Can lightning strike twice? Niantic is betting that it can with its latest augmented reality game based on the best-selling multimedia franchise Harry Potter.

In recent years, unwanted calls have become a top priority for the FCC. In 2016, analysts estimated that US customers received over 2.4 billion robocalls per month. As a result, the FCC has provided carriers new tools to combat this problem.

For the first time, you can officially use a computer mouse with your iPhone, thanks to Apple's new Accessibility settings in iOS 13. It works for all types of Bluetooth mice, so if you have one, it'll already work. Plus, those with wireless receivers and even wired mice are supported by using a USB to Lightning adapter.

Apple's scheduled to show off the first look of iOS 13 at WWDC 2019 on June 3, but what will the new operating system hold for iPhone? Rumors suggest that many features initially planned for iOS 12 will show up in iOS 13, codenamed "Yukon," and dark mode will be the big ticket item this year.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

OnePlus always seems to offer affordable yet powerful tools for videographers of all kinds. The camera hardware itself is crucial, but what's hardware without good software to highlight its real potential? It doesn't matter which version of the smartphone you have, they're all powered by the very same OnePlus camera app.

It feels strange to be walking through an open field in a small village in the English countryside. There's no one else around — just the four of us: me, my husband, my 12-year-old son, and my adult niece. The day is spectacular, particularly for England. The sun is shining, and the temperature is in the low '70s.

Hacker's are always looking for new ways to exploit systems and exfiltrate passwords, even in hashed form. Sophisticated brute-force attacks powered by high-end GPUs can perform millions of password attempts per second. But Ubuntu and Debian users aren't completely helpless. There are ways to harden the hashed password to better defend against Hashcat attacks.

Before attacking any website, a hacker or penetration tester will first compile a list of target surfaces. After they've used some good recon and found the right places to point their scope at, they'll use a web server scanning tool such as Nikto for hunting down vulnerabilities that could be potential attack vectors.

If you've ever spent any serious time examining the Chinese tech startup world, you know that it moves fast — very fast. The tech startups hailing from Beijing and Shenzhen are moving so fast that they're now in serious competition with Silicon Valley.

When you want to install a new tool or game on your iPhone, you go straight to the App Store to do so — but it's not the only place you can get apps from. Some developers use back alleys to get their apps to you, while others can trick you into installing them without giving it much thought. This can lead to malicious software running on your iPhone, software you'll want to get rid of asap.

The latest film addition in the American-produced Millennium series, The Girl in the Spider's Web, was just released on Blu-ray a few days ago. As you could expect, the movie has many hacking scenes throughout, just like the previous English and Swedish language movies centered around hacker Lisbeth Salander. Of course, with the quick pace of some scenes, the hacks can be hard to follow.

For anyone wanting to keep information private, plain text is a format of the past. Instead, cheap, powerful encryption is widely available, but often not easy enough to use to attract widespread adoption. An exception to this rule is EncryptPad, an easy to use application that lets you encrypt text, photos, or archives with strong encryption using a password, keyfile, or both.

So, you've lost your Apple TV remote. Maybe it's busted. What are you supposed to do now? You could go out and buy a new one, but they're expensive if you have a newer Apple TV with a Siri Remote, and wouldn't you rather spend that money on a movie? You might be without a working dedicated remote, but you likely have the next best thing already in your pocket.

A powered-off MacBook can be compromised in less than three minutes. With just a few commands, it's possible for a hacker to extract a target's password hash and crack it without their knowledge.

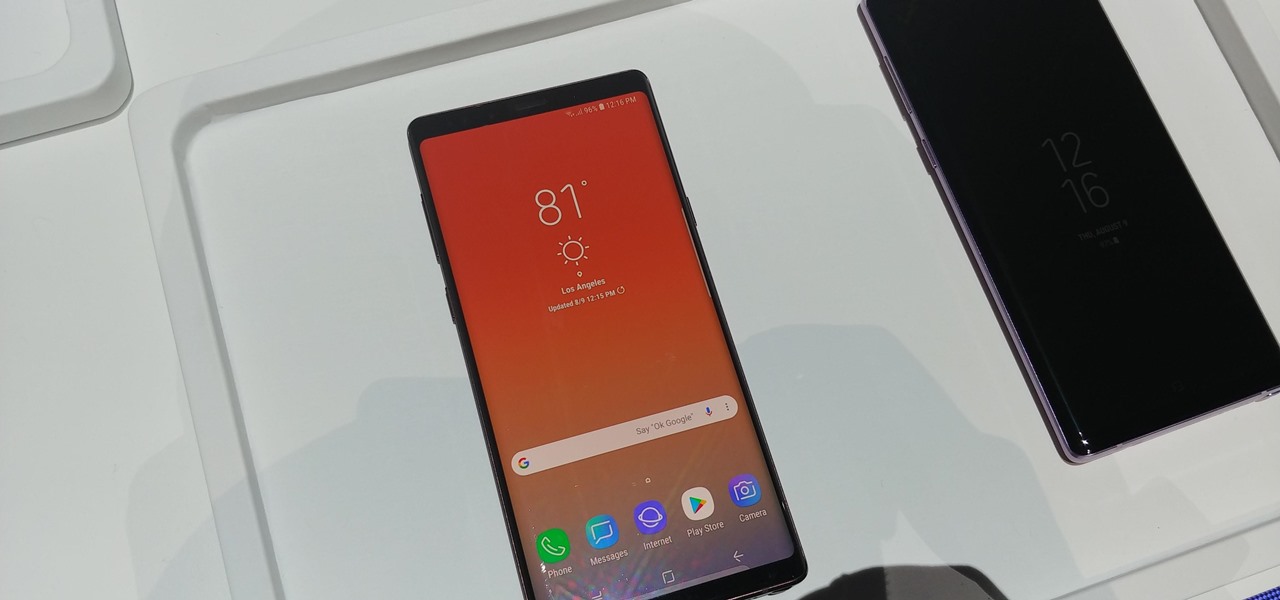
While many are familiar with Samsung, I'm pretty sure most Americans couldn't name the second-largest smartphone OEM. It's actually Huawei, and they recently released a spec-sheet dream of a phone in the Mate 20 Pro. So naturally, we wanted to see how it compared to the largest OEM's best offering.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.

