The mouse is the primary tool most people use for accessing their computer and the vast stores of information on the Internet. Wouldn't it be funny if instead of allowing you to click icons on the computer screen, your mouse just lit up and made noises when you pressed it buttons? Well now you can prank a friend's optical mouse and make it so. This video will show you how to do it using only a mouse, simple tools, and a light-up, noisemaking keychain cow toy. Prank an optical mouse by replaci...

If you are sitting in front of a computer all day for your work, make the most of it by exercising your different muscle groups even while you are finishing a PowerPoint presentation or filling out cells in an Excel worksheet.

The back row is black wool. The table lamp is a glowstone with trapdoors, sitting on a nether fence.

This tutorial will be based on creating a partition in Windows Seven. I have seen so many people attempt to do this themselves without guidance. Ultimately, they end up with a corrupt system. The aim of this tutorial is to make sure you don't corrupt your system.

Facebook's new Timeline feature has been rolling out gradually since its unveiling in September, but yesterday it finally became available to Facebookers everywhere. It's even available on your mobile device, too. Those who want to upgrade to the radical new profile design can do so by simple logging into their Facebook account and visiting the About Timeline page on Facebook.

This is an excessive performance mod for a computer, but ecxessive is good in the computer world.

Your IP (Internet Protocol) address is your unique ID on the internet. It's synonymous with your home address. Anyone in the world can contact your computer through its IP address, and send a retrieve information with it.

It's a question I've been pondering a lot lately. Technically, children under the age of 13 are not allowed to join Facebook. But according to a Consumer Reports in May, 7.5 million children 12 and younger are already on the site. Currently, federal law prohibits websites from collecting personal data from children without parental permission. The Children's Online Privacy Protection Act, or COPPA, as it is more commonly known, has been in effect since 1998, but has not been updated since.

Redstone inventions are a staple of Minecraft, and computers designed with it have been a popular form of construction. User dudearent006 takes this to another level with this staggering creation - a highly advanced redstone computer! Featuring 150 bits of RAM, a 10-bit processor and a GPU advanced enough for its own topic, this mind-blowing creation has to be seen to be believed.

Behavioral ad targeting companies are diving deeper into the realms of your subconscious with a new approach to serving adverts to you online—and they're using your television.

It's been about five months since Google first unveiled their prototype future computers running Chrome OS, and the time is nearly here for the Chromebooks to be unleashed on the public. But there are a lot of qualms over the release of Chromebooks, with most criticism coming from their lack of traditional laptop-based features such as an optical drive, storage space and the ability to run comprehensive software programs like Adobe Photoshop.

At Google I/O this morning, Google finally announced the launch of its much awaited Google Music service. It's currently in invite-only beta mode, but they claim it will open up to the masses soon enough. To start syncing your music library with Google's Cloud now, you need make sure you're signed into your Google Account, then click here for a personal invite. It's currently free for a limited, undisclosed amount time.

Have you ever left your computer one all night? Maybe downloading something, or just out of habit? Well there is a way you can turn that unused CPU usage in to cold hard cash: Distributed Computing.
computer zombies is our main site. we add all of our guides there (more than we have here) and it has a ton of ways to become a part of our community

Blacksmith Sage Werbock —also known as the Great Nippulini, "pierced weight lifting extraordinaire"—welded together this Star Wars Imperial Walker sculpture with a bunch of old computer parts and scrap metal. Currently listed on Etsy for $450, the AT-AT is artfully assembled as follows:

