Who wouldn't want to know if someone was trying to log onto their personal computer without their permission? Be it your annoying co-worker or your girlfriend, there are many cases where people may try to gain access to your desktop or laptop.

While Siri's integration with the iPhone is becoming increasingly substantial, restrictions with the intelligent personal assistant are apparent when it comes to third-party apps like Google Maps, Netflix, and Spotify (unless your iPhone is jailbroken, of course). As an avid Spotify user, it's distressing that I can't use Siri to navigate through the music streaming service's extensive library. In the car, I use Spotify about 90% of the time and it can become increasingly frustrating to chang...

Having to read a bunch of articles and tweets everyday can be tiresome, but if you can have a sweet-ass personal assistant read them for you, you're pretty golden.

This is my first ever clothing haul video and I was so very excited about creating this video for sammydress - you might have heard of this company , who sent me this stuff for review purposes, hence the title "How to Wear the Same Top and Belt in Different Ways and Samydress Haul +Review "

This is such a fun manicure that when I saw for it for the first time on blogs, I just knew I had to try it out. What made me all the sure of the fact was that not only was it eye catchy but also incredibly easy to do .

The title may sound a bit weird to some of you. But when I did this design I really could not resist putting this for a title when a youtube subscriber suggested it to me !

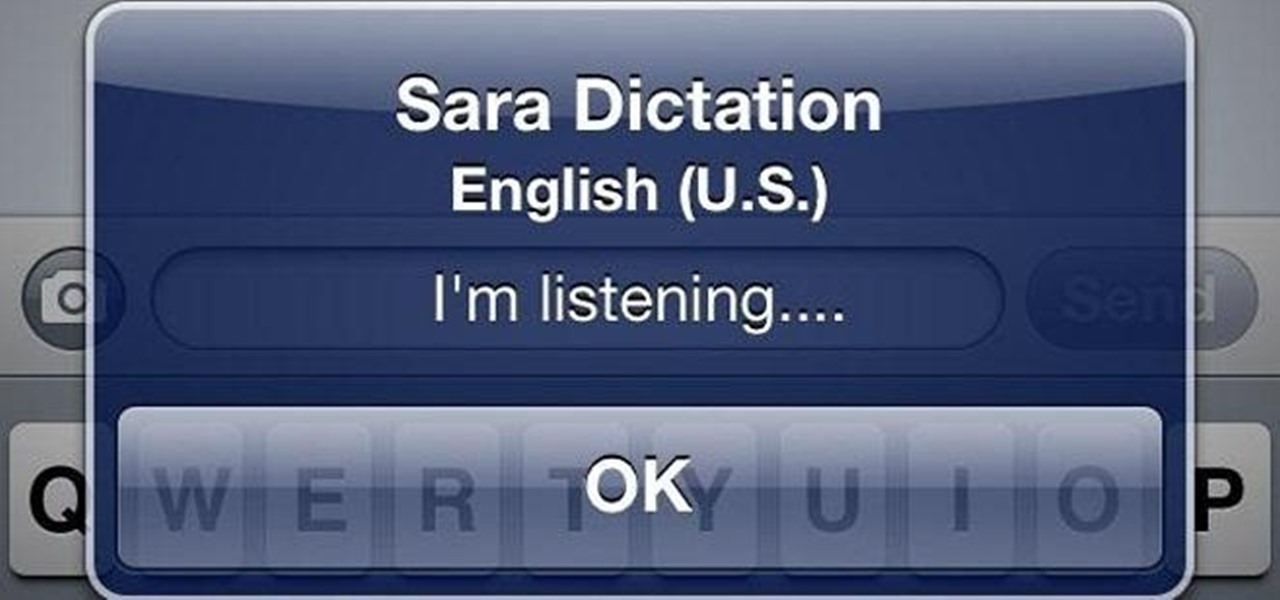
My obsession with Siri is well documented, and after I jailbroke my iPhone 4 recently, I thought I would finally be able to rekindle our imaginary love. But, when I downloaded the Siri Port, I found that the app was buggy and super slow.

This is one of my personal favorite designs from last year, that I wanted to share with you all for this year's valentines day !

