Just days before the release of the first image of the Magic Leap device, the company's CEO, Rony Abovitz, knew that the biggest moment of his life was about to unfold the following week. But instead of hunkering down in the Florida-based confines of the company's skunkworks, he instead decided to deliver a speech to the public about, what else, the future.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

In recent years, the US military has been utilizing augmented reality as a training tool, giving officers and soldiers an opportunity to train and hone their decision-making, tactical efforts, and weapons accuracy via virtual scenarios.

Like clockwork, Apple has unveiled the latest additions to its ARKit tookit at the annual Worldwide Developers Conference, where ARKit first said hello to the world in 2017, as well as some new tools that take a direct shot at Unity, Unreal Engine, and others.

Describing how and why the HoloLens 2 is so much better than the original is helpful, but seeing it is even better.

The HoloLens has made enough of an impact on the healthcare industry for Microsoft technology partner Medivis to convince investors to pledge $2.3 million in funding for its surgical platform.

A Series B round of funding, totaling $30 million, will enable Helsinki-based startup Varjo to launch its industrial-grade augmented and virtual reality headset capable of "human-eye resolution" before the end of the year.

Web 2.0 technology has provided a convenient way to post videos online, keep up with old friends on social media, and even bank from the comfort of your web browser. But when applications are poorly designed or incorrectly configured, certain flaws can be exploited. One such flaw, known as CSRF, allows an attacker to use a legitimate user's session to execute unauthorized requests to the server.

Following the surprise release of Magic Leap's SDK on Monday, March 19, Unity, Unreal Engine, and Mozilla followed up by announcing official partnerships with the company.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

While self-driving cars appear to be as inevitable as augmented reality headsets, the auto industry and its technology partners likely have years of testing to complete and regulatory loopholes to jump through before self-driving cars hit most highways.

Amazon Web Services (AWS) opened its re:INVENT developers expo with a bang by launching Amazon Sumerian, a new tool that could become the dominant platform for building cross-platform augmented and virtual reality applications.

Up until now, experiencing augmented reality through Vuzix's next-generation Blade 3000 smartglasses would have required a trip to a tech conference where the company has an exhibition booth.

According to Digi-Capital, investors poured $1.8 billion into augmented and virtual reality companies over the last 12 months, including $300 million in the third quarter. These investments are not made without a means to monetize products and services.

A remote administration tool, or RAT, is a piece of software used for remotely controlling machines. They are commonly used by tech support to gain remote access for troubleshooting purposes, but RATs are also an important part of a hacker's advanced persistent threat (APT) toolkit. Unlike standard administration RATs, these tools are designed to be delivered stealthily and operate undetected.

In the first part of this series, we looked at the surface detection that is provided by the ARKit. We looked at how it worked and covered some of the tools that could help us determine what is not working; when it doesn't. Now let's take this to the next step.

Augmented reality is quickly becoming a popular tool for marketing use cases, as demonstrated by new projects serving the automotive, entertainment, and tourism industries this past week.

Beginning in November, National Football League (NFL) fans visiting New York's Times Square can come as close as any civilian can to stepping onto a professional football field. All for less than the price of a pair of cleats.

Augmented reality software developer Edgybees has launched Drone Prix. The new mobile app immerses DJI drones and their pilots in more than 30 augmented reality obstacle courses.

I was a slap-happy T-Mobile customer before, but now, after hearing that the company sent out a box of rolling papers to certain media sites with memes bad mouthing #VerHIGHzon ... I love you even more, John Legere!

Asobo Studios, one of the first companies to partner with Microsoft on HoloLens development, is applying their expertise towards building applications for various business verticals through their internal HoloForge Interactive team.

Upskill, an enterprise software developer for industrial augmented reality applications, recently received an influx of funding and a major vote of confidence from two of their top customers.

There's now more reasons to make sick workers stay home—a new game theory study suggests adequate hand washing and other illness-aversion tactics aren't as useful as we thought to keep you from getting infected when a virus or bacteria is circulating.

The US Department of Education has put together a competition called the EdSim Challenge with a $680,000 purse to facilitate next-gen education. The event calls upon augmented and virtual reality, as well as video game developers, to bring immersive simulation concepts to prepare the workforce of the future.

When we talk about augmenting our reality, we often first think about vision instead of our other senses—but there's more to an immersive experience than what you see. One inventor figured out how to utilize sound and touch to create a simple, upgraded version of laser tag that you can play with your smartphone.

You may not know what HTTP is exactly, but you definitely know that every single website you visit starts with it. Without the Hypertext Transfer Protocol, there'd be no easy way to view all the text, media, and data that you're able to see online. However, all communication between your browser and a website are unencrypted, which means it can be eavesdropped on.

