Google Now is an extremely intelligent personal assistant that automatically updates and prepares the most pertinent information for you on your Android device. Traffic updates, alternatives routes, weather conditions, and other important data is constantly being monitored and updated for you.

Remember how the bad guys in Scooby Doo would always use cut-out portraits to spy on people through walls? Well, unless your landlord is super cool, you probably shouldn't start cutting holes in your wall just yet, but you can make a higher tech version, thanks to NASA employee Mark Rober. Mark used a cheap picture frame and a portrait with the eyes cut out to make the "Scoob Cam," which also doubles as a surveillance device. He used an iPhone and an iPad to start a FaceTime chat, then taped ...
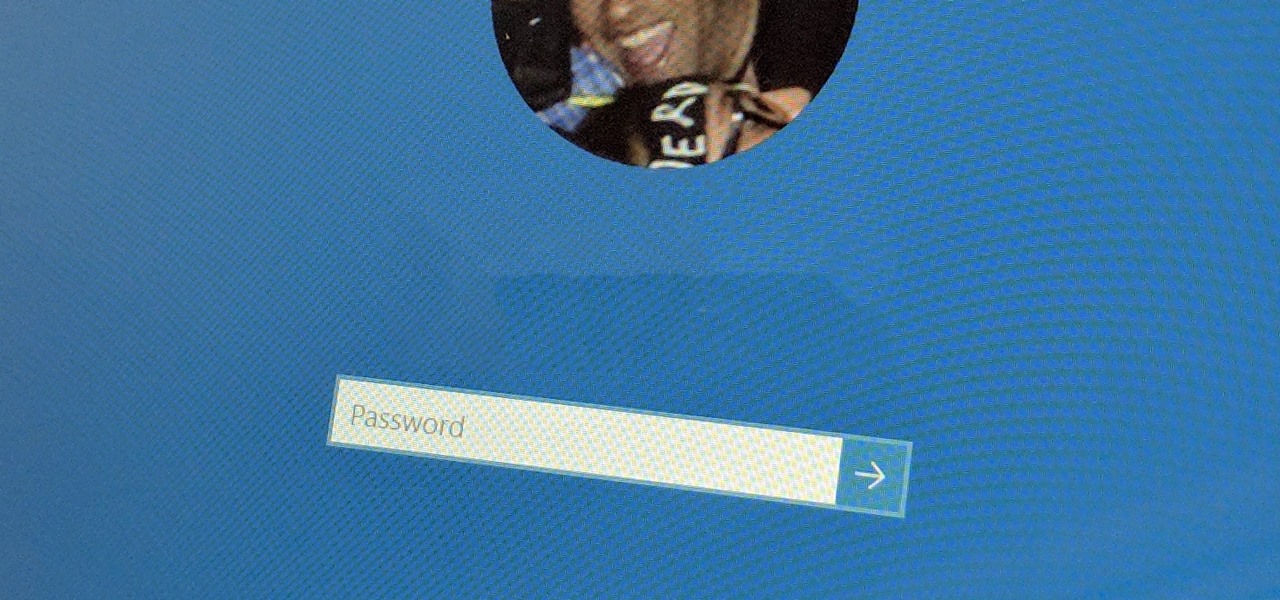
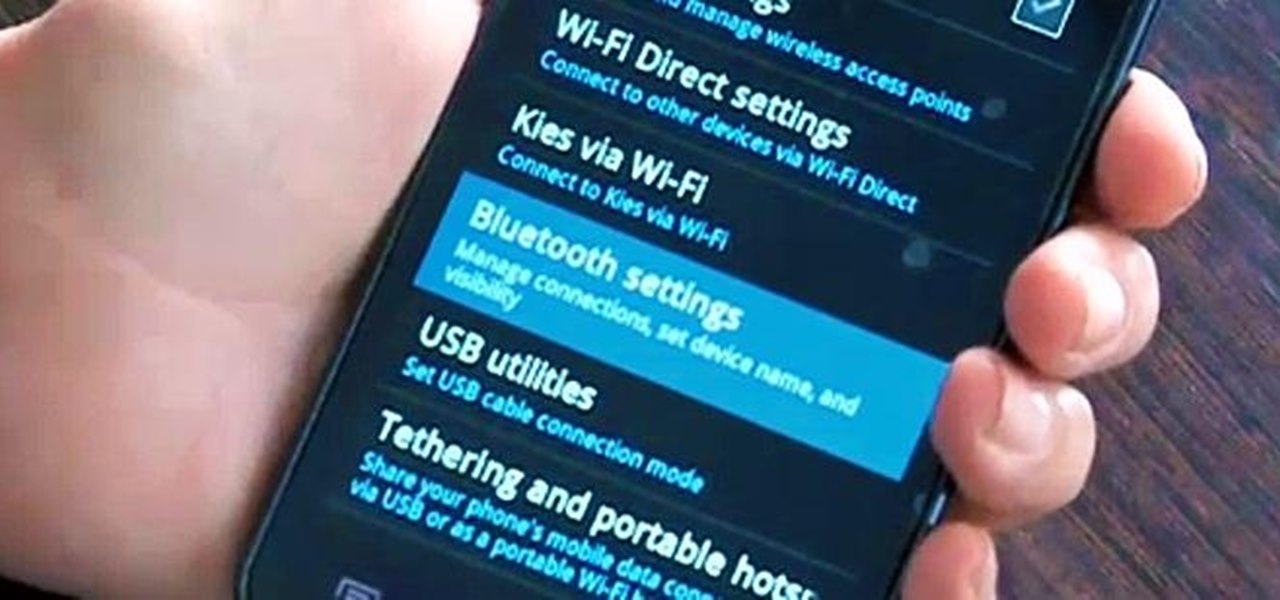
It's good to password-protect your PC to make sure that your personal files, folders, and important documents are safe and can't be modified without your permission. Though, entering the password all of the time before using your computer might frustrate you.

