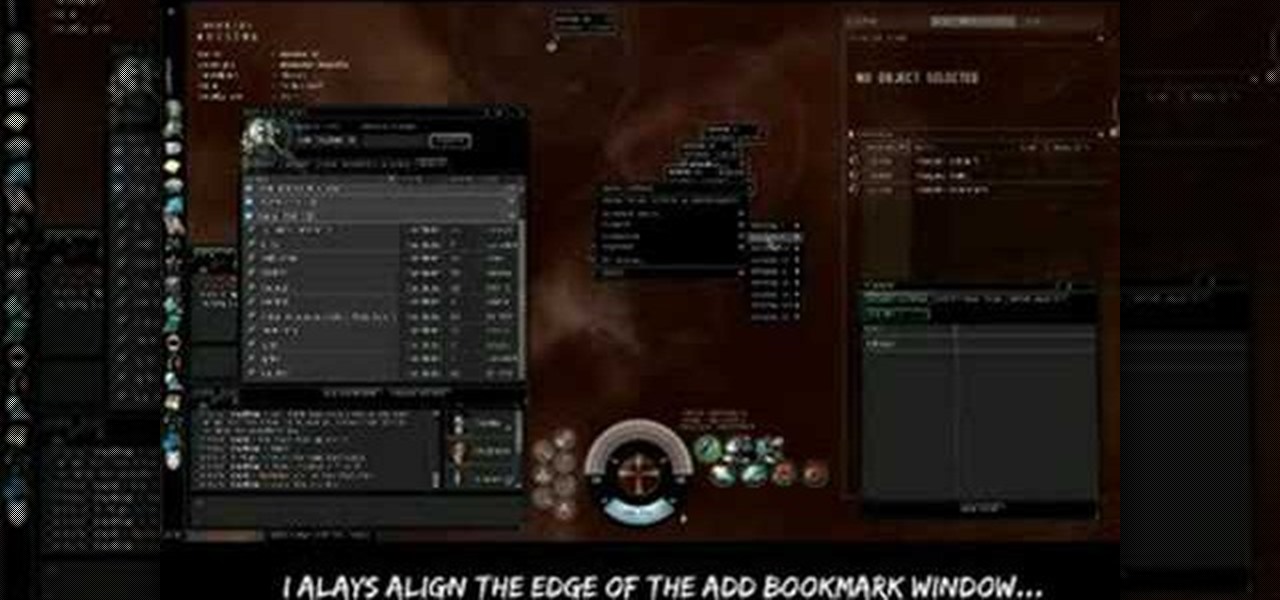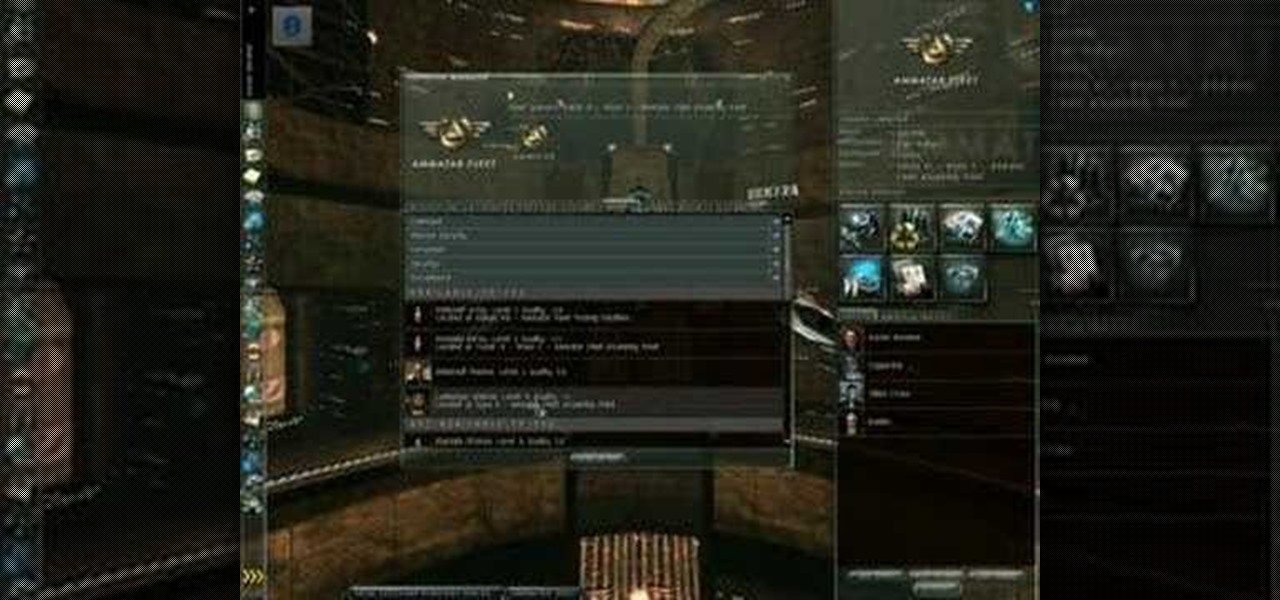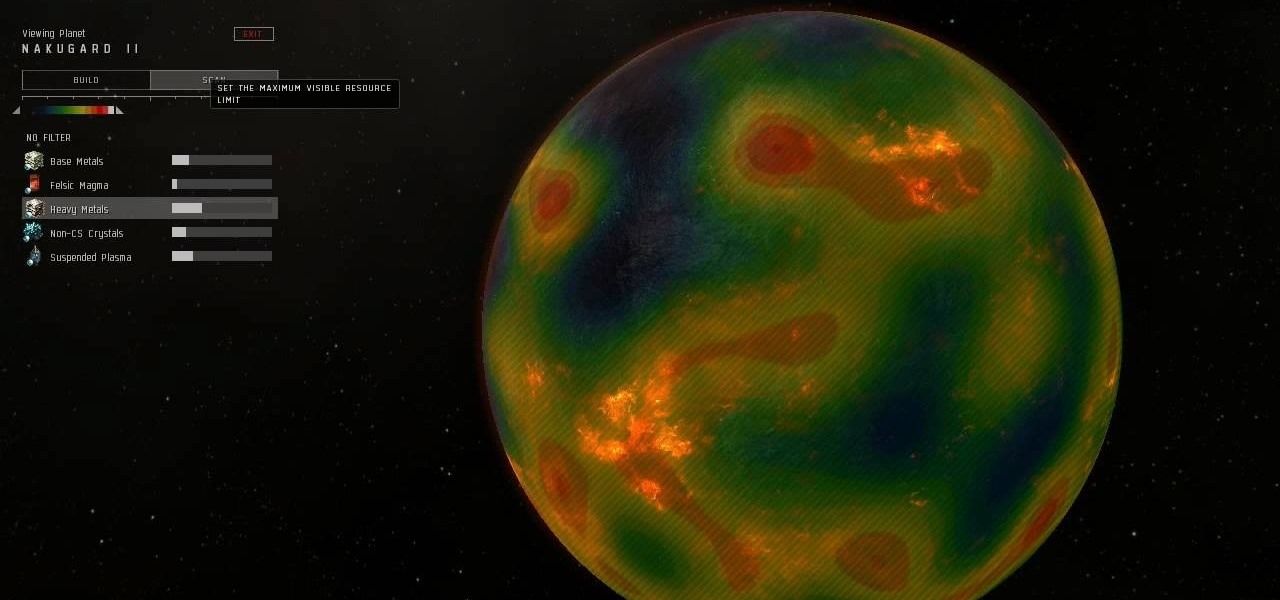
Mining is one of the best ways to earn resources when you play EVE Online. This tutorial includes everything you need to know in order to profit from mining - all you need is a ship and a mining laser!
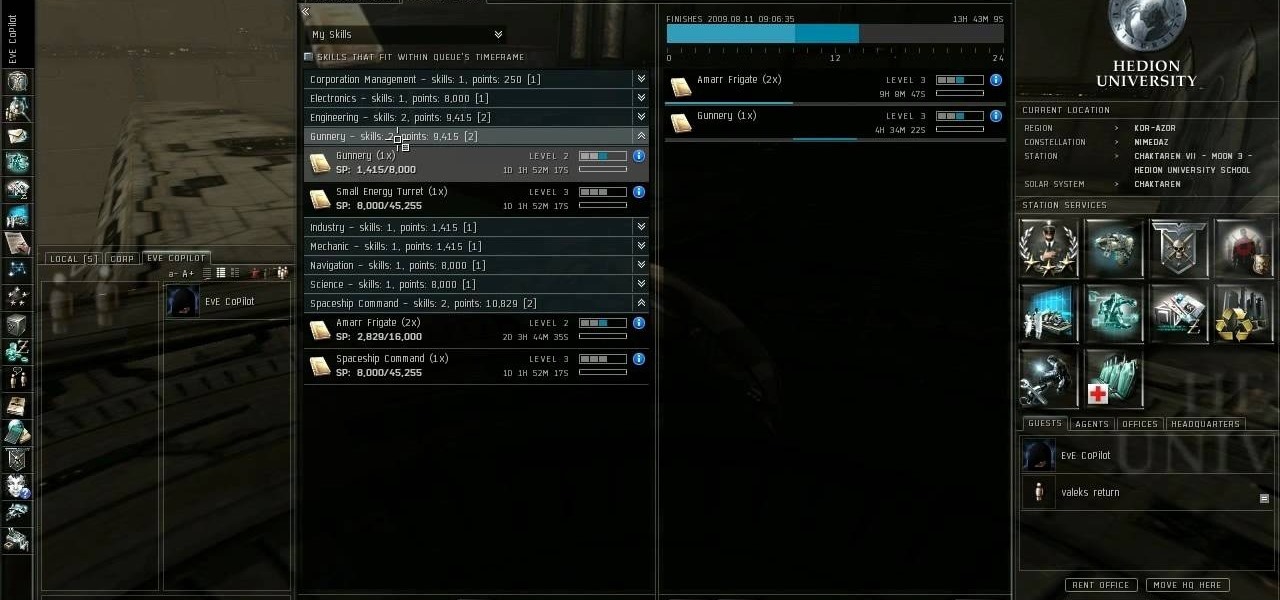
