In this short how-to video, self-described earth mother Mayo Underwood demonstrates how you can germinate seeds in damp paper towels prior to planting them in your personal garden. Watch this tutorial and start some seeds of your own today!

Designer Andrew Hanson shows you how to take an old pair of Chuck Taylor's shoes and add your own personal designs and flair to them.

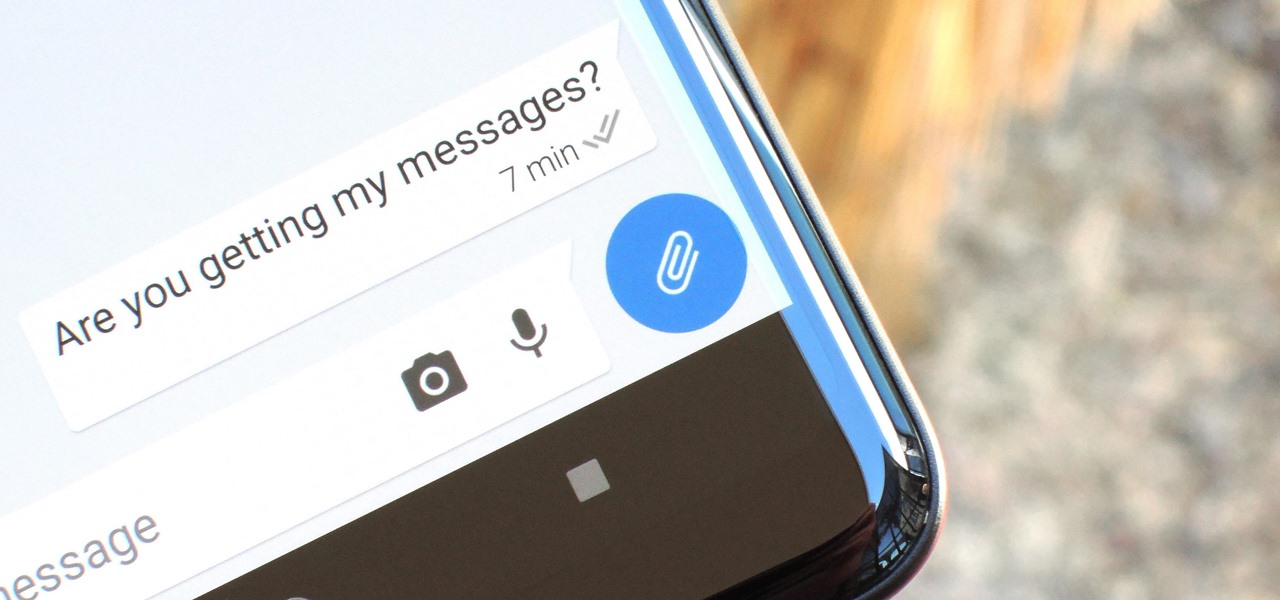
Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.
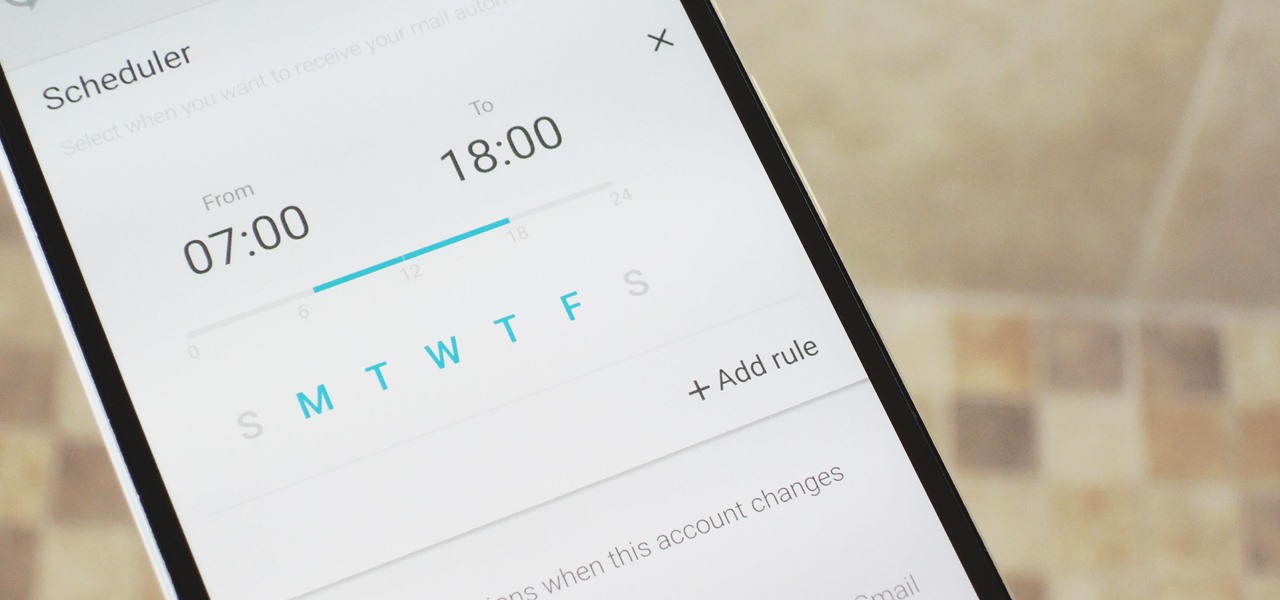
Low Power Mode (LPM) decreases the amount of battery your iPhone uses by disabling background app refreshing and automatic downloads, locking your screen after 30 seconds, and more. While it's only meant to be used temporarily, if you're struggling with battery life, you may want to enable LPM permanently.

