While change is good, it isn't always welcomed. All software updates with radical redesigns and brand-new features bring at least a few complaints from those accustomed to previous versions. iOS 7 got a lot of flak from iOS 6 users, as did iOS 8 from iOS 7 users.
Whether you're in a movie theater, driving, or just want to temporarily unplug from the grid, you need to ignore or completely silence your phone. You'll still receive calls and texts during this time, but in a world where people expect instant gratification, you'll end up looking like a jerk who doesn't answer back.

Can you tell when someone is shooting you a fake smile? Even though fake smiles are easy enough to see through, we all still do it, attempting to show others just how happy we are when we're really feeling less than fantastic. Unfortunately, every smile we fake makes us a tiny bit more miserable.
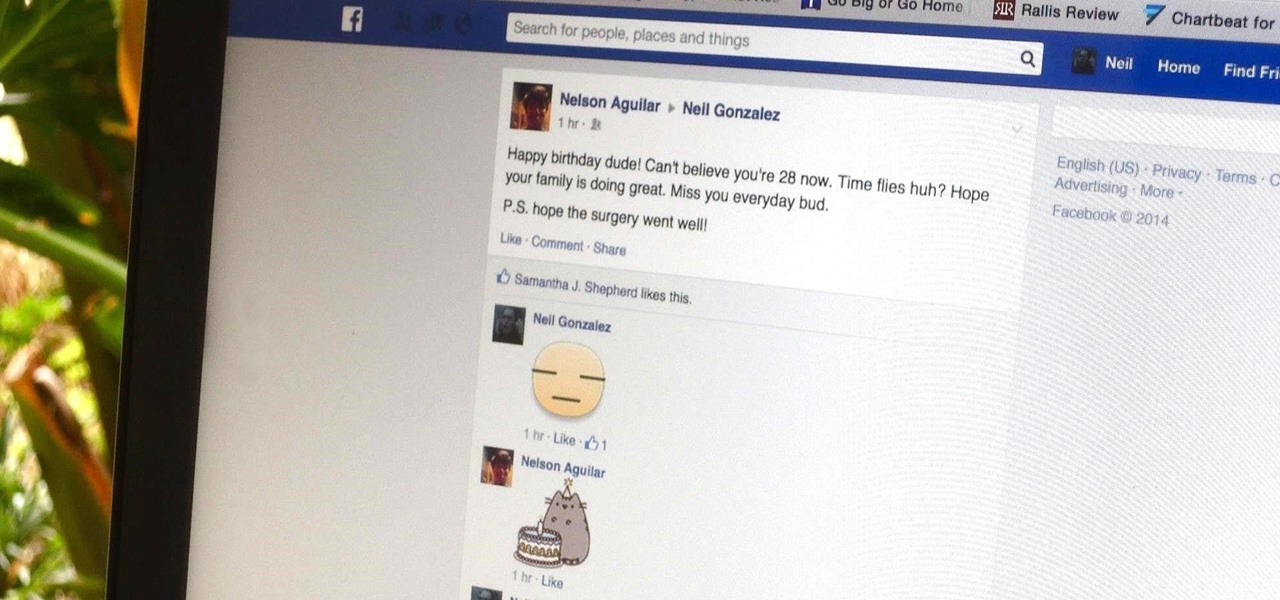
While stickers have long existed in the messages section of Facebook, they've only just recently rolled out sticker capability in comments for events, groups, and timeline posts. That means you can now reply with a cute sticker of a cat eating a slice of pizza on someone's status instead or writing something more thoughtful. While an animated sticker can show off enthusiasm and excitement that words or a too-simple emoji may not be able to convey, you can bet that your comment section will qu...