Most of the spam messages are commercial advertisements, phishing websites and get rich quickly messages that asks users to provide personal details and other confidential information.Spam filters in Gmail prevent its users from these spam messages and restrict them to enter in user’s Gmail inbox.Generally, it acts like a firewall between spam messages and Gmail Inbox.Gmail filters detect the sender’s email address and accordingly send the received messages in Inbox or Spam folder.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Dried out markers are the worst. They take up space, and for some reason, even though they're totally useless, most of us have at least a few lying around just for the sake of not throwing them out. Luckily, Julie Finn over at Crafting a Green World has come up with a way to repurpose them into alcohol ink, a versatile type of ink that can be used on non-porous materials like plastic, glass, and metal. This is truly a tutorial for the pack rat in all of us. First, a little primer on what you ...

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

As if the world needed one more reason to be obsessed with Shark Week, Volkswagen has teamed up with Discovery Channel to create this awesome "underwater car" that's actually a mobile shark cage.

One of the biggest time-consuming nuisances for any barbecue is prepping corn on the cob. If you've got a lot of mouths to feed, shucking corn is just downright painful, thanks to all of those silk strings that hide in the crevices of the kernel rows.

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

Would you know what to do if someone ingested poison? Equally important, would you know what not to do?

Rumors, gossip, exclusion. Mean girls have a lot of weapons in their repertoire – here's how to combat all that nastiness.

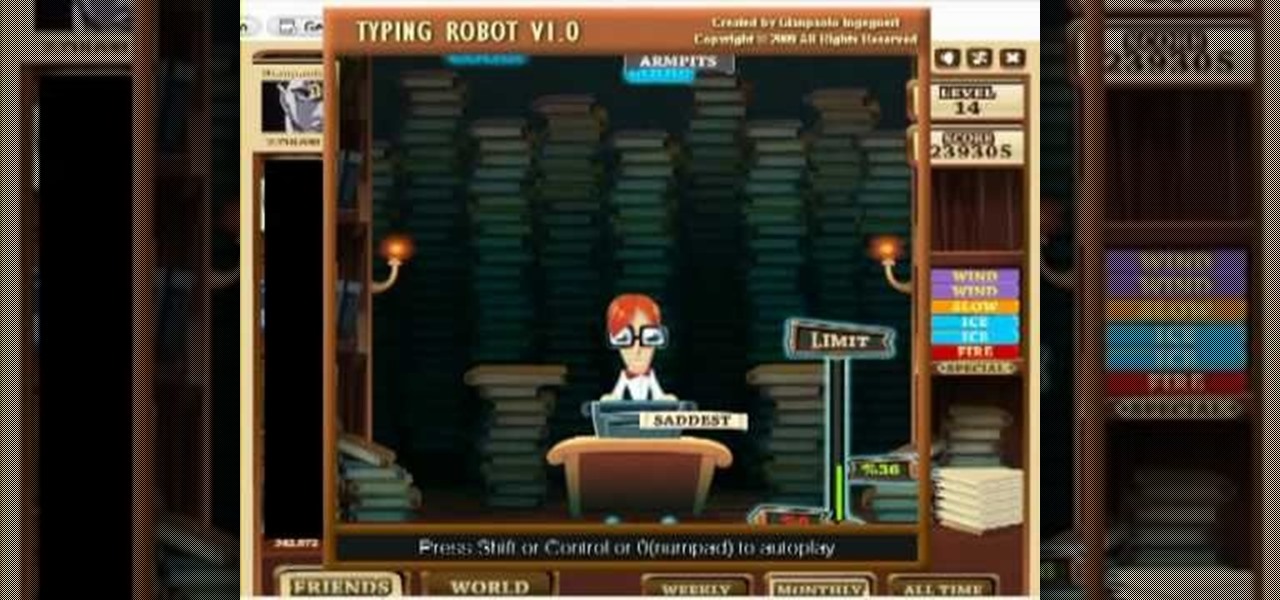
http://www.texturemind.com/post463/ TypingRobot is an artificial intelligence studied to increase your points record with the Typing Maniac game on Facebook. It can recognize several labels because it uses a powerfull OCR system (tesseract) and some principle of word correction. With this program you can make millions of points without problems (my personal record is about 2.700.000 points).