While modern browsers are robust and provide a lot of functionality, they can be unlocked to do some pretty spectacular things with browser extensions. For hackers and OSINT researchers, these tools can be used to defeat online tracking, log in to SSH devices, and search the internet for clues during an investigation. These are a list of my top ten favorite browser extensions for hackers — and how to use them.

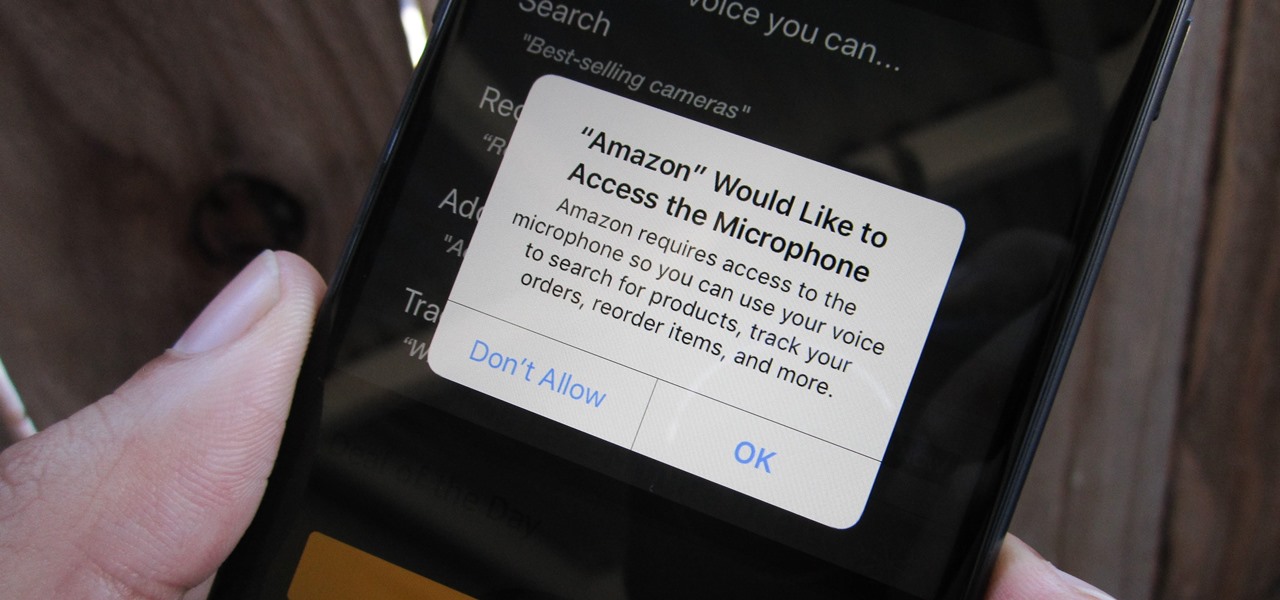
Any app on your iPhone could potentially listen in on your conversations and use that information to target you with tailored ads. Although most companies, including Facebook and Apple, have come out and vehemently denied these claims of spying on consumers, who's to say they're telling the truth? The only way to be sure you're safe is to take matters into your own hands.