In this video i shall be sharing some super amazing glitter nail polish swatches of Elixir nail polish collection!

Starting your own seedlings is a great way to save money, have a wider selection of varieties and gain personal satisfaction. Here are easy to follow tips on getting your seeds off to a great start.

Every so often, a big site will make a change to its terms of service that's not so great for its users—without even informing them—and they (understandably) get really pissed off. Recent examples are Facebook's and Instagram's changes, which resulted in user backlash.

There are plenty of times when it would be nice to be able to give other drivers a piece of your mind, or let them know you're having car trouble so they go around instead of riding your bumper.

As with most things on the Internet, browser cookies can be either helpful or harmful, depending on how they're used. On one hand, they make your experience more convenient by storing information about sites you use frequently. On the other, they can help companies track you across the web or cause your computer to be more vulnerable to attacks on public networks.

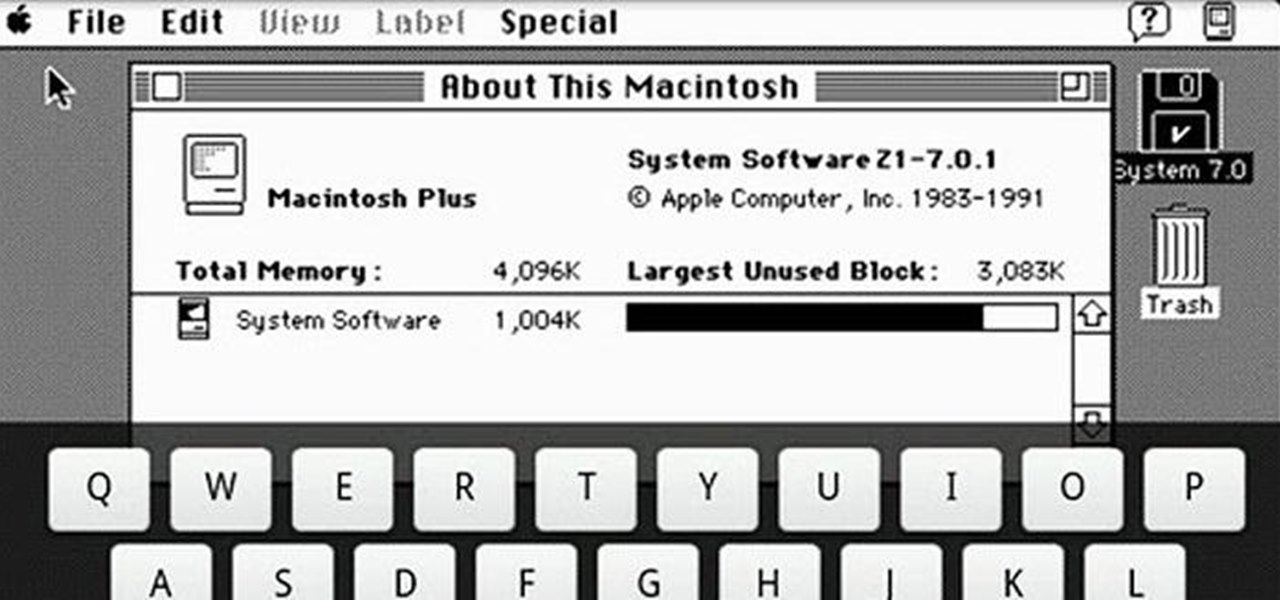
Remember these? Sadly, I don't, but I'm sure someone out there does. Anyone? This monstrosity, called the Macintosh Plus, was introduced in 1986 for the low-low price of $2,599. Wait...what? Almost three grand for that bulky baby?!? With a whopping 1MB of RAM standard?!? Whoa there...

So i'm a 14 year old photography and art student and one of our topics was to create a final piece that reflected the covers of popular magazines. We had to link our magazine cover with our chosen topic and mine was fashion and the environment.

In the Windows 8 Enterprise edition, you can use the Windows to Go feature to travel with Windows 8 OS, personal files, documents, settings and many more. All you need is an external hard drive or USB drive of 32 GB space or more and USB 3.0 support or more for fast Windows 8 booting. We need the storage media of above specification to create bootable USB to access the data anytime by plugging the media into different PC running latest version of Windows 8 PRO or Windows 7.