Make sure your character progresses the way you want! This tutorial explains how character attributes and skill training work within EVE Online so you can maximize your character's potential in the game. This tutorial also explains how to navigate the character sheet function. Always be learning at least one skill!
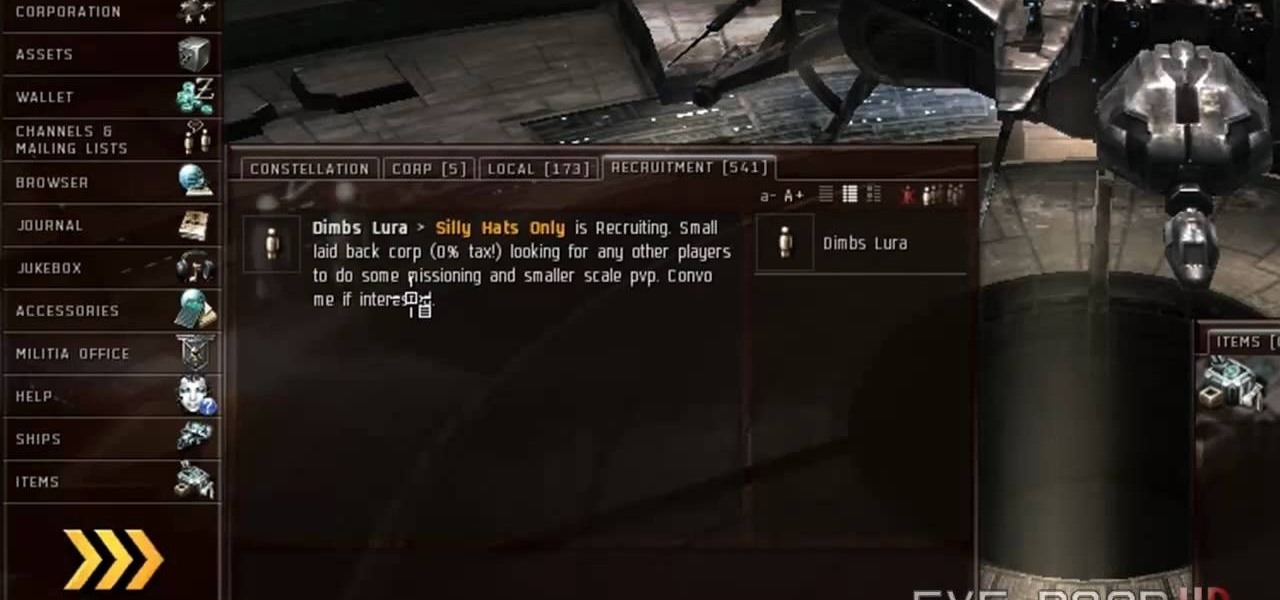
Part of the fun of an online game is being able to chat with your friends! This tutorial goes