Welcome back, my novice hackers! Before we try to attack a website, it's worthwhile understanding the structure, directories, and files that the website uses. In this way, we can begin to map an attack strategy that will be most effective.
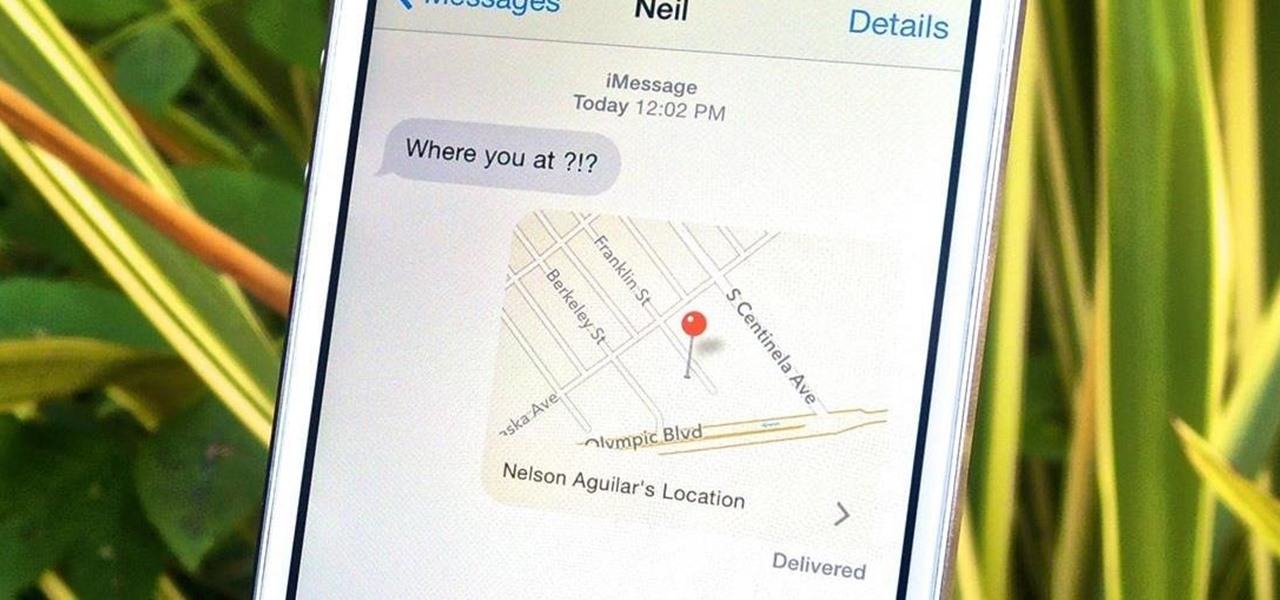
In certain situations, it can be a little difficult to get a handle on my exact location when others ask where I am or how to get to me. Now, thanks to one of the newly introduced features on iOS 8, I can easily share my exact location with friends, right from within the Messages app on my iPhone.

