This is a video from yourteacher.com on simulations for Pre Algebra. It explains what simulations are and gives an example problem. The teacher reminds us that it is important to remember that there can be more than one simulation for a problem. The teacher suggests a simulation for the problem given and suggests how many times to run the simulation. The teacher makes a simulation for what sex a child is by flipping a coin and suggests to flip the coin 50 or 100 times. The teacher also explai...
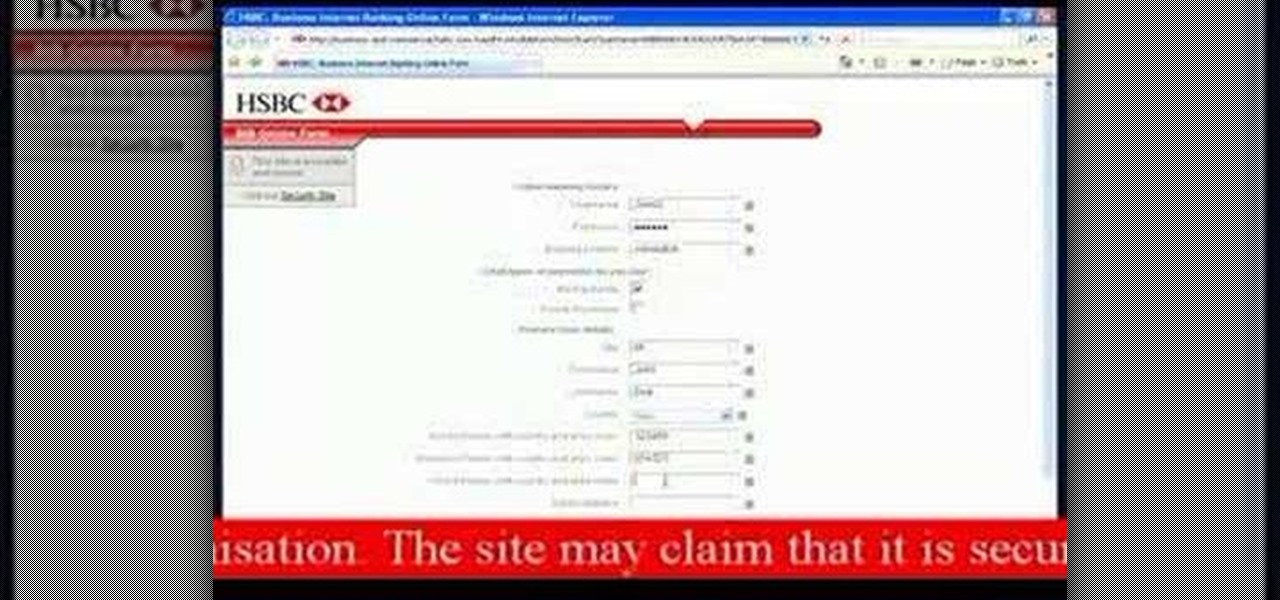
See what phishing (attempts to steal your online information with fraudulent email and webpages) is all about and read the tips on how to avoid becoming the next victim. In this example a HSBC bank phishing attempt is displayed.
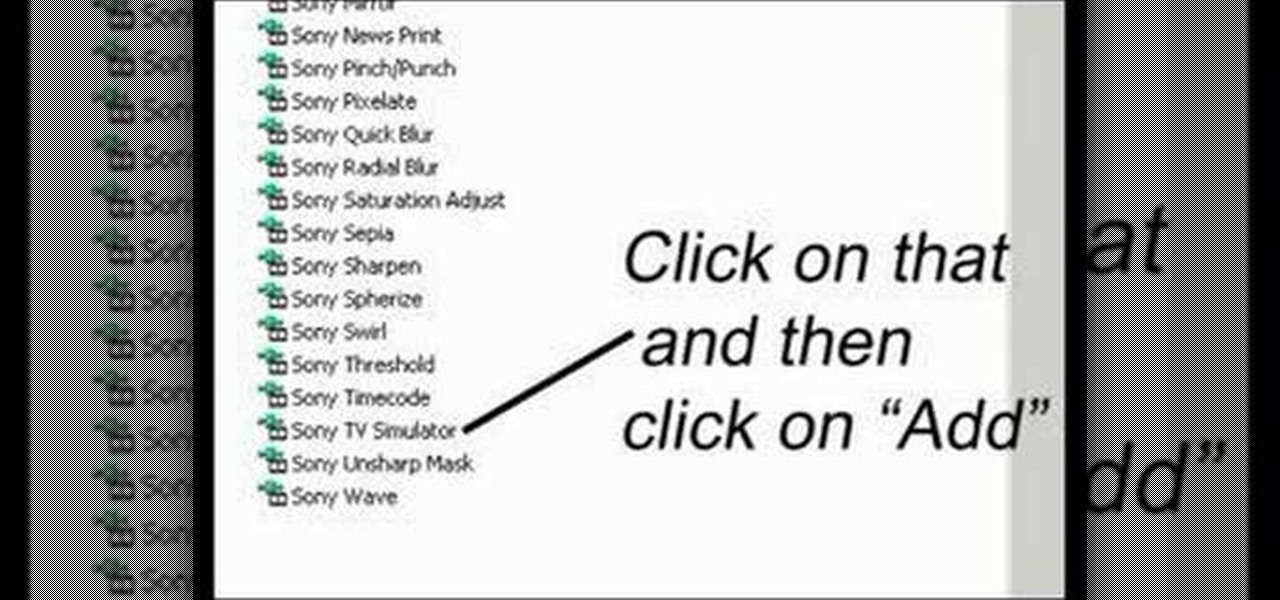
In this video editing software tutorial you will learn how to create a television simulation effect in Sony Vegas 7. All you need to do is add the Sony TV Simulator Media FX tool, input the right values and you'll have a cool TV simulation effect on your video footage in Sony Vegas 7.