over how you can use the in-game chat system to join a chat channel. It also gives you a few channels useful for everyone to join, especially new players. Or create your own channel. Avoid pirate corporations!
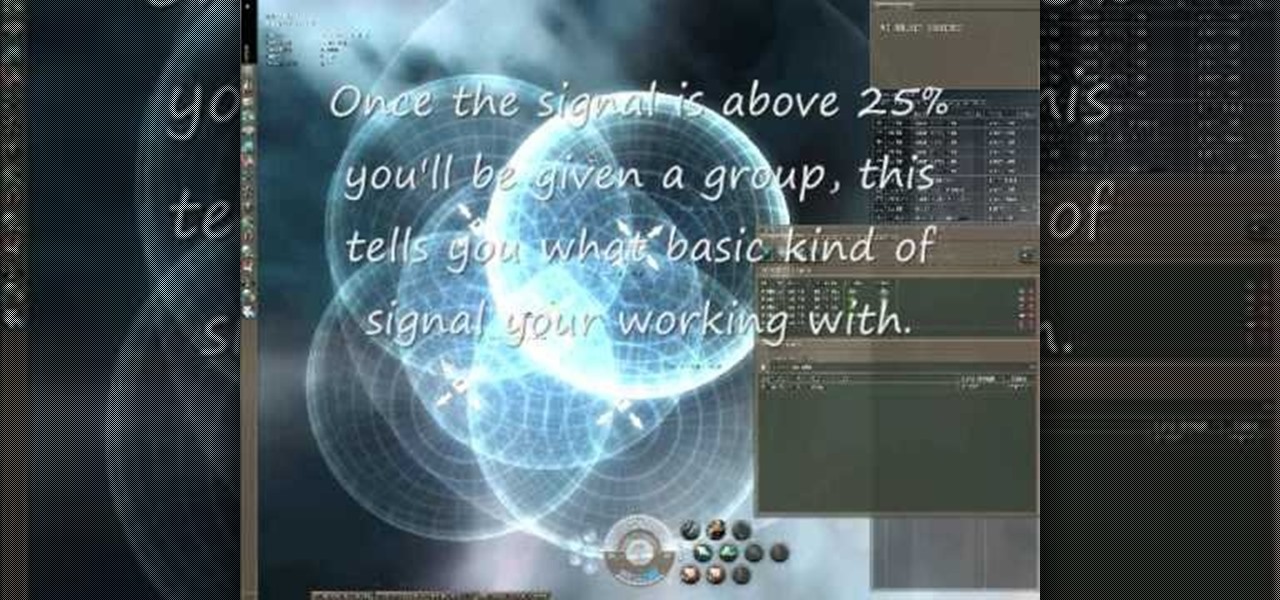
Know what's out there! You can send out probes to explore the area surrounding your ship. This tutorial shows you how to send out five probes and manipulate