A few days ago, Russian hacker Alexy Borodin found a way to get free in-app purchases on an iPhone or iPad. In-app purchases include things like items and power-ups for iOS games, as well as subscriptions and "premium" memberships for certain apps.

Playing backline is a key position for rugby players on the field. Learn how to play rugby, including rules and skills, in this video rugby lesson.

Playing backline in rugby is an important position on the field. Learn how to play rugby, including rules and skills, in this video rugby lesson.

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

Would you know what to do if someone ingested poison? Equally important, would you know what not to do?

Rumors, gossip, exclusion. Mean girls have a lot of weapons in their repertoire – here's how to combat all that nastiness.

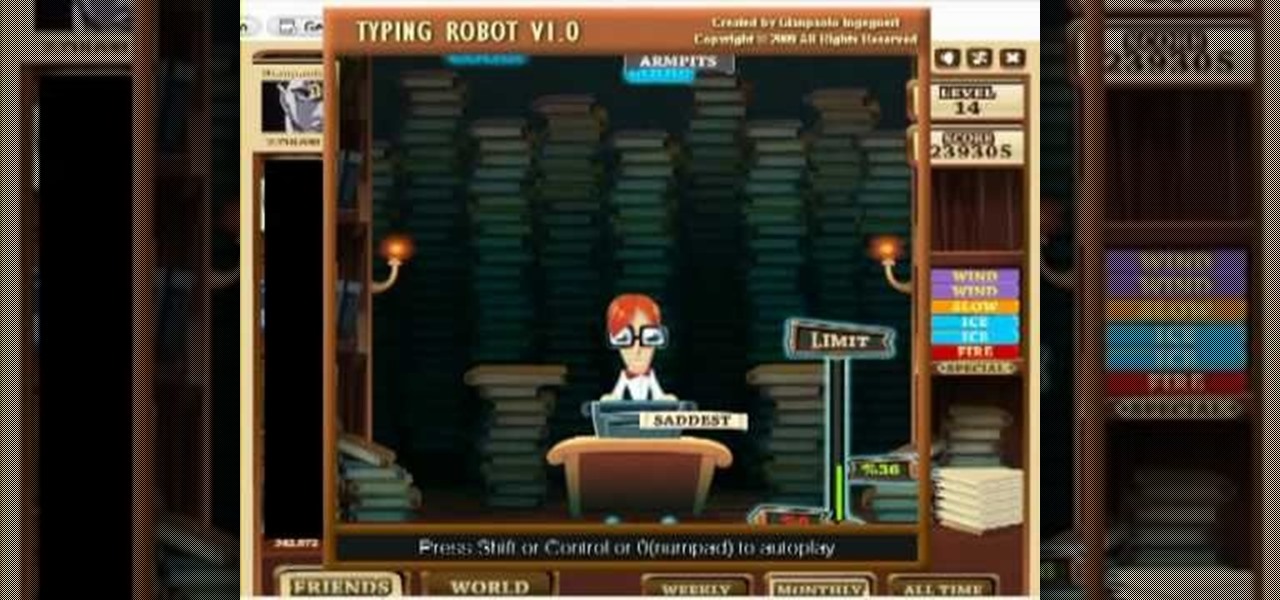
http://www.texturemind.com/post463/ TypingRobot is an artificial intelligence studied to increase your points record with the Typing Maniac game on Facebook. It can recognize several labels because it uses a powerfull OCR system (tesseract) and some principle of word correction. With this program you can make millions of points without problems (my personal record is about 2.700.000 points).

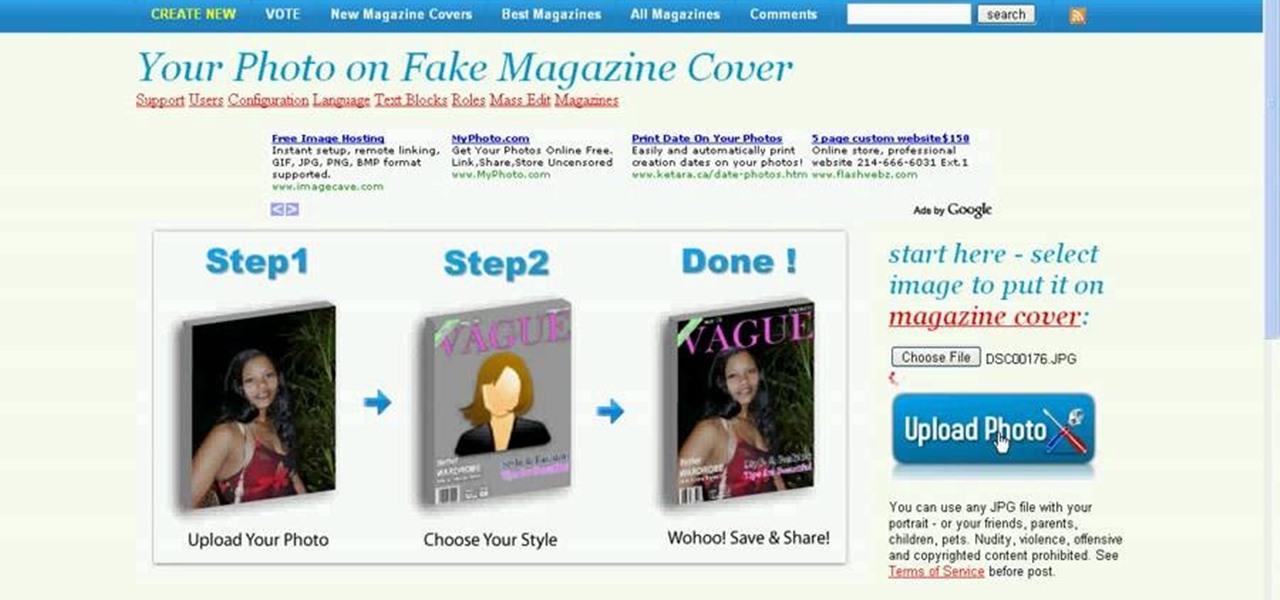
Want to impress your friends by showing that you're hot stuff? Put your face on a magazine. This short tutorial shows you how to create a fake magazine cover on the web, using your own personal pictures. Just go to MagMeNow.