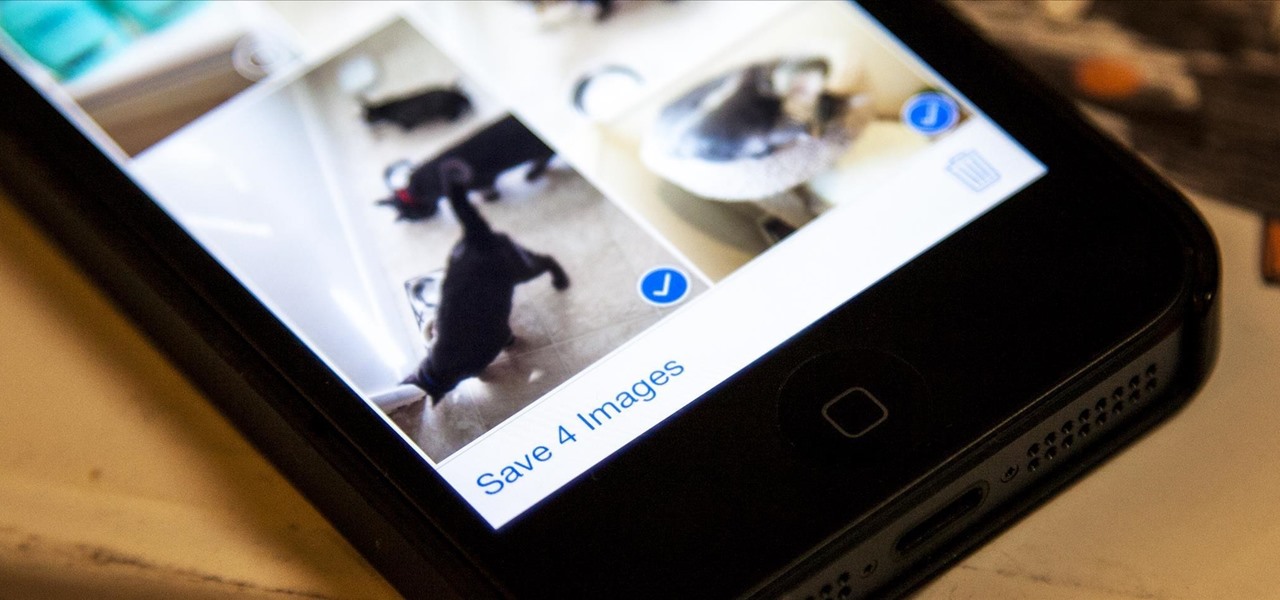
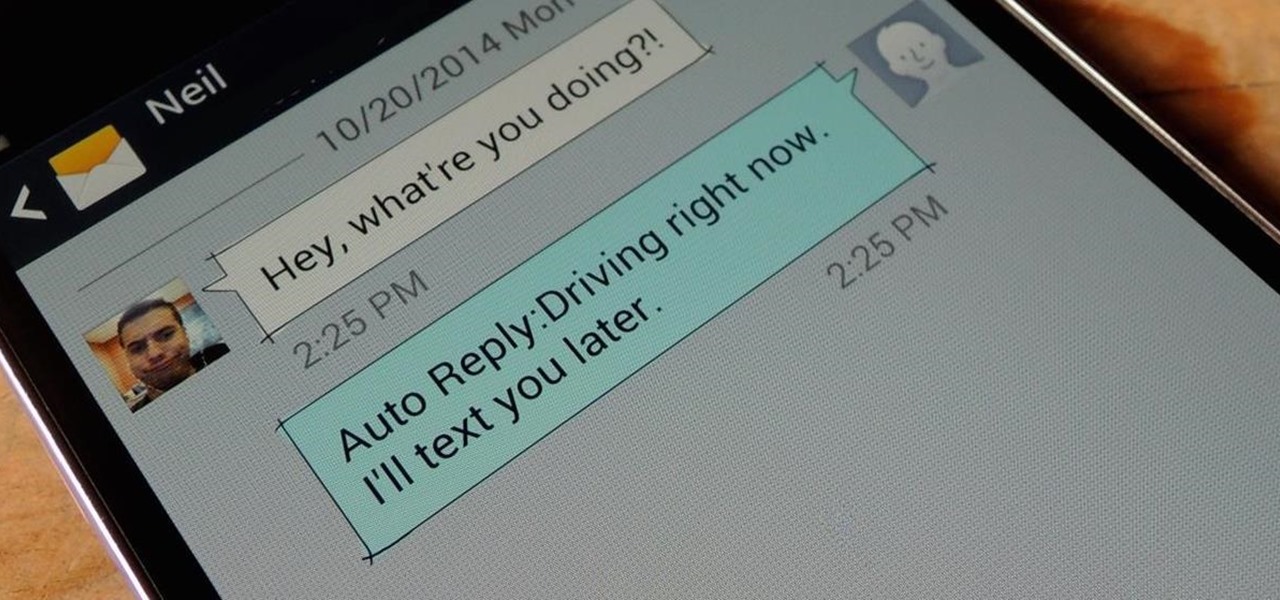
Viewing all of the attachments in a message thread within iOS 7 has never been particularly easy. To see every single picture and video dating back to the beginning of the conversation, you have to manually scroll through the entire conversation and refresh it until all of it appears on your screen. Depending on how long the conversation is, that could take some time.

Sometimes, it helps to be prepared before jumping into a new relationship; look before you leap! To have a healthy relationship with someone who has an STI, it is advisable that you enter the relationship knowledgeable about sexually transmitted infections and what your risks might be.

These days, phones are more like portable entertainment systems. It's a hybrid mobile device for gaming, texting, watching movies, and listening to music more than it is an actual "phone" that you talk on.