them in order to quickly and easily scan the local territory.
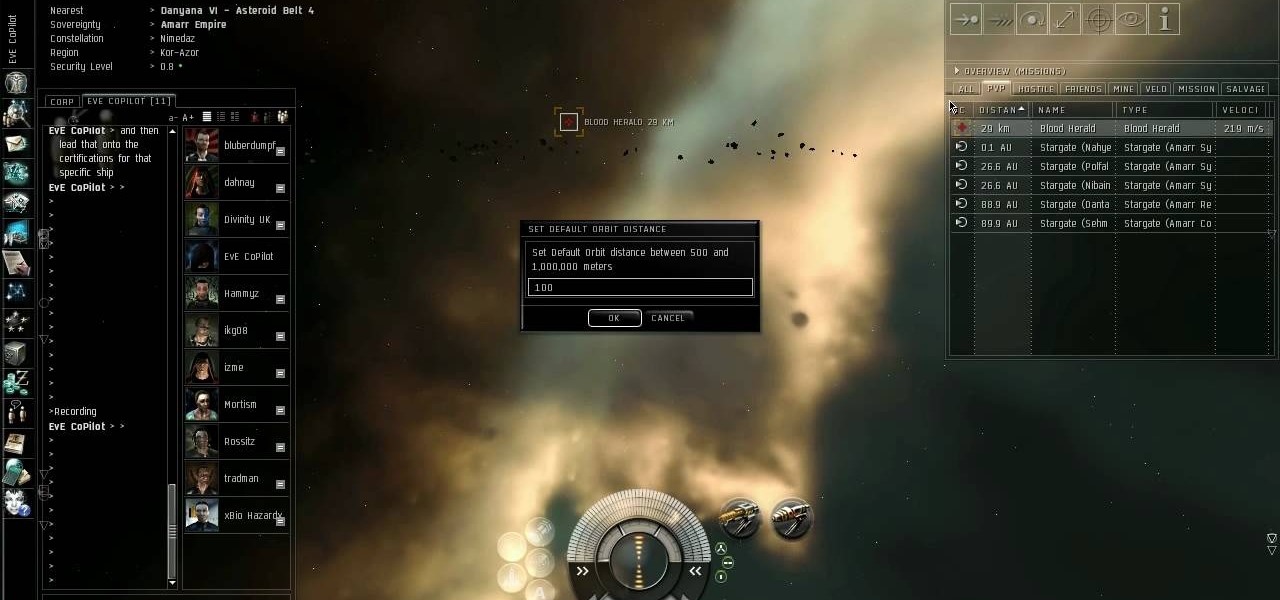
Quickly turn a profit during a combat mission by ratting - killing NPC enemies who spawn in asteroid belts. The difficulty of rats depends on how secure your system is - the lower security, the harder the rats are to kill. This tutorial shows you the best way, as a new player, to earn money by ratting.