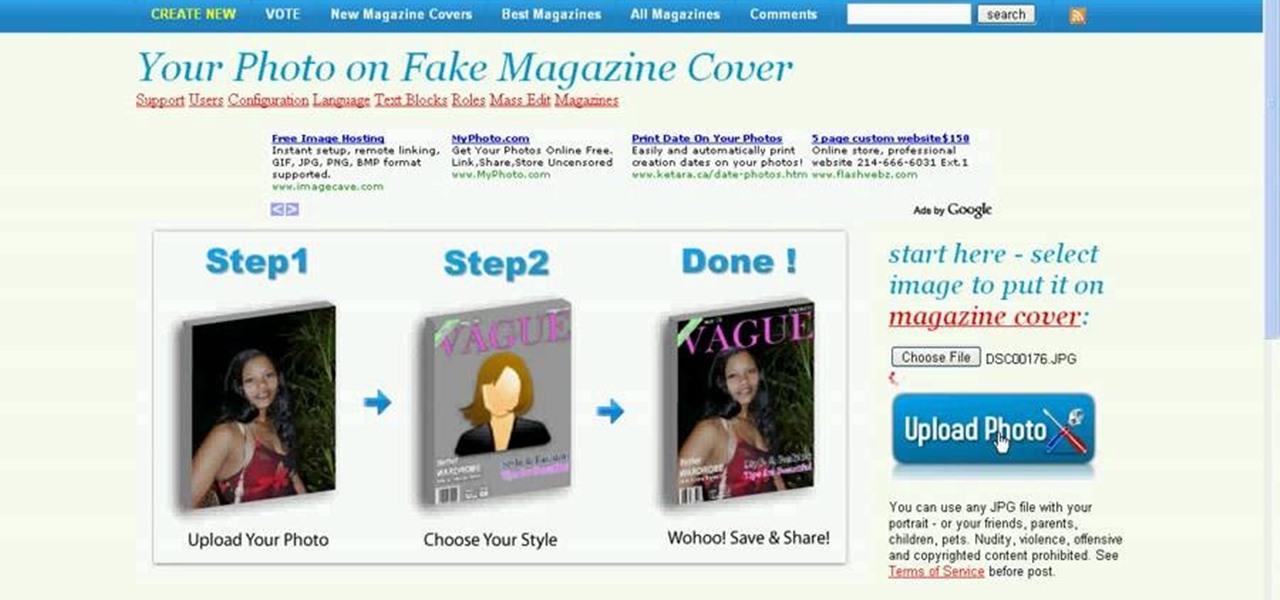
Want to impress your friends by showing that you're hot stuff? Put your face on a magazine. This short tutorial shows you how to create a fake magazine cover on the web, using your own personal pictures. Just go to MagMeNow.

Add even more personal touches to your crocheted items. This how to video is a tutorial on how to embroider crochet projects using the lazy daisy stitch. You can embroider just about anything with the daisy stitch. Watch and learn.

Are you going out in that little black dress that you've always wanted, but you don't know what to accessorize with? Well, The beauty of the little black dress is that you can accessorize it to reflect your personal style. A fashion designer shows you how to incorporate funky and classy pieces into your wardrobe.

If your not sure how to steam your media files to your Playstation3 this video will explain three different ways to achieve just this. Your options will include using a thumb drive, a personal web server or get the appropriate software.

Nothing says you care like a hand-made card. Show that special someone what they mean to you or just have fun with this cute arts and crafts project. Get your markers and colored pencils. Get your glitter and glue. Get creative.

