Each day, we read about another security breach somewhere in our digital world. It has become so commonplace that we hardly react anymore. Target, J.P. Morgan, iCloud, Home Depot, and the list goes on and on.

Sharing files has always been one of Android's greatest strengths. A system of "share intents" allow apps to freely exchange data with each other, making it possible to take a picture with your favorite camera app, then send it over to your choice of photo-sharing apps, for instance.

If you're anything like me, you started down the Android-modding path for two distinct reasons; to run cutting-edge software and squeeze every bit of performance out of your hardware. Utilizing the new F2FS file system on your rooted Nexus 4 or 5 fulfills both of those desires at the same time.

If you're like me, then you've got an incredibly complicated Wi-Fi password with uppercase and lowercase letters, numbers, and special characters.

Trying to explain something difficult over the phone can be pretty frustrating if the other person doesn't understand you. Using text messages can be useless for auditory learners, and a phone call won't do much good for a reading or visual learner.

It's time to enjoy one of America's longest lasting favorite pastimes. No, not baseball—pranking our friends! With the internet currently overrun with countless pictures and memes of cats, there's no way for your feline-hating friends to surf the web without coming across a kitten or two. But things can get worse for them. Way worse...

Welcome back, my neophyte hackers! I have already done a few tutorials on password cracking, including ones for Linux and Windows, WEP and WPA2, and even online passwords using THC Hydra. Now, I thought it might be worthwhile to begin a series on password cracking in general. Password cracking is both an art and a science, and I hope to show you the many ways and subtleties involved.

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Old habits die hard. It may be a cliché, but it's undeniably true, especially when it comes to the bad ones. Nail-biting, fidgeting, and overspending can label you as someone who is obsessive-compulsive, overly nervous, and routinely stressed out, but you can make the break less painful with a few simple tweaks to your routine and by understanding how your habits work.

Welcome back, my aspiring hackers and those who want to catch my aspiring hackers! As most of you know, this series on digital forensics is inspired by the motivation to keep all of you all out of custody. The more you know about the techniques used by law enforcement and forensic investigators, the better you can evade them.

While text messaging has become one of the most frequent ways we communicate with our friends, the missing body language, tone of voice, and eye contact can make it difficult to tell when someone is being dishonest. That said, it's not impossible. There are a number of subtle hints you can train yourself to recognize that will to help you detect written lies hiding in your SMS and iMessages. Here's what you should look out for.

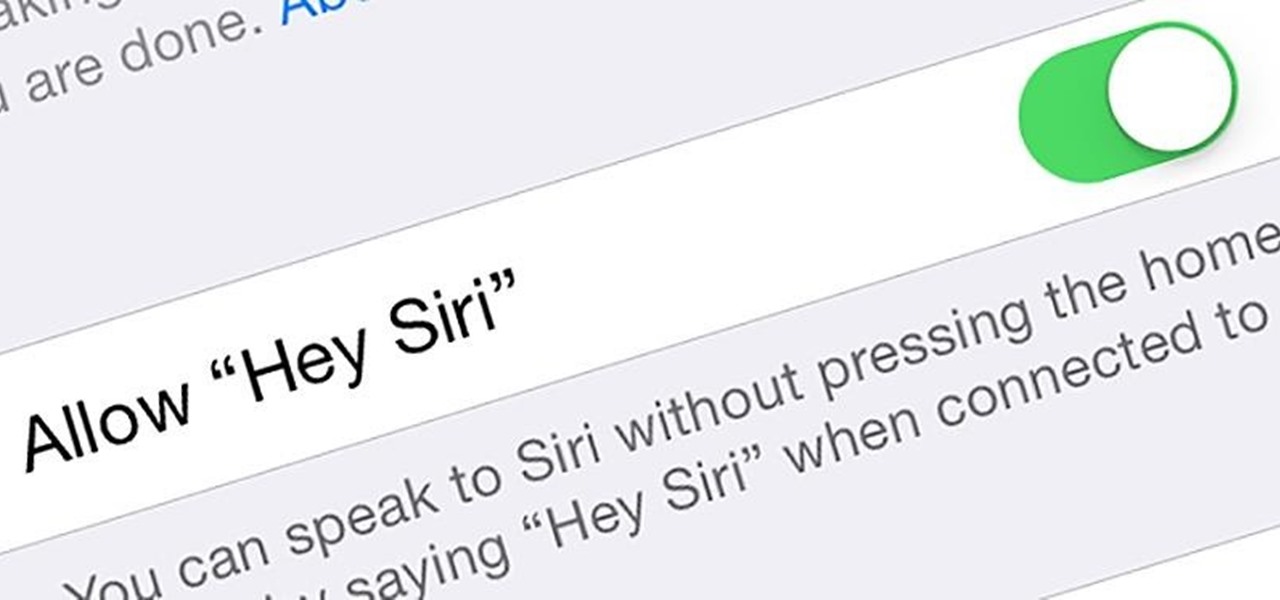
It seems that Apple is taking a page from Google's book with their new "Hey, Siri" voice activation feature in iOS 8. This feature mimics the one found in Google Now, the voice-activated intelligent personal assistant available to just about all Android users. Apple's version allows you to bring up Siri with a simple voice command, but there's a small catch.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Whether it's bad timing, or some trying-to-be-funny photobomber, it sucks having a photo ruined by someone or something getting in the way. While you can always retake the photo, it's simply impossible to capture the moment you intended, no matter how much restaging you do. But with an HTC One, there's no need to retake anything, as we have access to built-in features that will remove those photo intruders.

