It seems like every other day there's a new security threat or data leak in the news. Whether it's your credit card PIN or your smartphone's apps leaking your email address, no one wants their personal information out there, especially passwords. And if you use the same email address and/or password for more than one site, the effects of someone getting hold of your credentials can be catastrophic.

Dried out markers are the worst. They take up space, and for some reason, even though they're totally useless, most of us have at least a few lying around just for the sake of not throwing them out. Luckily, Julie Finn over at Crafting a Green World has come up with a way to repurpose them into alcohol ink, a versatile type of ink that can be used on non-porous materials like plastic, glass, and metal. This is truly a tutorial for the pack rat in all of us. First, a little primer on what you ...

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

As if the world needed one more reason to be obsessed with Shark Week, Volkswagen has teamed up with Discovery Channel to create this awesome "underwater car" that's actually a mobile shark cage.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

One of the biggest time-consuming nuisances for any barbecue is prepping corn on the cob. If you've got a lot of mouths to feed, shucking corn is just downright painful, thanks to all of those silk strings that hide in the crevices of the kernel rows.

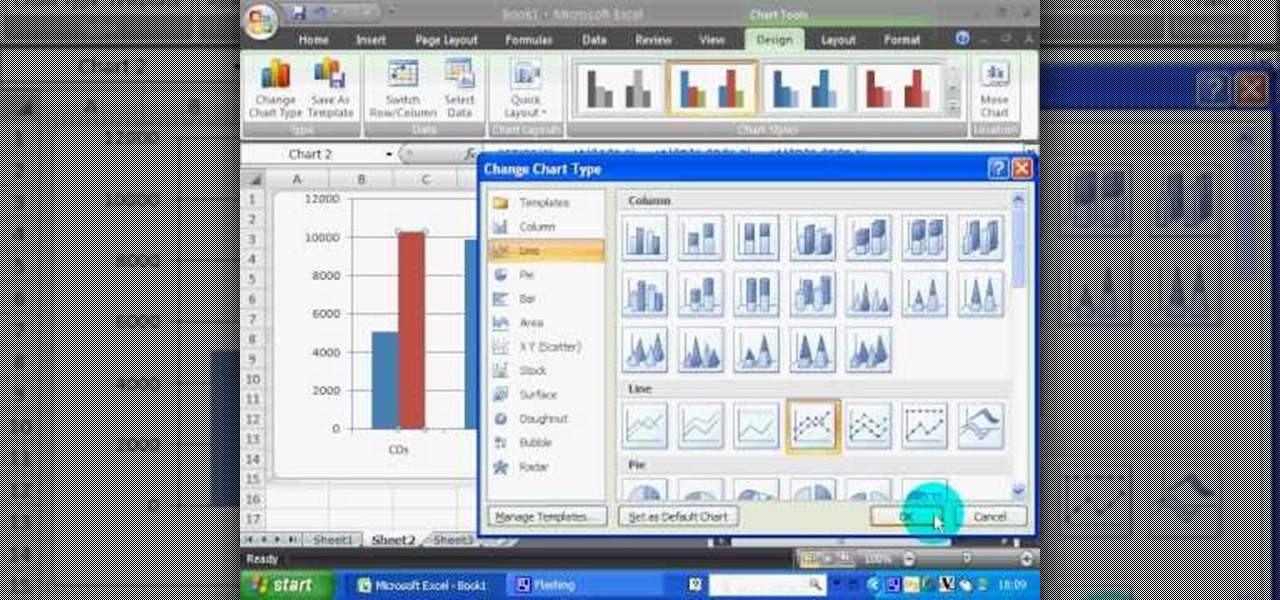
In this software video tutorial you will learn how to create a column line graph in Microsoft Excel 2007. First you type in the data in to the work sheet. Then highlight the data and click 'insert' on the menu bar. Here you select the 'column' option and go down and click on the type of column that you want. And the graph is automatically presented. Now click on 'move chart' and select a sheet where you want the graph to be moved to and click OK. To change any field in the chart in to a line ...

Use the Excel Vlookup function in Microsoft Excel 2007 to look up data in a table. This tutorial looks up the level and value of a product from a stock list using the Vlookup function in Excel.

We know that spring seems ions away, but if you're a gardener then it's time to begin thinking about what flowers you'll be planting to bloom during the spring. If you don't have much garden space but would love a very fragrant bloom, check out this video to learn how to grow lavendr provence in a container.

