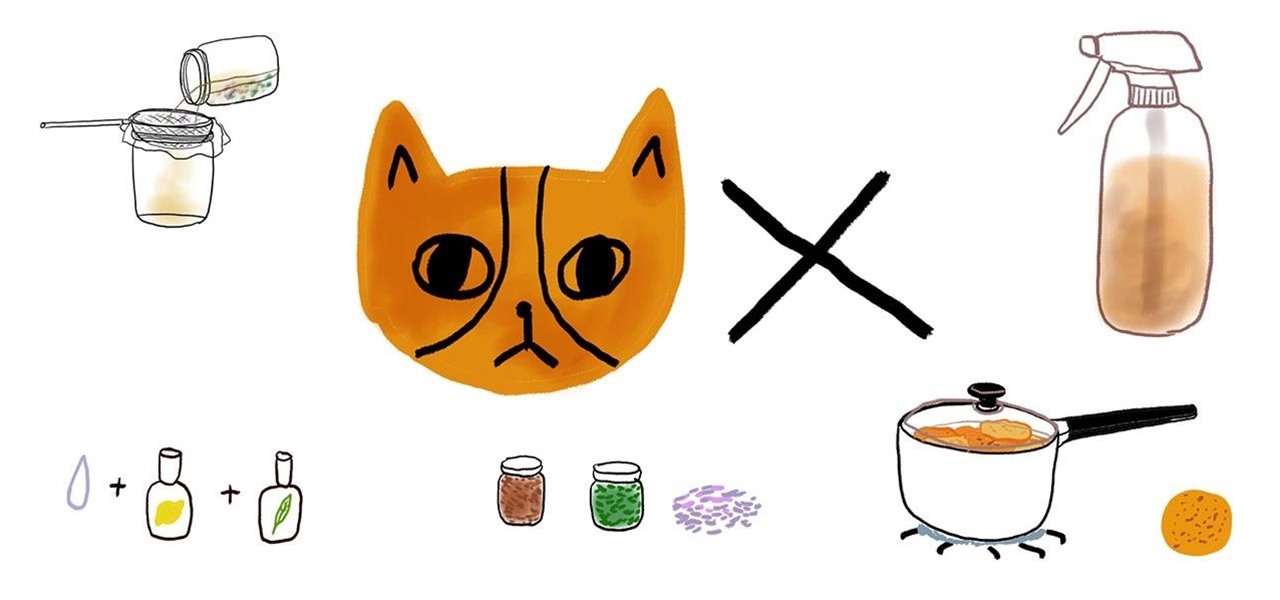Between school, work, and your personal life, there's a good chance you have multiple Google accounts. Most Google apps let you log into all of them simultaneously to receive applicable alerts when they arrive. Well, there's a dead-simple way to switch between these accounts, and it just takes one swipe
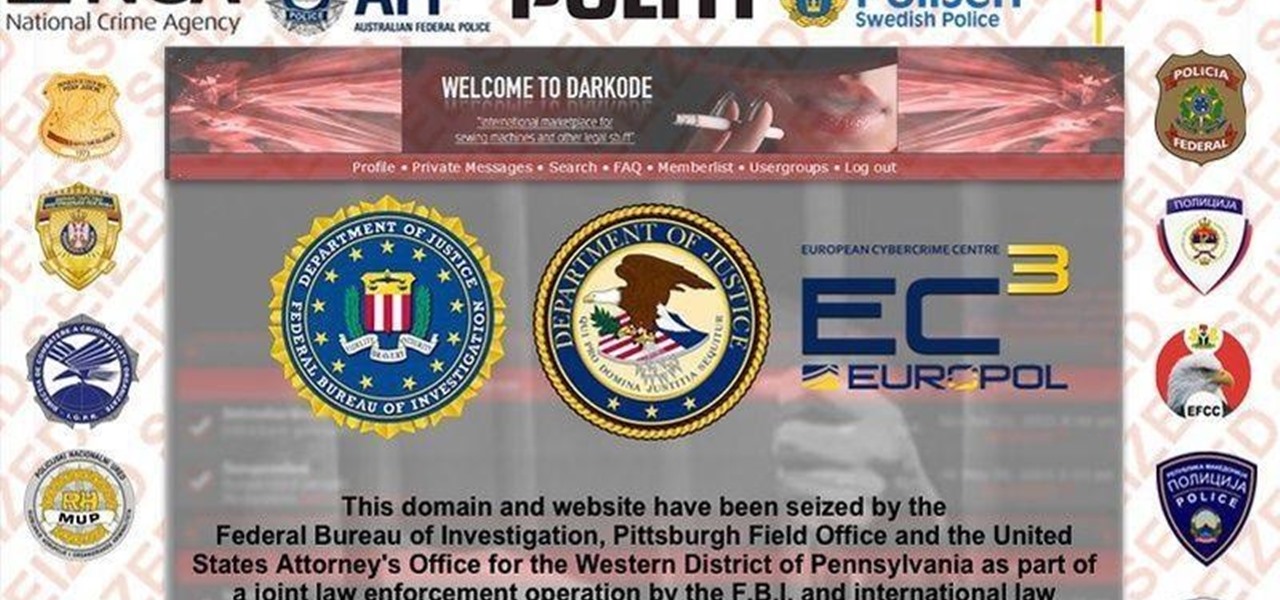
FBI has taken down a notorious hacking forum called "darkode" where