Armis Labs has revealed eight vulnerabilities, called "BlueBorne", which put 5.3 billion Android, iOS, Windows, and Linux devices that use Bluetooth at risk. With it, hackers can control devices, access data, and spread malware to other vulnerable devices through networks. In this post, we will learn about the vulnerabilities, then look at how to find devices that have them.

During a penetration test, one of the most important aspects of engaging a target is information gathering. The more information you have coming into an attack, the more likely the attack is to succeed. In this article, I'll be looking at SpiderFoot, a modular cross-platform OSINT (open-source intelligence) gathering tool.
Hello and welcome to my article. I have made this article for anyone who wants to become a hacker, and wants to know how to get started.

The latest software update for iPhone has a few new features you should know about, including an enhanced security feature to protect your Apple ID account from phishing and other attacks. Keep reading to see everything new that's included with iOS 16.3 for iPhone.
Generative artificial intelligence has taken the tech world by storm, and Google's AI chatbot will give you a taste of what it offers.

If you think you might be a likely target of a black-hat hacker, there's a new iOS security feature that offers extreme protection for your iPhone against spyware, phishing attempts, and other highly sophisticated cyberattacks.

If you use Apple's Mail app on your iPhone for iCloud and third-party email accounts, install the new iOS update ASAP if you haven't already. While there's not a colossal number of new features, the latest tools and improvements are powerful enough to make the update feel like Mail's biggest ever — and there are features we've been waiting for for years!

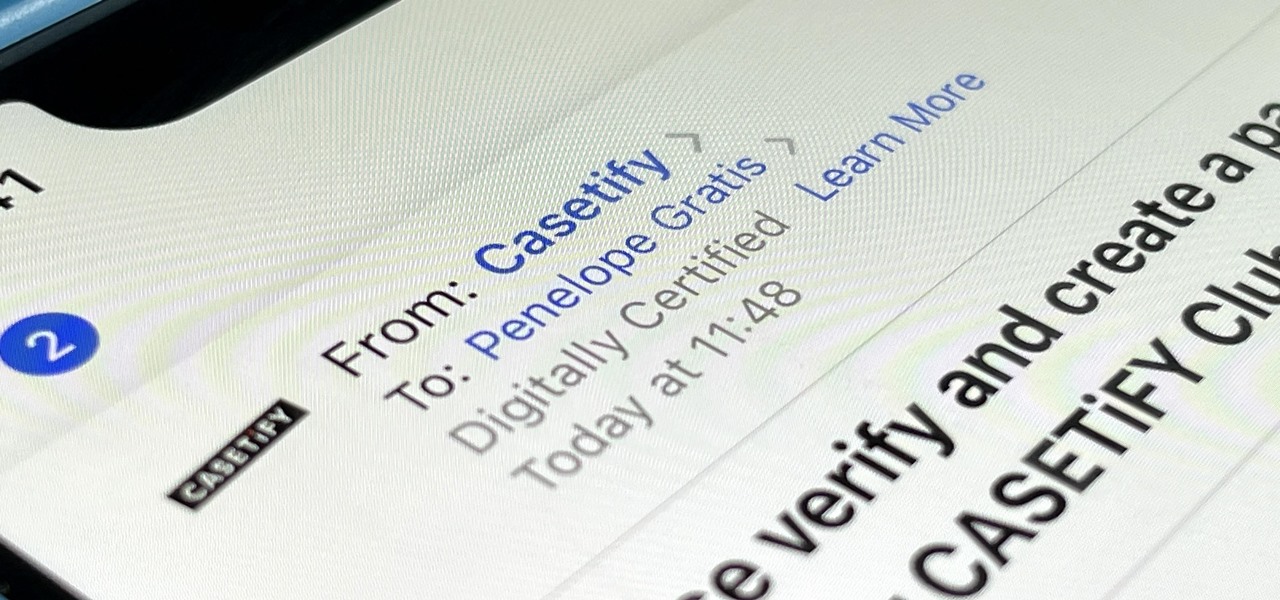
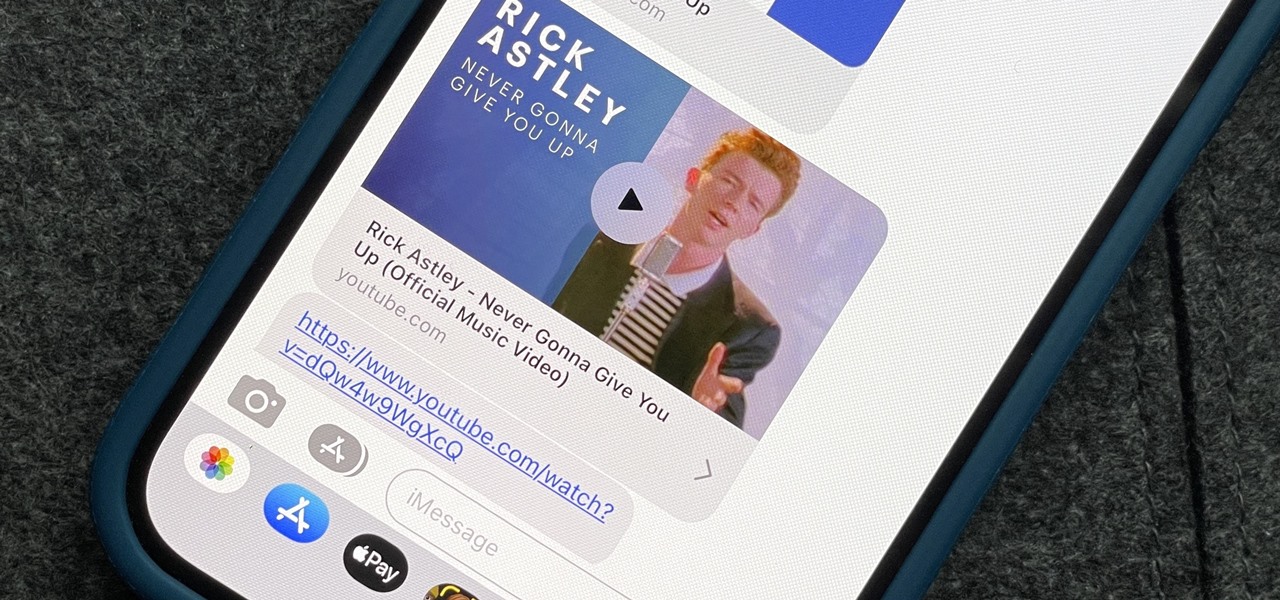
Apple automatically converts most URLs in the Messages app into rich link previews, but they aren't always pretty, and sometimes you just want to see the full URL instead. While there is no setting on iOS, iPadOS, or macOS that disables rich link previews in the Messages app, there is an easy way to show the URL complete with the scheme, domain name, and path.