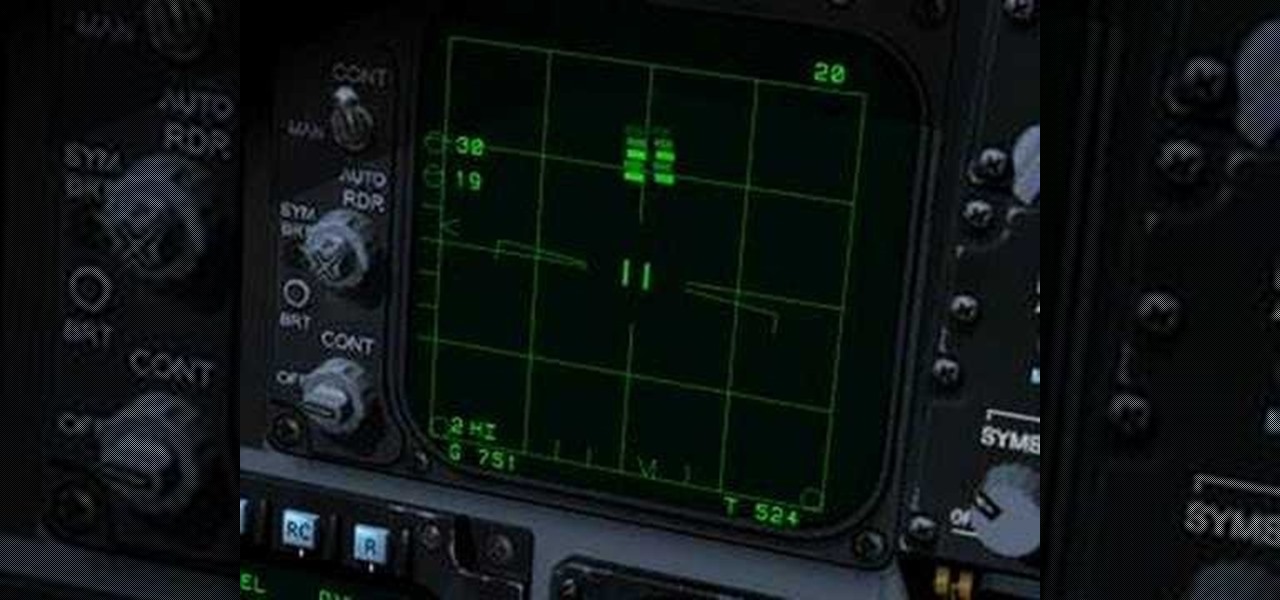
This is the first of what will surely be a long and detailed series on operating the F-15 Eagle in the simulator Lock-On: Flaming Cliffs. This first one introduces you to the Eagle's radar with off and Range-While-Search modes and their symbology.
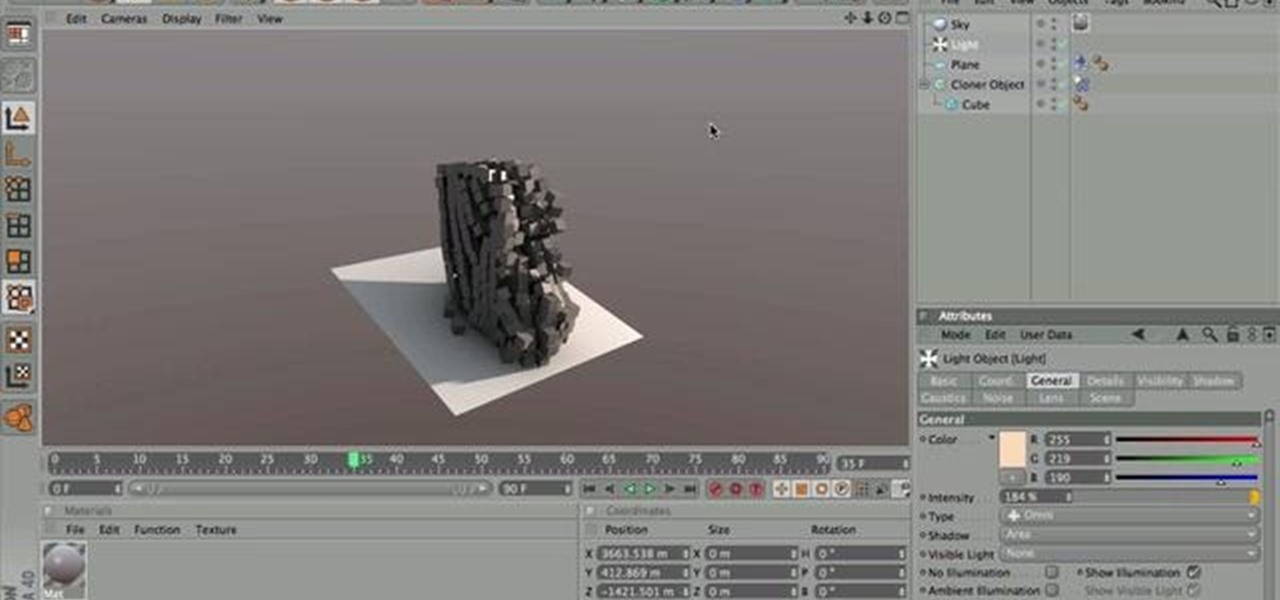
In this amazing video, Nick goes over the various ways of getting your physics and dynamics set up in your simulation for Mograph 2, as well as some trouble shooting for common problems that you may find, and, how to get your simulation ready for render!
If you want to be a character animator, you should probably learn Maya, and definitely learn rigging. This tutorial shows you how to create muscle movement simulations (or muscle rigging) for any creature or character with bones.