cyber criminals bought, sold and traded hacked databases, stolen bank accounts, and malicious software that steal information from other computer systems and helped each other to infiltrate other computers. The FBI called the site one of the most serious threats to data security in the world. criminal charges has been filed against 12 individuals who were associated with the forum and the investigation is still ongoing, more ...
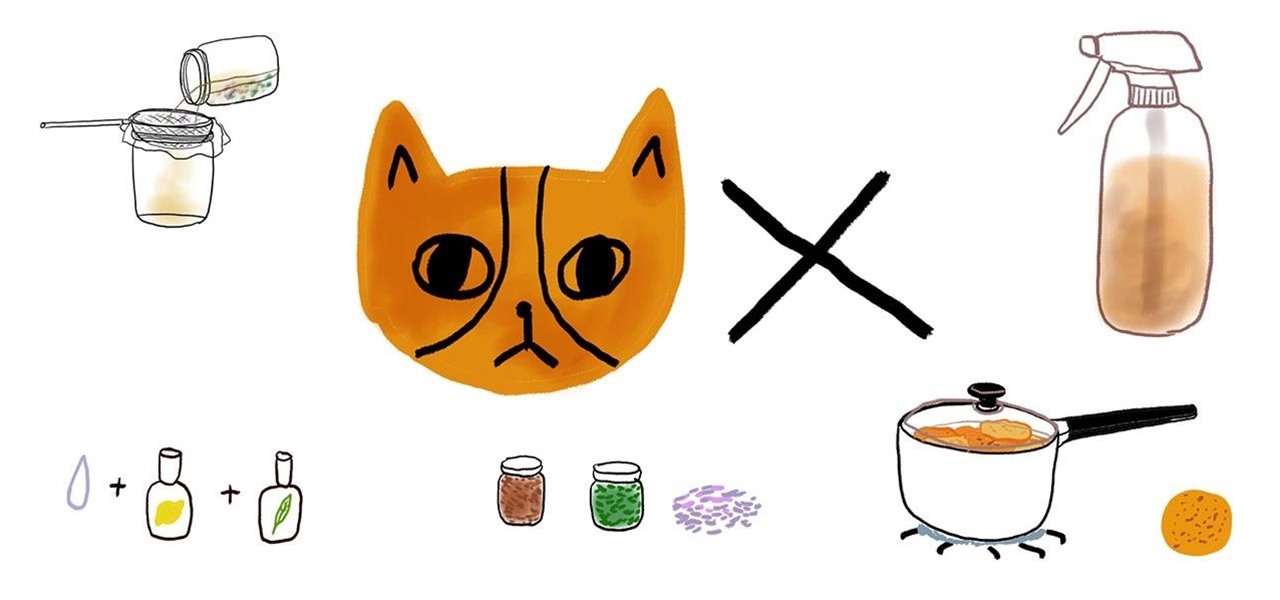