For some reason, when you're typing in landscape mode, Android extends the text input field to cover every bit of the screen that the keyboard's not occupying. This gets pretty annoying sometimes, especially with messaging apps where you might need to reference what the other person just said in order to properly form your response.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

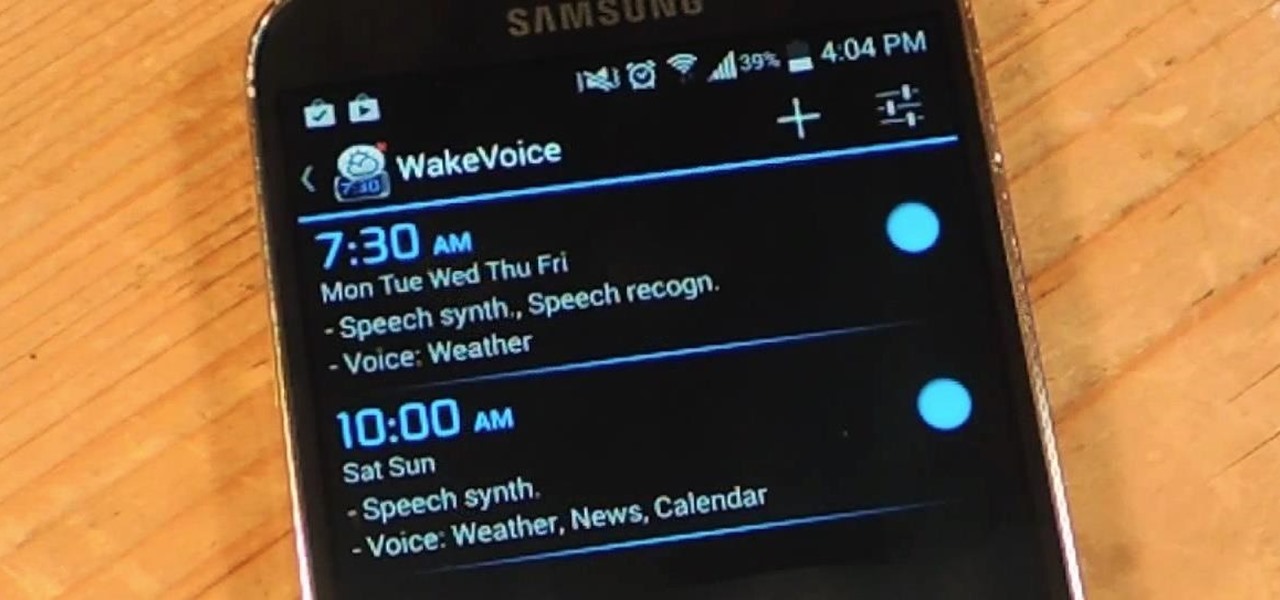
My stock alarm clock does exactly what it's supposed to—it wakes me up. But for those really tough mornings when I just need to hit the snooze, getting my head out of the sheets is a no-go. This leads to trying to find my phone with an outstretched arm, which means knocked-over water glasses and my phone falling under my bed—even more out of reach. Ugh!

It looks like Snapchat, it feels like Snapchat, but after using it for a few minutes, you realize there is a huge difference between Facebook's new Slingshot app and the Snapchat we've all grown so accustomed to.

They say that behind every joke is a half-truth. If that adage itself contains a grain of verity, the Daily Show's satirical Glass piece should raise a few eyebrows amongst the Glass Explorer community.

Prying into people's lives without them putting up their guard can be difficult, unless you can convince them that you already know them very well. Most people don't have many friends they can be honest with, and this can be exploited. Once they're convinced you already know their secrets, they'll start to fill you in on the little details.