If you've haven't had your fill of Apple's security issues in recent weeks, Siri is now the latest to join the slew of problems with the most recent version of iOS (7.1.1).

Many of my aspiring hackers have written to me asking the same thing. "What skills do I need to be a good hacker?"

Have you ever been called a "noob" or "eZ" after some person kills you? have you ever said "you hack" or "you suck" after getting your butt kicked by another player? this wont ever have to happen again. It is actually possible to be very good at PvP in Minecraft, and you can also be good at it. Now, it is your turn to win in every battle you fight in Minecraft PvP.

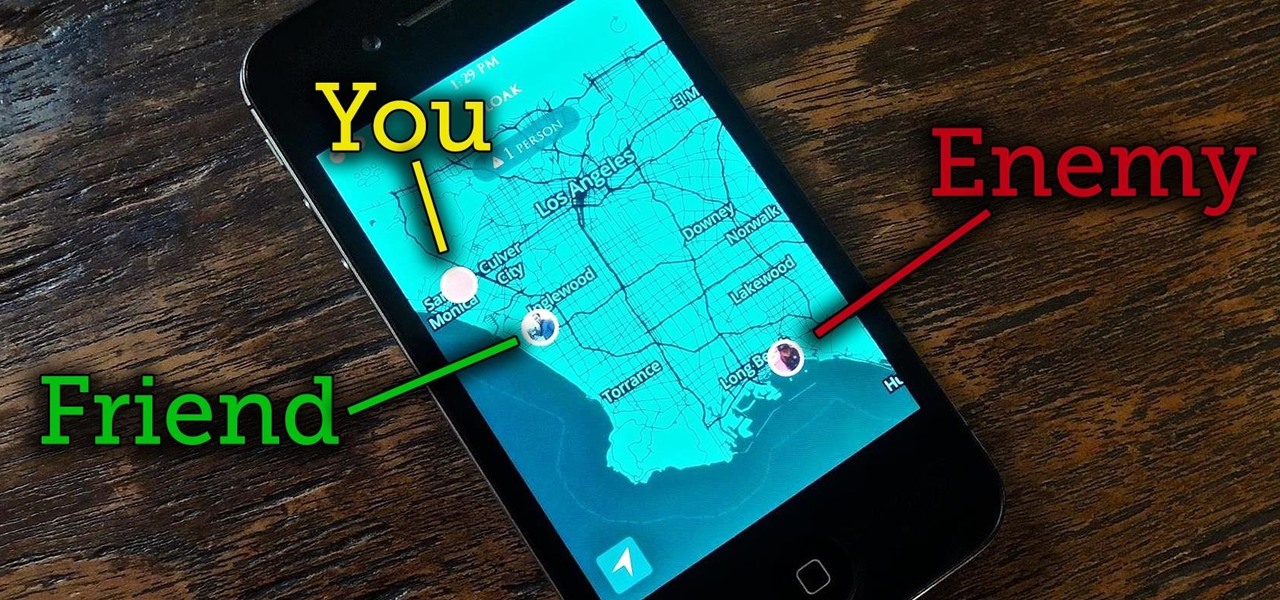
I never want to bump into my ex-girlfriend while out in the city (talk about a buzz kill), so if I could get an alert telling me that she's at Shortstops down the street, I'll avoid that area completely. This is where the new, interesting app Cloak - Incognito Mode for Real Life from dev Brian Moore comes in.