Google Now is an extremely intelligent personal assistant that automatically updates and prepares the most pertinent information for you on your Android device. Traffic updates, alternatives routes, weather conditions, and other important data is constantly being monitored and updated for you.

Remember how the bad guys in Scooby Doo would always use cut-out portraits to spy on people through walls? Well, unless your landlord is super cool, you probably shouldn't start cutting holes in your wall just yet, but you can make a higher tech version, thanks to NASA employee Mark Rober. Mark used a cheap picture frame and a portrait with the eyes cut out to make the "Scoob Cam," which also doubles as a surveillance device. He used an iPhone and an iPad to start a FaceTime chat, then taped ...

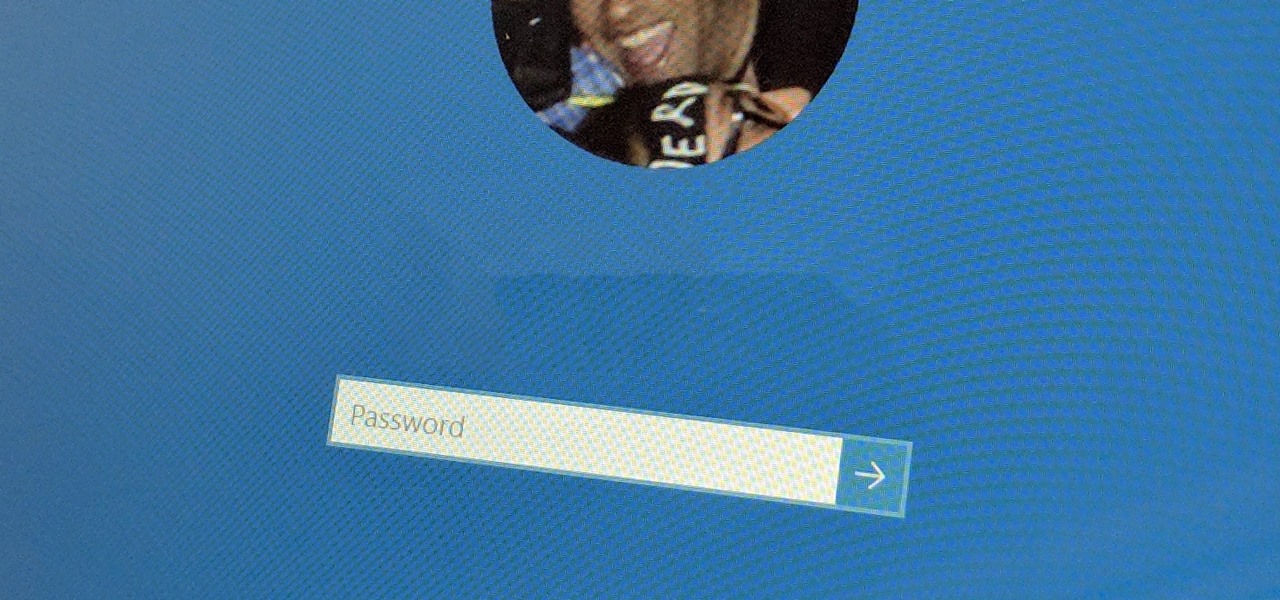
It's good to password-protect your PC to make sure that your personal files, folders, and important documents are safe and can't be modified without your permission. Though, entering the password all of the time before using your computer might frustrate you.

Most of the spam messages are commercial advertisements, phishing websites and get rich quickly messages that asks users to provide personal details and other confidential information.Spam filters in Gmail prevent its users from these spam messages and restrict them to enter in user’s Gmail inbox.Generally, it acts like a firewall between spam messages and Gmail Inbox.Gmail filters detect the sender’s email address and accordingly send the received messages in Inbox or Spam folder.

It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Dried out markers are the worst. They take up space, and for some reason, even though they're totally useless, most of us have at least a few lying around just for the sake of not throwing them out. Luckily, Julie Finn over at Crafting a Green World has come up with a way to repurpose them into alcohol ink, a versatile type of ink that can be used on non-porous materials like plastic, glass, and metal. This is truly a tutorial for the pack rat in all of us. First, a little primer on what you ...

