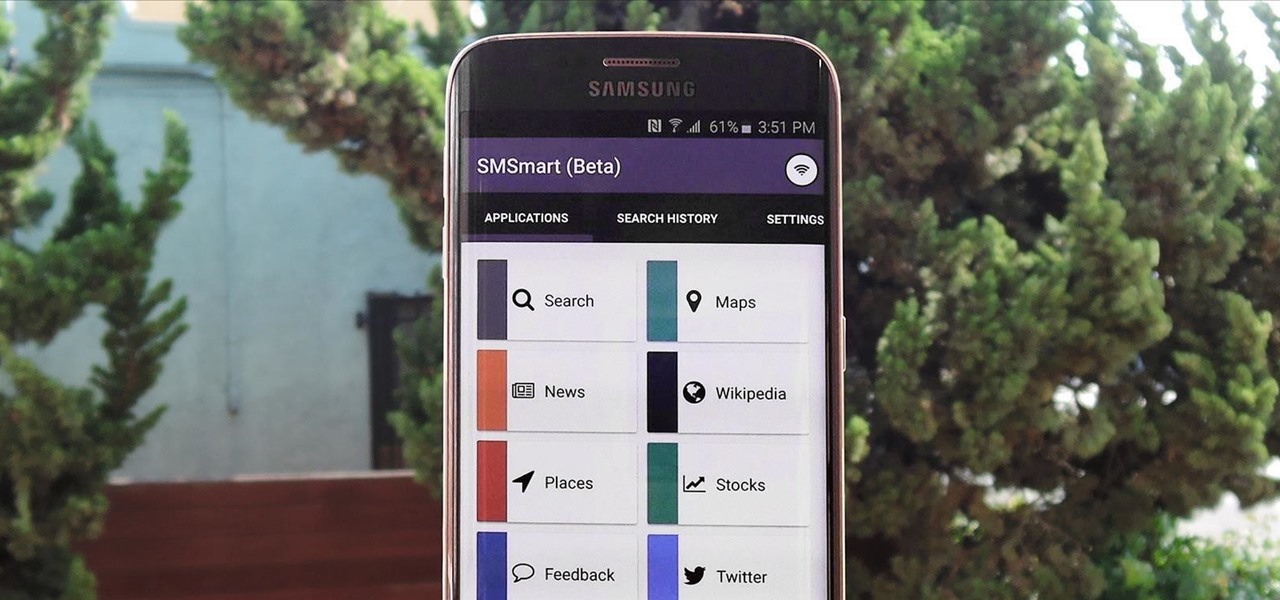
Websites and web applications power the internet as we know it, representing a juicy target for any hacker or red team. TIDoS is a framework of modules brought together for their usefulness in hacking web apps, organized into a common sense workflow. With an impressive array of active and passive OSINT modules, TIDoS has the right instrument for any web app audit.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