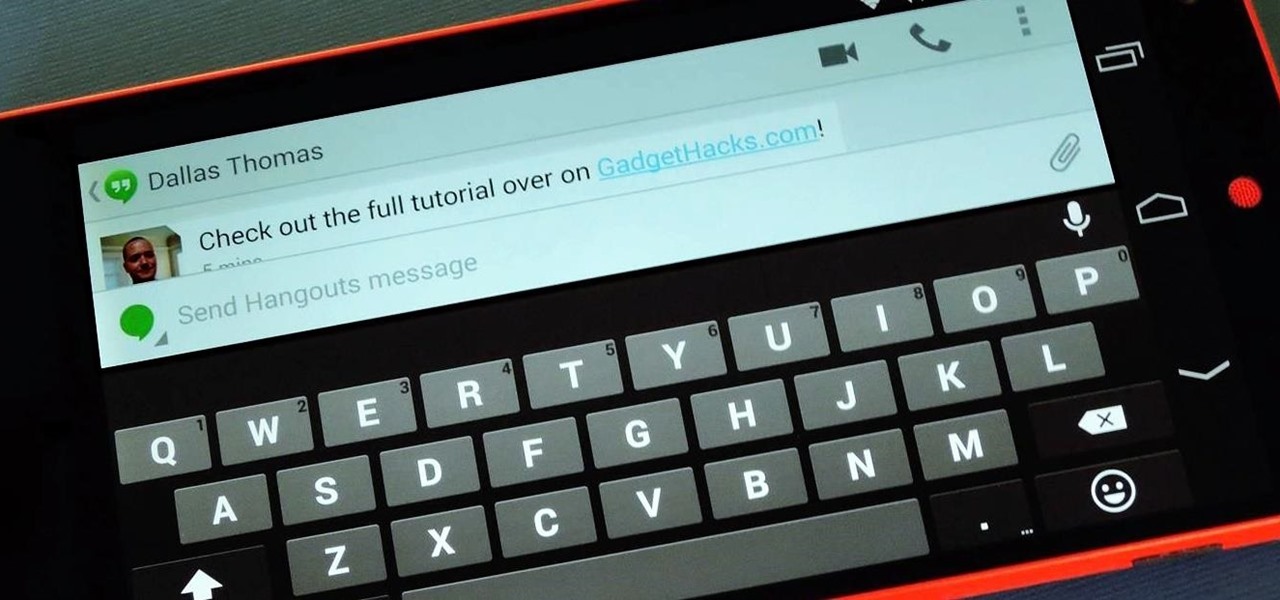
The official Google Hangouts app has been around for a while, and is the standard messaging app on Nexus devices, but Google didn't make each version equal. On the iOS version, you get the feature of adding "stickers"—GIF emoticons—but Google left that out of the Android version.

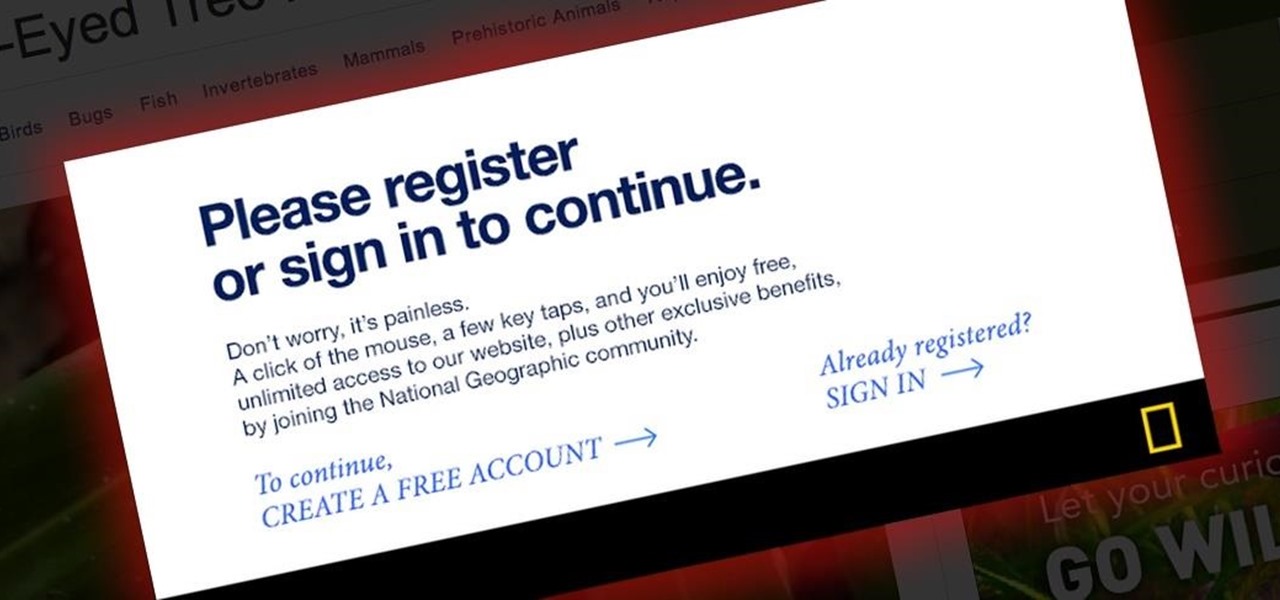
Last night, I was reading a riveting National Geographic article on the green-eyed tree frog, until I was quickly interrupted by an annoying popup asking me to "create a free account" or "sign in." Really, I'd like to do neither. I just want to read about tree frogs.