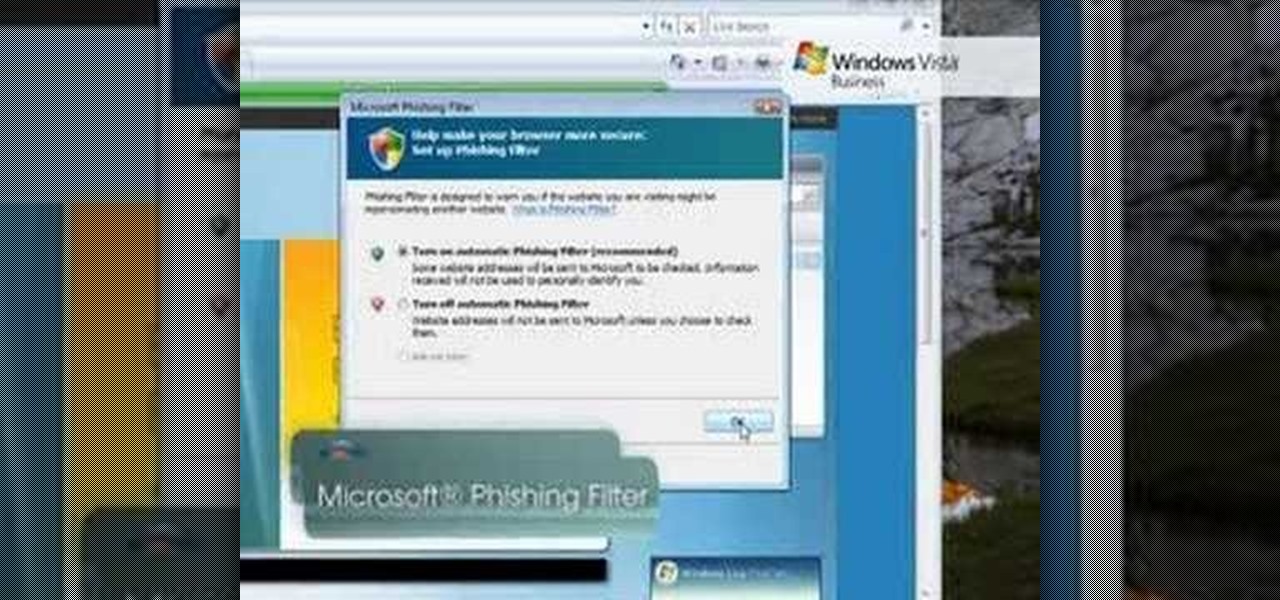
Check out this video tutorial to learn more about the Phishing Filter on Internet Explorer 7. Web browsers such as Microsoft's Internet Explorer 7 have become an important part of the computing experience for business and home users around the world. With the popularity of web browsers for accessing information, running programs, and even accessing corporate resources, the browser has become a target for viruses, malware, and phishing schemes that present real dangers to Internet users. Inter...

