Antibiotic use in infants has been associated with a host of childhood conditions later in life. Yet when an infection is suspected in a newborn, usually a sample of their blood is drawn to check for the presence of bacteria and 5 to 8 percent of them receive antibiotics while the diagnosis is pending.

Sky Zhou, also know as Matrix Inception on YouTube, is no stranger here on NextReality. We loved his Pokémon concept game for HoloLens, as well as his D3D Keyboard that lets HoloLens users leave notes around the house. He just can't seem to stop creating cool mixed reality apps, and he's already got another one in the works.

In this first part of our tutorial series on making physical objects come to life on HoloLens, we are going to set up Vuforia in Unity.

No one can dispute the evolutionary success of bugs. The oldest insect fossils were found encased in crystallized mineral silica in Scotland in 1926, and they're between 396 and 407 million years old.

Students from Carnegie Mellon University's Entertainment Technology Center have been working on an augmented reality system to help teach music in a project called Music Everywhere.
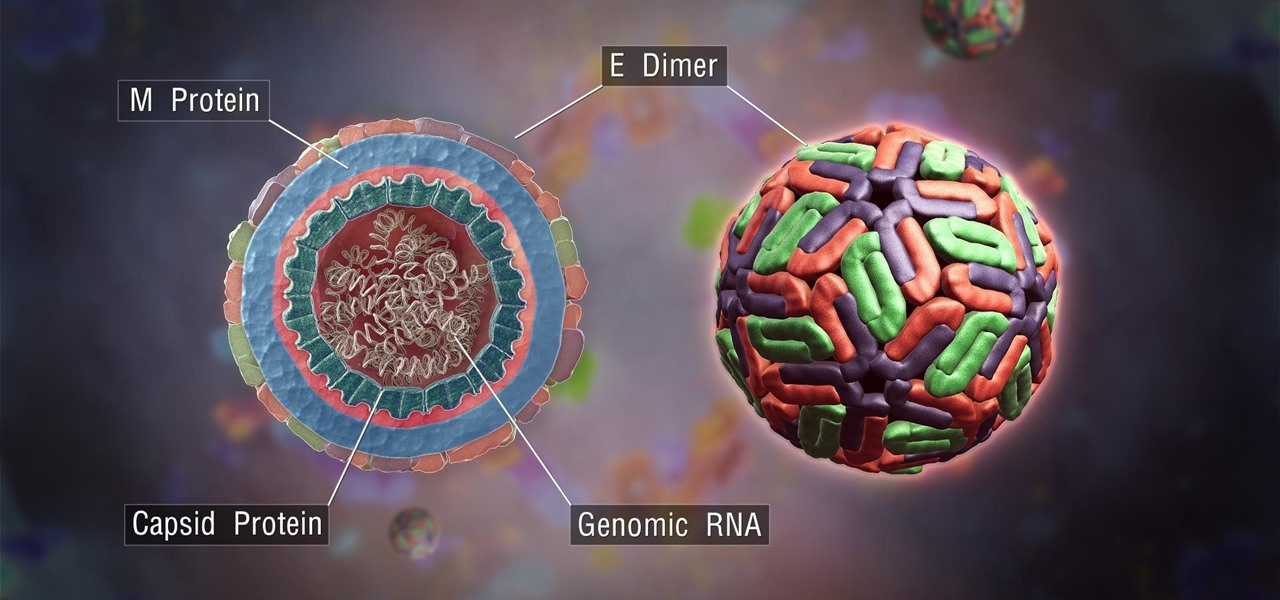
The mention of Zika can strike fear in the hearts of pregnant women. With infections increasing around the world, including in the US, researchers are fighting the clock to figure out how the virus can have such horrific effects in some people.

For some time now, there has been quite a bit of speculation as to when the selection of augmented and mixed reality head-mounted displays would begin to trickle out to the public. Pricing, availability, and software selection are all issues that will have to be addressed before widespread adoption will start.

