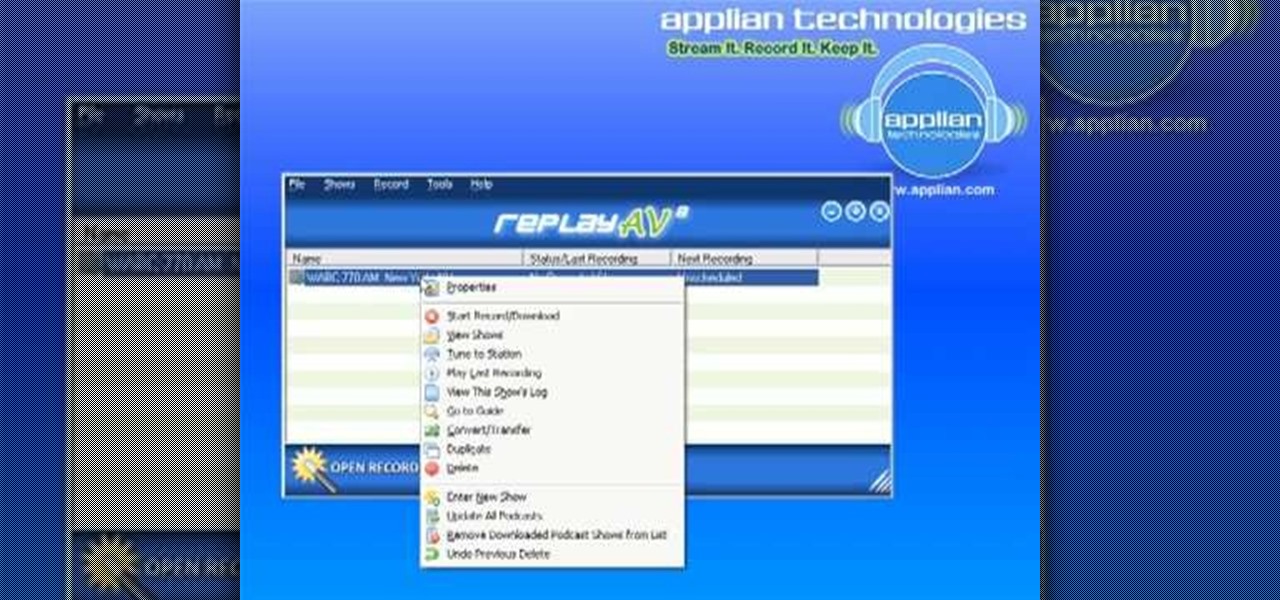
Replay AV is the newest software to come out for downloading steaming audio from the web. Replay AV allows you to download audio from different sources all over the web. You can even record radio broadcasts and set your account to record the station. This video will show you how to add a radio station to Replay AV.

This is an intensive one-day overview video tutorial of the fundamental concepts of the Ruby on Rails Web programming framework, presented by the UC Berkeley RAD Lab. The overview consists of six sections of approximately one hour each. Click through the video chapters to go through the Ruby on Rails programming course.