If you've ever wanted to barge into Jerry Seinfeld's apartment like Cosmo Kramer, you can now do so without having to book a ride on the Peterman Reality Tour.
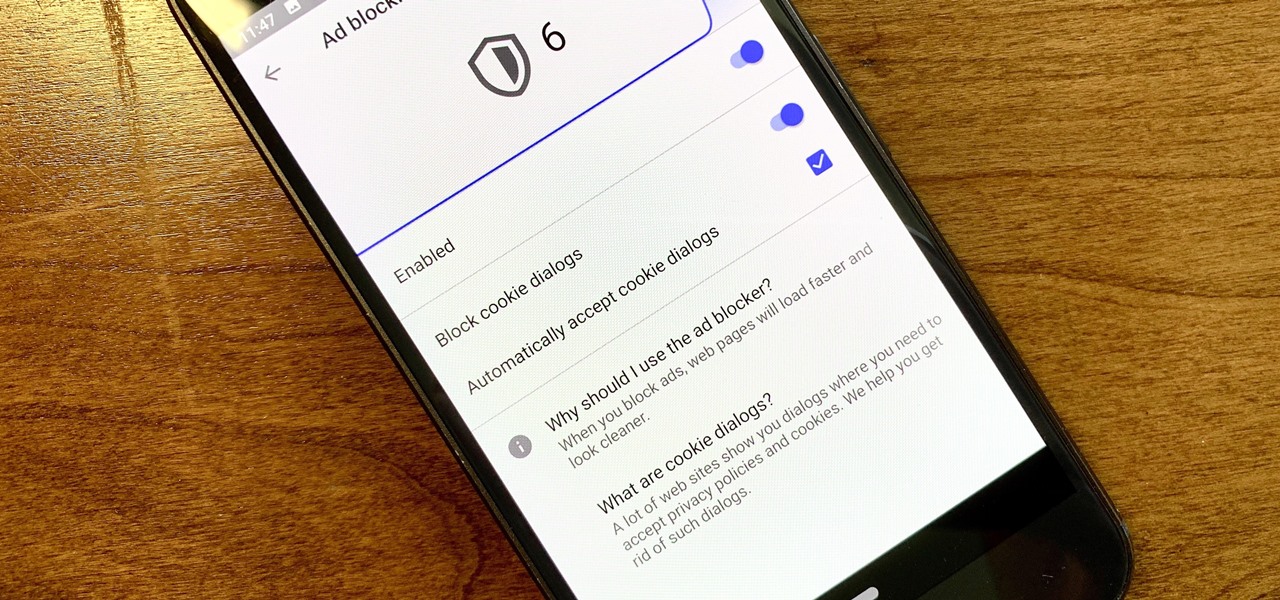
Ever since the GDPR was implemented, it seems every website on the internet needs to inform you of how its privacy policies have changed. If your web browsing experience has been marred by a constant barrage of these cookie pop-ups and privacy dialogs, you should know there's an easy way to block these web annoyances so you never have to tap another checkbox or accept button again.

It only takes a few commands to manipulate a MacBook's secure HTTPS traffic and pluck login passwords out of the encrypted data. Let's take Facebook and Gmail hacking to the next level by intercepting Safari and Google Chrome web traffic in real time.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Developers can now publish augmented reality experiences that are viewable through the experimental version of Chrome and ARCore.

With its recent acquisition of 3D gaming engine PlayCanvas, Snapchat parent Snap, Inc. appears to be preparing a challenge to the existing players in the world of game development, particularly in terms of augmented and virtual reality gaming.

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

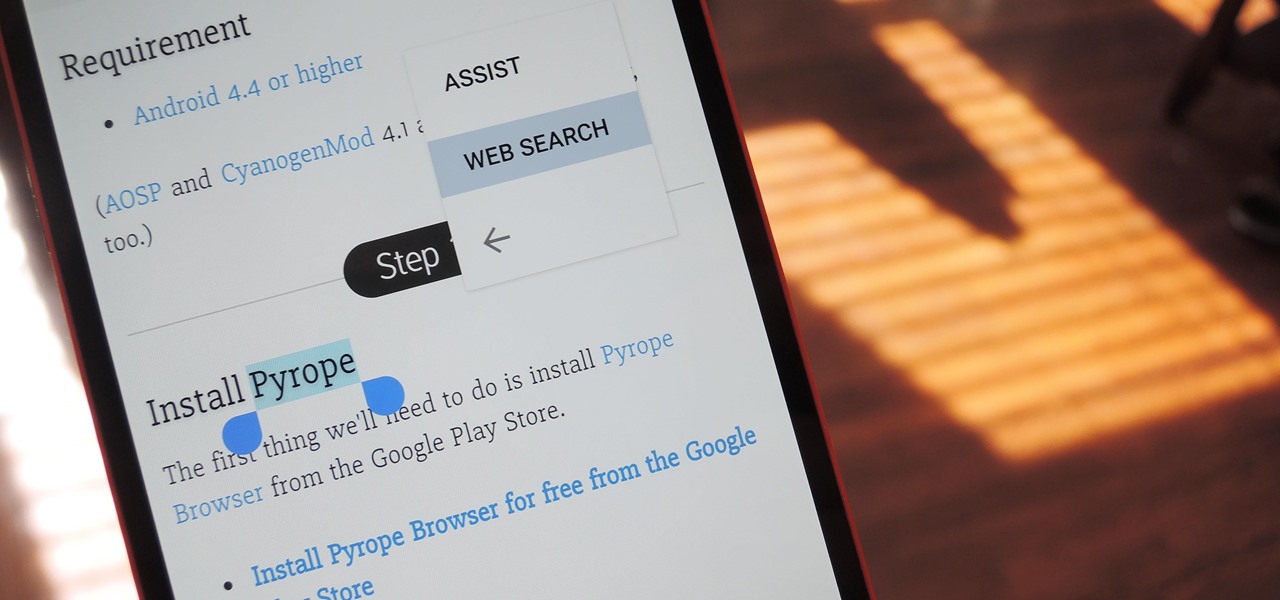
Chrome's text selection interface is pretty nice, but it could definitely use some improvements. For instance, when you're in Incognito Mode, you can't perform a web search for words you've highlighted. And when you're typing out a forum post or using any text input field, for that matter, there's no option to search or share any of the text you've written.