On the surface, AppleCare+ seems like an expensive and gimmicky option to tack onto your already pricey iPhone 11, 11 Pro, or 11 Pro Max. Upon further inspection, however, you'll see that its seemingly expensive price tag is chump change compared to the fees you'll have to pay if you end up having to repair your premium device outside its one-year warranty.

In order to increase the security and harden the integrity of an email account and its content, you'll want to use PGP on your Windows, macOS, or Linux computer. This is usually the first thing security analysts do to protect communications with encryption, and everyone else should consider it too, especially since there's an easy way to incorporate PGP that anyone can follow.

Apple officially released iOS 12 to everyone on Sept. 17, and while the new iPhone XR, XS, and XS Max will come with the software by default, you have a choice on whether or not to update your current iPhone model from iOS 11. There are a lot of tempting features to want to update right away, but there are also some compelling reasons to wait it out and install at a later time.

Performance and stability improvements, as well as new features, are just some reasons to install iOS 12, but new changes mean new battery health challenges. It can be difficult to boost battery life while taking advantage of everything this update has to offer. Luckily, there are plenty of ways to avoid unnecessary battery drain when using iOS 12 on your iPhone.

Kali Linux, by default, probably doesn't have everything you need to get you through day-to-day penetration testing with ease. With a few tips, tricks, and applications, we can quickly get started using Kali like a professional white hat.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Following the launch of the Magic Leap One earlier this month, the device and the company took a few hits from early reviewers. But it turns out those were just love taps compared to the absolute scorched earth acidic screed penned this weekend by someone well credentialed to dissect Magic Leap One: Oculus Rift creator Palmer Luckey.

Since getting our hands on the Magic Leap One last week, we've been methodically delving into each feature and reporting our findings step-by-step. Earlier this week, we took a look at the Screens app (a video viewer) and the Helio app (an AR web browser). This time around, we'll be digging into the Create app, the experience that allows you to fill the real world with objects that transform the nature of your local reality.

It was only a few years ago when the idea of a 5+ inch display on a smartphone was unreal. With most hovering around four inches at the time, a phone that big seemed impossible to hold. We've come a long way since then, but it appears another wave of large displays will soon hit us, and they are all at least six inches.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

Net neutrality is dead and your internet service providers can collect all the data they want. While VPNs are a great way to protect some of that privacy, they're not perfect. There is another option, though, called Noisy, which was created by Itay Hury. It floods your ISP with so much random HTTP/DNS noise that your data is useless to anyone even if they do get it.

While many of you were off surfing and lounging on some sandy beach or trying to figure out how to balance work with sky-high summer temperatures, I've been talking to all the companies that make augmented reality what it is today.

Apple released the third beta of iOS 12 for developers on Tuesday, July 3. The update comes exactly two weeks after the release of the second developer beta, which introduced a variety of fixes as well as new issues, and just one week after the release of the public beta. Public beta testers received this iOS 12 update on Thursday, July 5, labeled as public beta 2.

While there isn't as much personal data residing on your Apple Watch as there is on your iPhone, it's still a good idea to set a passcode for it and lock it up when you're not using it. If you don't, while it's charging or otherwise off your wrist, others may be able to sneak a peek at your activity, messages, emails, and other personal details. Plus, you won't be able to use Apple Pay without one.

Don't think because your MacBook is using FileVault disk encryption your device is secure or immune to hackers. Here's how to find out if that FileVault password is strong enough to withstand an attack from a motivated attacker.

Have you been noticing SpaceX and its launches lately? Ever imagined how it would feel to launch your own rocket into the sky? Well, imagine no longer!

Many operators use elevators to control access to particular floors, whether it be the penthouse at a hotel or a server room in an office building. However, the law requires them all to have a fire service mode, which gives emergency access to restricted floors, and a hacker can use that to bypass security altogether.

Developed by Open Whisper Systems, Signal is a free, open-source encrypted communications app for both mobile and desktop devices that allows users to make voice calls, send instant messages, and even make video calls securely. However, a vulnerability was recently discovered for the desktop version that can be turned into a USB Rubber Ducky payload to steal signal messages with a single click.

Samsung Experience (better known as TouchWiz) can take some time to get used to when you switch to a Galaxy from another Android device. It's a bit heavy-handed with the features, and many consider the UI theme to be a little over the top. Thankfully, there are several stock settings that can dial this back.

A burner number isn't just for criminals and cheating spouses. In this digital world, with many of our interactions being conducted online, a throwaway phone number acts as a buffer — it lets you enjoy the web without having to give out your personal information, such as real name or phone number.

The conversation of which operating system is most secure, macOS vs. Windows, is an ongoing debate. Most will say macOS is more secure, but I'd like to weigh in by showing how to backdoor a MacBook in less than two minutes and maintain a persistent shell using tools already built into macOS.

Hashes containing login passwords are transmitted between Windows computers on local Wi-Fi networks. By intercepting and decrypting these hashes using Responder and John the Ripper, respectively, we can learn a target's login credentials which can be later used to gain physical access to their computer.

Contrary to popular belief, augmented reality apps have been available for a while now. I remember using the Layar app (still available for iOS and Android) to explore nearby businesses and landmarks with varying success via an early-generation Android handset.