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

As if the world needed one more reason to be obsessed with Shark Week, Volkswagen has teamed up with Discovery Channel to create this awesome "underwater car" that's actually a mobile shark cage.

One of the biggest time-consuming nuisances for any barbecue is prepping corn on the cob. If you've got a lot of mouths to feed, shucking corn is just downright painful, thanks to all of those silk strings that hide in the crevices of the kernel rows.

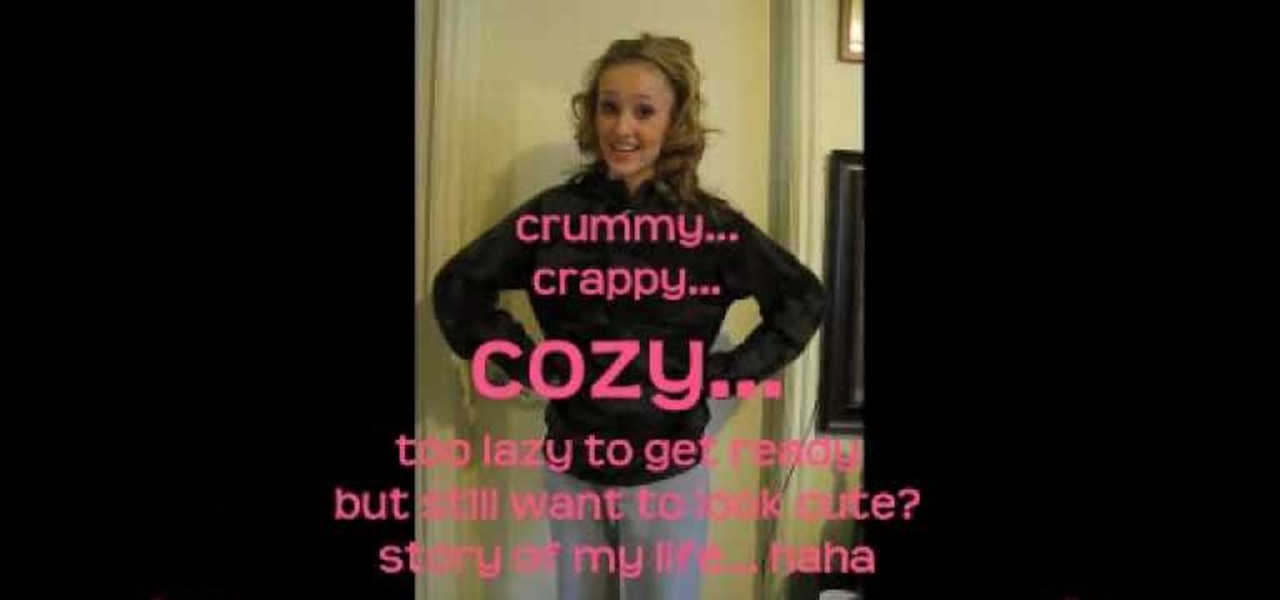
Track suits and Uggs are the way to go if you're feeling lazy, and just want to stay comfortable. But don't give up on looking cute at the same time, because it's totally possible. Watch these tips for feeling crummy and crappy, but looking cozy and cute. You don't even have to style you hair! With just a few changes, you'll go from grubby to cute and trendy.

Redecorating your home can seem like an overwhelming task but it doesn’t have to be. You don’t need a professional as long as take into consideration the key elements such as your budget, the style you want and a color pattern.

Everyone could benefit from shedding a few pounds, but what about those who need to lose a little bit more weight? Exercise isn't an option for everyone, with as busy as our lives are right now. It's hard to go running and do a few pushups when you have a hard enough time scheduling your day already. But if you're looking to shed a couple pounds here and there— without lifting a finger— this two-part video will help you out with some Jedi mind tricks!