When a dead body is discovered, finding out when the person died is just as important as finding out how the person died. Determining the time of death has always involved lots of complicated scientific detective work and less-than-reliable methods. However, a study by Nathan H. Lents, a molecular biologist at the John Jay College of Criminal Justice in New York, is the first of its kind to show how microbes colonize a body's ears and nose after death.

If you follow tech, you're probably familiar with Siri, Apple's personal voice assistant, which has been integrated heavily into iOS ever since iOS 5. But you might not have known that Siri is capable of performing some tasks when the iPhone is in a locked state. The default state of iOS is to allow access to Siri from the lock screen, most likely for the convenience of hands-free access to the phone.

Fall is here, and it's time for warm, filling meals... that don't involve a lot of effort, because it is getting cold outside and you spent a full day at work wishing you were on the couch with a blanket over your head, dammit.

Although professional sports has been no stranger to emerging technology, it still seems hard to think about how a football player might benefit from strapping on a VR headset. While it won't do much in an actual game, many athletes can improve by using virtual reality as a training tool.

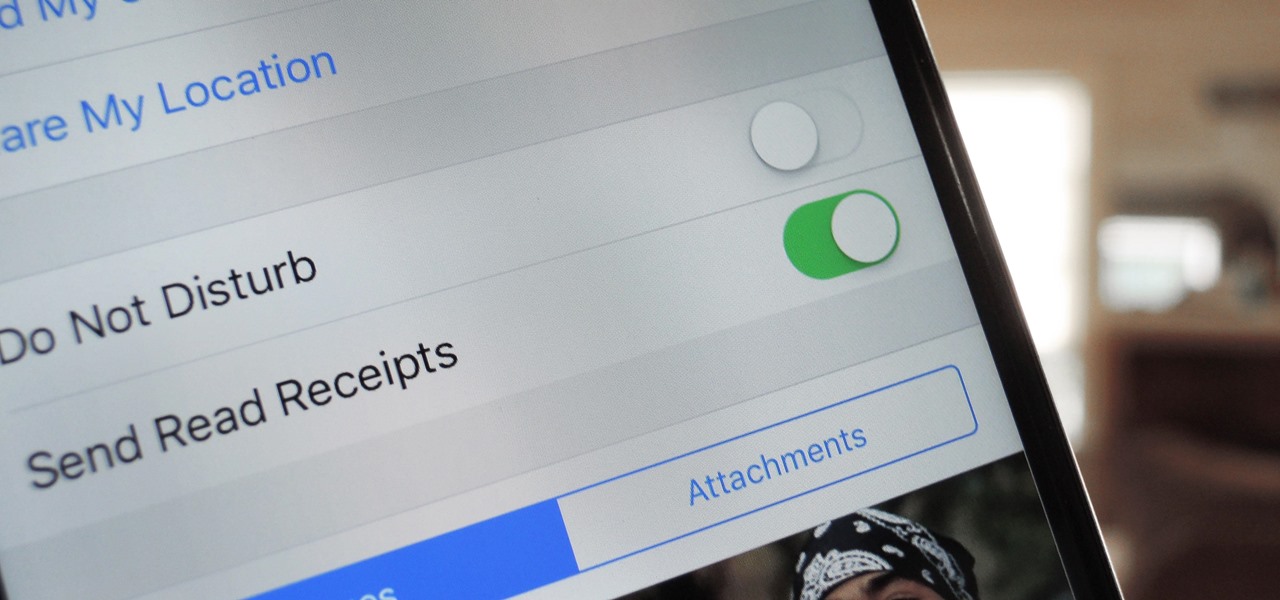
With iOS 9.3.5, as well as all of the versions prior to that, you had two choices when it came to "Read Receipts" for iMessage — either on for everybody or off for everybody. So if you weren't comfortable with one or two of your contacts knowing whether or not you've read their messages, you had to keep the feature disabled and miss out on Read Receipts for people you're a bit closer to.

