When you make or receive a call on your iPhone, you're forced to use the built-in ear receiver at the top of the phone to hear anything—unless you're already connected to a Bluetooth device. If you don't have Bluetooth in your car, or prefer to just use the speaker instead, having to manually switch to speaker mode can get annoying real fast.

Facebook Messenger is getting ready to roll out a Snapchat-esque feature that will let users send messages that self-destruct after a certain amount of time, so you'll have an extra level of security when you need to send sensitive financial information or, more likely, risqué texts or images.

The team behind Minecraft, the popular open-world game beloved for its freedom to create and build, has teamed up with Oculus to release an official edition that takes you even further into the block-based world using a Samsung Gear VR headset. While the Oculus Rift version itself is still forthcoming, Gear VR users can play right now.

Developers across the U.S. and Canada have started getting their augmented reality headset packages from Microsoft, and so far, everyone's raving about one gaming experience that shatters all doubts of just what the HoloLens can do... RoboRaid.

Speeding tickets suck, and I don't know a single person that can tell me otherwise. But the reality is, most of us will break the speed limit for one reason for another, regardless of the pricey risk.

Welcome back, my novice hackers! As many of you know, recon is crucial to a successful hack/pentest. In most cases, hackers spend more time doing good reconnaissance than actually hacking. Without proper recon, you are simply guessing at what type of approach or exploit is going to work and, as a result, your time is wasted without any useful outcomes.

Welcome back, my greenhorn hackers! A few years back, Microsoft implicitly recognized the superiority of the Linux terminal over the GUI-based operating system by developing PowerShell. Since Windows 7, every Windows operating system has had PowerShell installed by default, and they even made PowerShell capable of running Linux commands on Windows!

We've been on a constant hunt for the best way to make almond milk at home, and we think this trick might just be the most genius yet.

Cellular carriers like to nickel-and-dime us out of every bit of money they can feasibly justify, so as consumers, we owe it to ourselves to make sure that we're getting our money's worth.

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

Welcome back, my tenderfoot hackers! As most of you know, I am strong advocate for using Linux as a hacking platform. In fact, I would say that without knowing Linux, you will never become a professional hacker/pentester.

Well, here we are. We've come a long way, we really have. Watching this community grow has been amazing. Well, before I start babbling on about the community, let me get to the point...

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

Like a strong-tasting cup of joe, but want more caffeine out of it? Start double brewing your coffee. To paraphrase a big fan of the double brew process on Reddit, it'll make you feel like you can throw an orange at 60 percent the speed of light. It's that strong. Really.

When I first moved to Los Angeles, I rented a bed in a tiny studio. I was too broke to afford my own place, so all I had was a mattress in someone else's apartment. Unfortunately, this person had no interest in cooking, and therefore no kitchen equipment whatsoever. To make matters worse, there wasn't even room for my kitchen equipment. Needless to say, I ate a lot of tubs of Trader Joe's hummus, and frequented a lot of taco trucks.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

There are a lot of great tutorials on Null Byte using Python to create backdoors, reverse shells etc, so I thought it might be worthwhile making a tutorial on how to convert these python scripts to exe files for Windows victim machines.

If you have seen the movie Fast and Furious 7, you know what "God's Eye" is. Well this might spark interest to you.

Welcome back, my amateur hackers! As many of you know, Null Byte will soon be re-establishing its IRC channel. In preparation of that event, I want to show how to set up a secure IRC client with OTR, or Off the Record.

When eyesight deteriorates, either due to illness or advanced age, many people turn to audiobooks as an alternative to reading. With today's technology there is an abundance of services and devices one can use.

Baking is one of life's greatest joys. There's something truly magical about taking a half a dozen humble ingredients, mixing them until they're an odd-colored sludge, tossing them into an oven, and watching them emerge as something elegant and delicious.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

Apple has once again improved functionality of Siri, their personal voice assistant for iPad and iPhone, in iOS 9—and this update is a big one. You can now use Siri to find photos based on location and date, set up contextual reminders, find your friends and family, and more.

With each day that dawns, there is a new, major hack that makes the news headlines. If you are paying attention, there are usually numerous hacks each day and far more that never make the news or are kept private by the victims. Every so often, a hack is so important that I feel compelled to comment on it here to help us learn something about the nature of hacking and IT security. This is one of those cases. Last week, the U.S. Office of Personnel Management (OPM) revealed that they had been ...

Like most people, you probably use hand gestures when you talk, whether you wave your hands excitedly when discussing the latest episode of Game of Thrones or smack the back of your hand as you rattle off points during an argument. As your speech teacher probably told you, gesturing while talking is a great reinforcement tool—when used appropriately, of course.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

Living in Southern California means I don't really have a need to check the weather all that often. But every now and then, I'm caught off guard by a particularly chilly or hot day—no one wants to be the only person walking around with a T-shirt and sandals on a rainy, 50-degree day.