Mixed reality can give you the feeling that you've uncovered a hidden world layered into the physical one you already know. This can happen in so many ways, from a trading card that births a hologram or a first-person shooter with robots blasting through your walls. Xperiel—a California-based augmented and mixed reality company—wants to create a platform to make that a whole lot easier for developers.

Google is reportedly working on an iOS keyboard that brings key features to the iPhone, including Google's image and text search functions. (GIFs, yay!) According to The Verge, the keyboard has been in development and testing for months, and will act much like the Android version.

This Video is about my Trying a New Braid pattern for a Crochet Weave.

I will Show you in this Video How I dust my Ends... PLEASE NOTE:

Chrome apps and extensions are powerful tools for students: they can help optimize your web browsing experience by helping you take notes, check your grammar as you compose documents and emails, and even help you squeeze a little more juice out of your laptop's battery by freezing unused tabs and optimizing YouTube streams.

This Video will show you How to Do Two Strand Twist. I had been practicing looking at different YouTube Videos

before I move on to more exciting areas in this series, I want to also point out some things to protect your information & how to not get DoXed.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Hello, my web huggers! In today's tutorial we will learn how to use the Google Hacking Database (GHDB) developed by Exploit Database, to find vulnerable web servers and "juicy" information.

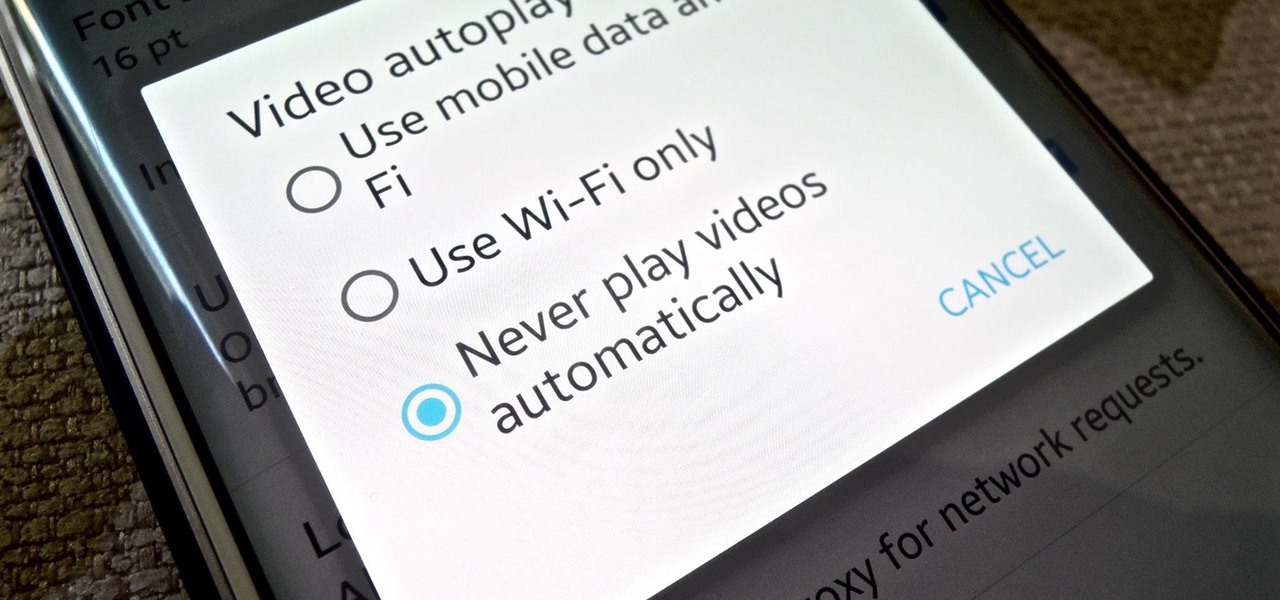
It's bad enough that we have to deal with autoplaying video advertisements all over the Web, so why do we have to be subjected to autoplaying videos on Twitter, too? Autoplay video are muted by default, but that doesn't make them any less annoying, especially if you have a small data plan on your phone.