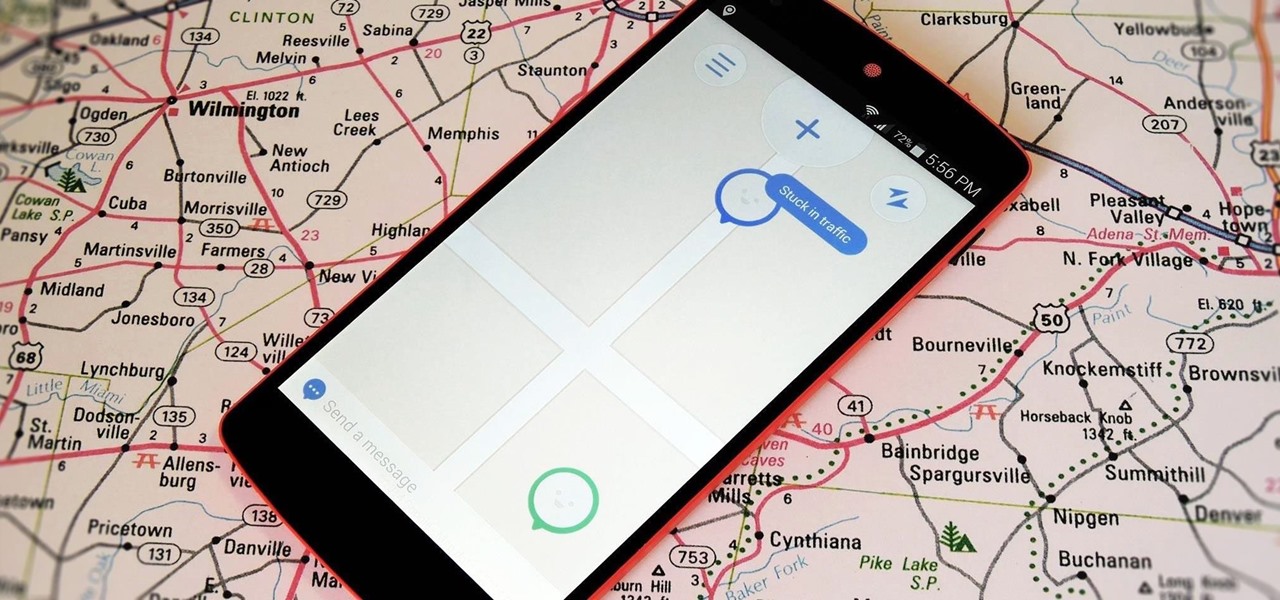
It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

If you already have speakers that you love, you don't need to ditch them for an expensive wireless set for convenience's sake. With products like Chromecast Audio, you can turn any set of wired headphones or speakers into wireless versions for much less, and stream music or audio to them from pretty much any device connected to the same Wi-Fi network.

A video showing what is alleged to be the new Apple iPhone 7 has appeared online. The uploader of the video claims that it was shot on one of Foxconn's assembly lines.

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

Developing GUI apps in python is really cool. I ask those who understand the language to help convert some of the command-line or console programs or apps ( I mean programs that are useful to a hacker ) to GUI. I know GUI makes us lazy and not wanna learn but we should all know its fast. Today's tutorial is on p2p chat app I developed last week and decided to share it with the community since its kinda cool.

Last year, Apple debuted a feature that allows families to share iTunes and App Store purchases across their various accounts. Us Android users, on the other hand, have to buy separate copies of apps for each of our accounts—well, at least from an official standpoint.