Keeping data private is vital in the days of smartphones and the free-floating information they carry. Justin wrote a guide on many of the deeply hidden and sometimes concerning privacy settings in iOS 7. Now we're back to cover some of the new (and old) privacy settings in iOS 8 that you need to address right now.

This video explains how to delete cookies in Windows XP, Mozilla Firefox, Internet Explorer and Opera. To delete cookies in Mozilla Firefox, choose the "tools" option from the tool bar, then choose "options", then choose "privacy". Many options will be given under the "privacy" menu, but make sure to choose the following options- "accept cookies from site" and "accept third party cookies", then choose the option "I close Firefox option" under "keep until" then choose "ok" to delete the cookie...

Starting to work at home? With more and more people trying to make a solid living at home, it's important to know the best way to set up a home office – even if you don't have a spare room. Learn how to set-up a solid work environment with tips from this video on how to create the perfect home office.

With social networking systems, YouTube comments chains, chat rooms, bulletins boards, Twitter updates... It seems as if almost everyone has at one time publicly stated an opinion on the Internet. Nearly half of all prospective employers research job applicants online. Make sure that what you’re posting today doesn’t cost you a dream job tomorrow!

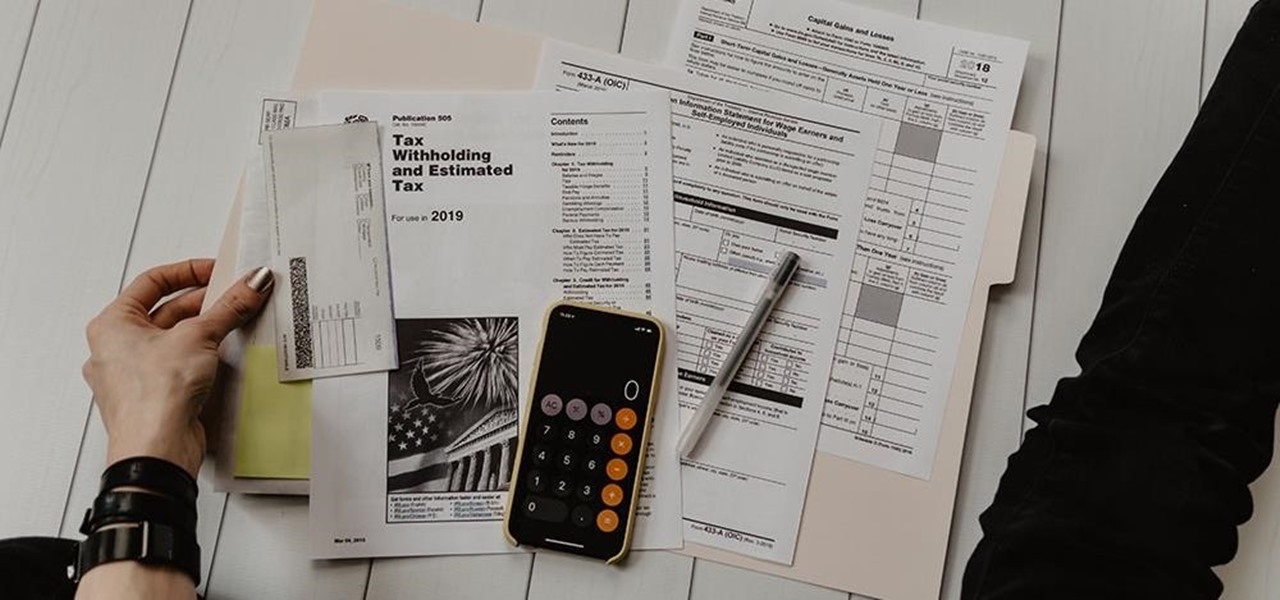
The COVID-19 pandemic has hit everyone hard. With over 36 million American workers filing unemployment claims, finances are at the front of everyone's mind. Understanding your accounts has never been as important.