Erudite. Barbiturate. Cacophony. Denouement. Okay, that last word is technically French, but words like these make the average person sweat, and it turns out that the key to learning how to pronounce them once and for all just might be getting them wrong.

There are many mods and tweaks you can do on your Samsung Galaxy S4 to make it feel more fresh, like using a more customizable keyboard and a better PIN unlock, but if you want to make your Galaxy S4 feel even fresher, add a little Galaxy S5 touch to it.

Welcome back, my tenderfoot hackers! We have looked at a number of ways that we sniff traffic on the network with such tools as Wireshark, tcpdump, dnsiff, and others, but each of these tools is only capable of pulling packets off the wire.

I don't mean to offend anyone, but some phone calls are just plain boring, and being put on hold is shittier than eating three-day old sushi.

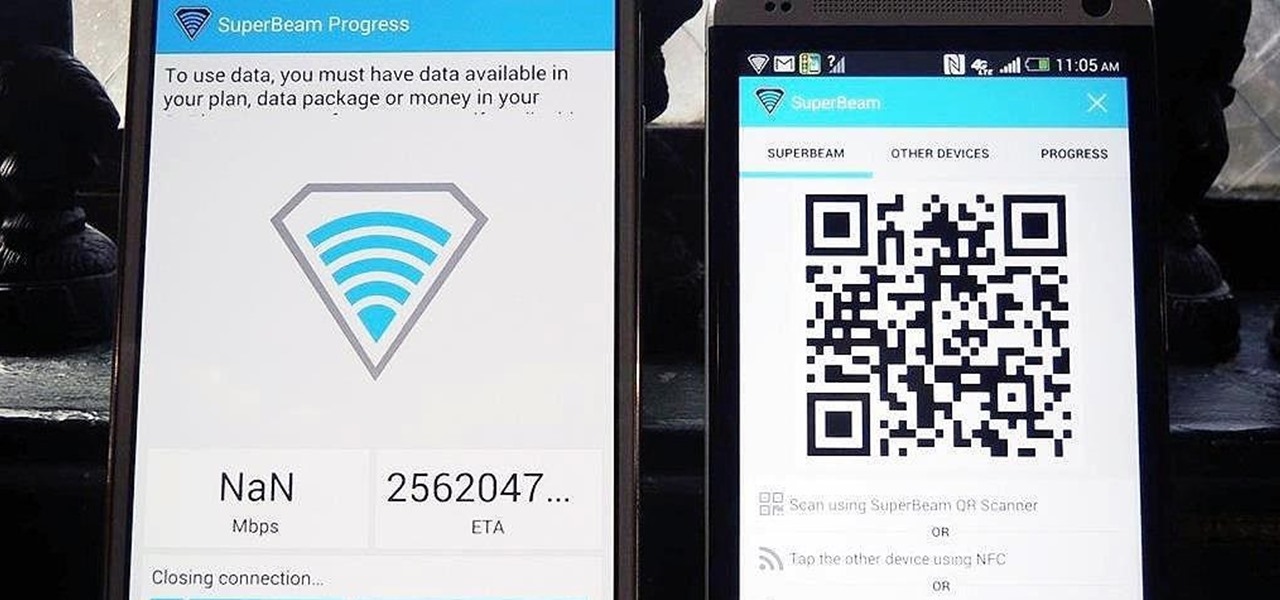
Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use.

It may be cheesy, but whipping out an origami flower while you're at the dinner table can really make someone's day, whether it's made out of a napkin, dollar bill, or burger wrapper. It's great for showing your waitress how much you appreciate the service, or for breaking the ice with your Valentine's Day date.

