
How To: Superimpose images with a green screen and chroma key
This video gives a ten minute tutorial on how to achieve the superimposition effect for web videos with a little props and software.


This video gives a ten minute tutorial on how to achieve the superimposition effect for web videos with a little props and software.
In this video tutorial, Chris Pels will show how to use a control adaptor to provide different renderings for an ASP.NET server control without actually changing the control itself. In this video, an ASP.NET BulletList control will be adapted to display each list item horizontally using div elements instead of the traditional ul elements. First, see how to create a class that inherits WebControlAdaptor and then implements the code to render the new list format. Next, learn how to map the new ...
While sliding doors is far from a new concept and will be obsoleted once we see wider support for multiple backgrounds (CSS3), it is still a good one for your bag-of-tricks. The theory is that if we have an extra hook in our markup, we can apply two overlapping background images to a single spot of text. When that text grows or shrinks, these overlapping images and reveal more of themselves creating the illusion it is a single expandable graphic. In this video screencast, we do a quickly exam...
This video covers creating and programming a a PHP-based web forum. Topics include basic layout, login and logout, Admin start, creating categories and subcategories, creating topics, and more...

There are some very powerful tools in CINEMA 4D that you can use very quickly to create some 3D graphic elements. Once you start practicing you'll find it may be easier to create your own reference than to find the "just right" one on the web. So, if you're in need of some barbed wire, for reference or otherwise, check this tutorial out. Of course, it takes quite a bit longer to actually SHOW you how to create the barbed wire (creating the barb, wrapping it around the wire, using MOGRAPH in o...

As a Boy Scout, when the First Class rank is attained, a scout has learned all the basic camping and outdoors skills of a scout. He can fend for himself in the wild, lead others on a hike or campout, set up a camp site, plan and properly prepare meals, and provide first aid for most situations he may encounter. A First Class scout is prepared.

Add even more personal touches to your crocheted items. This how to video is a tutorial on how to embroider crochet projects using the lazy daisy stitch. You can embroider just about anything with the daisy stitch. Watch and learn.

Are you going out in that little black dress that you've always wanted, but you don't know what to accessorize with? Well, The beauty of the little black dress is that you can accessorize it to reflect your personal style. A fashion designer shows you how to incorporate funky and classy pieces into your wardrobe.
If you're a hacker, pentester, or any other type of Null Byte reader, and would like to create a website to showcase your services and skill set, you may not have the time or energy to do it the long way.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.
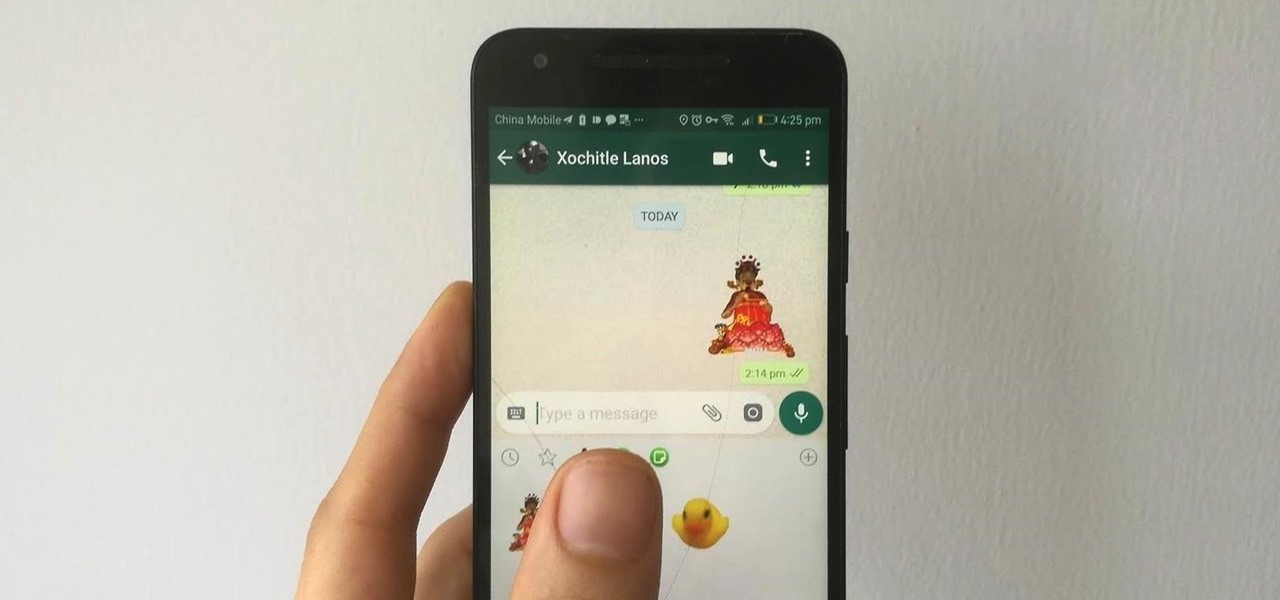
WhatsApp stickers can make your chat more fun. The stickers that come with WhatsApp are fine, but they're standard and accessible to everyone. What if you wanted to show off unique stickers that your friends haven't seen? To take things to the next level, you can create your own WhatsApp Stickers.
Canary tokens are customizable tracking links useful for learning about who is clicking on a link and where it's being shared. Thanks to the way many apps fetch a URL preview for links shared in private chats, canary tokens can even phone home when someone checks a private chat without clicking the link. Canary tokens come in several useful types and can be used even through URL shorteners.

