In this Outdoor Recreation video tutorial you will learn how to mount a fish finder on your kayak. There are many ways of doing this. All the methods work. It’s just a matter of personal choice where you want to mount it. Some boats are designed for a through hole transducer and have a space for it to mount it in a hole. Take a piece of foam, trace out the transducer and cut out the foam. Now open the front hatch of the boat and glue down the foam on the flat surface of the boat. Once that ...
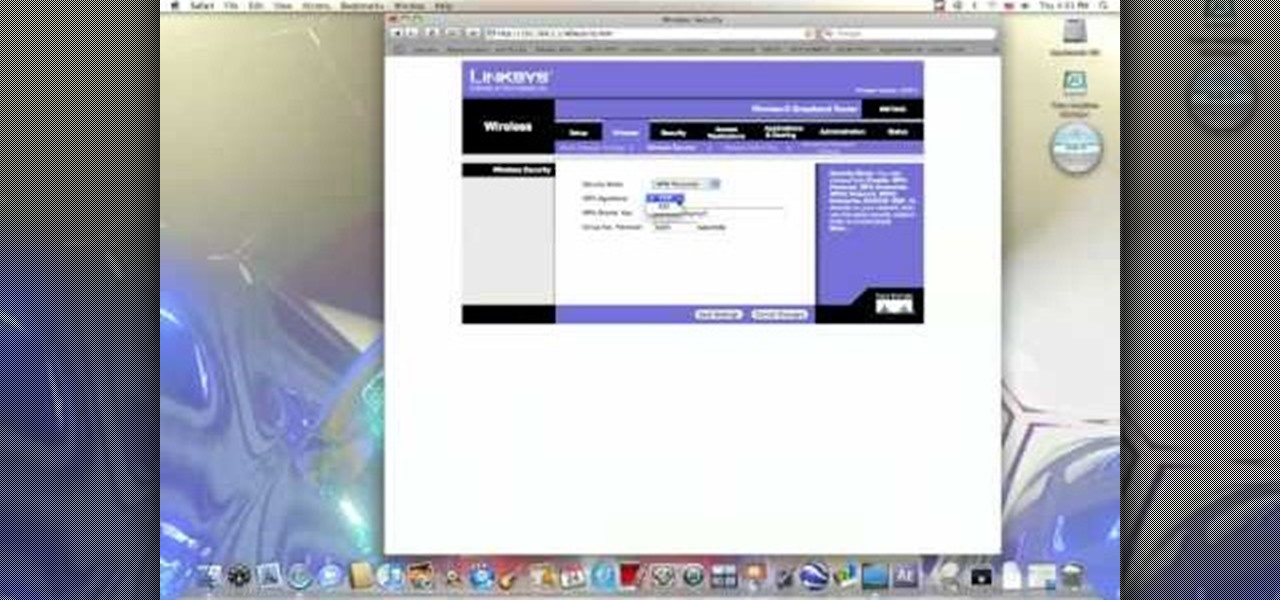
In this video from benjamoon we learn how to secure a linksys wifi network from a Mac. First type in your IP address in your browser bar which is 192.168.1.1 then press enter. If it asks for a password it is admin. Click on Wireless and here you can edit your name and who can access your wifi network. Under wireless security, go to WPA personal from the drop down menu. When you make your password, make it very challenging. He recommends just banging your hand against the keyboard, as long as ...
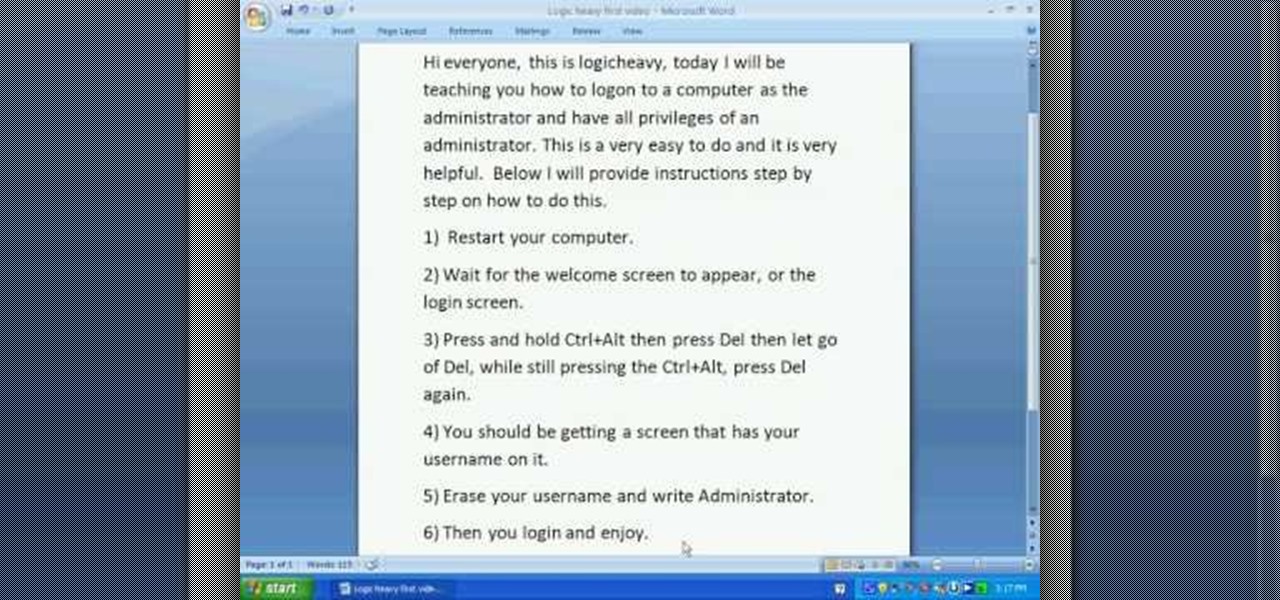
The video starts with a guy talking while we see a computer screen with instructions on how to log in as an administrator of your Windows XP Personal Computer.
Linking your social networking activity together has never been so easy. Randy Ksar shows us the simple process of linking your Facebook and Flickr accountstogether so you and your friends can view your them both easily without navigating from site to site. First, you should log into your Facebook page click on Profile, select settings and you should see Activity. All you need to do is simply click on the Flickr link and type your Flickr user account name and you're done. Note that your Flick...

