Going to school to be a nurse? Then one of the many techniques you will learn is how to irrigate a bladder. In this nursing how-to video our host demonstrates how to do a Nesbitt Young irrigation. This type of bladder irrigation demonstration is not a CBI, continuous bladder irrigation, it is an intermittent irrigation. However it does use a continuous infusion of sterile solution into the bladder, most often, using a three-way irrigation closed system with a triple-lumen catheter. Infrequent...

Massaging the foot benefits the entire body. It is very important to know the proper massage technique and have the right equipment. Learn the art of giving massage in this health how-to video.
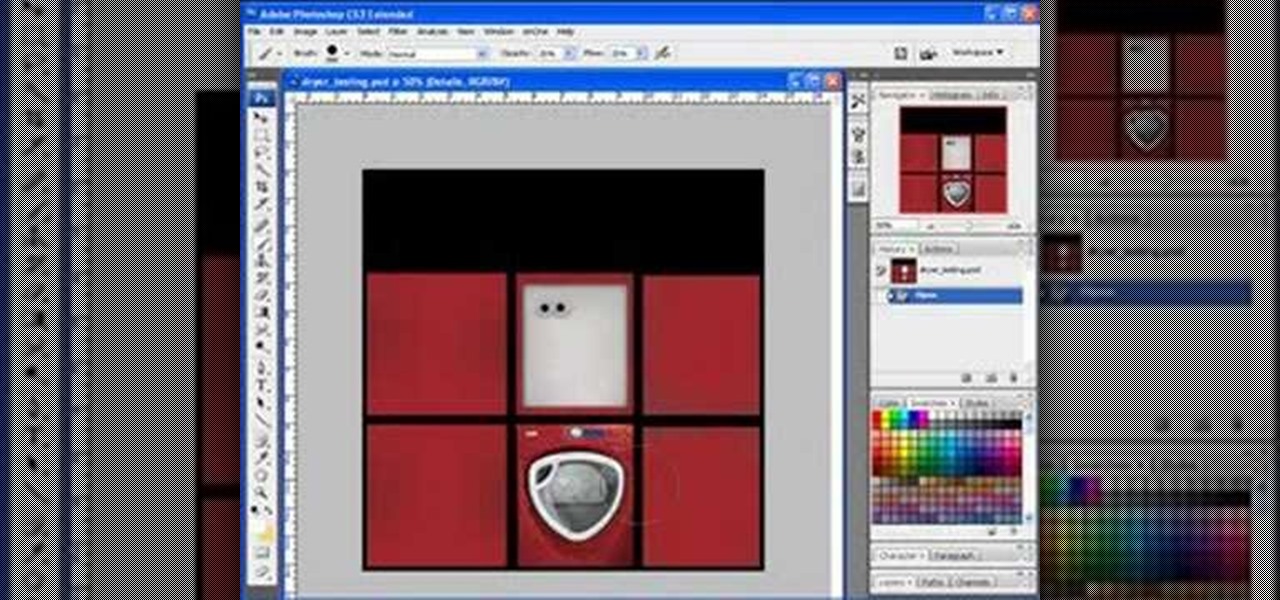
The third dimension has finally arrived to internet browsing! Be sure to catch the wave of innovation with this series of tutorials. Initially, we'll be examining the importance of texturing basic 3D objects. Watch as the almost magical effects of texturing in 3ds Max transform a simple cube into a trendy clothes dryer. Polygons are saved, browsing is made speedier, and clients are bound to be happy. Next stop, bring it into Papervision3D! If you wish to learn about using 3D elements on the i...

The clavicle is a V shaped bone that makes up the shoulder area. Massaging the clavicle, or collar bone, relieves tension in clients. Learn the art of giving massage in this diet and health how to video.

Find yourself going to the same websites or blogs every morning? In this video tutorial, you'll learn how to open them all using a single click. First, view all of your bookmarks. Then, create a new bookmark folder in your bookmarks bar. Add the desired books and check the autoclick box. Whenever you click on the bookmark folder in your bookmarks toolbar, your Safari client will launch all of the websites in separate tabs. For more, watch this OS X video tutorial from Apple.

The Seal is an original pilates exercise that increases core strength and balance while delivering a fun exercise. The goal of clapping the feet like a seal claps its flippers is to stabilize the torso against the movement of the legs and increase the time your suspended on each side of the movement by just a second or two to develop ab strength and balance. The Seal exercise is probably our favorite exercise as it always makes clients smile. Watch this fitness how to video and you will be st...

This pilates how-to video illustrates the Obliques Roll Back exercise. This is a challenging rotational pilates exercise for athletes and advanced clients.

Zune is a digital media players and services sold by Microsoft. It includes portable media players, client software, and the Zune Marketplace Internet music and video store. If you hate the Apple iPods, you probably have one of these MP3 players.

In this video tutorial, Chris Pels will show how to include JavaScript to an ASP.NET page for use on the client page to provide a richer and more robust user experience. First, see how to include JavaScript directly within an ASP.NET page and reference the script from within HTML page elements. Next, see how to abstract the JavaScript to an external JavaScript file which offers the advantage of being cached by the browser and can be used by multiple pages. Lastly, learn how to add JavaScript ...

Don't want to shell out the big bucks for some fancy, expensive budgeting software? Well, if you have Excel 2008 for Mac installed, you can manage your budget right there. Personal financing doesn't get easier than this— even business finances are easy to keep track of. The Microsoft Office for Mac team shows you just how to manage your finances with pre-formatted Ledger Sheets in this how-to video.