Among the younger generation, Roblox rivals major titles like Minecraft as one of the most popular online games out there. In fact, it's common to hear children tell new playmates to "friend me in Roblox!" so they can play together online. There's nothing inherently sinister here, but with all the online interaction, kids' safety becomes a factor.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

Over the years, we've seen security breach after security breach, as well as high-profile data scandals where collected personal information was misused by companies. Apple makes customer privacy a priority, so there have been few issues to worry about when it comes to its services on your iPhone. However, there are still plenty of privacy settings to explore and change, especially within Safari.

The iOS App Store is a big place, offering over two million applications in total. However, there are actually some apps you can and should install on your iPhone that the iOS App Store doesn't include. And no, these apps do not require any difficult jailbreaking or complicated sideloading techniques — they are really simple to install.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

Despite their sometimes fluffy reputations and occasionally ethically compromised viewpoints, tech evangelists are important, don't let anyone tell you otherwise. The right passionate voice behind the right technology platform or piece of hardware can sometimes spell the difference between fostering a community of potential users and watching a product die on the vine.

While iOS 11.3 doesn't have as many new features as iOS 11.2, there's still a lot to love about Apple's latest update for iPad, iPhone, and iPod touch, even if some of the best features we were expecting didn't make the cut.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

There is an Indian story called the Legend of Paal Paysam, and while it doesn't seem like it at first, it has a lot to say about what motivated Paul Travers in the augmented reality space.

Greetings my fellow aspiring hackers,

Brand loyalty is one of the main factors behind our decision to choose a particular mobile device, but it doesn't have to be the entire equation. Educated consumers know that certain devices simply fit their budget and usage better than others, which means you can't always let a logo dictate what kind of phone or tablet you buy.

I have been on Null Byte for a long time, a very long time and. I havent always had an account here, ive like many of you also have, been looking and decided to make a profile to contribute.
There are a bunch of new and interesting features packed inside of Windows 10, but one of the most exciting ones is the Microsoft Edge web browser, the long-awaited replacement of Internet Explorer.

The telecommunications industry has come a long way since Ma Bell opened the first telephone exchange in the late 1800s. With the advent of fiber optics and wireless broadband technology, we no longer have a need for a dedicated phone connection, as today's data networks can carry much more than a simple voice conversation.
Canvas fingerprinting is the web's trickiest privacy threat, but it's not impossible to stop. With all the media attention it's gotten lately, it's time we lay out exactly how to detect and prevent this invasive tracking technique.

Google recently updated the camera software for the Nexus 5, and in doing so, made the app available to all devices running Android KitKat. This means that not only do we get a nice new camera interface on our phones, but we also get the benefit of an expanded development community.