Corn is everywhere, and there are a large amount of methods for preparing it. If you're a corn on the cob kind of guy, you may be fascinated to know that a microwave is all you need to cook it. Bring the fresh taste of summer to the dinner table in a few short minutes by using your microwave to cook corn on the cob.

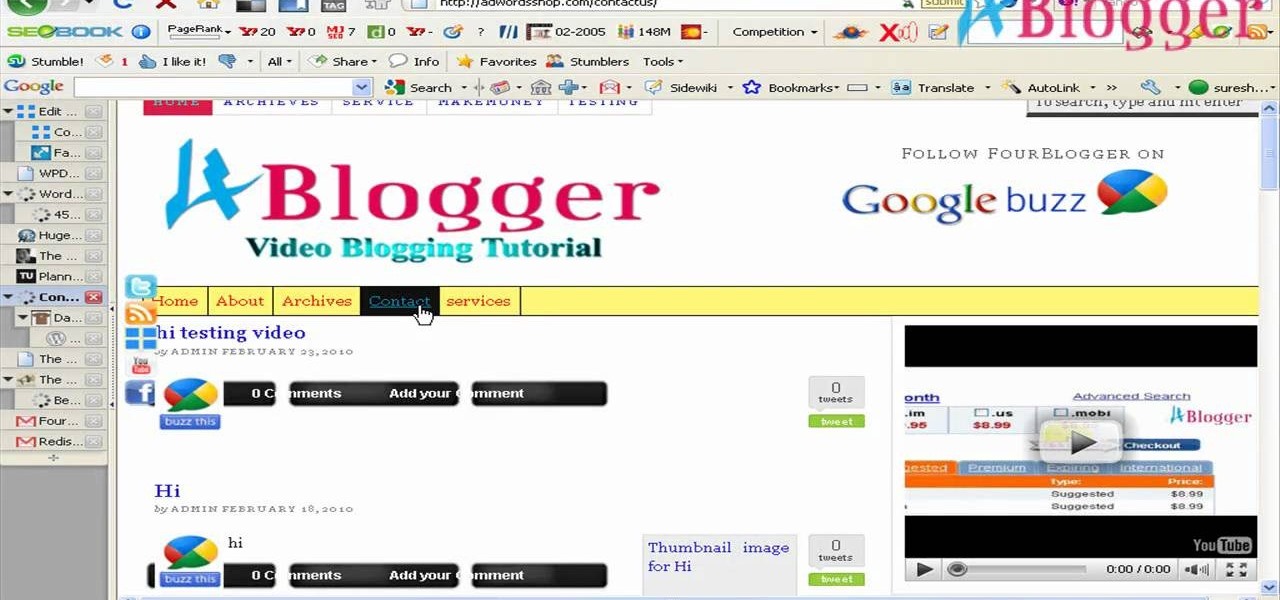
These easiest way to create contact pages for your WordPress blog is with a plugin. Not fuss needed. These two videos attempt to tell you how you can create contact forms in your WordPress blog with the Contact Form 7 plugin. The "contact us" page made easy!

This video shows how to setup the Firefox as your browser for web, on Macbook Pro. First, Open the Safari browser by double-clicking, from the list of Applications. Then, enter the URL of Firefox website, in the URL address field of Safari, to open it. When the website is opened, click the link "Firefox 3, Free download.", which will automatically start downloading. Then when asked to proceed, a message comes, click "Continue". It starts to download Firefox 3. When done, it will open a window...

Do you like to play hockey but have no idea how to skate? Are you more of a summer person than a winter one? Do you live somewhere where ice is hard to find? Well, then check out this tutorial and learn to play street hockey! Get all the fun of hockey without the cold, icy mess!

This video explains how to send the Text message to any where specifically to mobile using Yahoo mail. To do that first type the "www.yahoo.com" or "www.yahoomail.com" in the browser. And then choose the Mail option from the front page of the yahoo website. From that click the sign in option, and give your Mail id and password in the yahoo sign in page now you will logged into your yahoo account. Into your account you will have the "New" menu option on left to corner. From that you have to ch...

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Game terrain dioramas are an essential playing field for miniature war games, like Warhammer 40K or Lord of the Rings games. While these terrains can be purchased ready-made, make your own to get the exact look desired. Watch this hobby how-to video and learn how to build a game terrain diorama for Warhammer 40K.

Identifying snakes is difficult to do accurately. Identify snakes using field guides and the Internet with tips from a certified animal control officer in this free reptile pets video.

Defending against the dribble is one of the hardest things to do on a soccer field, get expert tips and advice on footballing techniques and skills in this free video.