With the introduction of the Control Center in iOS 7, we finally had a way to access common system toggles like Wi-Fi, Airplane Mode, and best of all, Flashlight. Of course, there were plenty of adequate flashlight apps in the iOS App Store, but none that made it available straight from the lock screen.

Applying for jobs can be a truly miserable experience. Sending out endless résumés, filling out those janky online applications, and creating cover letters can really wear a person down. So, any suggestions that make that process easier are always welcome.

Welcome back, my novice hackers! This next subject might seem a bit obscure, but I promise you, this lesson will benefit you significantly either as a hacker or system admin. This tutorial will cover what is usually referred to as a regular expression, or regex for short.

Presentational video for our DIY Camera Crane project. Video: .

In the wake of the NSA controversy and its subsequent fallout, many dashed towards finding means of secure communication—using private internet browsing and encrypted text messaging applications—out of fear of being spied on.

One good thing about having friends who are constantly on their phones and tablets is it's easy to figure out what to get them for Christmas. Everyone hates getting gifts that just sit around, so it's always nice to get something that improves an item you use on a daily basis.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

Welcome back, my greenhorn hackers! Recently, I asked the Null Byte community what subject they would most like me to cover in future tutorials. Many of you cited scripting, and I decided it's best to cover this subject soon, so here goes.

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

While the legality of secretly recording phone calls varies in each country, sometimes it's useful to have audio documentation of conversations you have on your Samsung Galaxy Note 2.

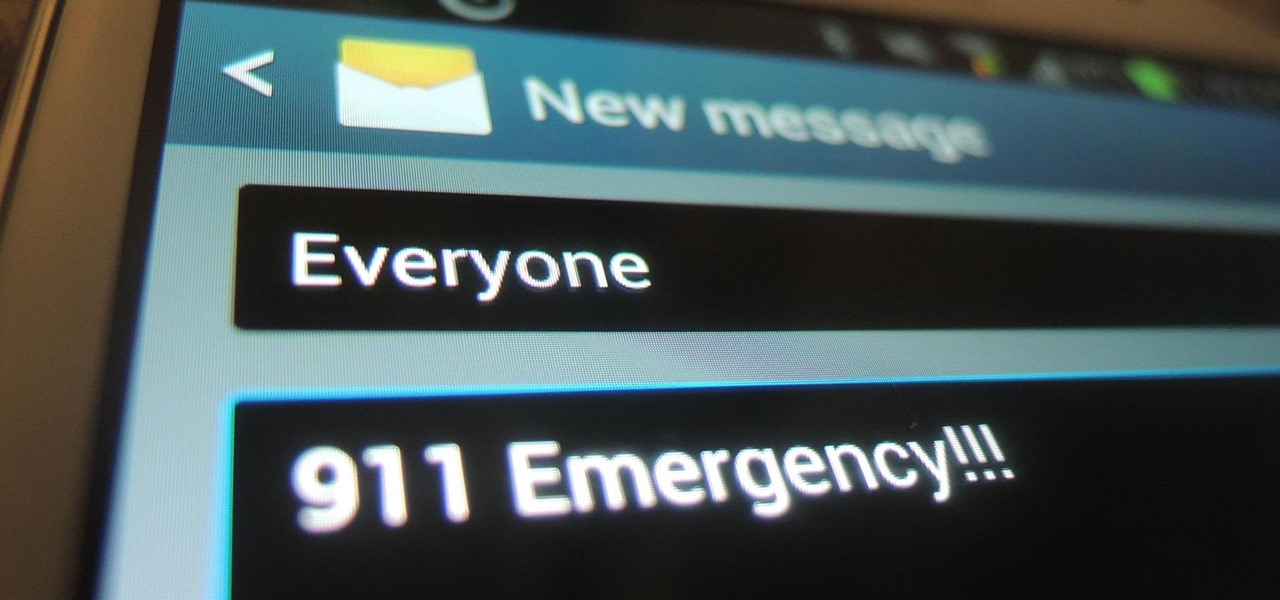
Just because your Samsung Galaxy Note 2 is on silent doesn't mean that the world stops spinning. Emergencies can pop up at any time, even when your phone is put away during a lecture in class, in the library, or at an important business meeting.