Video: . Optimize your Marketing with a Mobile Website

You may or may not have heard of alt-rock band Panic! at the Disco, but a year and a half ago they released a single called "The Ballad of Mona Lisa", which had an accompanying music video that was Steampunk-themed. In fact, here's the video:

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...
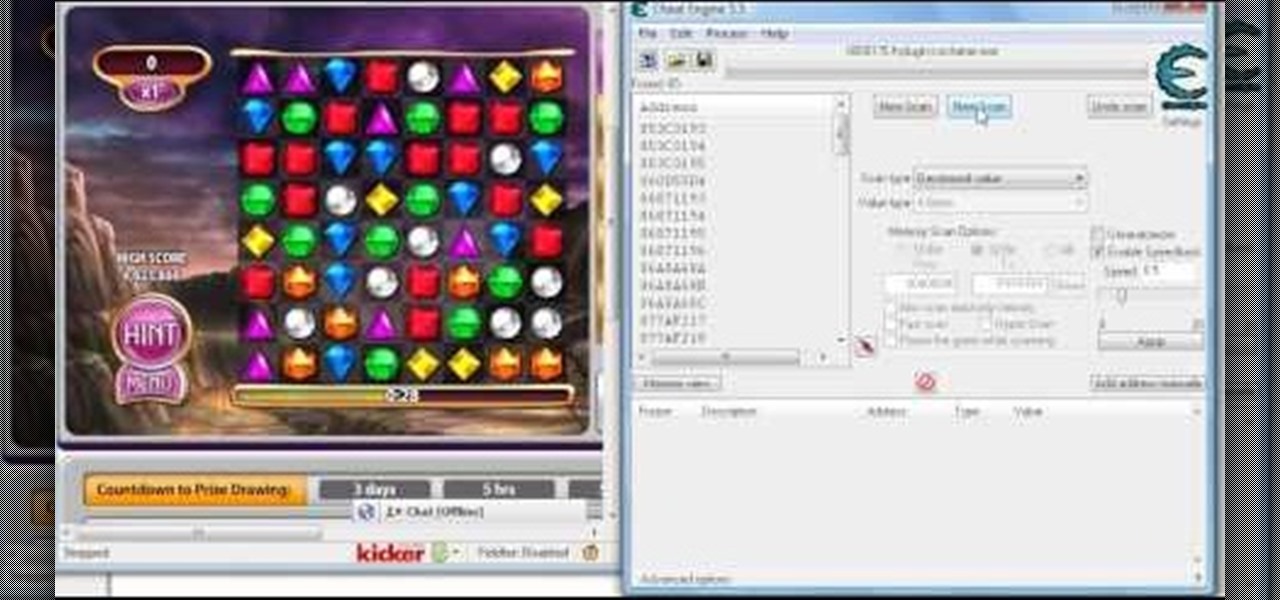
Don't let Bejeweled Blitz get the best of you. Show it who's boss and get the highest score possible. Of course, you'll need Cheat Engine to overpower the game, so make sure you have Cheat Engine 5.5 or higher and check out this video for the hacking Bejeweled Blitz (10/09/10).

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

Would you know what to do if someone ingested poison? Equally important, would you know what not to do?