Gmail uses TLS, or Transport Layer Security, by default for all email communications, so all of your emails will use the standard encryption as long as the recipients also support TLS. But there's a way to add even more security to your Gmail emails, and you can use your iPhone's Mail app to do it.

"I want to make video games" — Is there anyone who hasn't ever thought that? It's almost universal among gamers to want to get on the other side of the screen and design the games themselves, especially those of us who have played less than impressive games and thought that we could do a better job. But it's hard to know where to start — or how — when it comes to creating our own games.

Now that more and more people are working on their personal computers and smartphones as opposed to their work computers as a result of the coronavirus outbreak, hackers are having a field day. Unencrypted home networks and public WiFi connections make it incredibly easy for cybercriminals and even government agencies to access everything from your browsing history to your banking information, and a Virtual Private Network (VPN) is the only way to stop them.

Since its founding in 1984, Cisco Systems has been a global leader in information technology. From networking hardware and software to domain security and energy management, the company dominates the IT field.

More and more tech-savvy leaders are flocking to the lucrative and exciting world of project management thanks to the high-pay, analytical environment, and nearly unparalleled flexibility. But this means that competition for the best positions in this dynamic field is fierce. If you want to stand out from the crowd, you're going to need to have more than a few base-level certifications on your résumé.

The term "hacker" often has negative associations attached to it, yet the world is in dire need of professionals with hacking skills. White hat hackers are ethical computer hackers that use their hacking skills to pinpoint network vulnerabilities and patch them up before they can be exploited by the bad guys.

If you're reading this, you're likely a tech-savvy coding pro whose analytical talents are mostly applied to designing apps, cracking passwords, and infiltrating networks — all of which are admirable activities for both aspiring and seasoned white hat hackers. But there are other profitable ways that you can put these types of skills to use, namely in the world of investment and trading.

With Samsung's One UI version of Android, it's easier than ever to take a screenshot and quickly edit the captured image. However, the downside to that convenience has manifested itself in an overlay ribbon that can also get in the way.

If you've ever wanted to track down the source of a Wi-Fi transmission, doing so can be relatively easy with the right equipment.

The cosmetics brands are among the earliest adopters of augmented reality, using virtual try-on tools to preview shades of makeup before buying.

After drawing attention from nostalgic Gen Xers for its Motorola Razr reboot with a foldable screen, Lenovo has a new augmented reality smartglasses concept that the company hopes will also turn some heads.

Restarting your iPhone can cure software glitches, but it should only be done as a last resort if your device has a semi-tethered jailbreak, because it will disable any tweaks you've applied. Luckily, your jailbroken iPhone has a faster alternative to rebooting to help you troubleshoot and make changes on the fly.

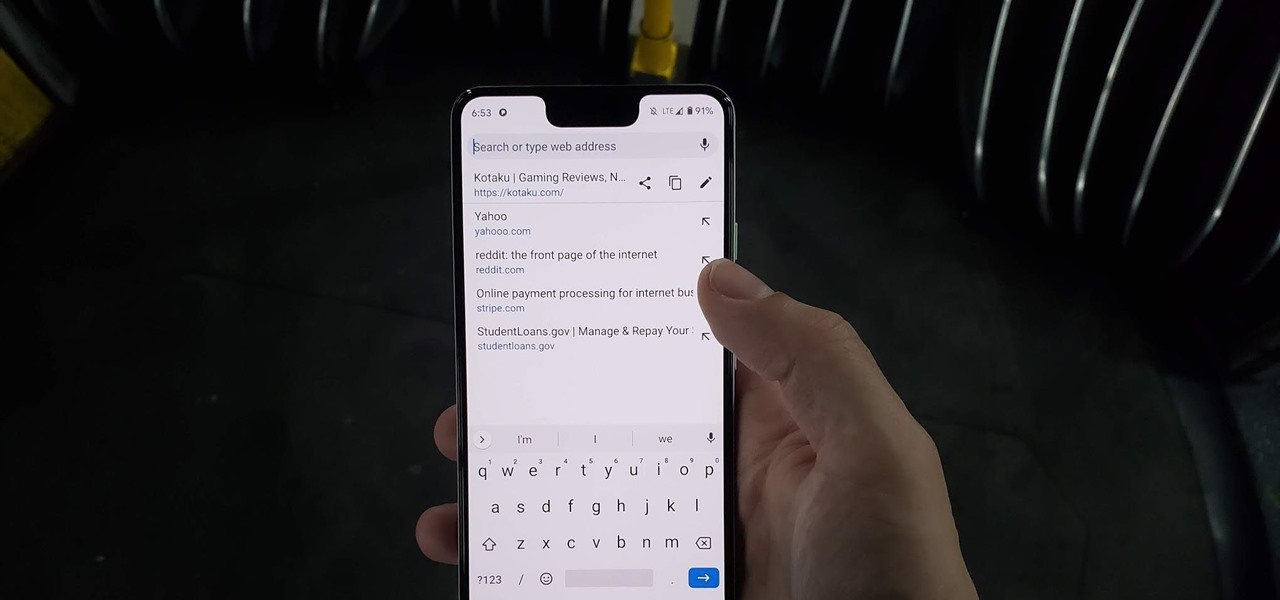
Chrome has just introduced some new UI elements for web exploration. The new URL bar is not intuitive. But once you get to grips with it, you will be so much more efficient in your address bar editing, pasting, and navigation.