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

If you want to keep your online world secure, your best bet is to have a different password for every site and service that you use, and to make sure each of the passwords are comprised of random characters instead of familiar words or numbers. But this obviously creates a problem—how exactly are we supposed to remember all of these complicated passwords?

Sophisticated hackers have been exploiting vulnerabilities in Chrome and Firefox to trick even the most careful internet users into logging into fake domains for sites like Apple, Google, and Amazon.

With products and solutions offered by the likes of Scope AR, Trimble, DAQRI, VIATechnik, and others, augmented reality is becoming a hot commodity for improving productivity while maintaining safety in the construction and manufacturing industries.

Check out this masterclass on Houdini 9.5 and how to rebuild the fire simulator. Houdini's Fluid Tools offer a powerful simulation environment for visual effects artists. Senior Mathematician Jeff Lait introduces you to the basic building blocks for generating fluids and low level tools that make it easier to control the simulations.

Created by Houdini Product Specialist Stephen Tucker, this crash course series focuses on the concept of Smooth Particle Hydronamics and how they work within Houdini. The following videos on Particle Fluids continue working with fluid dynamics in Houdini 9.5 and assume that the viewer is relatively familiar with how dynamic simulations work, or have been following along through the series. The basics are still covered including creating water from an object but also include more conceptual si...