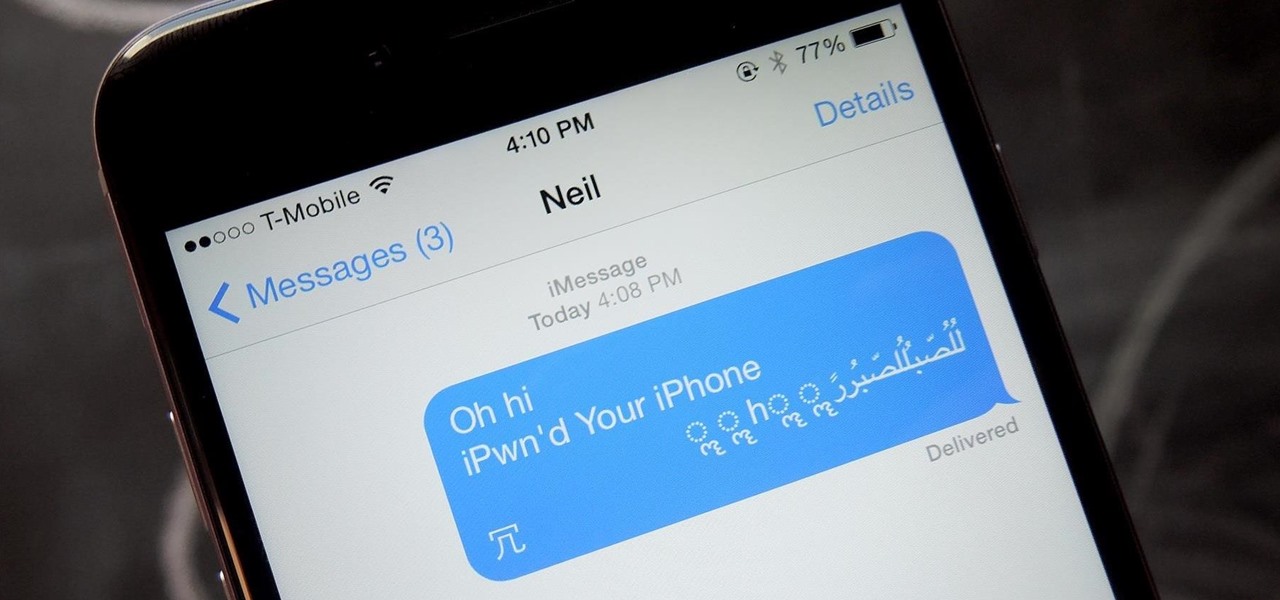
Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out several times here, and to our surprise, it worked perfectly each time.

If a tree falls in the woods and nobody is there to hear it, does it make a sound? If a person makes calls but doesn't have a Facebook account, are they even really a person? Yes, of course they are, but it just makes life easier when you're part of the world's biggest social network, as proven with Facebook's latest application, Hello - Caller ID & Blocking.

With platforms like Facebook, Instagram, and Snapchat available for anyone to take advantage of, I'm all about differentiating from the mundane and repetitive images we see on social media everyday.

Are you a lawyer who's married to a computer programmer? Chances are you might not have even dated if you first met online.

Welcome back, my nascent hackers!

Brought to you by Brother International Corporation. Whether you are looking to complete a home improvement task, or you are hoping to start a new hobby, staying focused and energized during projects can be daunting. With emphasis on organization, planning, and creativity, we gathered together tips that will help you successfully tackle any project on your plate!

Early last year, Google purchased Quest Visual, acquiring the immensely popular augmented reality translator app Word Lens in the process. While Google did put the feature on the Google Glass, they spoke more about implementing Word Lens into their Translate app sometime in the future.

It's becoming more and more apparent that Siri continually drops the ball when it comes to lock screen security. In the past, Siri was exploited in iOS 7.0.2 to send messages without needing a passcode. Then in iOS 7.1.1, Siri was use to bypass the lock screen again to access contacts, make calls, and send emails and texts.

With GPS chips and Wi-Fi positioning systems, a modern smartphone is capable of tracking its user's location with pinpoint accuracy. This being the case, it's strange that the most common text message sent today is still "Where are you?"

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

With the emergence of rumors that Amazon, Google, and Samsung are all making their foray into the gaming console market, it's a possibility that our Android-powered mobile devices might become tools that play a central role.

You don't have to be Drake to realize that some friends are better than others. There are friends you know are only there for the party, and friends who actually listen when you whine about your life. There are friends you go out with for a beer, and friends you call when you're drunk and need a lift at 4am.

Welcome back, my tenderfoot hackers! I recently began a new series on digital forensics to help tenderfoot hackers from being detected and ultimately, incarcerated. In this installment of that series, we will look at recovering deleted files. This is important to hackers because you need to know that even when you delete files on your computer or on the victim's computer, a forensic investigator can usually recover them.