Purchase the necessary equipment for this project. Pumice stones can be purchased at any beauty supply store. Chlorine can be purchased from any household supply store. Sodium bisulfite can usually be found at hobby stores. Obtaining the industrial washing machines for personal use is the hardest step. Call local cleaners to see if they will allow you to use their machines. Soak the pumice stones in chlorine overnight. This will allow them to soak up the bleach and create a good absorbency fo...

Testing products for a living is a bit more complicated than it sounds. You Will Need

It's easy to make a peck of pickled peppers – or any other vegetable – with this basic recipe. You Will Need

Sure, they have personal trainers and chefs to help them shed their postpartum pounds. But here are a few of their other secret weapons.

Step 1: Score! Watch for the referee signaling a touchdown, field goal, extra point, or successful try by raising their arms straight up over their head. Raising their hands above their head with palms together signals a safety.

A good party guest should live by this motto: Ask not what the party can do for you, but what can you do for the party!

If your new window treatments include blinds, save the hefty installation fee by hanging them yourself.

So you've been given the slip -- the pink slip. Take a deep breath, and do the following. You Will Need

Lower back injuries are common but preventable. Learn simple lower back exercises to increase strength from tips from a personal trainer in this free exercise video series.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

As government officials scramble to contain the new coronavirus outbreak with bans on large gatherings, travel restrictions, and school closures, the rest of us have to worry about how we're going to safely purchase water, toilet paper, groceries, and other household goods during the global COVID-19 pandemic.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

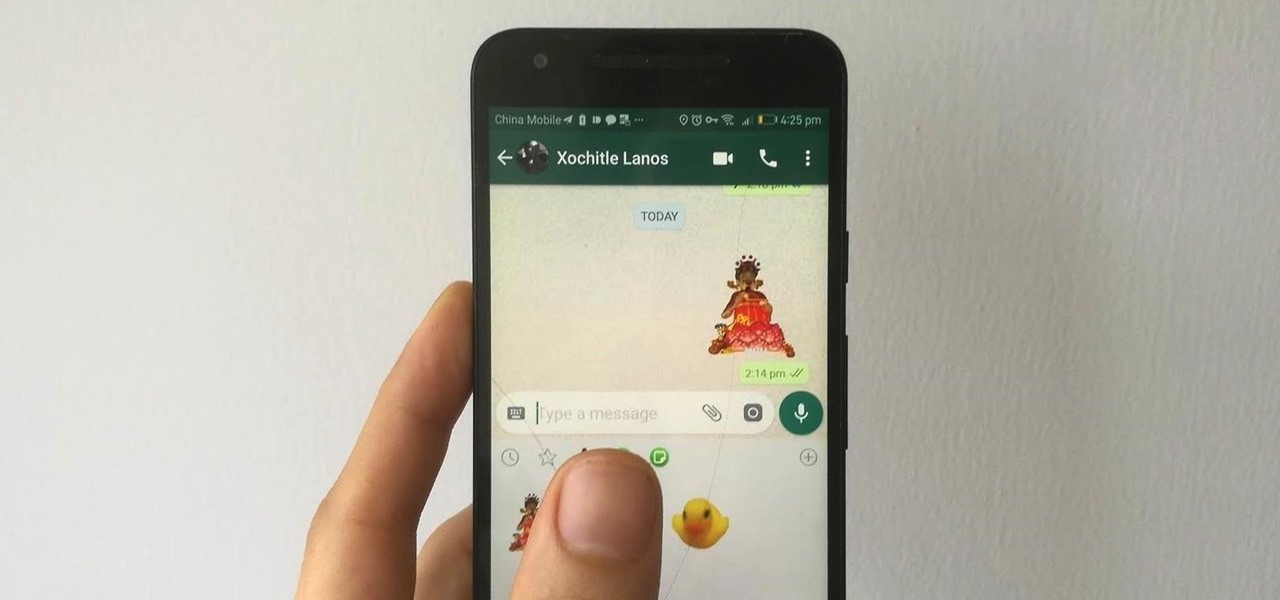
WhatsApp stickers can make your chat more fun. The stickers that come with WhatsApp are fine, but they're standard and accessible to everyone. What if you wanted to show off unique stickers that your friends haven't seen? To take things to the next level, you can create your own WhatsApp Stickers.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

Despite their sometimes fluffy reputations and occasionally ethically compromised viewpoints, tech evangelists are important, don't let anyone tell you otherwise. The right passionate voice behind the right technology platform or piece of hardware can sometimes spell the difference between fostering a community of potential users and watching a product die on the vine.