While Wi-Fi networks can be set up by smart IT people, that doesn't mean the users of the system are similarly tech-savvy. We'll demonstrate how an evil twin attack can steal Wi-Fi passwords by kicking a user off their trusted network while creating a nearly identical fake one. This forces the victim to connect to the fake network and supply the Wi-Fi password to regain internet access.

While some researchers look for drugs to treat HIV, other scientists delve deep into the virus itself for answers on how it causes infections.

Trying to do some Runescape phishing? Watch this video to learn how to use Runescapersr to set up your own Runescape phisher. Get all the info you need by phishing with this Runescape phisher when you follow the instructions in this video.

Part of what makes EVE Online so much fun is the option to explore different moons, planets and asteroid belts. However, it can be dangerous. This tutorial explains the equipment you'll want and the best way to explore in a non-combat situation.

Need to find a good agent for your character when playing EVE Online? Starting from docking your ship in the station, this tutorial shows you how to find the best agent possible to help out your character in the game.

Planetary Interaction is a feature of the EVE Online expansion, Tyrannis. This video guide shows you how to use this new function. Choose your own planet, buy the command center and start exploiting its resources for your own gain!

China's Baidu, the Chinese equivalent of Google, live streamed a video yesterday of CEO Robin Li riding a self-drive vehicle along the streets and highways of Beijing.

NextReality will be giving readers a rundown of the augmented and mixed reality news briefs from the preceding week that we didn't cover already. This way, you'll never miss anything of importance in the NextReality landscape, and will always know what's going on with new augmented and mixed reality tech and applications. The first one starts right now, and you can enjoy future ones every Tuesday going forward, so stay tuned.

No website, service, or platform is immune to being abused or exploited by hackers, and Google Analytics is no exception. To better understand how Google Analytics can help deliver payloads and bypass security protocols, one might want to learn how to use Google Analytics from a user's perspective first.

Locating and abusing files containing unsafe permissions is an easy and surefire way to elevate shell privileges on a backdoored macOS device. This time around, we'll be more aggressive and attempt to phish a user's login password by prompting a convincing popup message merely asking the target for their password.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

It started in Australia, and now seems to have made its way statewide—hackers are remotely locking iOS and Mac devices, holding them for a $100 ransom. Users awoke to the loud "lost iPhone" ringtone, with a message on their lock screen stating that "Oleg Pliss" has hacked their device, and that "they" will unlock it after being sent $100 through PayPal.

Weapon grouping has become available in the Quantum Rise expansion for EVE Online. This allows you to load ammunition for up to three separate weapons at a time - useful in a dogfight! This tutorial shows you how to group your weapons to take advantage of this new feature.

Forex— what is it? Any investor could tell you a complicated description of what Forex is, but the basics of the FX currency markets is— an over-the-counter financial market for trading currencies. The foreign currency exchange market has no central exchanges like the stock market and little regulatory oversight. With this beginner’s guide, learn the trading basics.

How to hack Yoville! Yoville cheats, tricks, hacks. Watch this video tutorial to learn how to max people with macros on YoVille (10/01/09).