When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.

Many popular apps automatically share your personal data. While I have accepted a certain amount of data collection from Google, to know companies such as Facebook perform this without my consent bothers me. After some researching, I've found a great solution, and it doesn't require root.

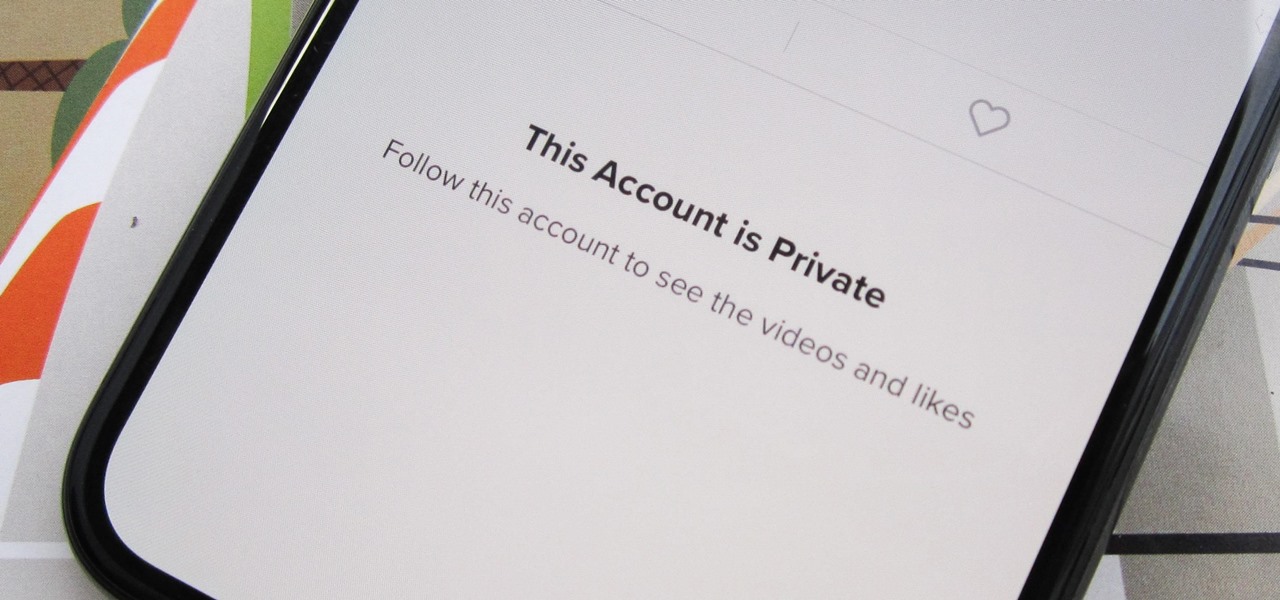
Can you trust every user you come across on TikTok? The answer to that may depend on how use the service, but the real question is — can you trust every user that sees your content? Not everyone on TikTok is someone you want viewing or interacting with your content, and there's a way to prevent them from doing so.

