will last a very long time by weaving together this friendship bracelet with an "S" spiral.

In this tutorial, we learn how to draw a graffiti alphabet. If you aren't familiar with drawing graffiti, this is a very personal type of drawing that you can do anyway you would like. Make the letters close together, but give them wide arches so they look bold. When you write out the alphabet, you will color the space between them black, and then shade the inside of them. It may be hard to see exactly what the letters are, but that is the fun with graffiti. Make it completely unique to you a...

The best thing about going Gaga for Halloween is the variety of possibilities. Lady Gaga's wardrobe is vast and colorful: the Meat Dress, her trippy Anime Eyes, the scantily clad Caution Tape look, the Soda Can Hair Rollers, the light up Gothic Crown, the Cigarette Smoking Glasses, and, of course, the classic Hair Bow from Poker Face. It's my personal favorite, and the following illustration is easy to follow. If you don't feel like messing with your own hair and have a wig around the house, ...

There could be multiple reasons why you would want to input a name in the Windows taskbar on your PC, like when dealing with a network of computers, to help identify workstations, or simply for a customized personal feel. With this tutorial, you'll see how easy it is to put your user name or computer name (or any other name) down in the taskbar, right besides the time in the bottom right.

Worried about a hard drive failure? Or a virus that destroys your operating system? Well, don't worry… Windows 7 lets you backup and restore your Windows 7 operating system and all of the files and folders you choose.

You aren't just born with broad Stallone shoulders and arms, gentlemen. Of course we know you wish you never had to work to get those tight, chiseled arms and shoulders, but even the best of the best - that's right, including Stallone - have to work what their mama gave them to keep in shape.

Isometric exercises are strength training exercises that don't let the joint angle and muscle length contract during the movement. This means that the exercise is done in a static position with the muscular intensity coming from the weights and your own body.

Blind is a Limbo-like platformer on A10 Games where the player must platform through 2D environment that is largely concealed to them. This video will walk you through all of the game's 21 levels.