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

If you know your internet history, then you fondly remember the Star Wars Kid and his epic lightsaber display on YouTube. Now, many years later, everyone is following in the footsteps of the Star Wars Kid thanks to the Lenovo Mirage and the new Star Wars: Jedi Challenges app.

Developers looking to create shared experiences that support both HoloLens as well as ARKit may be able to get it working in Unity since that the engine supports both platforms — though, the amount of effort it might take to get that working could be a bit much. Up to this point, Unity has been the only real approach to attempt this combination — at least, until now.

Hyundai Motor Company says it will launch its driverless tech ahead of schedule, but the Korean carmaker will remain behind mainstream rivals, including General Motors (GM), Nissan, and Honda.

A proof of concept for an overhead crane training simulator is in the works. Using Microsoft HoloLens and an industrial-style controller, trainees can pick up holographic loads and transport them throughout a warehouse setting.

While flying isn't easy, once an airplane gets into the clouds there isn't a whole lot to worry about—most of the work happens during takeoff and landing. Helicopter pilots, on the other hand, have a lot of dangerous obstacles (like power lines and buildings) to contend with. But, once again, augmented reality can save the day.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

Some things never change. You'd think that with all the focus on web security, people might take the slightest precaution to keep their online activity private. Maybe there are more people suffering from Paula Poundstone's password troubles than we'd like to believe.

infosecinstitute posted a handy article about what to expect in the new year for cyber security, along with highlighting major game changers from 2015; 2016 Cyber Security Predictions: From Extortion to Nation-state Attacks - InfoSec Resources.

Most of the spam messages are commercial advertisements, phishing websites and get rich quickly messages that asks users to provide personal details and other confidential information.Spam filters in Gmail prevent its users from these spam messages and restrict them to enter in user’s Gmail inbox.Generally, it acts like a firewall between spam messages and Gmail Inbox.Gmail filters detect the sender’s email address and accordingly send the received messages in Inbox or Spam folder.

Security researcher and iPhone hacker pod2g has brought attention to a flaw in Apple's iOS that allows the user to change the reply address of an SMS message. This bug has been a part of the iPhone's SMS since the first iPhone in 2007, but Apple has yet to address it. Basically, there's a section in the text payload called User Data Heading (UDH) that controls some advanced features, one of which is the reply address. By changing the reply address of a text message, you can make someone send ...

Conducting phishing campaigns and hosting Metasploit sessions from a trusted VPS is important to any professional security researcher, pentester, or white hat hacker. However, the options are quite limited since most providers have zero-tolerance policies for any kind of hacking, good or bad. After researching dozens of products, we came out with 5 potentials that are ideal for Null Byte readers.

A short tutorial showing how to make a very basic car running simulation using the 3D Studio Max reactor.

With its 3D engine being responsible for approximately 60% of augmented and virtual reality experiences, Unity is continuing to place a premium on tools that not only keep developers working in its development environment but also make their workflows easier.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

Barrow's article on Pupy made me wish for a RAT that could target an OS frequently used by gatekeepers at startups, tech companies, and creative firms: macOS. Once run, a RAT can do severe damage by dumping a user's stored credentials for many accounts. The best loot lives in the Chrome Password cache, and EvilOSX, an OS X RAT, infiltrates macOS and dumps these credentials.

Good day to everyone, today I will present some basic and advanced concepts that targets sophisticated attacks on the social basis, also I will write about some steps that can prevent this attacks from occuring, basically we will examine Social Engineering from the angle of attacker and victim, some people who are interested in security and work for middle-sized companys can learn and use something interesting from this post.

Null Byte users have often requested video content, but the question has always been what format would best serve our community. This week, we partnered with Null Space Labs, a hackerspace in Los Angeles, to test the waters by hosting a series of talks on ethical hacking for students in Pasadena Computer Science Club. We invited students and Null Byte writers to deliver talks on Wi-Fi hacking, MITM attacks, and rogue devices like the USB Rubber Ducky.

When it comes to antivirus software, you don't want some fly-by-night developer having access to the sensitive data that these apps can scan. Luckily, most of the longest-tenured antivirus companies from the realm of desktop computers offer complete security suites for Android these days.

Welcome back, my novice hackers! Most of my tutorials up until this point have addressed how to exploit a target assuming that we already know some basic information about their system. These include their IP address, operating system, open ports, services running, and so on.