People use browsers for all types of things, and in general, we trust a lot of personal information to them. That's why browsers are a perfect attack surface for a hacker, because the target may not even know they are infected and feed you all of the information you could want.
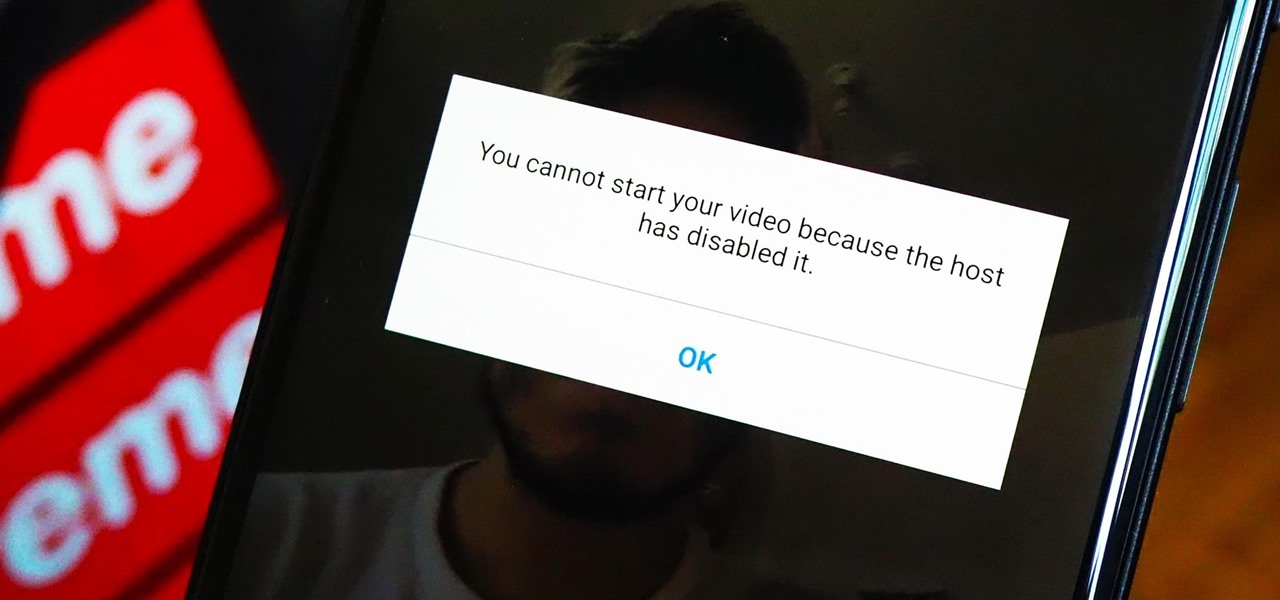
As a meeting host on Zoom, you can't control what a participant does during your live video call, but you do have the power to turn off their camera so that other people aren't subjected to distractions. So if you catch someone in your call purposely making obscene gestures or accidentally exposing themselves while using the bathroom, you can block their camera, as long as you know how.

While Apple and Google have paved the way for developers to create web-based AR experiences through their respective mobile toolkits, an open source option has entered the space.

When it comes to the athletic footwear retail game, it's just not enough to just sell shoes anymore.

During the recent Augmented World Expo (AWE), we had a chance to try out the Lenovo ThinkReality A6 AR headset. Unfortunately, the experience was all downhill from there.

When you can't think of a way to respond in Messenger with words, emojis and stickers will do the trick. Since Facebook is all about the "likes," which use a thumbs-up icon, there's a shortcut to the symbol just to the right of the chat field. It's always there to send a quick like in response to something. But it doesn't have to be the standard Facebook thumbs-up sign — it can be any emoji you want.

There are nearly 100,000 unique onion service addresses online with over two million people using Tor every single day. Join me as I explore a small fraction of what the Tor network has to offer.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Although it sounds like a foodie's take on Facebook, what Calabasas, California-based FaceCake actually offers is more about augmented reality fashion marketing rather than food selfies.

The Consumer Electronics Show (CES) is the first big tech event of 2018. This year, if the early news is any indication, augmented reality could be the big star of the show.

The narratives around virtual reality consistently revolve around human empathy and emotion, while the story around augmented reality has been decidedly more dispassionate and business-focused — until now.

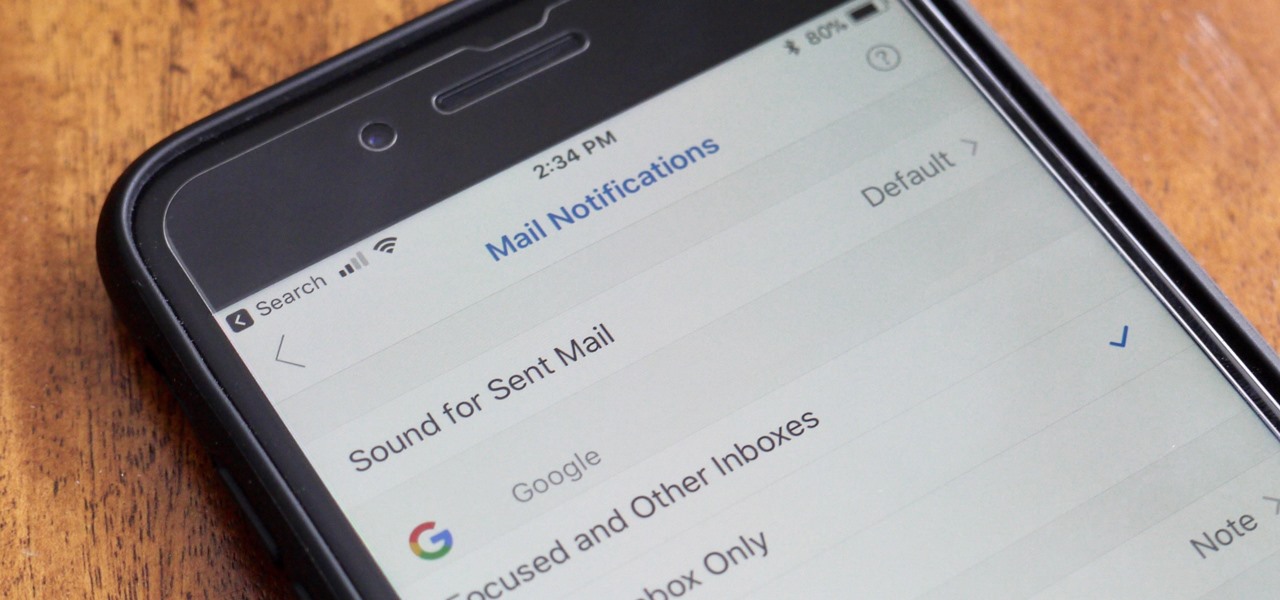
With email, one size does not typically fit all. You have multiple email accounts, each for different purposes and with varying levels of importance, so it only makes sense to customize the way your phone alerts you to each account's incoming emails. Luckily, Outlook allows you to do just that.