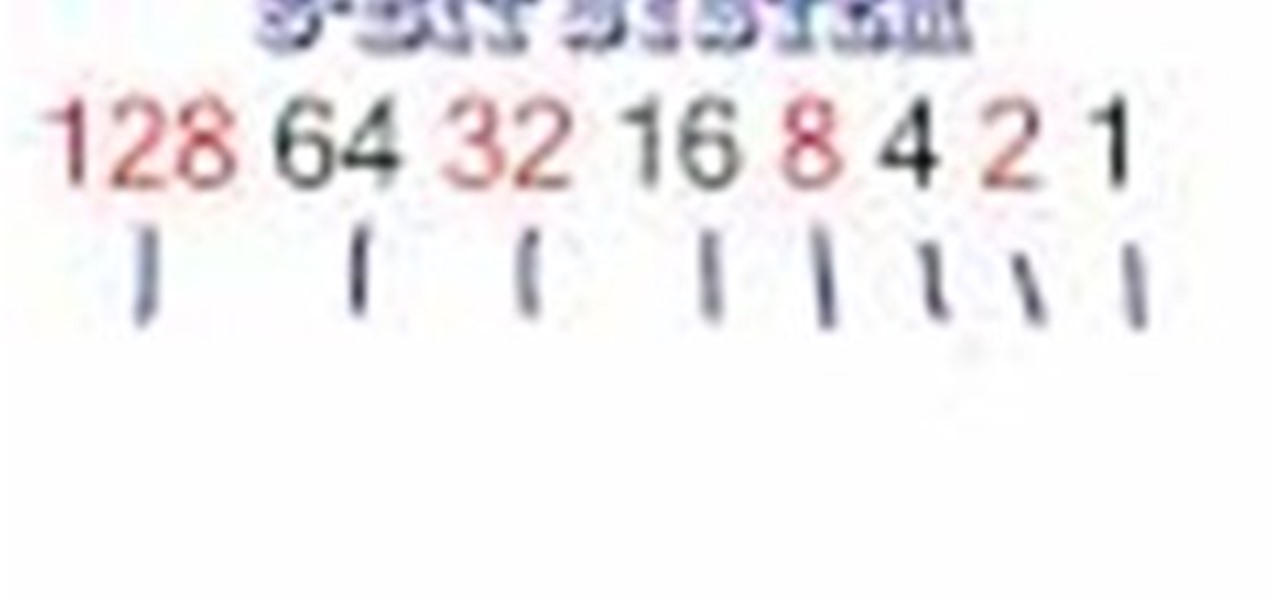
You may see the term "binary code" used in some of the blog posts here. You don't ever need to know what binary code is in order to use a computer. But if you're feeling curious and want to learn more about what makes your computer tick, check out this easily-accessible tutorial.

In this video we learn how find out IP addresses of websites and shut down the computers with those IP addresses. To do this click "start", then "run" then type command prompt. In the command prompt type "tracert website" (example tracrt Google.com) then hit enter. Various IP addresses should be returned. Then in the command prompt type "shutdown-i" and hit enter, this opens the remote shutdown dialogue. In this dialogue you can add the IP addresses and adjust the various other options then c...

This video shows you how to fix a sticky computer mouse. Probably one of the most infuriating issues surrounding computers, never let your mouse get sticky again! Fix a sticky mouse.

This film shows you how to replace your computer's internal power supply component. Install or change a PC power supply.

Becoming a competitive candidate in IT and Data Science takes more than knowing a few coding languages and being good with computers. To really stand out from the crowd, your knowledge should be extensive and your experience should be diverse. The 2021 Complete Computer Science Training Bundle provides that depth of knowledge and a starting point for gathering that experience. Right now, it's on sale for just $39.99.

With Avatar, Facebook's personalized stickers for use on its social and messaging platforms, those who aren't on Facebook or have otherwise dumped the social network may feel left out.