When we hack a web server, we usually want to be able to control it in order to download files or further exploit it. There are many websites that let you upload files such as avatar pictures that don't take the proper security measures. In this series, I will be showing you how to gain root access to such a web server.

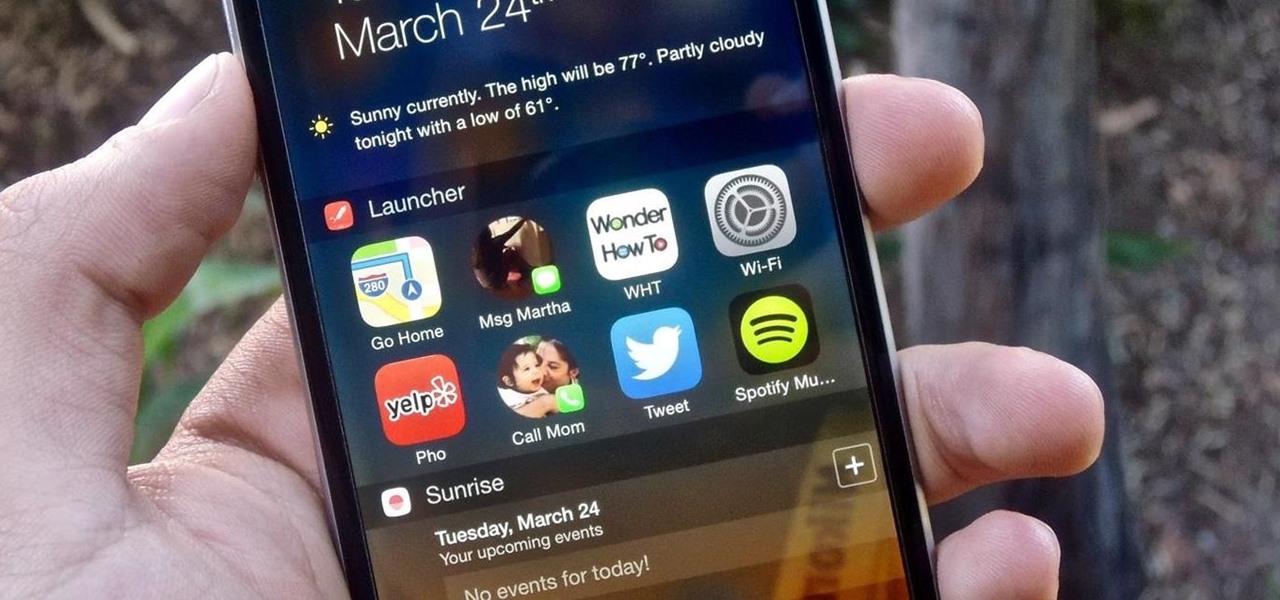
An app called Launcher was released for iOS 8 last September that let users open any installed app directly from a widget in the Notification Center pull-down. For some reason, Apple didn't take too kindly to this and banned Launcher from the iOS App Store just a few days after its release.