Facebook knows who all of your closest friends and family are. When you backpacked across Europe last summer, they went along on the trip. Remember that break up two years ago? Yeah, they were there. The breakfast you ate this morning? They probably have a picture of it. They're even right under your own feet.

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

With iOS 7, Apple is finally fighting back against spam, offering the option to block certain phone numbers from sending you text messages or iMessages (plus, phone calls and FaceTime too).

Any living creature will die if deprived of sleep for long enough. The longest documented occurrence of a person not fully sleeping and surviving is only 11 days. There is a rare disease where deep sleep is never achieved, affecting roughly 100 people worldwide. Patients usually only survive between 6 to 18 months after the onset of chronic insomnia, and only 3 to 9 months in a parasomnia state without any real REM sleep.

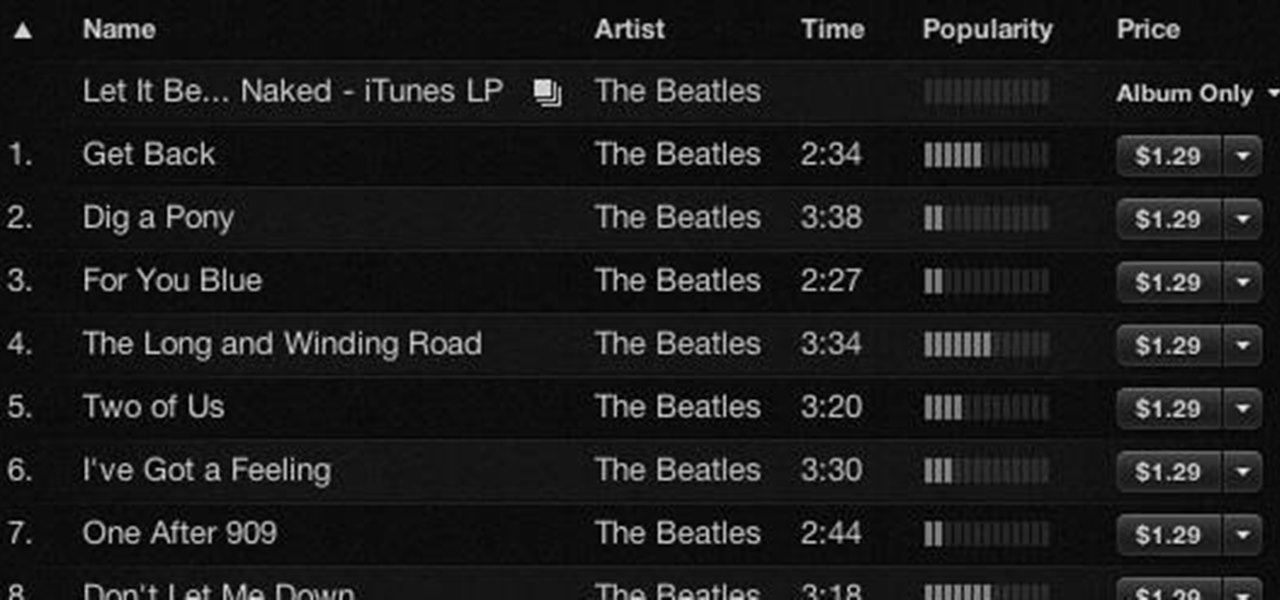
If you weren't aware, all music purchased online through iTunes, Amazon, and other digital audio providers have information embedded that can be used to identify the buyer and transaction of the digital music file. This may seem like something you should be disclosed about in their terms of use, but it's not.

We've all had that moment when we enter into a classroom, meeting, or theater and completely forget to put our cell phones on silent.
In any project management career, there is no such thing as a person who knows everything for each project. Many times, those who got too much confident with their jobs fail because they were not able to make things clear before and during the project implementation.

Whether you're at work or in class, there are times when using your phone is unacceptable, regardless of that subtle yet sudden twitch in your arm that arises every time you hear the vibration of a text message.

In most states, it's completely legal to record a telephone conversation that you're a part of without the other parties knowing. You can even record a conversation that you're not a part of, as long as you have consent from at least one person involved in the call.

If you're the type of person who constantly uses multiple tabs in your browser, you know how annoying it is when one of them starts playing unwanted music or video.