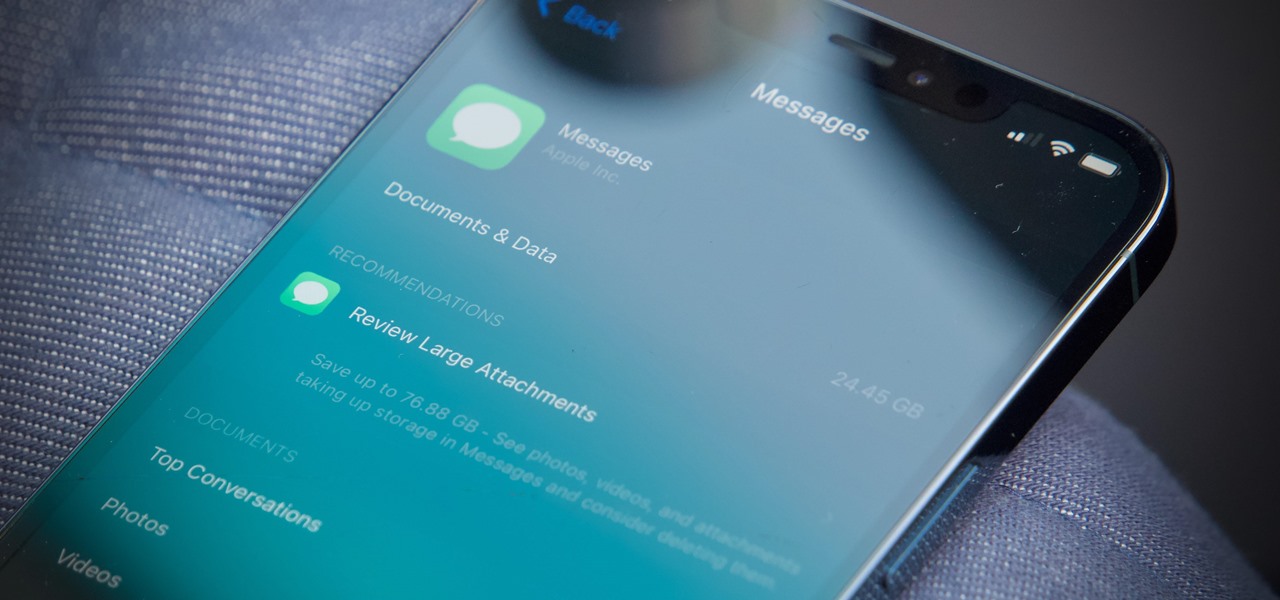
When iOS starts barking at you that you've run out of iCloud or iPhone storage, a quick trip to your settings to see what the culprit is may show that Messages is one of the worst offenders. But if deleting message after message doesn't free up your storage much, it's likely because "Messages" doesn't really mean messages.