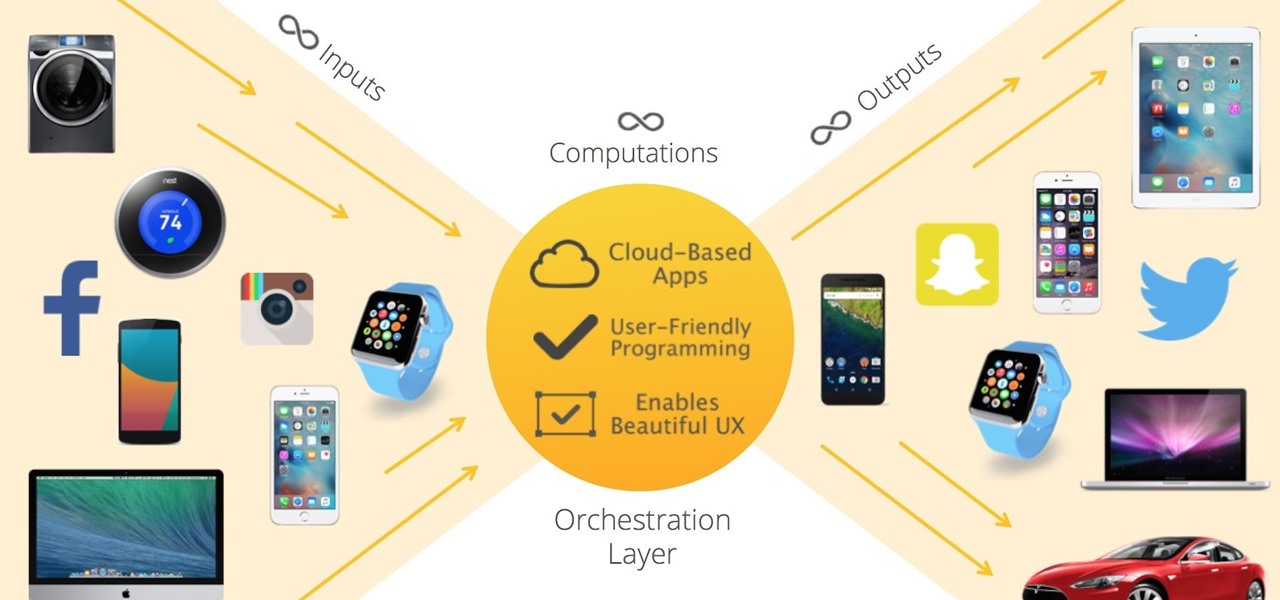
Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.

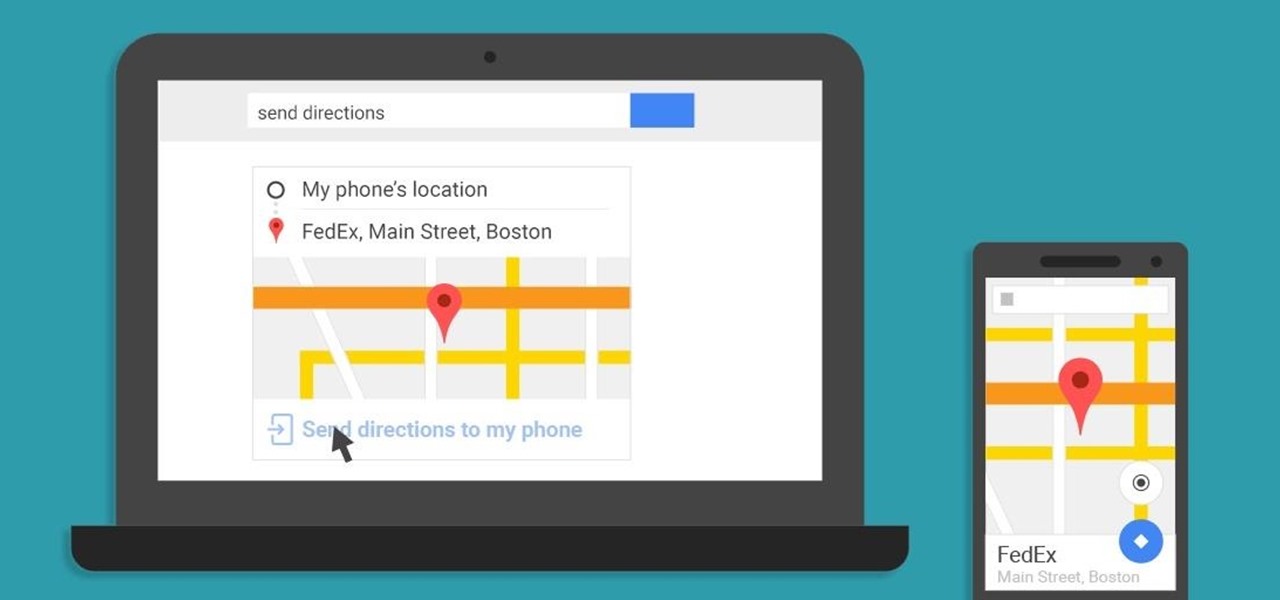
A set of cool new Android-related Google Search functions made their debut this week, which will allow you to locate your phone, send directions to your mobile device, set alarms and reminders, and send notes from any web browser.