A digital caliper is a good way to keep track of your body fat. With a caliper, you can measure body fat and keep track of your new diet or workout routine. This way, you will know the difference between muscle and fat, and not have to rely as much on the scale. A digital caliper is great in the sense that it is able to take an accurate reading in seconds, give you a clear output and beep when it is ready. A digital caliper can also be programmed with your personal gender and other informatio...

Gift baskets are a great way to celebrate the holidays and special occasions. They also are a great way for you to cheer a friend up and cure their blues. In this quick guide you will learn how to put together a kind and caring gift basket for someone recovering from illness.

In this video, you will learn how to grind and mix feed on a farm. Mixing feed allows farmers to buy feed ingredients in bulk, and prepare their own specialized blends, reducing costs. The farmers shown in this video use a Gel mixer, and they describe how theirs works, including a description and explanation of its parts and what they do. You will also learn about their own personal experiences with mixing feed on their farm with this mixer, as well as some tips based on this experience. The ...

Learn how to master tunes using Reason 4.0 software to get a more effective sound. The first step is to make sure the outputs are not in the red. If they are in the red, that means the sound is not that good, and you don't want to work with a bad mix. The next step is to add a McClass mastering suite to your mixer. As per the guide in this video, everything should be below 100 to 175 Hz mono. However, this is a personal preference and you should do what you feel is best for the sound of the m...

This video you shows how to send your pictures, videos, music and ring tones from your cell phone to your computer. The tutor asks you to find the pictures that you want to send to the computer, and then mail those pictures to your e-mail. We can then later open our computer and through the email download all the pictures and videos that we sent to ourselves. So in this way we can send all our personal stuff from the cell phone to computer without ever connecting the cell phone to the compute...

Emo and scene hair, distinct for its haphazard appearing fringes and bangs over the face, is probably the least daunting hairstyle for one to style for themselves, to add a certain personal, and a bit more unconventional touch. In this video, our host explains that, mainly, it's about just doing what you want, and not caring too terribly much, but, if you like the way he's done it, he explains that what he did was cut the sides to create more points coming out across the cheek. Then, for the ...

Start out by going to www.Facebook.com. From this page you will be able to create your own personal Facebook profile. Fill in your name, email, password, sex, and date of birth. Click 'Sign up' after you have filled in all of this information correctly.

Today, learn the basics of lock bumping. Lock bumping is a lock picking technique for opening a pin tumbler lock using a specially-crafted bump key. One bump key will work for all locks of the same type.

MAKE and Kipkay brings the do-it-yourself mindset to all the technology in your life. Make Magazine celebrates your right to tweak, hack, and bend any technology to your own will.

Sometimes we don't have the time or money to go to a therapist to have them help us manage our stress. Using a shower to reduce stress is easy with these tips. Get advice on reducing and managing stress in the shower in this stress management how-to video.

Abdominal exercises such as kneeling ab crunches work out the abdominal muscles. Learn abdominal exercises in this free ab workout video series featuring a personal trainer.

Check out this quick video tutorial on how to install Opera Mini 4 on the T-Mobile Shadow cell phone.

Tattoo lady and reality TV star Kat Von D is obviously extremely talented with the tattoo needle. Creating interesting designs for clients that include celebrities, Kat Von D exudes a distinctive style that includes looking like a tougher version of a classic pin up.

In this video, we learn how to give a professional hand massage. First, spread oil onto the hand with your hands, which will prevent you from sticking together. After this, open the hand up and interlock your fingers with theirs and start to massage the inside of the hand. Open the hand up and work your fingers into the sensitive muscle areas. Go slowly, but apply enough pressure around the hands to make a difference. After this, work the tendons on the front and work your hands around each o...