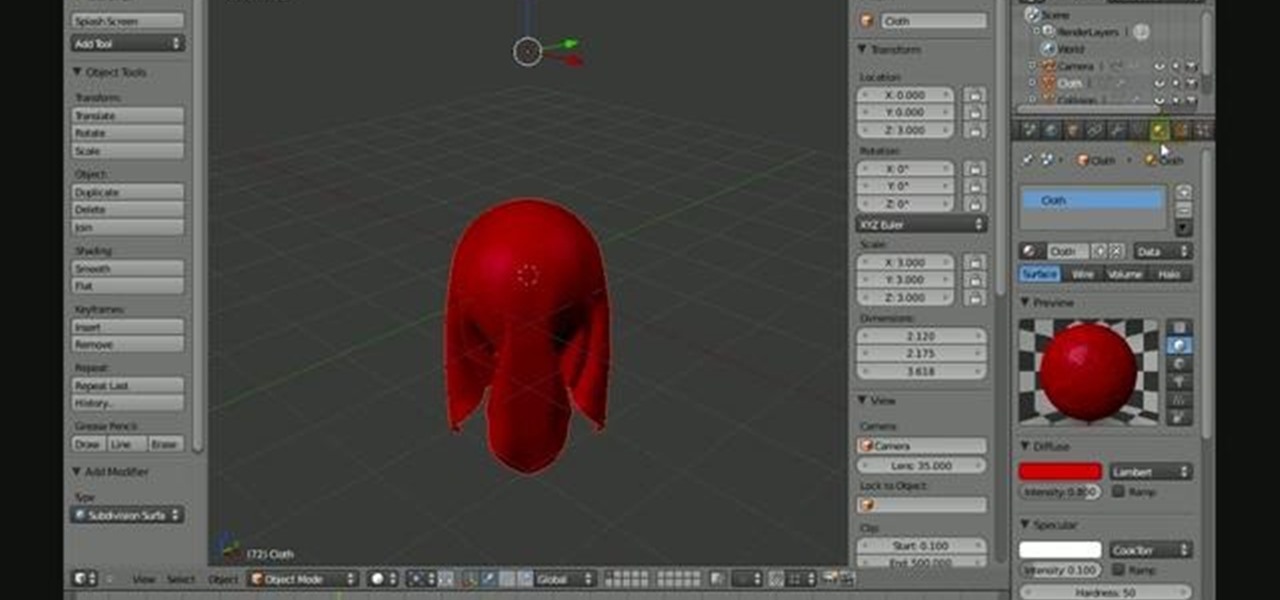
In this Autodesk 3ds Max video tutorial, you'll learn about a cool plugin that can create cloth-like animations. 3ds Max does have a built-in cloth simulation, but it's rather complicated to work with. The alternative to using the built-in feature is using the plug-in SimCloth 3, a free modifier. It works very easily and creates a smooth flowing cloth effect. This video is specifically working with a cloth cape on a superhero (if you could call it that). But this cloth-like effect could be ap...

Phishing is the easiest way to get your password stolen, as it only takes one mistake to log in to the wrong website. A convincing phishing site is key to a successful attempt, and tools to create them have become intuitive and more sophisticated. SocialFish allows a hacker to create a persuasive phishing page for nearly any website, offering a web interface with an Android app for remote control.

In the last few years, the HoloLens has become a popular tool for use in medical procedures and training. But recently, the Magic Leap One has gained momentum in the space as well when it comes to medical use cases.

Phish bone keychains feature a highlighted midsection with three different colors of hemp (in this video we use regular rafia-colored hemp, red hemp, and green hemp) that surround wooden beads.

If you're worried about having your private information taken away from you by hackers and other malicious people, this tutorial may help you. This tutorial will help show you how to easily use and understand the phishing filter in Internet Explorer 8. It only takes a couple of clicks to activate and can be the difference between making sure your private information is secure or out in the open for others to use. Good luck and enjoy!

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Yesterday, April 7th, it was revealed that the United States White House had been hacked by allegedly Russian hackers. According to reports, the Russian hackers used social engineering/phishing to get a foothold in the U.S. State Department and then pivoted from that system/network to the White House. Although the White House said no confidential information was compromised, the President's appointment calendar and other information were. Attribution or "blame" for the hack was made more diff...

Check out this Softimage Xsi tutorial in the fluids simulator. This is a great video showing SPH in ICE off. You can quickly see how flexible this is. Changing collision geometry while the simulation is running and ICE and SPH just deals with it.

Learn about some of the advanced features in Adobe Photoshop CS4 Extended for animating 3D objects in this software tutorial. In this project we will create a solar eclipse simulation from 2D, and video images of the earth and moon. This is an advanced users tutorial so you should be familiar with Photoshop first. Follow along as Russel Brown shows you how to work with the new 3D features of Photoshop CS4.