I'm a pretty nice person, so when someone asks me to take a group picture of their friends or family, I can't easily say "no," even if I have somewhere else to be. Even worse—sometimes I'm the one asking, fully knowing just how annoying it can be. Maybe you've been told "no" before, and have had to settle for being left out of the picture, which kind of sucks.

If you look at the label on your favorite processed snack, there's a good chance you have no idea what half the ingredients are. It's nothing new, but with natural and organic foods becoming huge trends, we're hyper-aware of all the "chemicals" we eat.

I listen to Pandora as I slowly drift off to sleep, so why not have the popular music app wake me up as well? Pandora only recently introduced the Alarm Clock feature on iOS, and now they've brought that same feature to Android—only it's better.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

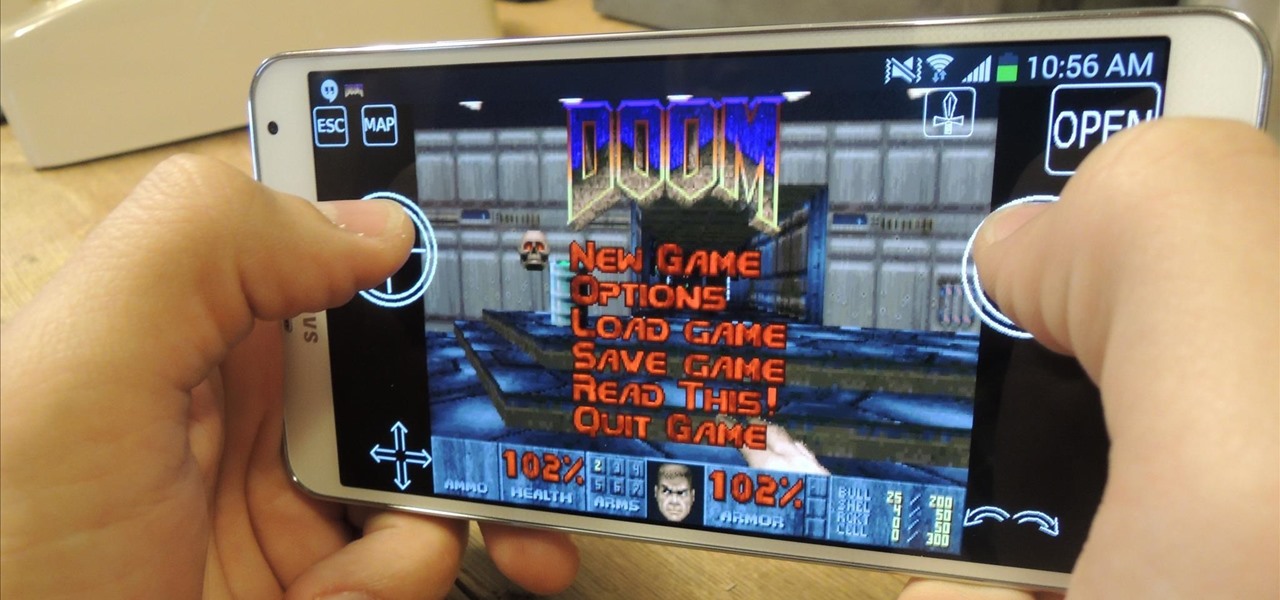
In the wake of its 20th anniversary, the folks over at Eltechs have released Original DOOM, a full shareware version of the revolutionary first-person shooter DOOM for Android, available for free on the Google Play Store. It's unmodded and unaltered from the original FPS classic.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

In spite of the degree of difficulty it is to install, CyanogenMod has steadily climbed the ladder to become one of the most popular third-party firmwares for Android devices.

Photographers have been using the Pepper's Ghost Illusion for over a century to play up the level of creepiness in their photos. Many of the pictures that claim to be real "sightings" use this technique to project a ghostly figure into the background of their images. Today, it's still used in theatre, "scary" rides at amusement parks, and haunted houses all over the world, which makes it a great photography trick for Halloween time. As shown in the tutorial below by Make's Jason Poel Smith, t...

Sharing just got a whole lot easier in the new iOS 7. Apple has decided to integrate AirDrop, the local vicinity file-sharing service found in Mac OS X, into the latest version of iOS.