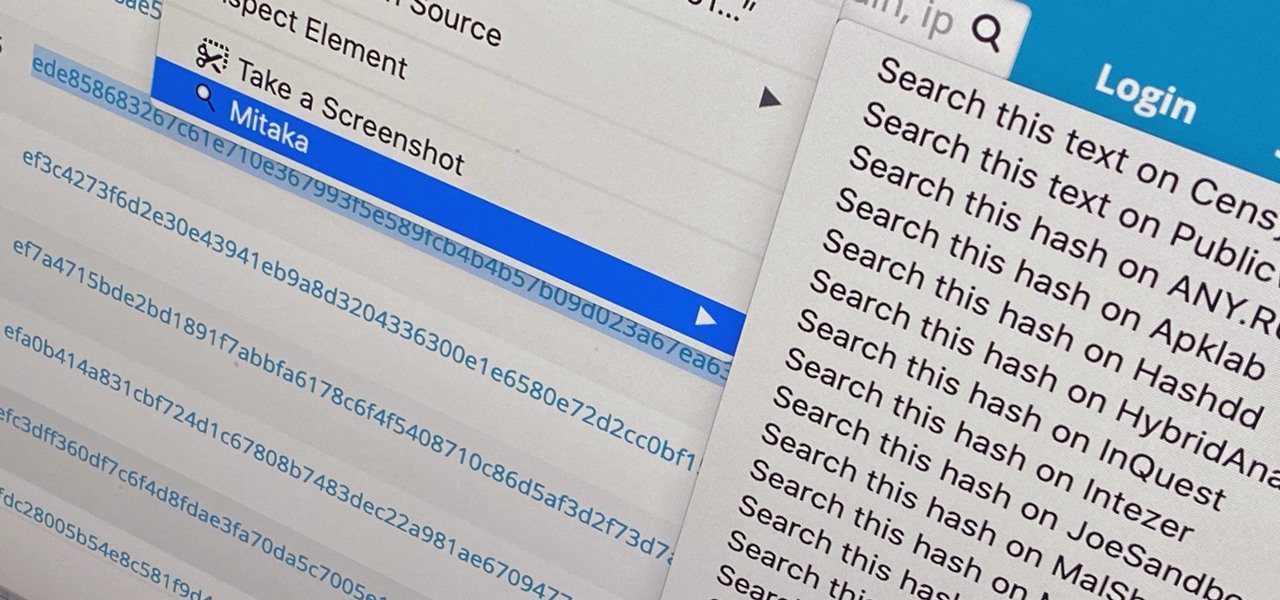
Web browser extensions are one of the simplest ways to get starting using open-source intelligence tools because they're cross-platform. So anyone using Chrome on Linux, macOS, and Windows can use them all the same. The same goes for Firefox. One desktop browser add-on, in particular, makes OSINT as easy as right-clicking to search for hashes, email addresses, and URLs.