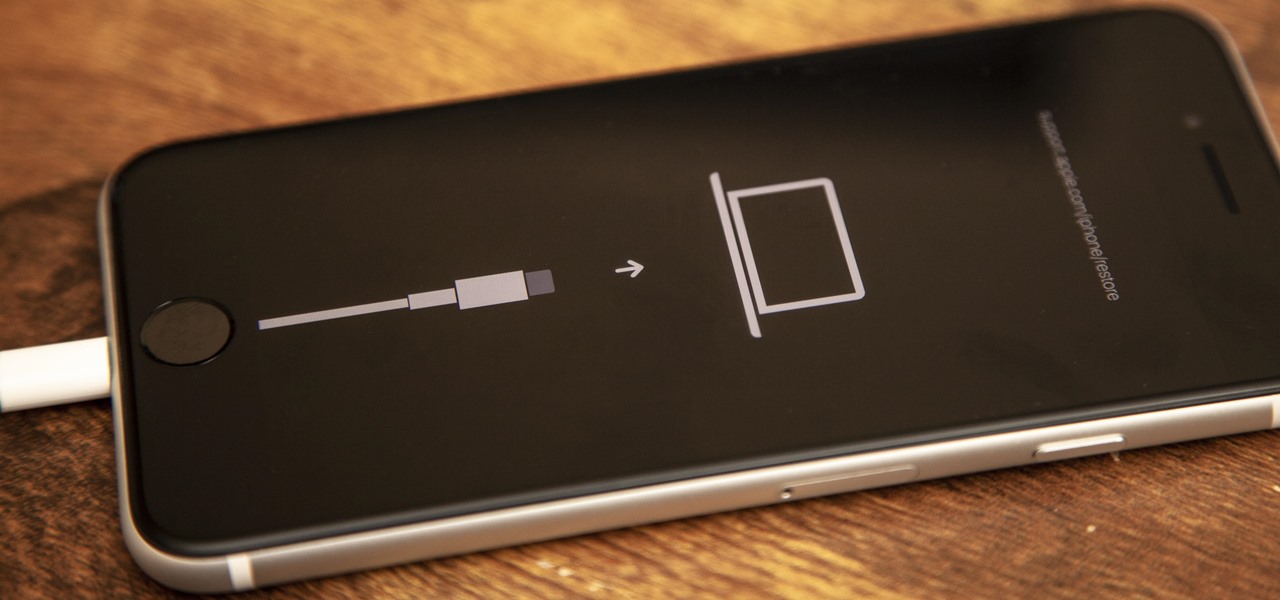
If your new 2020 iPhone SE is frozen, unresponsive, or won't load the system, and a standard power down and up procedure didn't work, there are few more things you can try. Force-restarting the device may do the trick, recovery mode is a last-ditch option, and DFU mode is your fail-safe.

The Digispark is a low-cost USB development board that's programmable in Arduino and capable of posing as a keyboard, allowing it to deliver a number of payloads. For only a few dollars, we can use the Digispark to deliver a payload to a macOS computer that will track the Mac every 60 seconds, even bypassing security like a VPN.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

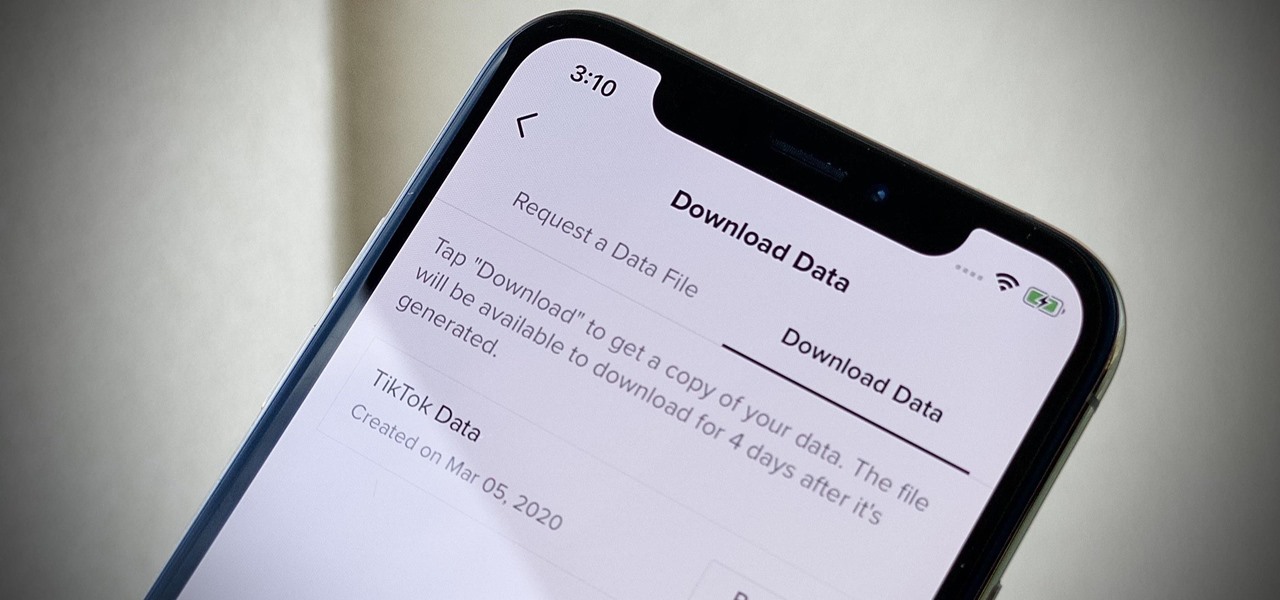
If you're concerned about your privacy, TikTok might not be the app for you. Its shady practices with user data have been the subject of concern, criticism, and even legal action by the US government. Then again, it's just so addicting. If, like me, you're not going to stop using TikTok anytime soon, you should at least know how to view the personal data it has collected on you.