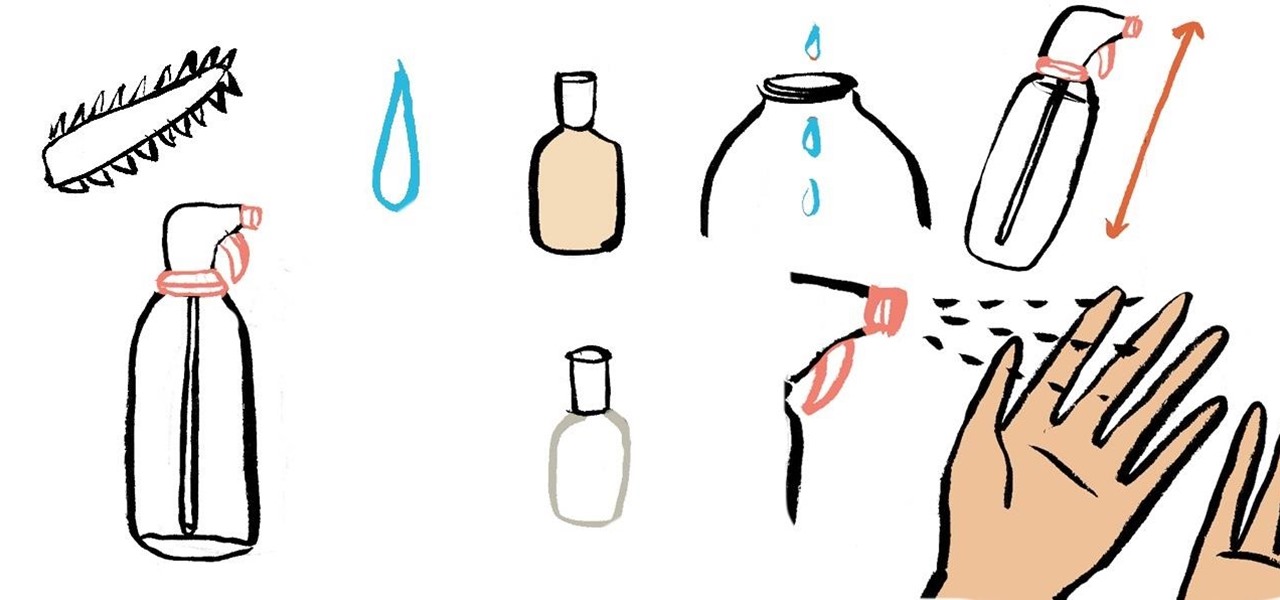
Whether you want to prevent your cat from scratching up the couch or deter stray cats from using your front yard as their personal litter box, a DIY cat repellent spray can go a long way in keeping unwanted furry guests away.
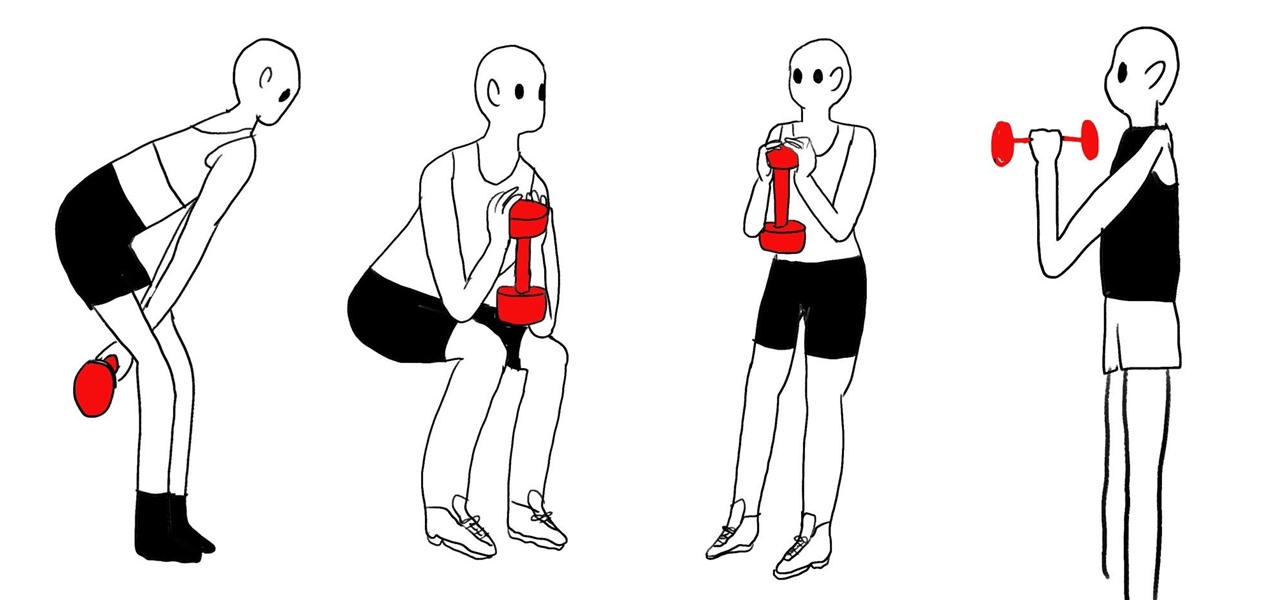
You can certainly exercise at a fancy gym with a personal trainer and state-of-the-art equipment if you have the money and time to do