By now, nearly everyone with any type of media access is aware that Sony Pictures Entertainment was hacked on November 24th. Although there can be many interpretations and lessons drawn from this audacious act, there is one indisputable conclusion: it and its ripples across the globe underlines how important hacking has become in our all-digital 21st century. As I have emphasized so many times in this column, hacking is the discipline of the future. From cybercrime to cyber intelligence to cy...

Amazon just signed a deal with HBO to host the cable channel's original content on its Instant Video service. For those of us with Amazon Prime accounts, this is great news—but there aren't any readily apparent options for playing it on Chromecast.

Welcome back, my fledgling hackers! As nearly everyone has heard, Target Corporation, one of the largest retailers in the U.S. and Canada, was hacked late last year and potentially 100 million credit cards have been compromised. Happening just before Christmas, it severely dampened Target's Christmas sales, reputation, and stock price (the company's value has fallen by $5B).

While the Play Store has a plethora of apps available for finding lost Android phones, Google came out with its own web-based application, Google Device Manager, earlier this year to help you keep track of all your Android devices and remote lock, erase, ring, and track if need be.

Need to clear you cache? This guide details how on any web browser (Chrome, Internet Explorer, Firefox, Opera, Safari, Internet, and Dolphin) for any platform (Windows, Mac OS X, iOS, and Android). What Is the Cache Exactly?
There has been much talk about how unsecure the cloud is because of PRISM’s newfound ability to demand all of your data without any resistance. This has spin doctors in the Cloud Storage industry losing their mind. They suddenly went from a central hub for 10GB of your files, to an easy window for Big Brother to track you through. Centralized cloud storage is no longer a safe way to keep your files, but we still need a way to access our files anywhere we go.

Our attention spans have vastly shortened thanks to the Internet and our subsequent procurement of information from it at a rapid pace. It's tough to pay attention to something for a good amount of time, unless it's ridiculously interesting and stimulating. It's gotten so bad for me that I keep checking my phone every ten minutes—I even did it during a midnight showing of The Dark Knight Rises.

A lot of people text nonstop, but there are situations where it's either not allowed or considered rude to use your phone. Let's say you're in class or in a meeting at work, band you're expecting an important message or phone call. Rather than trying to check your phone discreetly, wouldn't it be better if you could just see your calls and messages on your computer?

Yesterday, Microsoft released the customer preview of its newest version of Office, the first version optimized for both touchscreens and desktop systems. The entire suite got a much-needed facelift and a few new cool features. Here are some of the most notable changes.

Watch this video tutorial to learn how to book the best hotel room for your money. You've spent all year saving up for your dream vacation. The last thing you want is to end up in a hotel room that ruins the whole trip.

California is struck by earthquakes everyday, but the biggest ones, on average, appear every 150 years, just south of the San Gabriel Mountains. The last super-destructive earthquake in California was over 300 years ago, which could mean a long overdue Californian earthquake is on the horizon.

We don't know about you, but we're wondering how the hell Katy Perry even has time to work out these days with the countless number of promotional appearances, hostess jobs, planning a wedding, and singing gigs she's doing on a daily basis. But, after looking at a few recent pictures of the singer's fit and curvy body, she must be doing something to keep all that in shape.

Aliens… do they exist? Can anyone say for sure? No, but some do swear of their existence, and some swear on a more personal level, although some say that alien abductions are going a little "too" far in proving aliens exist. But a more common staple of proof of aliens are UFOs, or Unidentified Flying Objects. UFOs have been sighted all over the world, even by the military and NASA, so who's to say they're fake? I guess you, especially if you're the culprit behind it…

Do you swoon over Justin Bieber and wish you could have him all to yourself? Though he's probably not going to pay a personal house call to you anytime soon, you can draw yourself a very lifelike picture of him!

Do you find yourself getting rocked by your friends and relatives whenever you play Wild Ones on Facebook? A little more money would help right? This video will teach you how to use an easy cheat to acquire a theoretically infinite amount of money and coins. All you need are two Facebook accounts and two different web browsers and you can do this easily. Now get in there and buy yourself a better pet!

This educational safety video is geared toward public and private utility workers and linemen who need to remove pole tops while dealing with high-voltage electrical cables and electrical insulators. It discusses the proper pole topping removal procedure and demonstrates effective procedures for removal.