Google's push for your safety gained some much-needed attention when it released the Pixel 4 smartphone. It has an app called "Personal Safety," which uses the array of built-in sensors on your phone to detect if you've been in a car crash. The futuristic safety feature was exclusive to the Pixel 4 initially but is now available to all Pixel owners as well.

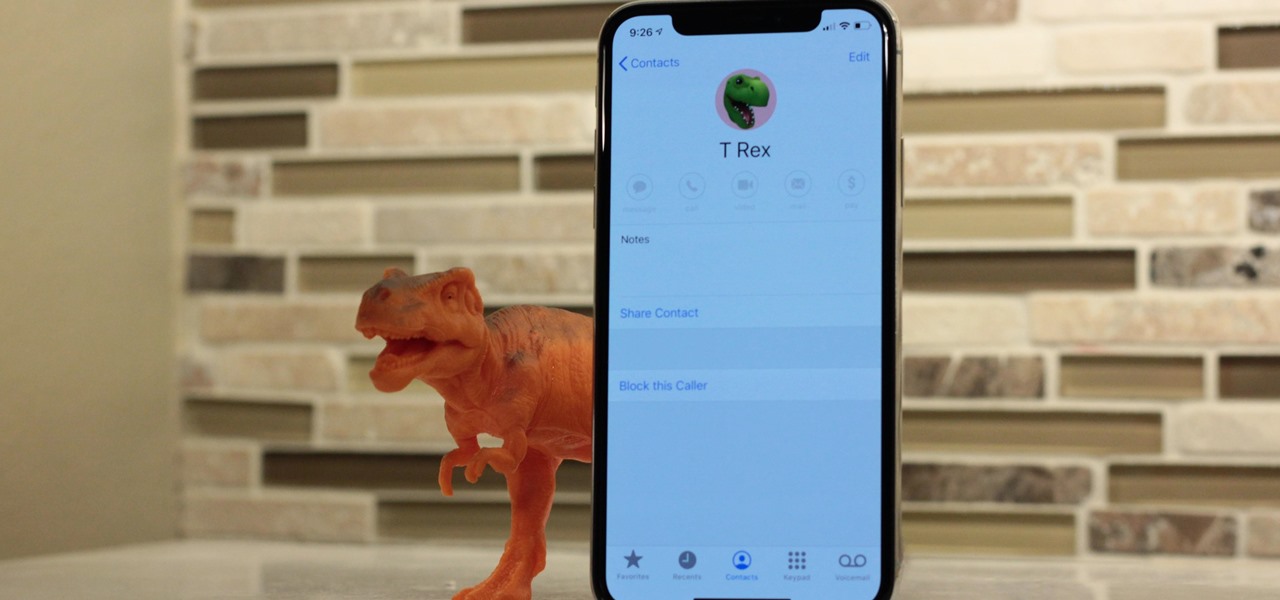
In iOS 13, Apple added the ability to use Memoji and Animoji for your contact photo and then share your name and photo with others through iMessage. It works excellent for contacts that use iMessage, but those that don't are stuck with old pictures or gray monograms. With a few simple steps, however, any contact in your list can have their own Memoji, Animoji, or colored monogram.