so. However, if you are on a budget and don't want to waste extra time getting into your best gym clothes and driving, you can give yourself an intensive workout at home using only one dumbbell.
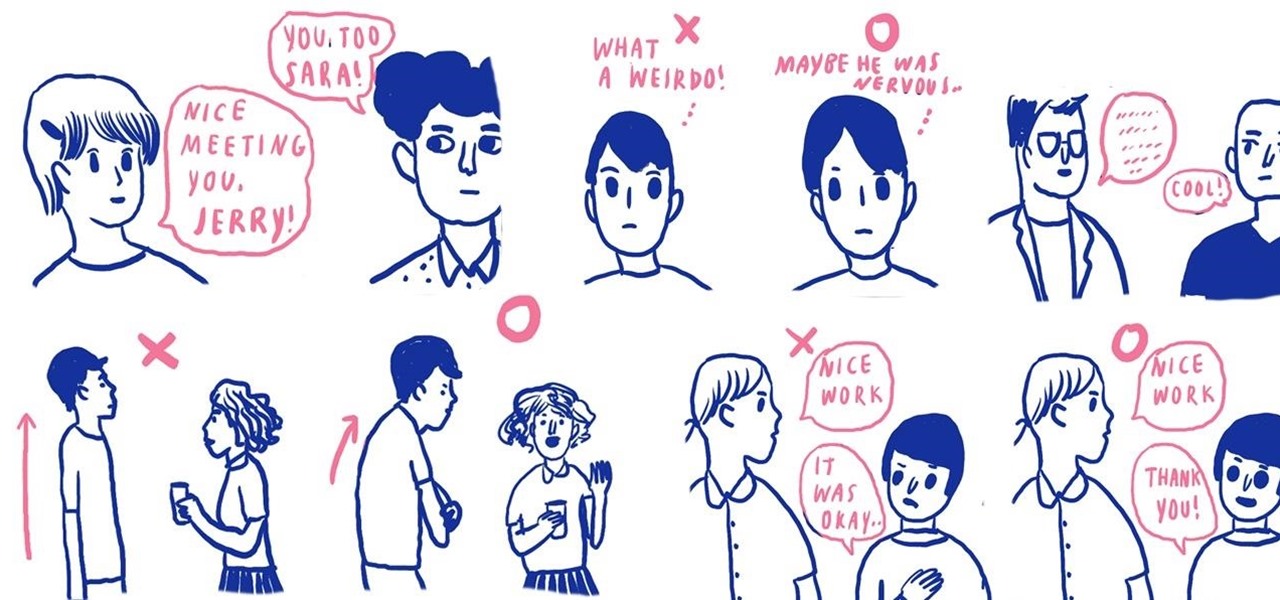
If you're in a social situation where you're meeting a lot of new people and you want to make the other person feel at ease, subtly mirror the other person's body language and make a point to say the other person's name.

