
There's always an iPhone in our list of top phones for privacy and security, due in large part to advanced security measures like Face ID, consistent iOS updates, and easy ways to prevent unwanted access and excessive data sharing. However, some of those options actually do the opposite and hinder security. It all depends on how you use your iPhone, but you should at least know everything available.

The one thing that separates a script kiddy from a legitimate hacker or security professional is the ability to program. Script kiddies use other people's tools, while hackers and security pros write their own tools. To that end, we're going to see how a stack overflow vulnerability allows us to flood a variable with enough input to overwrite the instruction pointer with our own commands.

If you need to know how to create a compound path in Illustrator, the quickest way is to go to the object tab in Illustrator. This gives you with the click of a button an easy way to create a compound path.
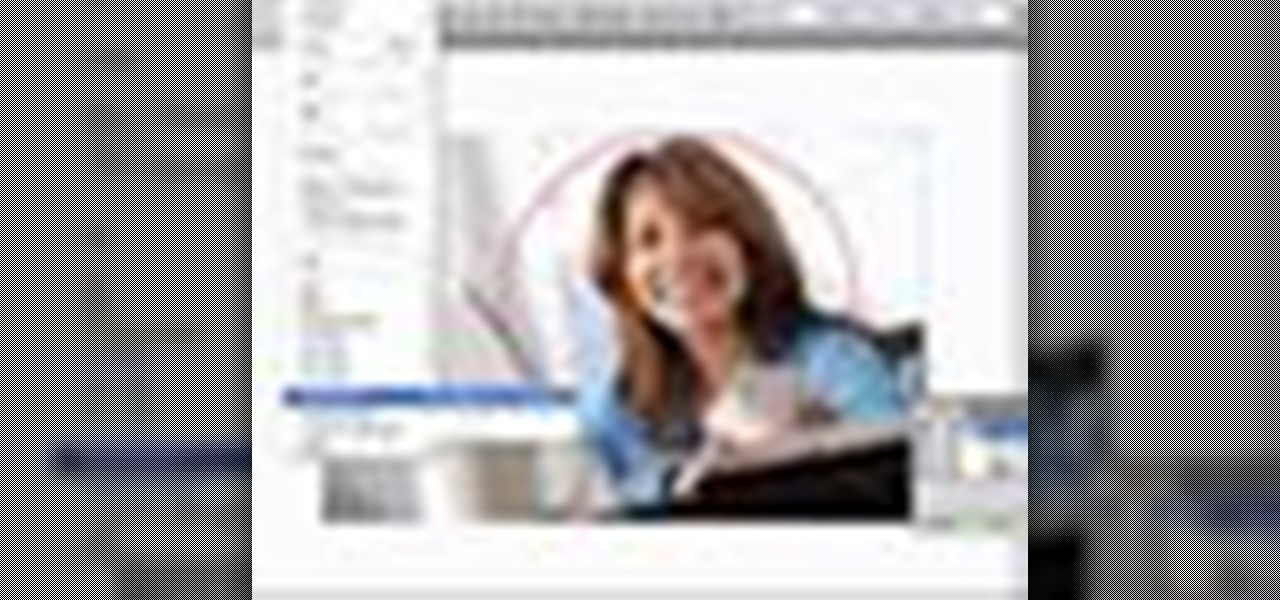
If you need to know how to apply clipping mask in Illustrator, the quickest way is to go to the object tab in Illustrator. This gives you with the click of a button an easy way to apply a clipping mask.
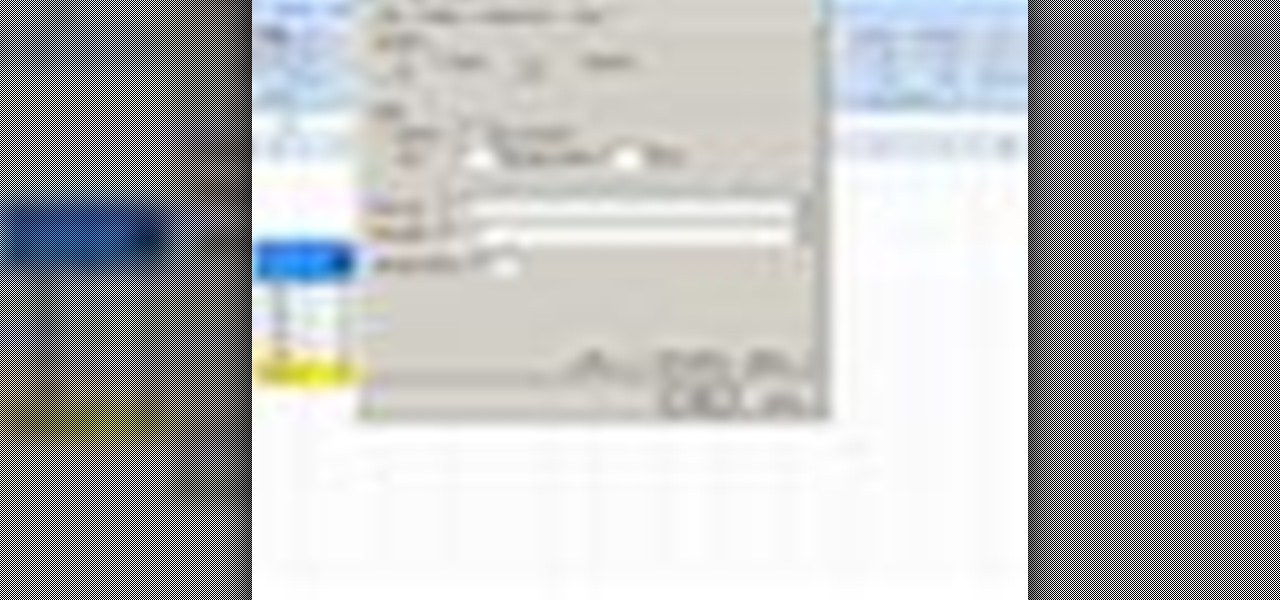
To customize the over all design of a specified document, you need to adjust Page Layout settings. This is easily done by clicking the Page Layout button and customizing settings such as orientation, scaling, and margins.

Whether you're a student, a toastmaster, just writing, or making articles on WonderHowTo, you will have to come up with a topic. The topic should be able to guide you to some of the things you want people to know about. Here are some ways that you can can come up with a topic.

Google has caught a lot of flack for various privacy infringements over time. Google Buzz was the latest uproar, when lack of proper prior testing allowed the tool to expose a slew of information users did not necessarily want shared, resulting in massive complaints. A Harvard student even went so far as to file a lawsuit (read more).