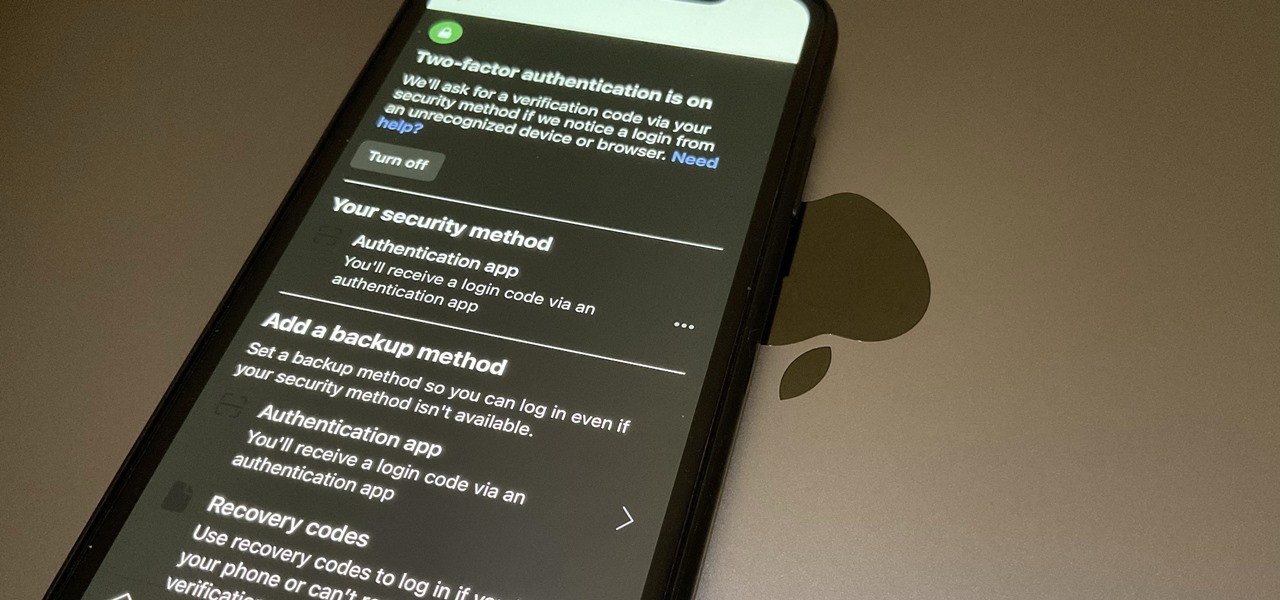
When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

For the uninitiated, it can be difficult to buy that special hacker in your life a perfect holiday gift. That's why we've taken out the guesswork and curated a list of the top 20 most popular items our readers are buying. Whether you're buying a gift for a friend or have been dying to share this list with someone shopping for you, we've got you covered with our 2018 selection of hacker holiday gifts.

Are you thinking of switching from an iPhone to an Android phone? Before you make a permanent change from Apple to the other side, it's good to try out the other ecosystem and see if it makes sense for you. If you can't get your hands on an Android phone to try it out, you can simulate Android right on your iPhone. You can even see what a foldable smartphone feels like!

When the topic of Pokémon Go comes up, the typical response is, "Do people still play it?" The answer is a resounding yes!

Most websites and apps support two-factor authentication (2FA), which adds an extra layer of security to your accounts by requesting another form of identification beyond username and password. The second factor can be a recovery code, physical security key, or one-time password (OTP) that only you can access, even if someone else has your password. This process is easier than ever thanks to iOS 15.

For its latest take on augmented reality-infused playsets, Lego is giving the young, and the simply young at heart, its twist on the viral lipsync format made popular by TikTok with Lego Vidiyo.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

Your iPhone is fairly secure by default, but Apple's Lockdown Mode takes it to Fort Knox levels of protection. If you're a high-value target for spyware, phishing attempts, and other sophisticated cyberattacks, it's an essential feature. But for almost everyone else, it's an extreme move. If you simply want to verify someone's identity when chatting, Contact Key Verification is a more practical option.

Safari keeps getting better and better on the iPhone, and that's exactly what happened with the latest Safari 16 update for iOS.