Whether it's your credit card, your parents' new zip code, or a new work phone number, number sequences are everywhere. Sometimes it's important to actually remember them instead of always relying on a smartphone or the internet to remind you.

Hate germs and hate spending money on expensive hand sanitizer bottles? With a few simple ingredients and a little extra time, you can whip up your own all-natural, DIY hand sanitizer that will make your hands feel squeaky clean anytime and anywhere.

If you're using an Android phone or tablet with Google Now, then you and your little ones are in for a little treat. Just tell Google, "Let's Go Caroling," and watch the holiday metamorphosis as your device changes into a personal, karaoke caroling machine. Just in time for the holidays! Choose from one of five famous Christmas songs (Jingle Bells, Up on the House Top, Deck the Halls, O Christmas Tree, and We Wish You a Merry Christmas), press Play, then keep up with the bouncing ball as it h...
I make silk flowers for personal use as of now. My sister suddenly passed away 18 yr ago, & I try to make sure she has a very nice flower arrangement for every season. I dont have alot of money but she deserves to have a nice flower arrangement. She was only 19 when she passed so I have been doing this for 18 yr. I would like to make a business of this , I just dont know how to get started

Forget the Segway, you don't even have to stand anymore thanks to Honda's U3-X. This self-balancing unicycle relies on an inclinometer instead of gyroscopes to keep the rider balanced. The personal transporter even allows the user to travel forward, back, left, and right thanks to the Honda Omni Traction (HOT) drive system. This automatic unicycle gives a whole new meaning to taking it easy. Check out this CNN video for a further demonstration of the Honda U3-X.

Wikipedia's definition of dice stacking: "Dice stacking is a performance art, akin to juggling or sleight-of-hand, in which the performer scoops dice off a flat surface with a dice cup and then sets the cup down while moving it in a pattern that stacks the dice into a vertical column via centripetal force and inertia."

Self proclaimed "Paper Airplane Guy", John Collins, is the master of paper crafted flight. Collins hosts workshops for Corporate America, using the paper airplane as a metaphor for success:

Papercraft guns are the new origami. The new origami for boys, that is. WonderHowto and YouTube are chock full of paper gun tutorials. Many models are simple, but some are impressively realistic, not to mention functional. My personal favorite (unfortunately no tutorial) is the homemade Desert Eagle .50 cal by YouTube user Changmobile.

Ok, so you clicked through and there's no Britney Spears. I would have used an image of the mysterious Molly Lewis, aka, sweetafton23, but you can barely see her face in her ukulele cover of Britneys Spears' pop classic, "Toxic".

This summer's Jell-O Mold Competition at Brooklyn's Gowanus Studio Space yielded edible facsimiles of jewels, caviar, cheeseburger and fries, chicken, eggs, and "real brochettes ensconced inside Jello-O that simulated plastic wrap."

Hovercrafts! Make your own magic carpet ride! Find your inner George Jetson! The World's Hovercraft Speed Record was set on September 18, 1995 by American Bob Windt. He got his air cushion vehicle up to a speed of 85.87 mph!

Coolio slammed onto the music scene with Fantastic Voyage and Gangster's Paradise in the mid 1990's. His persona has ever been an iconoclastic combination of Compton hood and class clown.

Did you know there is hidden data in your digital pictures? Well, there is, and that data might be a security risk to you. Think back at all of those pictures you're in and are connected with. I'm sure some of those you'd like to distance yourself from. And surely you wouldn't mind checking out the metadata in a few of those images. In this article, we'll be going over how to do just that.

Facebook's new Timeline feature has been rolling out gradually since its unveiling in September, but yesterday it finally became available to Facebookers everywhere. It's even available on your mobile device, too. Those who want to upgrade to the radical new profile design can do so by simple logging into their Facebook account and visiting the About Timeline page on Facebook.