I miss the days where my hardest assignment was drawing a Thanksgiving turkey using the outline of my hand and trying to stay in between the lines. It seems that there is some unwritten rule that adults shouldn't feel the need to draw. Well, not anymore.

Snapchat was created for the sole purpose of removing evidence from your mobile that a photo or video ever existed. That way, snoopers can't find any of these questionable selfies in your photo gallery. Of course, there are plenty of ways around this safeguard, but it's still more private than the standard social networking app.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

If you're new to Android phones, one of the first things you've probably noticed is how notification alerts differs from Apple devices, especially in regards to getting a text message.

If you're a frequent Snapchatter like myself, you're probably well aware that Snapchat can't stop you or anyone else from taking a screenshot of a photo received. Instead, they notify the sender that a screenshot was taken—a greatly appreciated fair warning when impetuous photographs are involved. However, there is a loophole to this.

Hello! My latest interest is screenwriting. I would like to share a few hints I find quite useful. I am a newbie, so the following post will not be taken from the treasury of many years of experience. Just plain facts,.. Thanks for reading! Step 1: In the Beginning

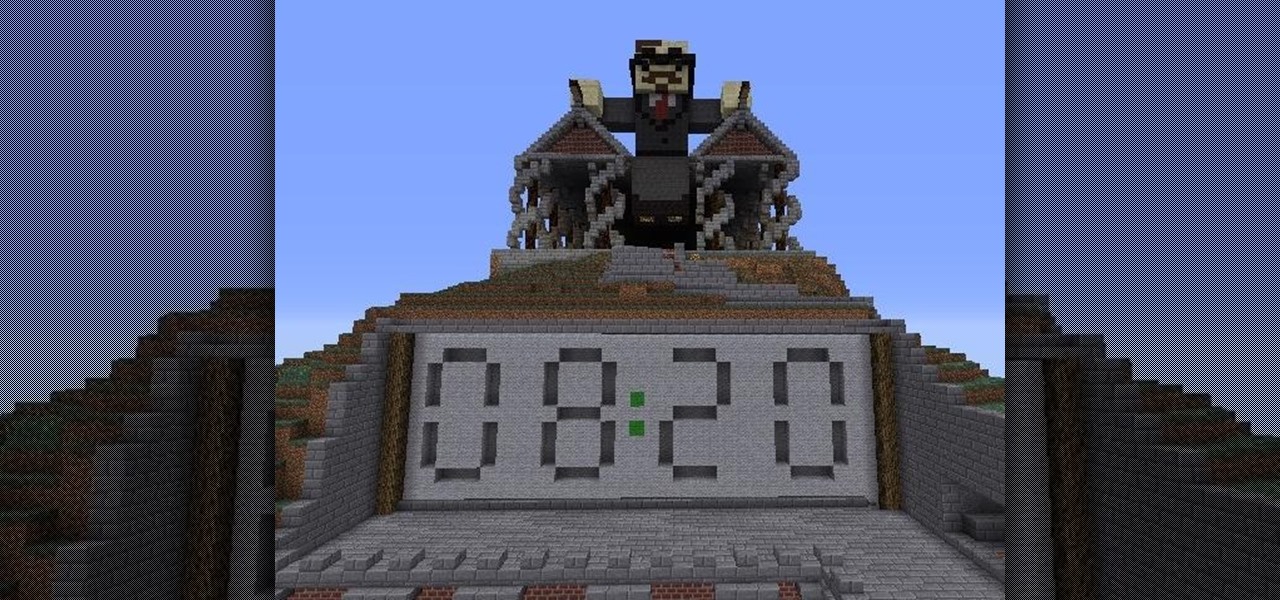
A redstone clock is a pretty easy mechanism to make. A digital readout for that redstone clock is a little harder, and that's what Lesnoydude has made that won him the staff choice award.

Welcome! Today I would like to share a few hints about picking the right color. So, if you do not know what color your today's outfit should be or your or which color you should choose for your room walls, please follow my suggestions.