While the automotive industry is moving towards adopting AR displays in future models, BMW is already shifting into the next gear with its vision of the technology.

Facebook and its Oculus subsidiary have been open about their intentions to bring AR wearables into the mainstream for some time now.

If waveguide display maker DigiLens has its way, enterprise businesses and consumers will soon be able to purchase smartglasses for less than $500 — as long as they can supply their own computing and battery power.

Using Netcat to backdoor a macOS device has its short-comings. If the compromised Mac goes to sleep, the Netcat background process will occasionally fail to terminate correctly; This leaves Netcat running infinitely in the background and the attacker with no new way into the device. As an alternative, we'll use the lesser-known Tcl shell which can handle abrupt backdoor disconnections.

If you ever want to root your OnePlus 6, install TWRP, get Magisk and Xposed, or flash a custom ROM, the first thing you'll need to do is unlock your bootloader.

We are still months away from Google unveiling the new Pixel 3 and 3 XL. As rumors continue to trickle in revealing more about what it will look like and its specs, we've learned an important aspect — who is actually manufacturing them.

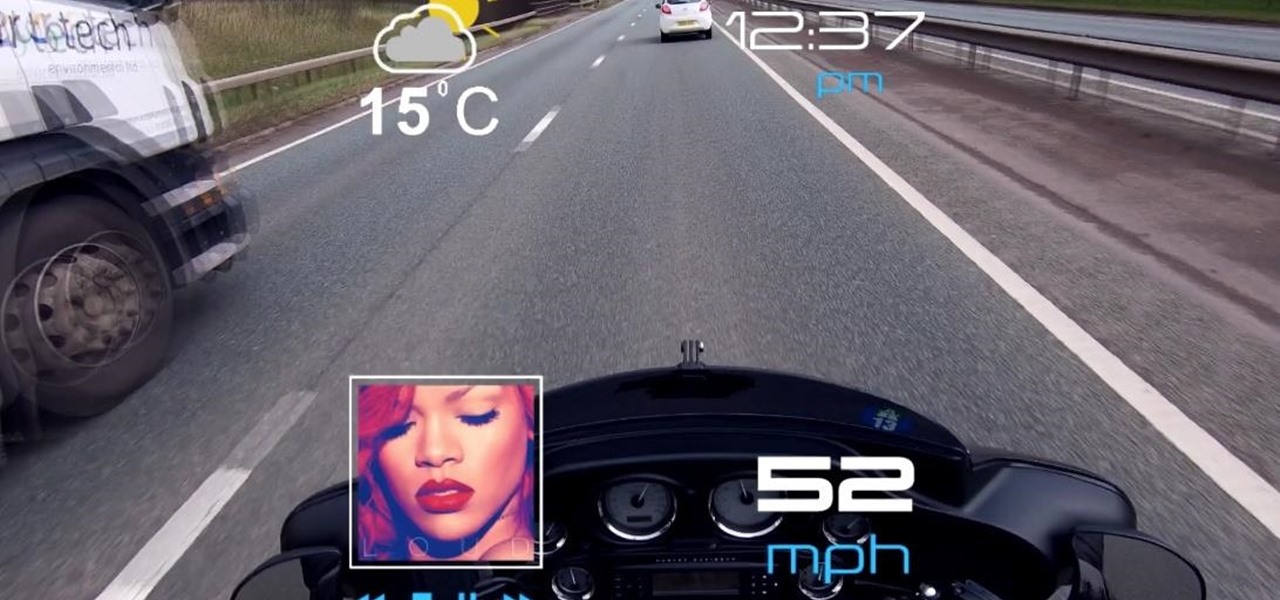
Less than a week after securing a $25 million Series C funding round for automotive HUDs, DigiLens has introduced a new waveguide display for motorcycle helmets that's thinner, lighter, brighter, and manufactured at a lower cost.