It's a question I've been pondering a lot lately. Technically, children under the age of 13 are not allowed to join Facebook. But according to a Consumer Reports in May, 7.5 million children 12 and younger are already on the site. Currently, federal law prohibits websites from collecting personal data from children without parental permission. The Children's Online Privacy Protection Act, or COPPA, as it is more commonly known, has been in effect since 1998, but has not been updated since.

Muay Boran Muay Boran (Ancient Boxing) is an all-inclusive term for the ancient boxing arts of Thailand, from which modern Muay Thai was born. In the old days, fighters would wrap their hands with strips of twisted hemp cloth or hemp rope. Although it is commonly thought that fighters would dip their wrapped hands in broken glass, this is largely a myth. They did, however, dip their hands in water in order to harden the rope.

Learn how-to use the Fiskars Personal Paper Trimmer for your paper crafts. Use the Fiskars personal paper trimmer.

Last week's social engineering phone calls were a blast. We made some friends, and even some enemies. We scored cheap food for some buddies, made some phone bills disappear, and even got a few people some free pizzas. So overall, it was a very successful night. In light of its success, I figured we'd all do another one!

This is the first official announcement for a new weekly activity on Null Byte for the community to participate in. Starting next week, depending on how much traffic we get doing it, we are going to start doing live social engineering calls via Skype. I've made a list below so that you can get a feel for some of things we'll try to accomplish in these calls.

These days, I keep multiple browsers open so I can keep track of all my work and personal items. As a staff member of WonderHowTo, a lot of my work is done through our Google Account, which is separate from my personal Google Account.

Earlier this month, game developer David Braben and his Rasberry Pi nonprofit foundation revealed a $25 USB PC. The computer can connect to an HDMI monitor on one end, and a USB peripheral on the other (such as a keyboard or a USB hub). You can use the USB hub to connect multiple items, such as a keyboard, mouse, printer, USB ethernet/wireless, creating a fully functional computer.

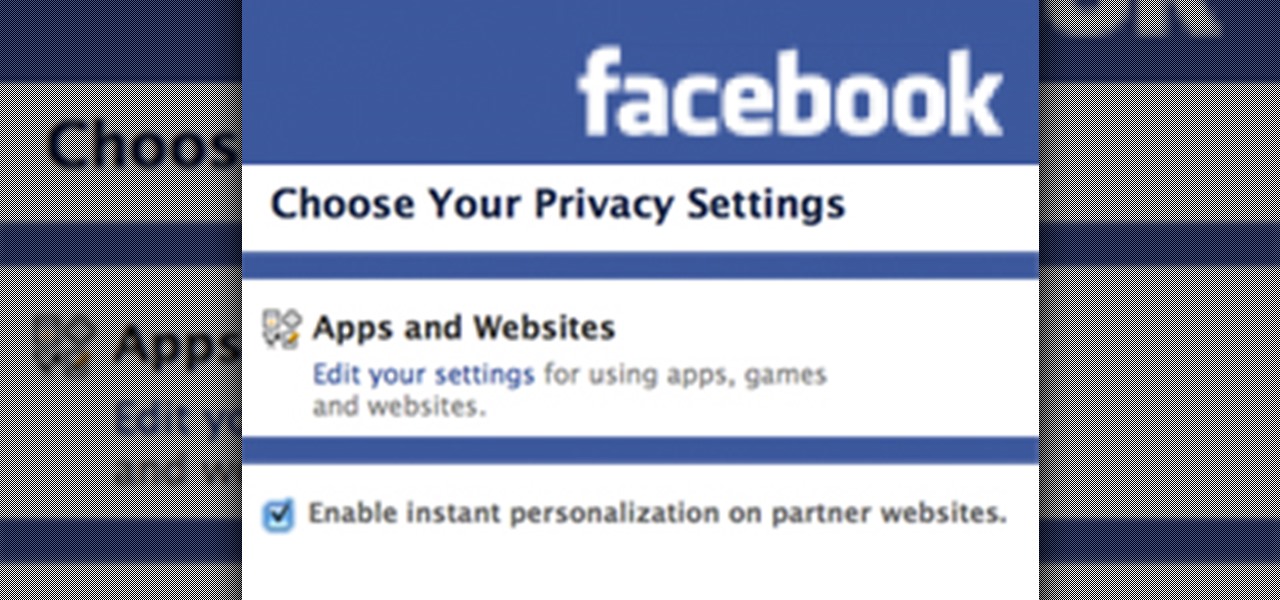
Instant Personalization. If you have a Facebook account, you've probably heard of it by now. If not, you need to educate yourself— and fast. Because they recently made some changes, affecting your privacy settings.