Although there has been much speculation about how much damage could be done if hackers were to take control of a country's SCADA systems, there have been few examples - until a few months ago, with the power outage in Ukraine caused by hackers.

While password cracking and WPS setup PIN attacks get a lot of attention, social engineering attacks are by far the fastest way of obtaining a Wi-Fi password. One of the most potent Wi-Fi social engineering attacks is Wifiphisher, a tool that blocks the internet until desperate users enter the Wi-Fi password to enable a fake router firmware update.

Edit: Some of the methods I show you may be difficult, or not work at famous or high quality hotels.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

Believe it or not, but people are actually texting less than they did before, and that's all thanks to Facebook Messenger, Snapchat, WhatsApp, and other split-second communication services. However, one communication method that is still going strong—and dominating—is email.

Welcome back, my greenhorn hackers! Although we have focused primarily on technical hacks here, social engineering can sometimes be especially effective. This one requires a bit of technical skill, but not too much. In addition, it's limited by how specific a target you can choose—but it will work.

Google recently updated their TOS to reflect the email scanning practices they use in Gmail, which are used to display more relevant ads, among other things.

Skype is a great way to stay in contact with friends and family over the internet, and people tend to share a lot in their chats, so why not try and find a way to hack it! Once a Skype account is hacked, you can view all conversations within the last three months, see how long each video call was, and even access files that were shared through chat.

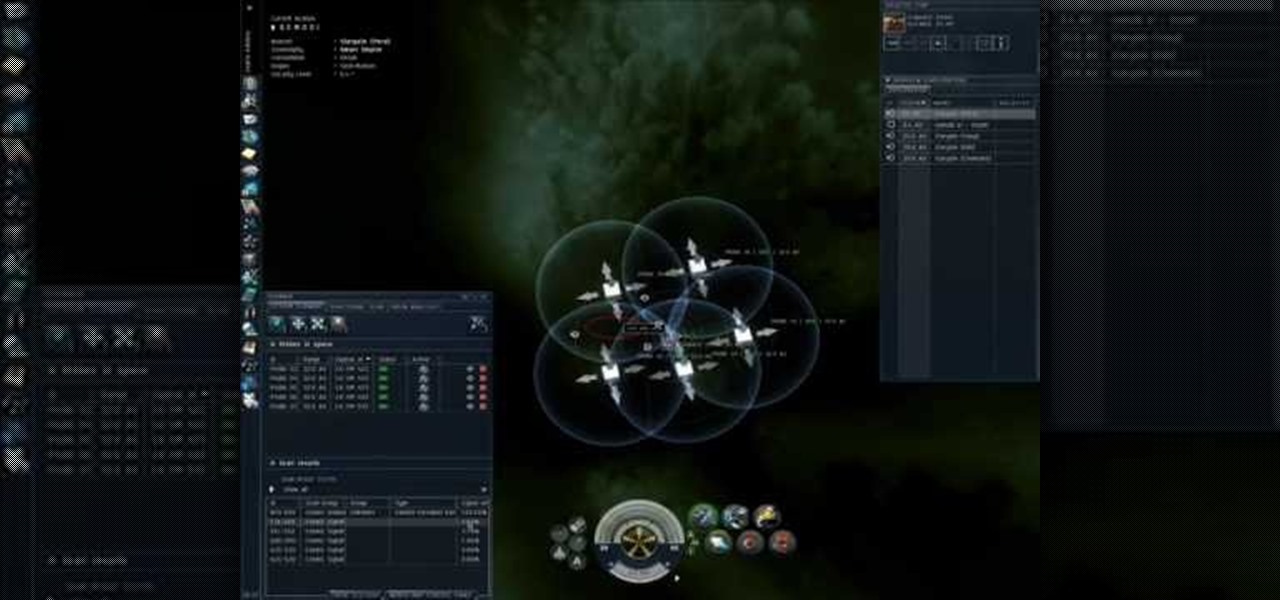
Avoid an ambush and detect what's available in a given star system! You'll need to learn how to use probes to scan the surrounding area if you want to do a lot of exploring in EVE Online. This video shows you how to set up your probes and execute the scanning function.

DarkStar One: Broken Alliance is an updated version of the space flight simulation video game DarkStar One (2006), and was made exclusively for the Xbox 360. It features updated graphics and presentation, making it the perfect space flight game for you wannabe astronauts.

For a hacker, there are a lot of advantages to creating a fake network. One advantage forces nearby devices to use their real MAC address if you happen upon a network that's stored in their preferred network list.

Automating port scanners, directory crawlers, and reconnaissance tools can be complicated for beginners just getting started with Kali Linux. Sparta solves this problem with an easy-to-use graphical interface designed to simplify a penetration tester's tasks.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.