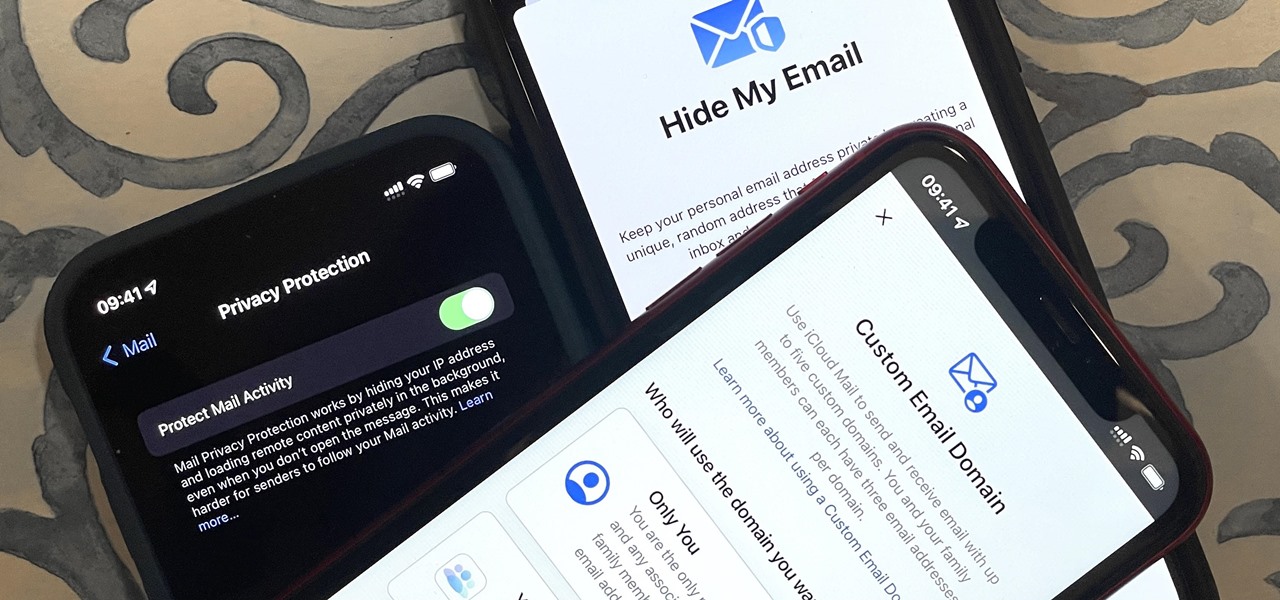
Privacy is a growing concern in the tech industry, but Apple has fallen behind many of its peers when it comes to email security. Fortunately, iOS 15 changes that. Your email address is the key to a vast amount of personal information, not to mention a stepping stone into your other online accounts, so it's great to see new features for iPhones that protect email accounts and their contents.

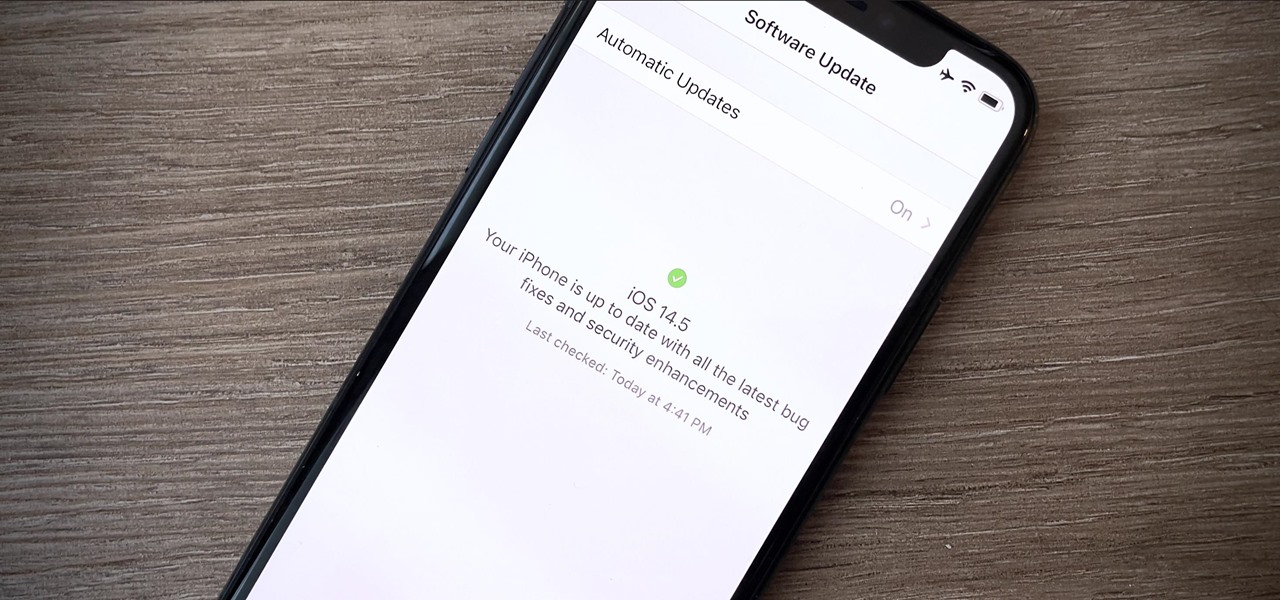
Your iPhone is full of features, many of which you might not even know about yet. Still, Apple keeps adding feature after feature with each new iOS update, and iOS 14.5 is no exception. The latest iOS version adds at least 69 features for your iPhone that you should be happy about.