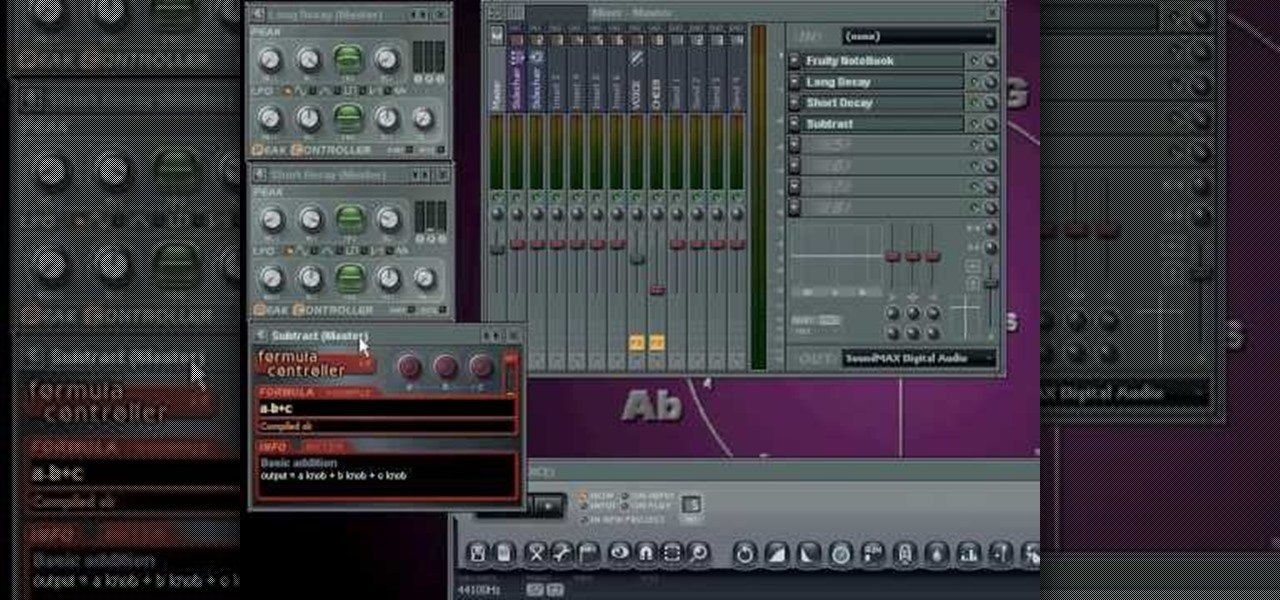
This audio production tutorial shows you how to simulate a live crown in FL Studio. Use a microphone or your audio output to trigger cheering or laughter in real-time with 5 easy steps in FL Studio. There's a little formula usage involved, but it's easy. See how to use fruity formula controllers for crowd simulation and reactions.

In this Houdini 9 video series, you will take a look at the new dynamics shelf tools and see how easy it is to create fairly complex simulations very quickly.

Ex girlfriend tracking you like a stalker? Find the leaks. She may be going through your email or phishing some information. Does she want a confrontation? Lure her to a public place then get her to cause a scene in front of security. Or last case scenario, fake your own death!

Learn how to create realistic cloth meshes within Blender 2.5. Whether you're new to the Blender Foundation's popular 3D modeling program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look!

In this tutorial, you'll learn how to create secondary motion without any simulations like softbody for your characters clothing, accessories, even hair! This method can also be applied to environmental animation. Whether you're new to the Blender Foundation's popular 3D modeling program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructio...

Mike Tadros demonstrates some useful techniques for incorporating the Space Navigator by 3D Connexion into your Google SketchUp workflow. Create smooth animations, pre-visualize motion graphics sequences, and even create a Star Wars flight simulation. All possible with the Space Navigator for SketchUp 6.

In this Houdini 9 video series, you will take a look at the new dynamics shelf tools in Houdini 9 and see how easy it is to create fairly complex simulations very quickly.

This video demonstrates the Heli-Chair and how you can use it to learn how to fly a helicopter. It has the same controls as a full size helicopter, but you are flying a model instead. This is not a computer simulation, it is a real helicopter that flys like a real helicopter!

This is the ultimate realistic combat simulation paintball markers, and is a replication of the famous M4-style military paint gun. See how to use it, and leaarn everything else there is to know about it.

This is an FSX tutorial on how to win against a jet truck. This is a flight simulation exercise.

