With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

In 2017, major breakthroughs in smartphone-based simultaneous localization and mapping (SLAM) opened up new doorways for developers and users of both Apple and Android phones. Unfortunately for Android users, the solution that Google is previewing, ARCore, currently only works on three Android smartphones. But Silicon Valley start-up uSens is stepping in to fix that with its new engine called uSensAR.
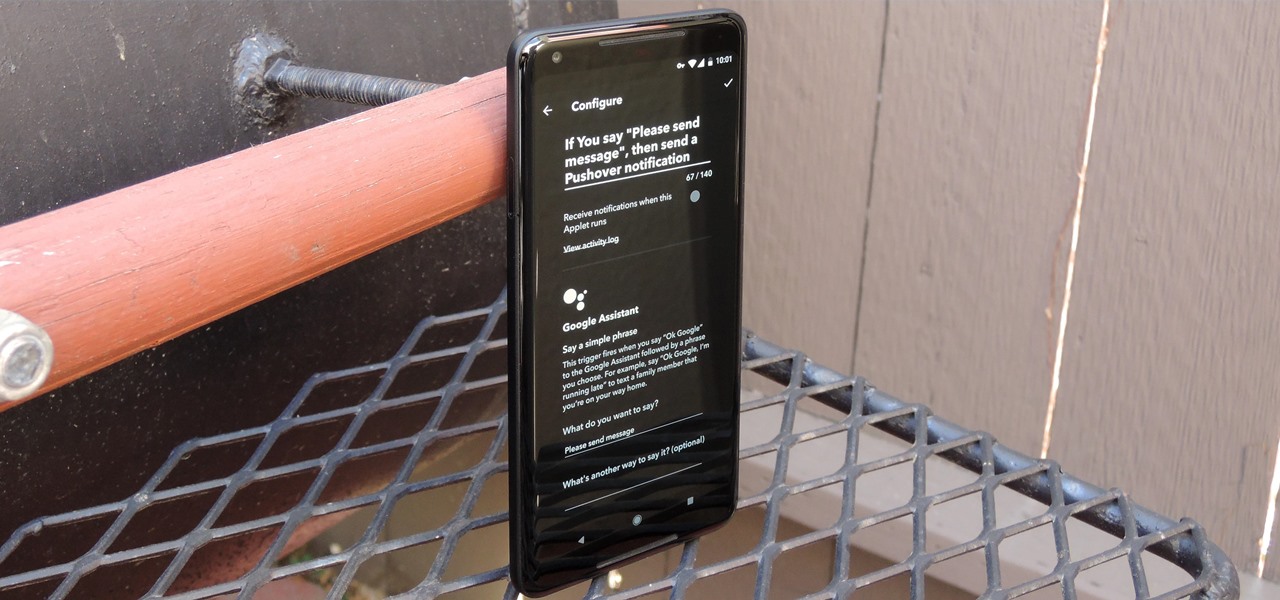
IFTTT is a fantastic tool that lets you trigger actions on your smartphone that normally require more advanced hacking. With the help of its friendly user interface, turning your phone into a more personal device has never been easier. However, the app has some more intricate options under the surface, making advanced implementations of applets difficult for beginners.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

The year is 2018. You just received your own Magic Leap One: Creator Edition. What now? Rewinding back to today, we know of one specific app that will be available for Magic Leap's device, along with two others that could be tagged as highly likely. Paired with Magic Leap's own experiments and demonstrations, we can get a sense of what the playground for this new toy will offer.

Having your home and work addresses set in Apple Maps makes them incredibly easy to navigate to no matter where you're located. If you move to a new house, stay in a hotel or resort while vacationing, report to a different office, or have multiple job sites to visit regularly, updating these addresses isn't only straightforward — there's more than one way to do it.

Mozilla's Firefox has always been a highly praised internet browser. Since it's open-source, users know what they're getting without any secrecy. It's got plenty of features that are unmatched by any of its competitors on mobile. However, speed and performance have always been a pain point for Firefox, but Mozilla went back to the drawing board to solve this problem with the release of Firefox Quantum.

Now that Apple Pay Cash has rolled out to compatible devices in the US, you're likely to give Apple's new person-to-person payment system a try since it's right there in the iMessage app drawer in Messages. However, just like with Venmo, Square Cash, and other mobile payment processors, there are some hidden fees, limits, and other fine print you need to be aware of.

When it comes to security, Apple is usually at the top of the pack when it comes to your personal data, minus a few embarrassing flaws here and there. However, a new iOS security concern has been discovered that protects your data less than it did before — and Apple designed it like that.

The next frontier for AR hardware is the consumer headset, and tech companies of varying size and tenure are working hard to strike the right mix between comfort, cool factor, and cost. How these companies handle the hype and flow of information vary wildly.