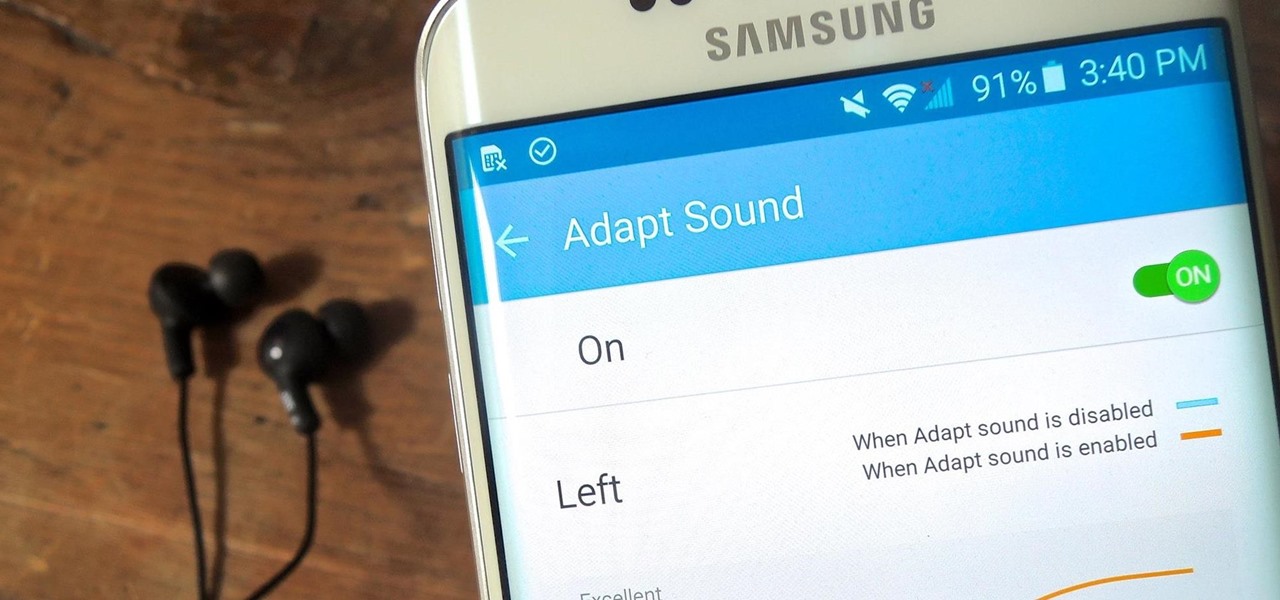
Chances are your hearing isn't the same as the person next to you. Personally, I have moderate hearing loss, so I tend to turn the volume nob towards the loud side. For others, it may be that one ear is slightly better or worse than the other, not only in perceiving volume, but tone as well. Considering this, is it possible for smartphone manufacturers to ensure the best sound quality on their devices?

If you have an Apple Watch, it's easier than ever to ask Siri for directions, send a quick text, or locate the nearest Chipotle—because you don't need to pull out your iPhone anymore. Luckily, Apple made it fairly painless to get Siri up and running on the Watch, so let's go over the two quick activation methods.

There's a built-in timer feature on the iPhone's Camera app that helps you set up your device, step back, and take a photo before time runs out. This feature is useful when there isn't another person around to take a photo of you, or when you don't want to be missing from a memorable group picture. Unfortunately, timers don't always work well. With a timer, no one can sit behind your iPhone to see if the picture is perfectly focused and framed, but that's where your Apple Watch comes in.

Welcome back, my aspiring hackers! Although this article may have been better placed first in this series, I doubt that anyone would have read it when just starting out studying Linux. Now, that you are well into your Linux studies and have some familiarity with how it operates, I'd like to take this moment to explain the philosophy around the Linux operating system.

An Amazon Prime subscription offers free two-day shipping and discounted rates on many Amazon products, while at the same time granting users access to Amazon's Instant Video library. While this service normally runs $100 per year, Amazon CEO Jeff Bezos announced today that the company will be offering a $28 discount on this price for one day only.

Among the many gifts that Italy has bestowed upon the world, culinary and otherwise, pesto stands alone. The exact birthplace of pesto, that herby sauce made of pine nuts and olive oil, is an area of Italy called Liguria, whose microclimate is particularly kind to basil, one of pesto's key ingredients.

Welcome back, my greenhorn hackers!

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Welcome back, my novice hackers! In my series on cracking passwords, I began by showing off some basic password-cracking principles; developed an efficient password-cracking strategy; demonstrated how to use Hashcat, one of the most powerful password-cracking programs; and showed how to create a custom wordlist using Crunch. In this tutorial, I will show you how to create a custom wordlist based upon the industry or business of the targets using CeWL.

Instagram is all about sharing and interacting with others, but sometimes we hide in the shadows and lurk. Whether their ex-lovers, current crushes, former high school classmates, or future coworkers, we silently view their content without them knowing. You can deny it all you want, but we've all lurked at one time or another.

Welcome back, my aspiring hackers! Those of you who use Windows in a LAN environment understand that Windows machines can share directories, files, printers, etc. using "shares." This protocol dates back to the 1980s when the then dominant computer firm, IBM, developed a way for computers to communicate over the LAN by just using computer names rather than MAC or IP addresses.