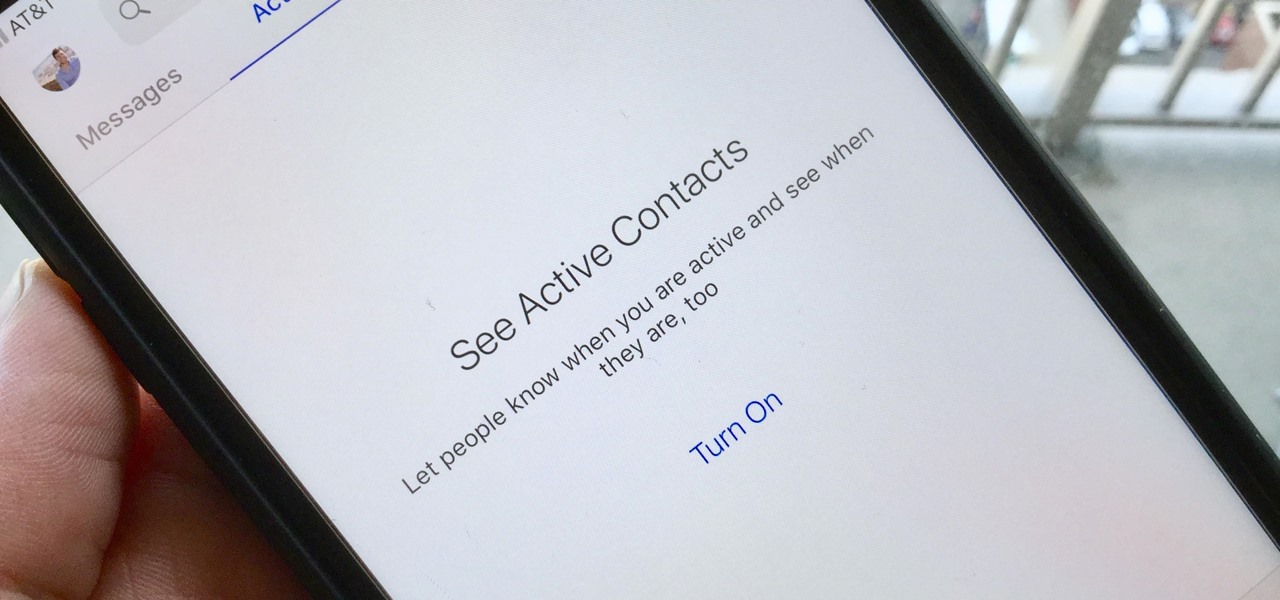
For all of its advantages, Facebook Messenger isn't the best for people who like their privacy. The popular app lets all your Facebook friends know when you're online by default, as well as how long you've been idle, making it impossible to check up with one person without leaving yourself vulnerable to your entire friends list. Luckily, this feature is one you can turn off.

When you visit a website in Safari, it's most likely keeping tabs on your browsing activity. It could be keeping track directly, or its third-party content providers and advertisers can be spying on you. All three could happen simultaneously. This enables them to serve you content that's tailor-made for you, but it can also feel like an invasion of privacy.

After receiving many requests for the feature, Signal introduced read receipts last year to its mobile apps. However, some users don't like the idea other people knowing when they've read messages. Luckily, Signal lets you disable this feature and reclaim a little privacy.

These days, when you're setting up an Android device for the first time, you'll be prompted to add extra email accounts directly to the Gmail app. It's really simple, too—just sign in with your work or exchange account, then emails from those accounts will be mixed in with your personal account in the Gmail app's "All Inboxes" view.

If you're tired of Google tracking you, but love how Chrome works, CyanogenMod has you covered. Their browser is called Gello, which is based off Chromium, Chrome's open-source counterpart. It's basically a souped-up version of Chrome—without all of the intrusive Google stuff. So if you're uncomfortable with Google displaying personalized ads based on your browsing history, or using your location to bring the "Physical Web" to your phone, you won't have to worry about any of that with Gello.