Basic Tips on Creating a Last Will and Testament To say that people do not like talking about composing their last will and testament documents is a reasonable assessment. But for preparing what lies ahead in the future, it is necessary to know what it contains and what it does once the owner of the will passes away.

Check out this interactive video tutorial from Verizon Wireless on the Samsung i730 mobile phone. If you have just purchases this sleek cell phone, here's your chance to learn everything you can possibly know about it.

Outside the realm of politics, where opposing sides are quite passionate and quite disagreeable, there are few areas in our society quite as divisive as Twitter. People who like Twitter love Twitter and are relentless in trying to co-opt the people they know into joining (this is both altruistic and an unsubtle attempt to boost followers).

A few weeks ago, I wrote about why I think streaming music services like Rdio.com are better than Apple‘s iTunes Music Store. This week, I follow up with a how-to about Rdio for Mac, a desktop music player that streams music from your Rdio.com account. Even though Apple is introducing new iTunes features, I think you will find Rdio for Mac a much more affordable option—especially if you like to listen to new music on a weekly, or even daily basis.

Movies like to show hackers breaking passwords with fancy software and ludicrous gadgets. The reality of busting passwords open is much more mundane. Simple as it may sound, most passwords are broken purely by guesswork. Check out this infographic from ZoneAlarm, as well as this list from the Wall Street Journal of the fifty most common passwords gleaned from the 2010 Gawker hack. If your password is on one of those lists, you need to change it. Right now.

The holiday season means you're going to be doing a LOT of entertaining and a lot of going to parties where you'll be expected to offer up a thoughtful hostess gift. While you could always make a last minute run to the store to purchase boxed chocolates or a nice bottle of wine, it's so much more personal to make something.

You never know when you may need to sharpen an axe... and who better to learn from than the Boy Scouts? Brace the axe head on the ground between a log about 6" in diameter and two woooden pegs or tent stakes. Sharpen your axe with an 8-10 inch mill bastard file. Be sure to wear leather gloves. Make a knuckle guard out of leather, plywood, or an old inner tube. Place the file on the edge of the blade and push it into the bit. Lift the file as you draw back for each stroke. Turn the axe around ...

Any talk about privacy is a complicated (usually) and touchy subject. In today's world, privacy is an ever eroding pleasure to be had. Numerous cases, like the monumental Kat'z vs United States, have been fought to hold on to this right.

If you follow the Anonymous, Occupy, and IT security scenes, you have no doubt heard about a dox release. What is it? How can it hurt you? And most importantly, how can you protect yourself from it? Some of these steps might seem common sense, while others will be an ah-ha! moment. Your private info is both your biggest weakness and your biggest weapon in your battle to remain anonymous. You must learn how to use it as both.

Jet engines combine oxygen from the surrounding air with on-board fuel to burn at very high temperatures and create thrust in the direction of the flame. Rockets, which we will learn about in a later post, are similar but carry oxygen internally and can therefore function in space!

In my recent Darknet series, I attempted to connect the dots on the Deep Web. I covered the two largest anonymity networks on the Internet today, Tor and I2P. While my initial four articles were meant as an introduction, I ended up receiving a lot of interesting comments and messages asking the technical differences between the two. I'd like to thank all of you for letting me know what was on your minds, as you should always!

We had a blast during last week's social engineering calls. One of our attending social engineers was so clever that she convinced several people on Craigslist that lost items were hers, even if it seemed she couldn't be trusted. But females are better social engineers, naturally. Some say that females have a special knack for manipulating men, but I think that's preposterous. I can't see why that would be true in a million years (note my sarcasm).