In this segment of Southwest Yard and Garden, John White and Bill Alford are going to be talking about fruit production and how to harvest figs in southern New Mexico. Bill starts off by talking about his nine year old Black Turkey tree. He says he digs holes and arbor each spring, then uses half a cup of fertilizer per hole. The roots of a fig tree usually grow out past the outer parts of the tree so it's important to make sure you plant has adequate room to grow correctly. A person can mayb...

If you're like most busy workers, your day doesn't get started until you have your first jolt of fresh coffee. When you are feeling extra sluggish and need a boost, try a strong Cuban coffee that is sure to start your engine.

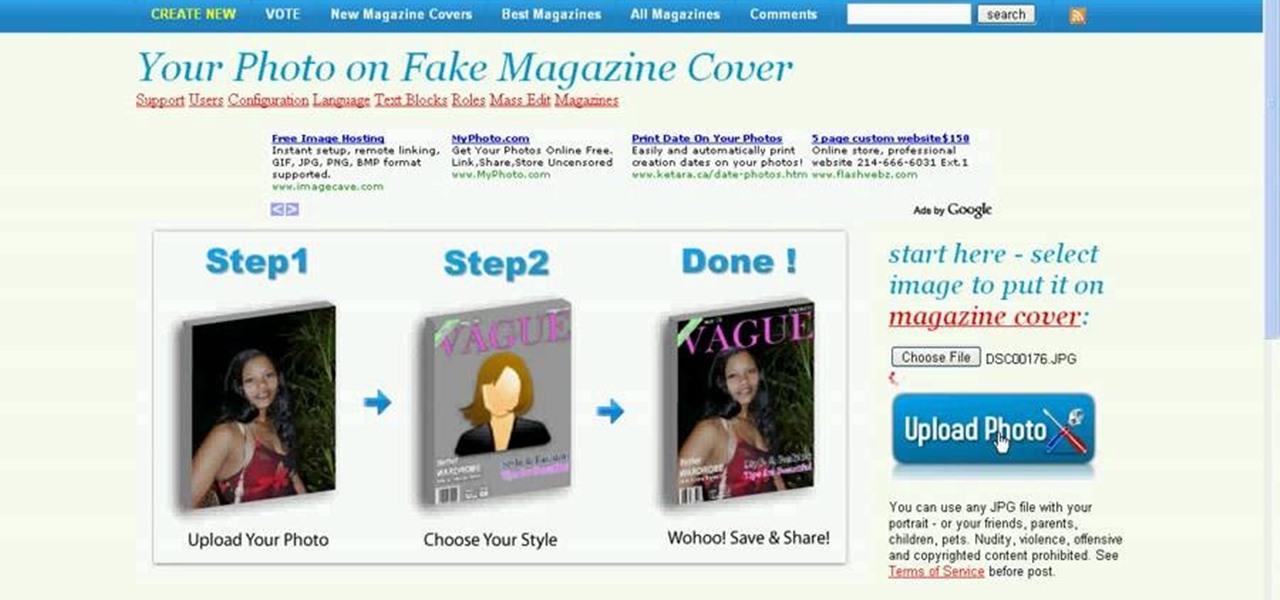
Want to impress your friends by showing that you're hot stuff? Put your face on a magazine. This short tutorial shows you how to create a fake magazine cover on the web, using your own personal pictures. Just go to MagMeNow.

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Add even more personal touches to your crocheted items. This how to video is a tutorial on how to embroider crochet projects using the lazy daisy stitch. You can embroider just about anything with the daisy stitch. Watch and learn.

Are you going out in that little black dress that you've always wanted, but you don't know what to accessorize with? Well, The beauty of the little black dress is that you can accessorize it to reflect your personal style. A fashion designer shows you how to incorporate funky and classy pieces into your wardrobe.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Nothing gets me functioning in the morning better than strong coffee. And if I'm going to start my day with a dreaded workout, that steaming cup of caffeine is the exact motivation I need to get going. Although coffee might not seem like the best beverage to drink before hitting the gym, it actually has a few hidden benefits over water that may surprise you.

No one ever wants to experience pain, whether it's as small as a stubbed toe or as great as recovering from surgery. Yet so much of our lives causes pain, lasting or brief in its form. With a few mental tricks and unusual home remedies, you can relieve some of the most common aches and ailments that arise painlessly.