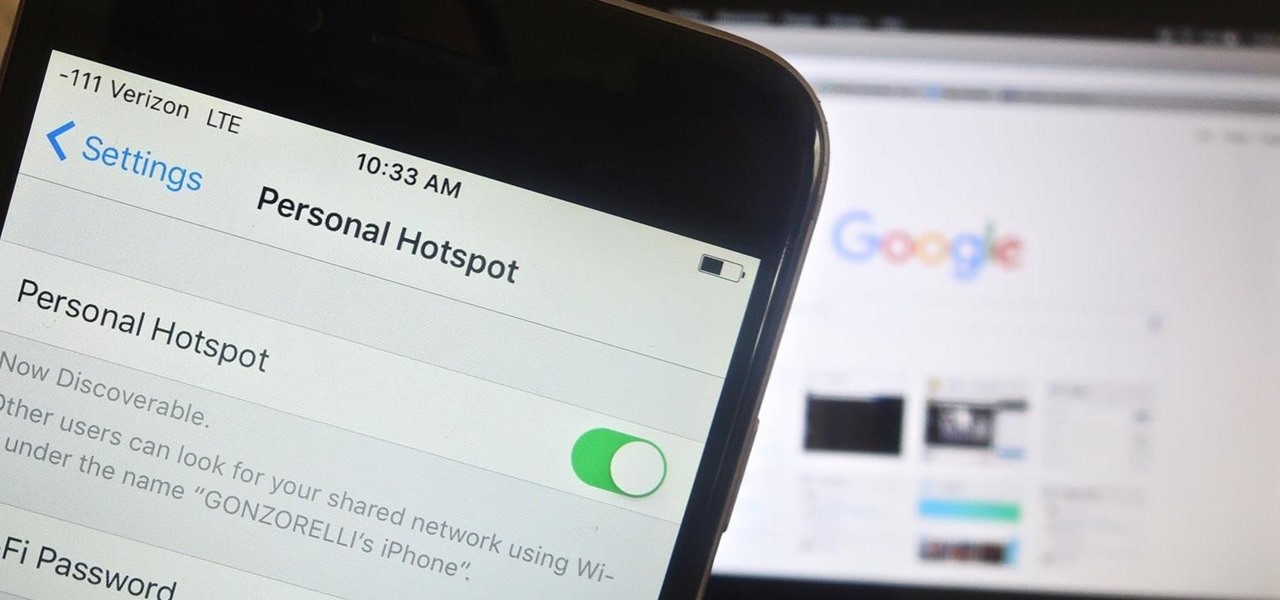
When you're in a bind and need an internet connection for your laptop, look no further than your iPhone. Using the Personal Hotspot feature in iOS, you can share your iPhone's internet connection with other devices by way of Wi-Fi, Bluetooth, or even USB.

In February of this year, the Higher Court of Berlin ruled that Facebook must follow strict German data protection laws, which Facebook's terms of services and privacy policies circumvent.

If you're a frequent Snapchatter like myself, you're probably well aware that Snapchat can't stop you or anyone else from taking a screenshot of a photo received. Instead, they notify the sender that a screenshot was taken—a greatly appreciated fair warning when impetuous photographs are involved. However, there is a loophole to this.

The creation of private browsing was brought upon by the backlash against ad tracking and other ways that sites and agencies take away users' privacy online. People were tired of getting spammed with ads for Vitamin C pills simply because they visited WebMD. Private browsing is now built into all of the major browsers and is used frequently. While private browsing is more infamously known as the "Porn Portal," and does prove to be a great way of keeping racy content out of the sight of others...

Microsoft's updated web browser, Internet Explorer 10, has only been out for a few days on Windows 8, and there is already a storm of controversy surrounding its launch.

If you've read anything in the news about Skype recently, it probably hasn't been good. First, there was the controversy over the company listening to and recording users' conversations. Now, there's a new spam tool for Skype that can harvest usernames, see whether or not you're online, and even parse your log files. Image by Lloyd Dewolf

You probably already know that your digital pictures have quite a bit of information embedded in them. What you might not know is just how much personal information is included in that metadata, including your camera information, and in some cases, even the precise GPS coordinates of where you took the picture.

Don’t play Russian roulette when it comes to your wheels. Keep your bike secure with these precautions.