The incidence of tuberculosis (TB) is dropping in the US, but the World Health Organization (WHO) considers it to be epidemic in the rest of the world — there were over 10 million new cases in 2016.

For years, astronomers have been trying to figure out how our galaxy came to be. Even with the help of high-performance computers, no model of a spiral galaxy has ever been able to recreate the Milky Way, until now. An international team of researchers has created the first successful simulation of what happened 14 billion years ago to give our galaxy its unique shape. Turns out, all they needed was a bigger bang. Photo by IntelFreePress

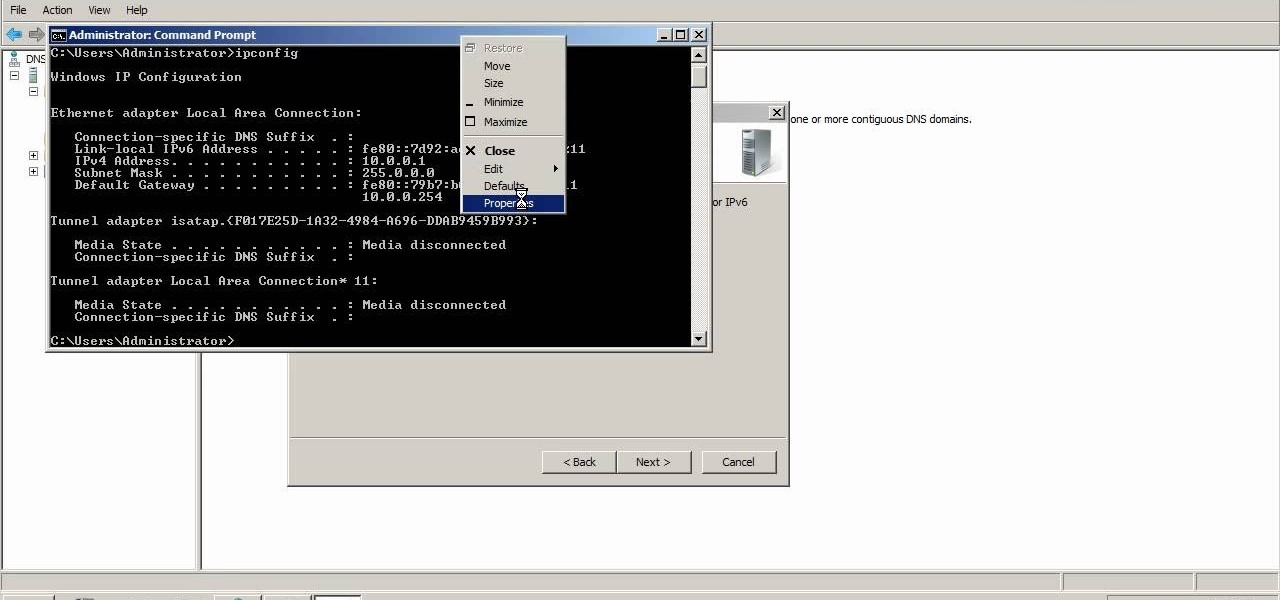
A reverse lookup zone will allow you to translate IP addresses to fully qualified domain names (FQDN). This can be a tremendous help against phishing in large organization. Keep your network secure by creating a reverse lookup zone in Windows Server 2003 or 2008.

A recently discovered bug in iOS 8's Mail app by Jan Soucek can allow the maliciously-minded to quite easily phish your iCloud password without you ever thinking something has gone awry. Using a bug that allows remote HTML content to be loaded in place of the original email content, unsuspecting victims would be prompted for iCloud credentials in a popup that resembles the native one found on iOS.

Check out this video tutorial on how to use the "double string method" to simulate cylinder fins on dummy model engine cylinders. If you like building engines for remote-controlled vehicles (airplanes), then this will definitely help you out with your RC projects, just by learning the "double string method" for cylinder fins simulation.

Ladder Safety is a video tutorial designed to highlight the important safety procedures associated with ladder use on construction sites. The video uses classic B&W comedic film footage and computer graphic simulations to illustrate safe ladder techniques. Learn how to use a ladder safely while on the job or at home by watching this instructional video.

NASA is going going to Saturn's moon Titan, and the space organization is using augmented reality help them do it.

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).