Rumors, gossip, exclusion. Mean girls have a lot of weapons in their repertoire – here's how to combat all that nastiness.
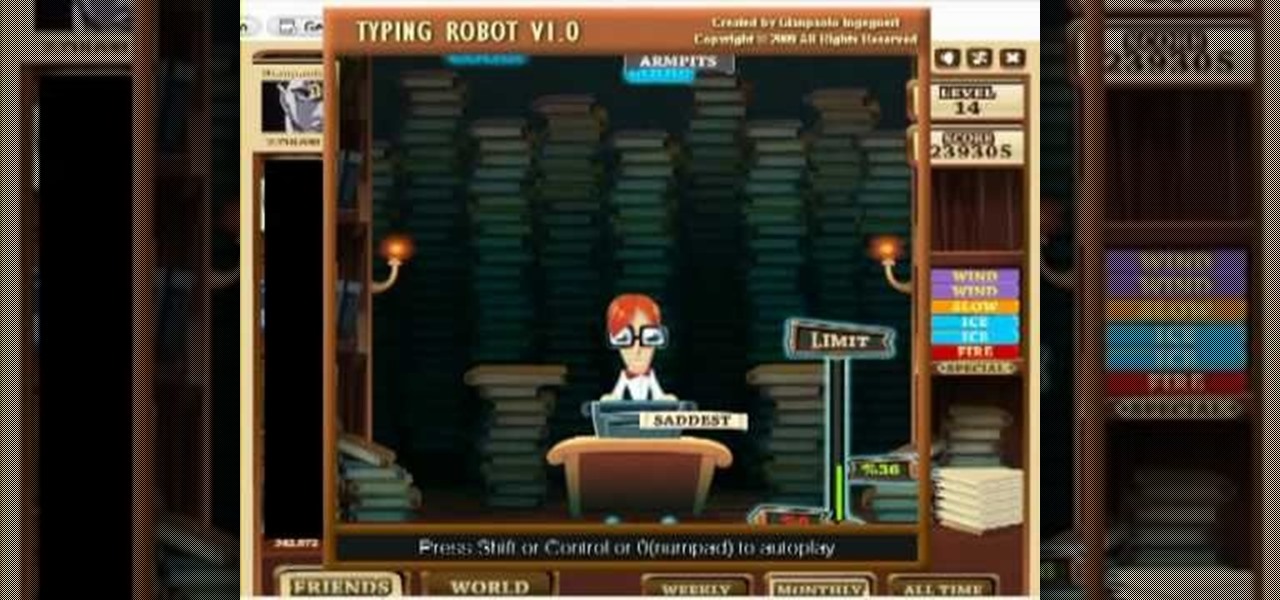
http://www.texturemind.com/post463/ TypingRobot is an artificial intelligence studied to increase your points record with the Typing Maniac game on Facebook. It can recognize several labels because it uses a powerfull OCR system (tesseract) and some principle of word correction. With this program you can make millions of points without problems (my personal record is about 2.700.000 points).
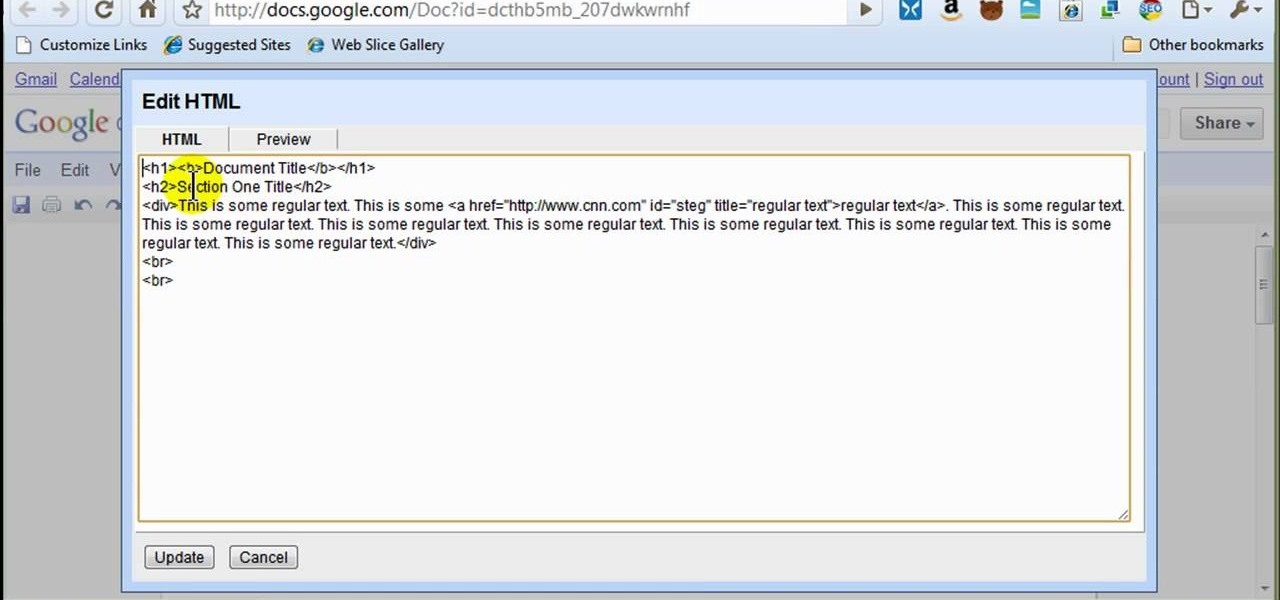
In this how to video, you will learn how to style documents with the Google Docs CSS editor. First, create a new document in Google Docs. First, click on the drop down menu for style. Type in a title in the document. Select heading 2 in the menu and type in the section title. Next, take off the style and type in the body for the