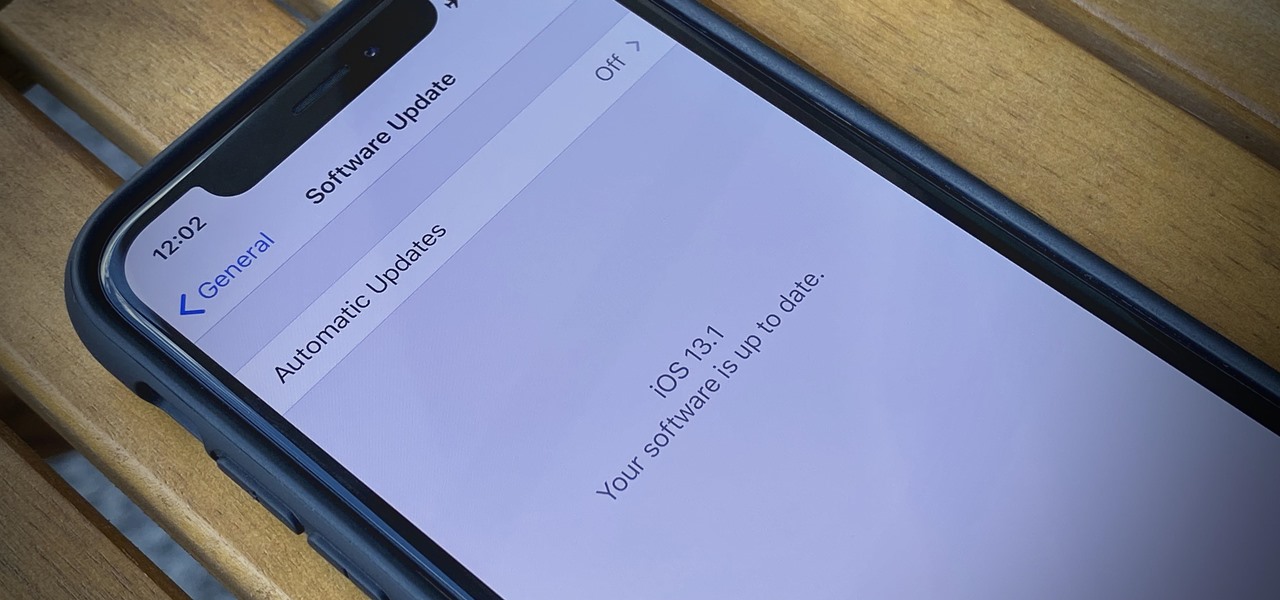
If you're still working your way through the hundreds of features and changes that iOS 13 brings to your iPhone, you might be a bit surprised to learn that your device is now out of date. While Apple only dropped the big update for iPhones on Thursday, Sept. 19, the company has already released its successor. All iOS 13-compatible iPhones can now update to iOS 13.1, out today, Tuesday, Sept. 24.

Microsoft has unveiled practically every detail of the HoloLens 2 except for when eager developers and enterprise customers can expect to receive the device.

It appears that the floodgates of consumer-grade augmented reality smartglasses from China are now open, with Mad Gaze being the latest company to rush its product through.

While Modiface, YouCam, and others have been playing in the virtual make-up marketing pool for a while, here comes Google ready to splash down with a cannonball.

It appears that the Project Aero 3D content development tool isn't the only augmented reality project that Adobe has in the works.

Under the rocket's red glare and the bombs bursting in air, the Statue of Liberty is swaying in celebration this Fourth of July thanks to Snapchat.

Metadata contained in images and other files can give away a lot more information than the average user might think. By tricking a target into sending a photo containing GPS coordinates and additional information, a hacker can learn where a mark lives or works simply by extracting the Exif data hidden inside the image file.