Add even more personal touches to your crocheted items. This how to video is a tutorial on how to embroider crochet projects using the lazy daisy stitch. You can embroider just about anything with the daisy stitch. Watch and learn.

Are you going out in that little black dress that you've always wanted, but you don't know what to accessorize with? Well, The beauty of the little black dress is that you can accessorize it to reflect your personal style. A fashion designer shows you how to incorporate funky and classy pieces into your wardrobe.

Instead of just going for a walk through the outdoors, try adding in the rewarding hobby of bird watching. The song sparrow is a great bird to look for on perches and will vary in appearance across the US.

If your not sure how to steam your media files to your Playstation3 this video will explain three different ways to achieve just this. Your options will include using a thumb drive, a personal web server or get the appropriate software.

Bird watching is a great activity to do on your own or to spend time with the whole family. Look for the habitat, coloring, behavior and call of this beautiful bird and enjoy its beauty and soft cooing.

Nothing says you care like a hand-made card. Show that special someone what they mean to you or just have fun with this cute arts and crafts project. Get your markers and colored pencils. Get your glitter and glue. Get creative.

Purchase the necessary equipment for this project. Pumice stones can be purchased at any beauty supply store. Chlorine can be purchased from any household supply store. Sodium bisulfite can usually be found at hobby stores. Obtaining the industrial washing machines for personal use is the hardest step. Call local cleaners to see if they will allow you to use their machines. Soak the pumice stones in chlorine overnight. This will allow them to soak up the bleach and create a good absorbency fo...

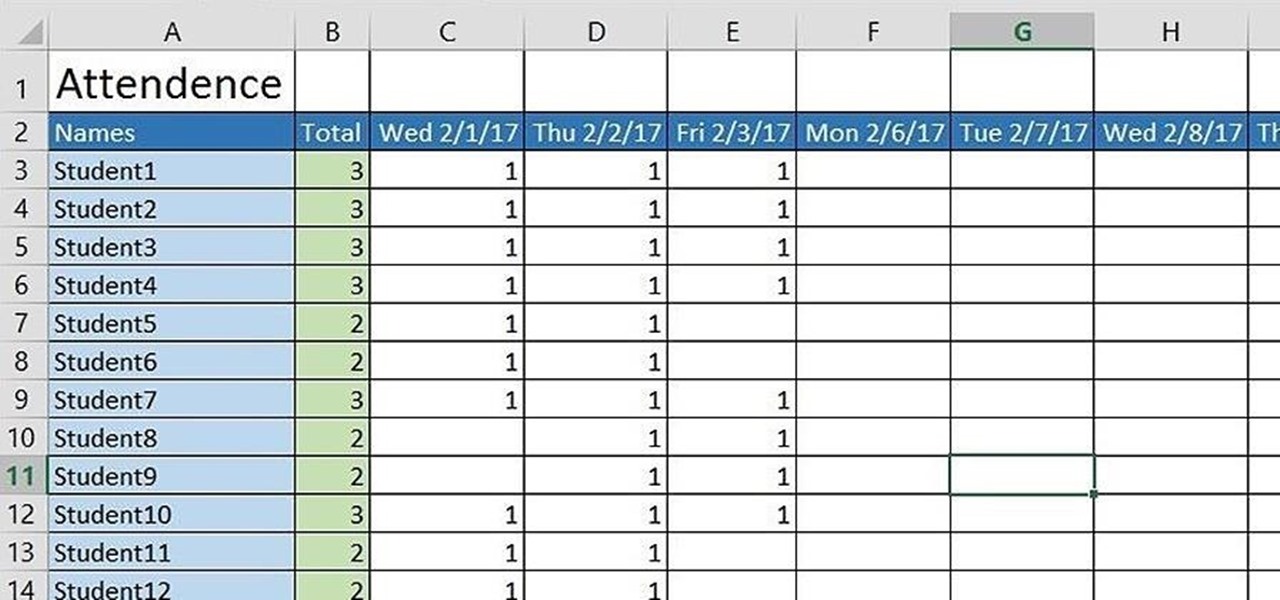
If you're a teacher in any type of school, whether it's high school, college, or middle school, it's imperative that you keep an attendance sheet. The paper and pen route can get pretty messy, and very disorganized, and that's where Microsoft Excel comes in. With this software, you can create a simple yet functional attendance sheet to keep track of your students.