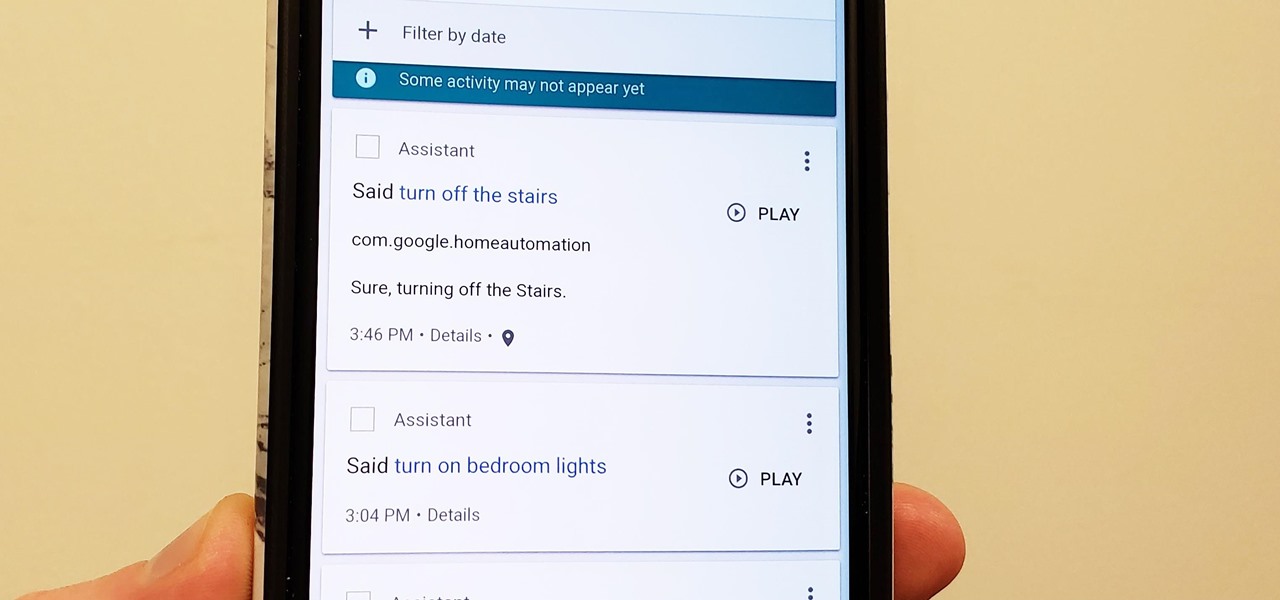
Privacy is a hot topic. In the wake of Facebook's data scandal, many want to safeguard their personal info. On the other hand, we all gain a certain amount of convenience by using services administered by huge companies like Google, Facebook, and Twitter. Google Assistant collects plenty of data, but you can easily check what is stored and delete items at will.

Following the surprise release of Magic Leap's SDK on Monday, March 19, Unity, Unreal Engine, and Mozilla followed up by announcing official partnerships with the company.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

Thanks to iCloud and AirDrop, it's really easy to sync photos between an iPhone and a Mac. But if you have an Apple phone and a Windows computer, this process isn't quite as simple. Thankfully, Microsoft has just released a new iPhone app that makes it a breeze to move photos and videos from your iPhone to your PC.

Android used to have a notification ticker, but those days are long gone. Now, important new messages pop up on the top half of your screen with what's known as a "heads up notification." If you're in the middle of something, these popup notifications can be pretty annoying — luckily, it's pretty easy to turn them off.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.