This instructional video Nehal Kazim from Site shows you how to make a complete Facebook fan page. Before creating a fan page evaluate the reasons of making a fan page. A fan page lets you connect with your future clients and fans and keeps them updated and gives them a platform to talk about your organization. To create a fan page go to the bottom of any page and click 'Advertising', select pages and click create a page. Select a suitable category and a suitable name make sure to select it c...

Instead of using Photoshop, why not give Apple's Aperture a try? Aperture is designed more for post-production work for professional photographers, letting you cull through shoots, enhance images, manage massive libraries, and deliver stunning photos.

Instead of using Photoshop, why not give Apple's Aperture a try? Aperture is designed more for post-production work for professional photographers, letting you cull through shoots, enhance images, manage massive libraries, and deliver stunning photos.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

In this episode of Full Disclosure we are explaining the website attack known as Cross-Site Scripting (XSS). Cross-Site Scripting is a type of security vulnerability that affects web applications that do not sanitize user input properly. This kind of vulnerability allows an "attacker" to inject HTML or client side script like JavaScript into the website. Cross-Site Scripting is most commonly used to steal cookies. Cookies are used for authenticating, tracking, and maintaining specific informa...

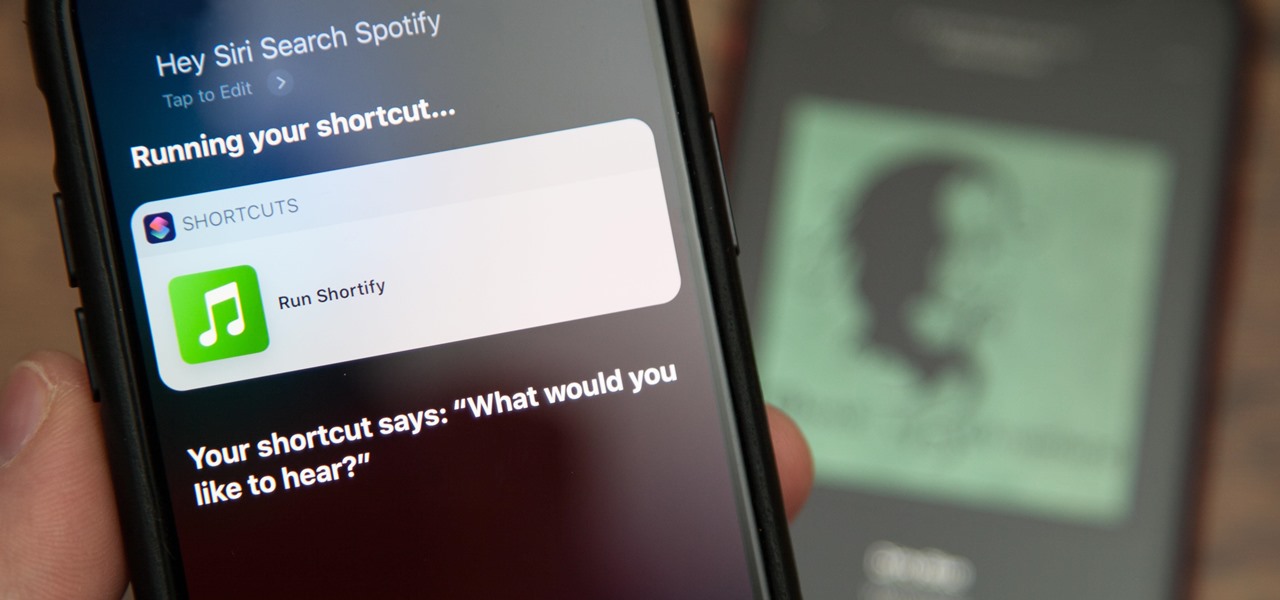
In iOS 13 and later, Spotify supports Siri commands, something we've wanted ever since Siri and Spotify were things. But if you're on iOS 12 still, you're missing out. All you can do is open the Spotify app, then pause and skip tracks with Siri after you start playing a song manually. There is a workaround, however.

The Consumer Electronics Show (CES) is the first big tech event of 2018. This year, if the early news is any indication, augmented reality could be the big star of the show.

The narratives around virtual reality consistently revolve around human empathy and emotion, while the story around augmented reality has been decidedly more dispassionate and business-focused — until now.

With the addition of the OpenSSH client and server in the Windows 10 Fall Creators Update, you no longer have to rely on third-party programs to open an SSH server and connect to a Windows machine. While still a beta feature, this represents a long-overdue update fulfilling a promise made back in 2015.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

First of all, Merry Christmas and Happy New Year to all Null-Byters that learn and teach in this wonderful site. In this article we will explore the basics of the meterpreter's IRB (Interactive Ruby Shell).

This is a short explanation and tutorial on how to grab saved passwords from Google Chrome, ideally from a meterpreter session. The idea behind this is to understand how saved passwords work and how to keep them safe. Let's have some fun :D Understanding Google Chrome Saved Passwords

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.