The new and improved Side button, as well as a plethora of new swipe gestures, are responsible for picking up the slack left by the missing Home button on the iPhone X. If you're really missing that Home button, however, Apple's built-in AssistiveTouch tool can help you out by adding a virtual Home button on your iPhone X's screen.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

With four major carriers, buying an iPhone X or iPhone 8 can be more complicated than you'd think. While Apple has its own iPhone upgrade program, AT&T, Sprint, Verizon, and T-Mobile all have versions of their own. Which plan you choose depends on your needs and, of course, your carrier. However, getting around to upgrading can be challenging to say the least.

Your iPhone has a lot of personal information contained within it, so of course you want your device to be secure. You don't want that information getting into the wrong hands — or any hands other than your own, for that matter.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

A recent initiative by the Cherokee Nation American Indian Tribe delivers a success story for knocking out a silent killer — Hepatitis C.

Andrew Mucci, a New Jersey-based vlogger who is also Social Media Coordinator at Sennheiser, likes to use Instagram not only as a platform for the brand but also as a place to experiment with content on his own account.

A recent study offers information that might help combat a deadly virus that affects an estimated 300,000 people each year in West Africa.

Crusty, itchy, red eyes? There is a decent chance you could have conjunctivitis, or pink eye, an infection of the thin lining around the eye and the eyelid, caused by bacteria, an allergen, virus, or even your contact lenses. Whatever the cause — you call up your doctor to get a prescription to clear it up, right? Not really.

Love is the spice of life — it is also the microbes that couples share through sickness and in health, through the bathroom and in a hallway.

An older man dies of Zika. A younger man who cares for him catches Zika — but doctors cannot pinpoint how the disease was transmitted. While proximity to the patient is sufficient explanation for the rest of us, for microbe hunters, it is a medical mystery. Why? Zika is not known to transmit from person-to-person casually.

Despite longer live spans, almost half a million people die of healthcare-associated infections (HAIs) each year, many of them preventable.

Bitmojis are not only a good way to personalize your Snapchat account, but also a really fun Snap addition to play around with. A bitmoji is basically like your little avatar, letting you design your mini-self whichever way that you desire.

Everything from disposed of drugs to hormones and disease-causing bacteria — anything that is rinsed or flushed down the drain — can contaminate wastewater.

The Deepwater Horizon oil spill that began on April 20, 2010, was the largest maritime oil spill in history. Killing 11 people and discharging 4.1 million barrels of oil and natural gas into the Gulf of Mexico, the event was an unparalleled personal, environmental, and business disaster. It was also the first major oil spill to take place in the deep ocean.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Facebook is testing a new feature in India. One that could help you protect your profile photos from being used on sites without your permission.

There are a lot of exciting improvements in store for Siri in iOS 11. Apple showed off some of the highlights at WWDC, but there are five changes in particular that you don't want to miss.

Move over whole wheat — white bread may be back in style after a new study shows that it may be your gut microbes that decide what kind of bread is best for you.

Breastfeeding is the ultimate in farm-to-table dining. It is sustenance prepared just for the baby and delivered with a very personal touch. Along with bonding, breastfeeding provides powerful protection to infants and young children in the form of beneficial bacteria, hormones, vitamins, protein, sugar, and antibodies manufactured on site to support infant health.

A disease called "citrus greening" has devastated and permanently altered citrus production in the United States, but a vaccine that could protect orange trees may be part of a winning strategy to beat the bacteria that is killing the trees.

A new technological movement without the technology itself is just an idea sitting and waiting. Once the technology is present in the equation, movement forward can begin. This is how many of us see the head-mounted displays (HMDs) and smartglasses that have recently entered the augmented and mixed reality market — or are coming out in the next few months. This is a movement that will sweep over the world, changing everything in its path, and these are some of the people behind it.

As much as you try to safeguard your personal information, you may have made a small mistake by giving your phone number to the wrong entity, and now you're being bombarded with dozens of spam calls every day. To help parse your call log and reject the proper numbers without answering or trudging through voicemail, a good reverse phone lookup app is needed.

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

The squiggly guys in this article's cover image are Propionibacterium acnes. These bacteria live in low-oxygen conditions at the base of hair follicles all over your body. They mind their own business, eating cellular debris and sebum, the oily stuff secreted by sebaceous glands that help keep things moisturized. Everybody has P. acnes bacteria—which are commonly blamed for causing acne—but researchers took a bigger view and discovered P. acnes may also play a part in keeping your skin clear.

Typing on a mobile device has come a long way since the days of flip phones. Today, there are awesome keyboard apps like Gboard, which integrates Google search features and makes typing a breeze. But the whole experience still stands to improve if you take some time to learn a few useful tips.

The photo-centric Instagram app is a great way to share "evergreen" pictures and videos when compared to Snapchat and Facebook's new Messenger Day feature. But like all social media, keeping the account secure is an essential aspect, as it restricts unwanted viewers from seeing your content and can prevent unauthorized users from accessing your account. Instagram has several methods for locking down the account including a new two-factor authentication (2FA) mechanism.

Even as health authorities describe the symptoms of Zika infection in the general population as mild, a new surveillance study finds serious side effects are more common, and serious, than previously thought.