It's easy to make a peck of pickled peppers – or any other vegetable – with this basic recipe. You Will Need

Sure, they have personal trainers and chefs to help them shed their postpartum pounds. But here are a few of their other secret weapons.

A good party guest should live by this motto: Ask not what the party can do for you, but what can you do for the party!

If your new window treatments include blinds, save the hefty installation fee by hanging them yourself.

Lower back injuries are common but preventable. Learn simple lower back exercises to increase strength from tips from a personal trainer in this free exercise video series.

The signal bars in your iPhone's status bar are great visual indicators for knowing how good your cellular reception is, but they're not very accurate. Instead of showing the actual amount of signal you're receiving, they just give you a general range, and you'll have no idea if three out of four bars is actually a good connection or not. But there is a trick to see the real numbers.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

As government officials scramble to contain the new coronavirus outbreak with bans on large gatherings, travel restrictions, and school closures, the rest of us have to worry about how we're going to safely purchase water, toilet paper, groceries, and other household goods during the global COVID-19 pandemic.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

Your phone's keyboard is one of the most commonly used apps. Whether you're typing out status updates, sending private messages, or just bombarding everyone in sight with as many emoji as you possibly can, you probably couldn't get by without a good keyboard app.

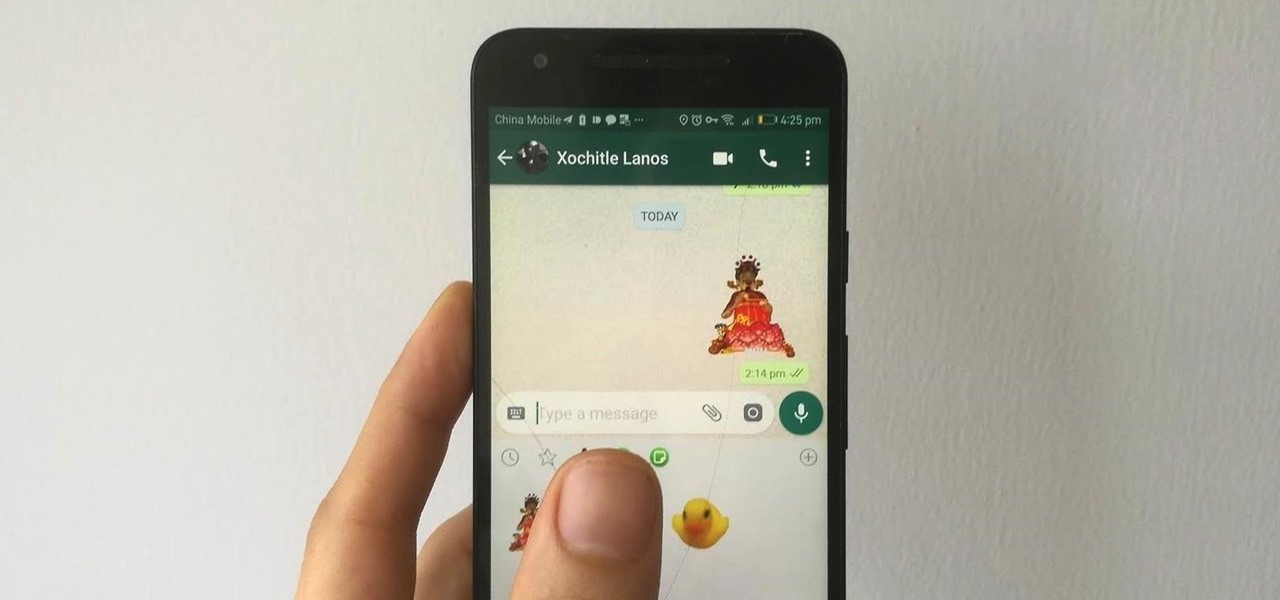
WhatsApp stickers can make your chat more fun. The stickers that come with WhatsApp are fine, but they're standard and accessible to everyone. What if you wanted to show off unique stickers that your friends haven't seen? To take things to the next level, you can create your own WhatsApp Stickers.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

Passwords and data stored in web browsers are extremely valuable to hackers. If not for financial gain, black hat hackers may still leak your passwords and personal information for amusement. Never undervalue what you're worth to a hacker.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

Despite their sometimes fluffy reputations and occasionally ethically compromised viewpoints, tech evangelists are important, don't let anyone tell you otherwise. The right passionate voice behind the right technology platform or piece of hardware can sometimes spell the difference between fostering a community of potential users and watching a product die on the vine.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.

I have a personal rule when it comes to an app's interface: If it doesn't follow Android's design guidelines, it was probably written with Apple's iOS in mind first and foremost.

The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can carry much more than a simple voice conversation.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...