As the level of data being generated grows exponentially, past the Information Age and into the coming Hyper-Information Age of immersive computing — as resistant as many of us are to the idea — personal data security is becoming a necessary consideration in our everyday lives. Recognizing this, Mastercard, Qualcomm, and Osterhout Design Group have teamed up to show what secure shopping could look like in the very near future with iris authentication.

You may not have woken up like this, but you're still #flawless thanks to Microsoft's new Face Swap app for Android.

Bose Corp is the latest company trying to make another dollar off of you without your permission. Bose Connect, the companion app to the swag $350 Bose headphones, is not the Jane to your Jack that maybe we all hoped it to be.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

No matter which smartphone you buy, it will come with an internet browser preinstalled. Depending on your OEM, the default browser might be called Samsung Internet, HTC Internet, Silk Browser by Amazon, ASUS Browser, or Google Chrome—there's just so many stock browsers available.

When you do an internet search, you'll see ads that are relevant to your query mixed in with the rest of your results. Nothing surprising there—it's how the internet is funded. But then, when you click one of the search results, you'll also see ads that are related to your initial search. Now that's a bit creepy, because it demonstrates that one webpage knows what you typed into a different webpage.

With the recent news that New York County's District Attorney's office is trying to get into over 400 locked iPhones for use in criminal investigations, you can see why it's important to keep other people away from your personal data. The fact that it can and will be used against you in a court of law is just one reason to protect your phone, because even if you make sure to stay above the fray, identity theft and bank fraud are still very real threats.

We're already glimpsing the future when we look at mixed reality through a headset, but is the real evolution of this technology something that will exist as part of our bodies? As intense as that may sound, TechCrunch's Jay Donovan offers compelling reasons why it's not such a crazy idea:

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

All across the web, you'll find guides on setting up various apps and mods for your Android device—but while these are certainly useful, they all seem to be working under the assumption that the reader has a certain level of knowledge about Android. For someone that's just getting started with the world's most popular mobile operating system, the basics of Android simply aren't covered as well as they should be.

Welcome back, my amateur hackers! With Halloween right around the corner, I thought you could have a little fun with your newfound hacking skills using a hack that is guaranteed to freak out your boss, teacher, coworker, friend, etc.

Welcome back, my tenderfoot hackers! In this series, we are exploring the myriad of ways to hack web applications. As you know, web applications are those apps that run the websites of everything from your next door neighbor, to the all-powerful financial institutions that run the world. Each of these applications is vulnerable to attack, but not all in the same way.

Google's Chromecast is quite literally one of my favorite inventions of the past five years, allowing me to kick back, relax, and enjoy the various forms of streaming entertainment it has up for grabs.

Managing files can be time consuming on your Mac, for the simple reason that keyboard shortcuts and right-clicks sometimes lack the effectiveness we need. But with a simple third-part app, you can expedite the process of sharing, moving, deleting, and overall managing files on your computer.

SoundHound, the Shazam-like song-matching service, recently announced a new mobile app called Hound, which wants to be your one and only intelligent personal assistant.

These days, there is no shortage of ways to exchange files to and from friends and family: text messages, email, Bluetooth transfer, and cloud services are just a tiny sliver of what you can use to share music, photos, videos, and more.

Some people are of extremely secretive nature. They do not like sharing their personal events in their lives with anyone. Thus people around that person wont be able to figure out details on their life's personal matters. It is not like they want to hide some mysterious secrets from the world, but it is just their nature that they do not want others to know much about them or are too shy to share their feelings with others. Being secretive is neither good nor bad, it is just how they are.