Malevolent hackers can divert your incoming calls and texts to any number they want, and they don't need to be a criminal mastermind to do it. Even friends and family members can reroute your incoming calls and messages so that they know exactly who's trying to reach you, and all it takes is seconds of access to your iPhone or wireless account. These secret codes can help uncover them.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

The last iOS software update was a modest one, but iOS 17.4 has a lot more for your iPhone, including changes to emoji, Podcasts, security, Safari, widgets, Apple Cash, CarPlay, and more.

This quick tip demonstrates a method of slowing down your cloth simulations. This method can be used with various other animation techniques that involve deformation of your objects at a point level. Whether you're new to MAXON's popular 3D modeling application or are just looking to get better acquainted with Cinema 4D and its various features and functions, you're sure to enjoy this free video software tutorial. For more information, and to get started using this trick in your own Cinema 4D...

This clip uses a smoke example to examine source variations and upres (techniques which are useful preparation for the pyrofx tools). Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look. Upres smoke simulations in Houdini 10 - Part 1 of 2.

Welcome to the second Null Byte in a series educating you on Social Engineering awareness and techniques. Today, I'm going to show you how a saavy Social Engineer would trick a friend into unknowingly surrendering their Facebook password. My intent is to warn and demonstrate how easy it is to succumb to phishing via Social Engineering, and therefore expose yourself.

This two-part tutorial series offers a look at the basics of smoke simulations. This first part looks at setting up a simulation, the fields involved, how to visualise them. It also looks at temperature and bouyancy as well as vortex confinement. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more informat...

Que es el phishing y como protegernos para que no nos roben nuestros datos.

Here's a nasty little Null Byte. An open redirect vulnerability was found in both Facebook and Google that could allow hackers to steal user credentials via phishing. This also potentially allows redirects to malicious sites that exploit other vulnerabilities in your OS or browser. This could even get your computer flooded with spam, and these holes have been known about for over a month.

This four-part tutorial series presents a look at how to combine traditional keyframe animation with DOPs simulation. This first part contains an overview of how DOPs differs from SOPs and how to examine DOPs data using the Details View. It then looks at the RBDKeyFrameActive node as a method for combining keyframe and simulation animation. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself wi...

A tutorial covering a classic rigid body simulation of ball crashing through a wall of bricks. The first two parts cover building a (procedural) brick wall, and the final two parts cover converting it into a RBD simulation. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed...

Larry Silverberg and Chau Tran of North Carolina State University tested more than 100,000 3-D simulations of free throws to come up with this HowTo for you. The two engineers have determined the perfect trajectory. Check out their strategy below, via Wired's How-To Wiki.

Taken at sunset, July 3, 2011 at Phish's Super Ball IX Festival at Wakins Glen International Speedway, NY

This two-part tutorial looks at the techniques for rendering millions of particles in Houdini 10. The first part looks at using the popsolver to manipulate particles using both the standard pop nodes and dynamics forces. We use the interact pop, and random grouping of particles to build an ink like effect. We set up a smoke simulation and use the velocity field of that to advect (move) the particles. Whether you're new to Side Effects Software's popular 3D production program or a seasoned gra...

This two-part tutorial looks at the basic techniques for emitting smoke from particles.

This clip covers how to enable motion blur in Houdini, the difference between standard and deformation blur, motion blurring dynamics simulations, motion blur quality settings. Whether you're new to Side Effects Software's popular 3D production program or a seasoned graphic artist just interested in better acquainting yourself with the application, you're sure to be well served by this free video tutorial. For more information, including detailed instructions, take a look. Create a motion blu...

Last Friday's mission was to accomplish solving HackThisSite, Realistic 5, the fifth and last in my series of realistic hacking simulation missions. This time, telemarketers are invading people's privacy, and it was up to us to stop them! The job was to get root on the site and delete the contact database in order to return the right of privacy to its victims.

Last Friday's mission was to accomplish solving HackThisSite, realistic 4. The fourth in a series of realistic simulation missions was designed to be exactly like a situation you may encounter in the real world. This time, we are told "Fischer's Animal Products is a company that slaughters animals and turns their skin into overpriced products which are then sold to rich bastards! Help animal rights activists increase political awareness by hacking their mailing list."