In this video, we learn how to transfer songs from an iPod to your personal computer. First, open up your computer and go into the folder with your iPod. Now, go to tools, folder options, view, and hidden files/folders. Apply this, then the folder with all of your music will show up! You can now unplug your iPod and then select all of the folders on your computer. Right click then and go to properties, then uncheck the hidden. Hit 'apply' and then transfer all the music to your computer. Now ...

Do you need to restore all of your digital music on your computer? Computer crashes are a pain, but if you also had all of your music on your Apple iPod, then there's a chance for you to get it back. And if you also need to get back all of your personal contacts, personal notes and calendar information, believe it or not, it's totally possible.

WPA-secured wireless networks, or WiFI Protected Access, is a form of internet security that secures your wireless LAN from being accessed by unauthorized users. Safer than WEP, or wireless equivalent privacy, WPA still has weaknesses that are prone to cracking - IF, that is, you know what you're doing.

Ahhh! You're locked out of your bedroom, or your bathroom! Well, watch this video and you won't be locked out for long. Fortunately, interior privacy locks are very simple to pick. There are essentially two kinds: one that requires a blade, or knife and the other which requires a long sharp "pin" like object to insert into the handle. Check out this video and never be locked out again! You'll need something like a flat head screw driver for locks with a "slot" in them, and something long and ...

When you first buy a corset from a retailer, you will need to give the thread and fabric the chance to shape itself according to your own personal shape. Here is the best way to break in or season a new corset to make it last longer.

These are great, personal gifts that you can hand out to friends this holiday season. Find a picture and a quote you like, then dress them up in a picture frame! All you really need is the frame, some paint, a few old magazines and some paper!

Before you know it, old Saint Nick's reindeer will be tapping on top of your roof and a Salvation Army bell ringer, festooned with a Santa Hat, will be around every corner. That's right, guys and gals, Christmastime is almost at our front door, which means you should get prepared for all the holiday gifting.

The Genoese Zipper Sinnet is actually a fusion of both the single Genoese Bar and the Zipper Sinnet, obvious reasons for the name. This knot can be great for making a strap, bracelet, or necklace. In this video you will learn how to tie the knot up close and personal, giving the video great detail and insight into the knot tying process.

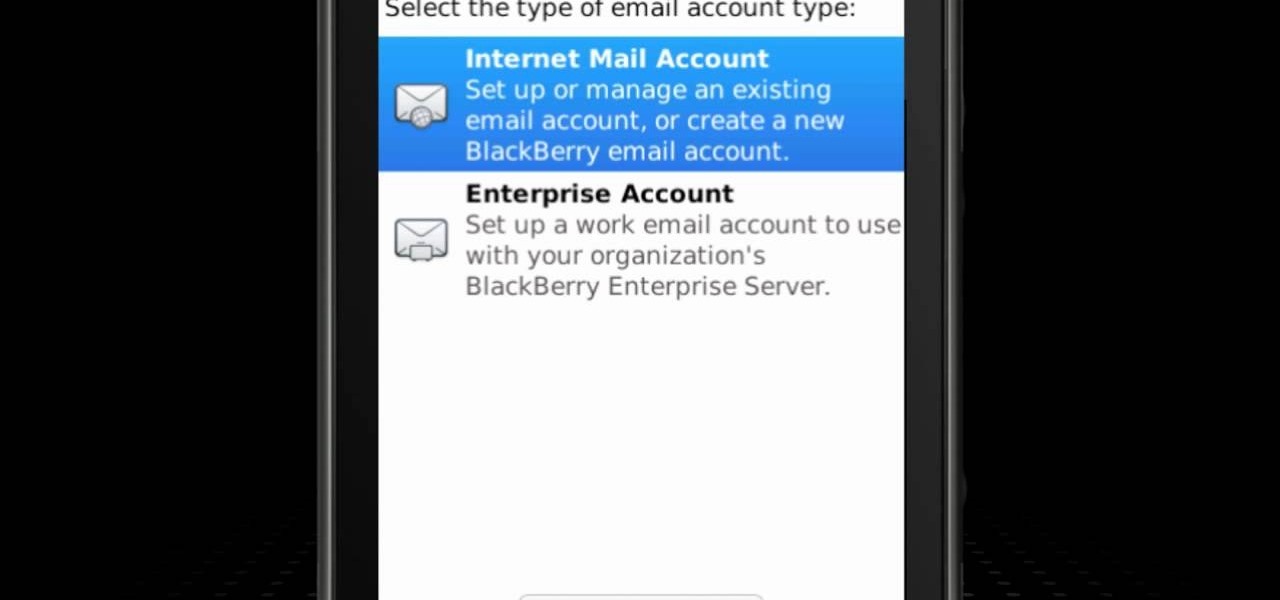
Learn how to create and configure a new email account on a BlackBerry Torch 9800 smartphone running version 6 of the BlackBerry OS. This clip will teach you everything you'll need to know. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this official video guide from the folks at Blackberry. For detailed information, including step-by-step instructions, take a look.