Your iPhone is full of apps that are all vying for your attention. Notifications from Facebook, Instagram, and even Apple Messages can get out of hand fast. With iOS 15, Apple gives you the tools to choose exactly who can contact you and when. Keep reading to see how to take control of your iPhone's notifications so that you only receive the most important alerts.

HomePod and HomePod mini are excellent smart speakers if you're entrenched in the Apple ecosystem. They even offer ways to protect your sensitive information from friends and visitors who try to ask Siri to spill your secrets. But there's an extra layer of privacy you can put in place to make sure nobody gains access to any important notes, reminders, and calendar events.

Once you start converting text to speech, you'll never go back. Allowing you to easily listen to large amounts of text while multitasking, the Notevibes Text to Speech Personal Pack: Lifetime Subscription will transform your daily productivity at home, work, school, and anywhere else you may be. Even better: it's on sale now for just $69.99, which is a huge 87% off the regular price of $540.

For some of us, mornings are difficult. But if you can manage to start your morning right, you can trigger a chain reaction that leads to a more productive day. Fortunately, our phones have the tools to help us get off to a good start.

Architects are natural candidates to be early adopters of mixed reality. Their trade consists of not only designing buildings and spaces, but also presenting those designs to clients, who then decide that their vision is worth spending thousands (if not millions or billions) of dollars to build in reality.

Kryptowire, a company specializing in mobile security solutions, released a report on Tuesday, November 15 that exposed firmware in a number of Android devices that was collecting personally identifying information (PII) and uploading it to third-party servers without users' knowledge.

Pokémon GO, the global augmented reality game that's brought fans out of their homes to catch Pokémon across the planet, has brought about plenty of real-world positives. Unfortunately, when players get power hungry and start taking game hacks too far, we all get a little screwed—both digitally and in real life.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

The personal computer is a strange and powerful entity, capable of bringing great joy. Just as often, you probably want to chuck the damn thing at the wall because it doesn't work right. If you want to pull a prank on a friend that will really upset them, messing with their computer is one of the best ways to do it. This hilarious video will show you how to do three great PC pranks quickly and easily, including changing the contrast on the monitor and pretending to edit websites using Javascr...

In this tutorial, we learn how to create a website with external CSS and HTML. Start off by managing your site like usual, then create a new HTML document and new CSS document. Now, name both of these to what you would like, then link them both together by linking the CSS in your HTML document. Now, make a container div, which is what will center your main document. Change your different settings so your div will be exactly how you want it to be. Next, make a banner for your page and set the ...

Lady Gaga is definitely in shape. No one can deny that. But how does she do it? How does pop music's most popular artist stay in perfect shape? How does she get those great looking abs?!?

Adobe Photoshop is the industry and personal standard for editing photos on a computer. If you have a digital camera, or ever want to have a digital camera, you need to know how to use it. This video series will show you everything you need to know about using Photoshop's many tools and options to do just about anything you want to a photo.

Michelle Trap, a Certified Personal Trainer from Gold's Gym, teaches the viewers how to do barbell leg squats. First, use the Smith machine to do the leg squats. It is beneficial because the machine holds you in place. You will also need to place a bench behind you since you will use this when you lift your legs. Rack the barbell slightly lower than your shoulder and have a slight split stance with your front food centered. With this stance, take your back legs and place it on the bench behin...

If done wrong, a backflip could be devastating. But if done right, a backflip just might make you the coolest person ever. This is a unique backflip tutorial that uses both video examples and instructional text. See how to do a backflip. Follow these steps, one by one, to see what you're doing wrong.

This clip goes over a Pilates arc modification on the Reformer for clients with kyphotic spines. With Pilates, as with any physical fitness system, a basic mastery of proper technique is essential for both maximizing the effectiveness of your workouts and avoiding accidental injury. Whether you're looking to slim down or merely tighten up your core, you're sure to be well served by this home fitness how-to from the folks at Balanced Body Pilates. For complete instructions, give this free exer...

Being in sales is hard work. After all, the only thing more painful than trying to sell a hand cream or knife set to a stubborn client is perhaps pulling out teeth - without novacaine. And God knows how many times we've hung up on telemarketers because, well, they're a little too persistant.

This 4 part video series is a gift from me to all the other singers out there who have shown me such great love and support. It contains a full vocal warmup that will improve tone, expand range, and increase control. This is pretty much the kind of warmup that I might do with a private client, but it's for you guys - free of charge.

One of the hallmarks of augmented reality's coming of age is that the technology is starting to find a home in business categories that are less obvious compared to typical AR enterprise use cases.

In the world of technology, there's often a trade-off between convenience and security. The Java Remote Method Invocation is a system where that trade-off is all too real. The ability for a program written in Java to communicate with another program remotely can greatly extend the usability of an app, but it can also open up critical vulnerabilities that allow it to be compromised by an attacker.

With all the recent activity around augmented reality, the possibilities involving immersive computing and commerce are quickly becoming obvious, and digital payments giant PayPal has no plans to sit on the sidelines

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back My sleepless army of young hackers, Everyone uses internet, right? So for this tutorial, i'll start with the basics and slowly we'll get to the UPD Protocol.

Video: . How to Stop Shrinkage with Shea Butter & the Banding Method!

BitTorrent—corporations hate it with a passion, but the people love it. The notorious file-sharing protocol was responsible for 36.8% of all upstream Internet traffic last year, as well as 10.3% of all traffic.

Welcome back my fellow hackers! In my last few articles, I've concentrated on what is called a listener, which is basically the same thing as backdoor and rootkit, only "listener" sounds much less malevolent than the other two terms.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.