I know I can't be the only person whose socks go missing in a shroud of mystery, but I'm determined to catch the sock-thieving gnomes in the act. While I have my suspicions, I can't quite prove it. Sure, I could drink a load of Red Bulls and never sleep, guarding my socks—but that's just crazy right? Luckily, I've found a way to set up my phone to catch the culprits.

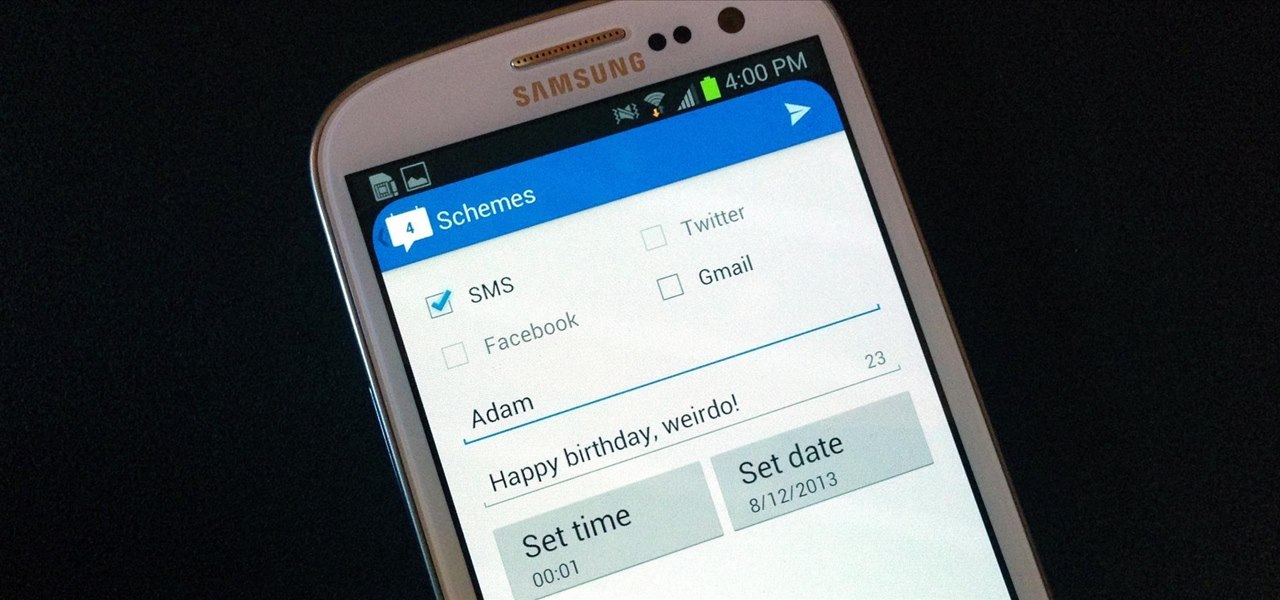
I'm sorry your mom hates you now, but it's pretty hard to forgive someone who forgets to say "Happy Mother's Day." Your poor ole ma could've spent anywhere from 10 to 20 hours popping you out, so the least you could do is set aside two minutes every year to say thanks. If you live to be 90 years old, that's only 3 hours over your entire lifetime!

Cinema is a matter of what's in the frame and what's out, according to director Martin Scorsese, who asserted that when describing his life's work. Getting the perfect shot can turn an otherwise ordinary scene into something great, both on and off screen.

There are some things that are just plain difficult to do for those of us with small hands. I started playing the piano when I was a little kid, and I learned the hard way that there were some chords that were just out of my reach.

In an increasingly mobile and globalized world, it’s not uncommon to lose touch with people we were once close with. Juggling between job demands, family responsibilities and our own personal needs, it’s often hard to put the time to keep all of our relationships going. Nevertheless, every now and then we get to reminiscing and feel the time has come for a reunion with people from the past.

I used to have nightmares when I watched Terminator 2. I mean, I didn't step on a playground for a least two months after I saw that movie. There was something terrifying about computers having so much intelligence.

Your average sit and go player will probably stick to the single, 9 or 10 person tables that are commonly found at all the popular online poker rooms. However, your more adventurous players aren’t afraid to try out the multi-table sit and go’s like the 180 man SNGs when they get a chance. But there are a few things players should keep in mind before starting out with the MTT SNG tournaments.