Grow Valley is an educational but fun flash game where you develop a valley with all the niceties of modern life, from cars to dams.

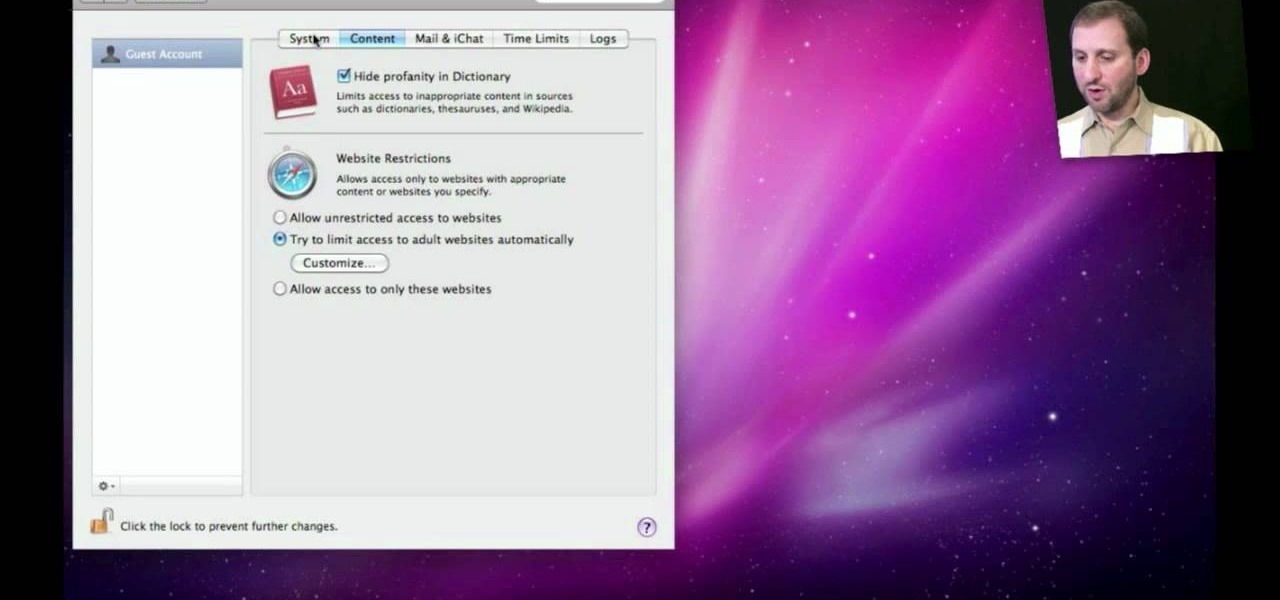
Want to allow someone to use your computer without giving them free reign of your personal documents? Then you'll want to set up a guest account. This helpful home-computing how-to from the folks at MacMost presents a complete step-by-step overview of the process. For the details, and to get started creating and using guest accounts on your own OS X computer, watch this video guide.