With troves of sensitive information, like receipts and password reminders, hiding in your email, your inbox can become a sort of Holy Grail for hackers—or anyone with your password. Although my crazy ex-girlfriend had no hacking experience, using my email login, she was able to find a lot of account information with just a general search for "password" in my inbox.

Facebook essentially strong-armed us all into installing their standalone Messenger app for mobile devices, but the recent initiative that allows third-party development on the platform definitely makes it worth your time.

Televisions used to be great for just one thing—watching TV. But a more connected world brought with it Smart TVs, devices that can access the web, stream Netflix, and even mirror your smartphone's display. And with this level of connectivity, OEMs like Samsung saw it fit to place targeted and interactive ads on your screen.

AllCast, from renowned developer Koushik Dutta (better known as Koush), allows users to stream personal media, such as movies, photos, and music from mobile devices to Chromecast and other streaming devices.

In the weeks before Apple officially released iOS 8, consumers were abuzz over rumors that a new feature would password-protect your photos and text messages from prying eyes. Unfortunately, this ended up being untrue, though we did cover some alternatives to protecting your important information using some built-in features and a third-party app. Now, there's a new iOS app that can do it all.

Steam is by far the biggest and best service for getting games on your Linux, Mac, or Windows PC. With their catalog containing everything from the biggest blockbusters to indie games created by one-man development teams, it's no easy task to keep track of their best values—until now.

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

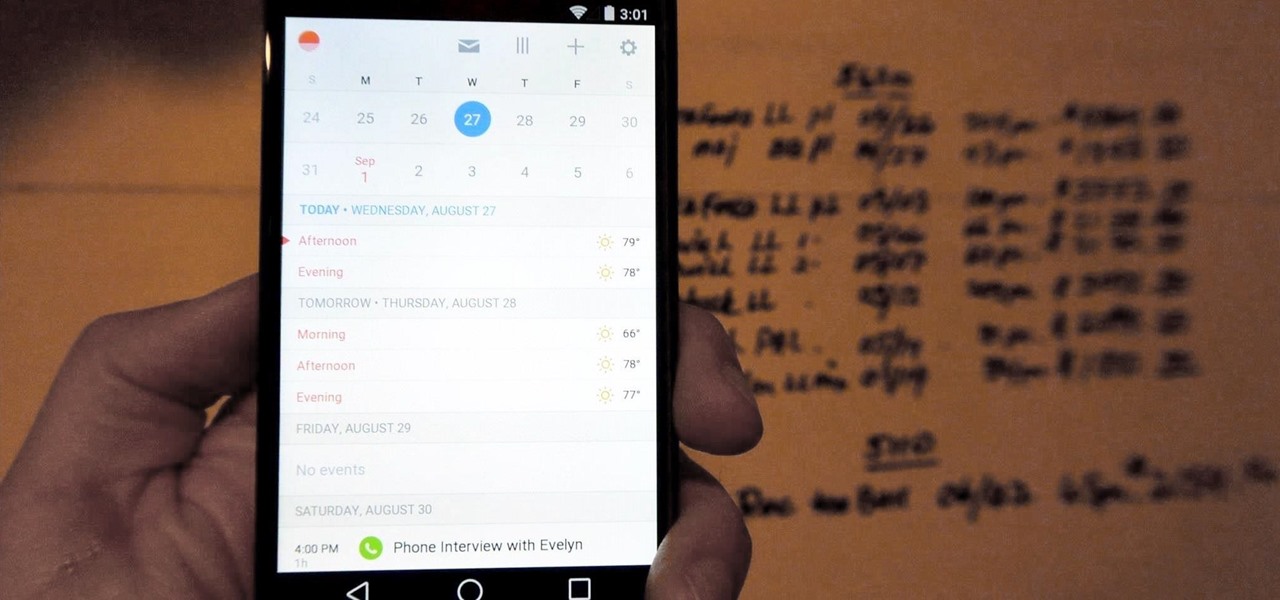
If you're anything like me, you rely heavily on your calendar to keep on track throughout the week, month, and year. While Android's built-in Google Calendar provides an excellent cloud-based solution for keeping our schedules properly maintained, it's not perfect.

With so many keyboard options available for Android, there's no reason to limit ourselves to the default one, or to just the ones available in the Amazon Appstore. While the Appstore does provide alternatives, such as SwiftKey, it doesn't come close to the selection available in the Google Play Store.