content. Select some of the body text and click the hyperlink button. Type in the address and click okay. Now you can click this text to go to a website. Go to file a...
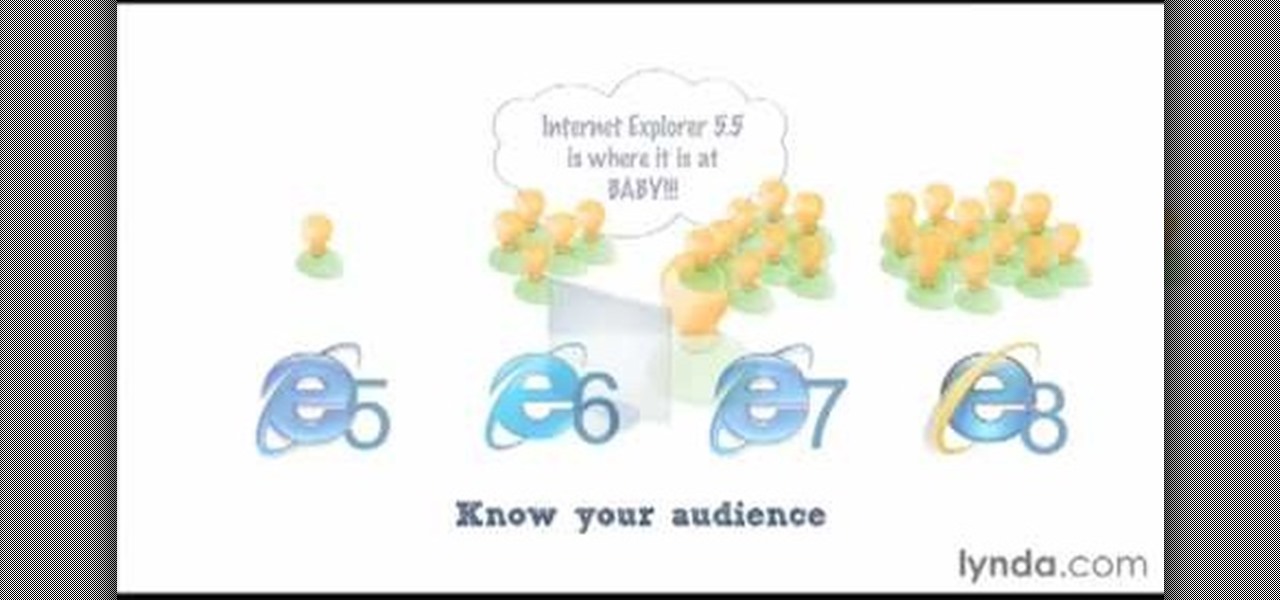
James Williamson for Lynda demonstrates designing for multiple browsers. The most frustrating aspects of web design is constantly dealing with the settle and some times not so settle differences in browser rendering. While they moved to a standard spaced, CSS control presentations has made life infinitely easier for web designs. Dealing with bad browser behavior is one of most unfortunate side effects. All browsers render our pages same because each browser reads and renders the HTML and CSS ...

Nothing says you care like a hand-made card. Show that special someone what they mean to you or just have fun with this cute arts and crafts project. Get your markers and colored pencils. Get your glitter and glue. Get creative.