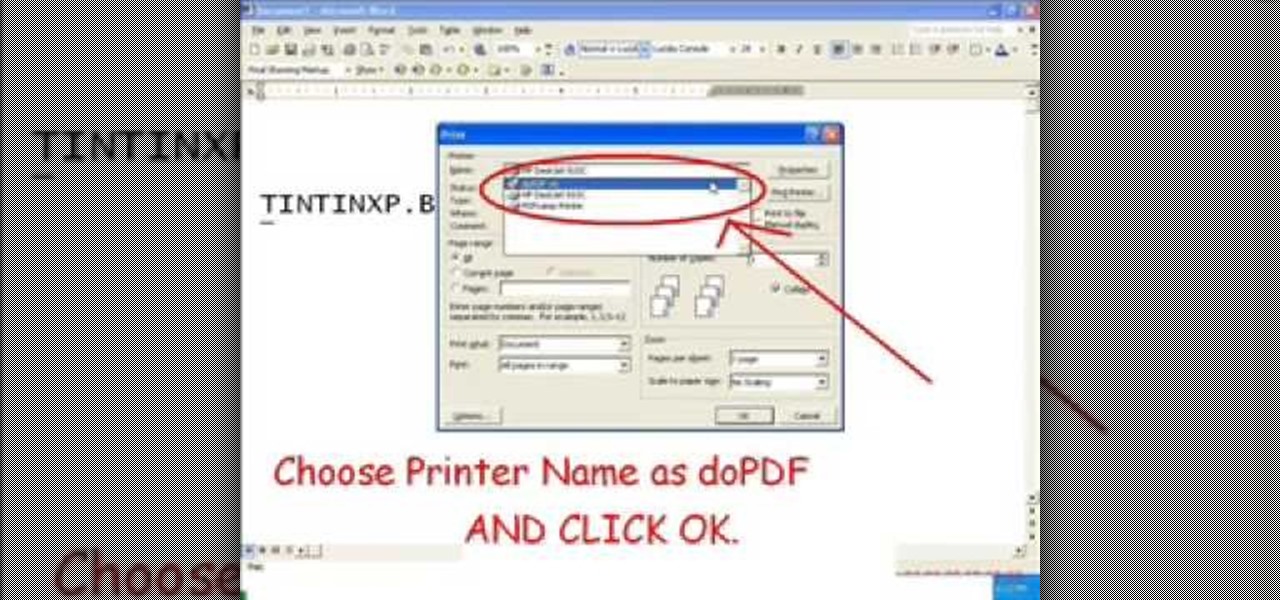
In this video tutorial, viewers learn how to convert word documents to PDF format. This task is very easy, simple and fast to do. Users will need to download a program from this site: DoPDF. Once downloaded and installed, open the program and open the file that you want to convert. Then click on File and select Print. Choose the printer name as "doPDF" and click OK. When a window pops up, select the location where you want to save the file. This video will benefit those viewers who have a tex...

Before you can work in Adobe Flash CS3, you'll need to know how to work with it. Learn how with this clip. Whether you're new to Adobe's popular Flash-development platform or a seasoned web developer looking to better acquaint yourself with Flash CS3, you're sure to benefit from this free software tutorial. For more information, including detailed, step-by-step instructions on how to use the program's draw tools, watch this video guide.

As many of you stop-motion animation practitioners out there have probably realized, Legos are a great material for that medium, allowing for great diversity while being relatively easy to work with. Can they fly though? This video features a British boy explaining how to use a free computer program called Bafran to make Lego characters appear to be flying in an animated video.
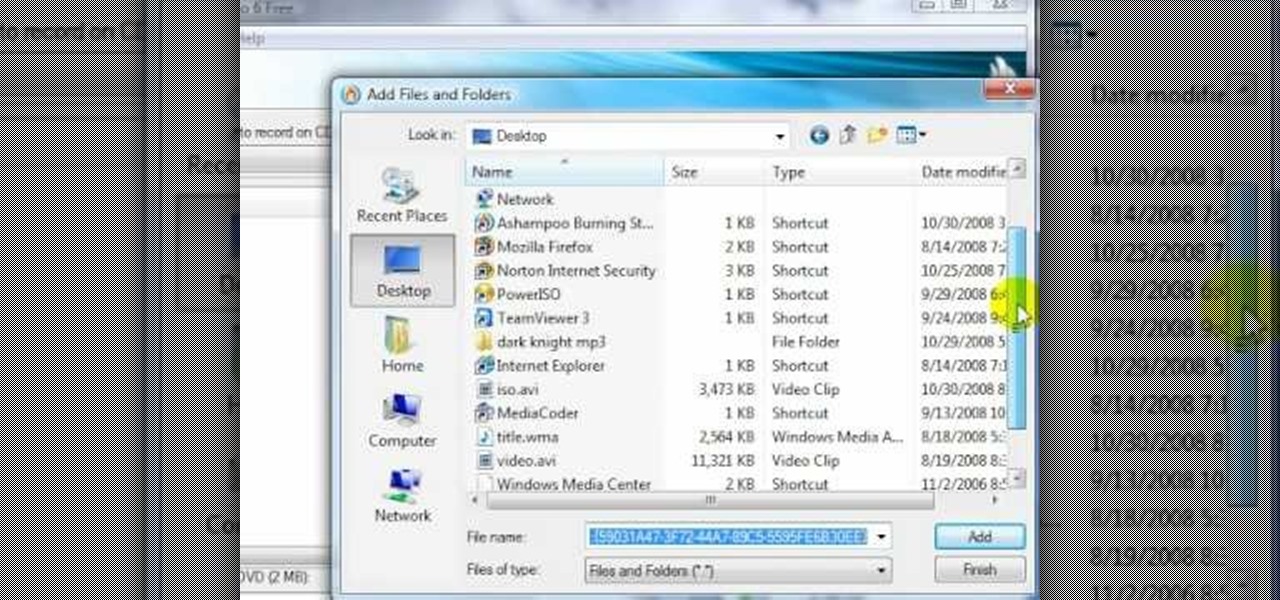
In this video tutorial, viewers learn how to create an ISO image. Users will need to download the program, Ashampoo Burning Studio 6. Begin by going to the Google search engine and search for the program. Select the result from download.com. Click on Download Now and save the file. Double-click on the file and follow the instructions to install it. Then open the program and select Create/Burn Disc Images. Select the type of disc image that you would like. Then click on Add and select the file...

In this video tutorial, viewers learn how to rip audio and video from You Tube to an i-Pod or computer. Users will need to download the Free Studio program from located the video description. Once the file is saved, double-click the file and follow the instructions to install the program. Now find a video or audio from You Tube and copy the URL. Now open the program, paste in the URL and download the file. This video will benefit those viewers who enjoy watching or listening to videos on You ...

This video from CNET Insider Secrets tells you how to recover deleted files from a data drive. If a disk is still readable by the computer, files may be recovered. Files may be recovered using the PhotoRec program, PC Inspector or other programs that may be available. An example is shown where mp3 files are deleted from a flash drive. We are then shown how files are recovered using the PhotoRec program, including how to select the correct file system. The mp3 files are recovered along with va...

This video teaches you how to open .zip files with a just few easy steps. First, you need to download a program Winrar. The download can be found at http://www.rarlab.com/download.html and the download should start immediately. Once the download is complete, open the program.

Now your computer is running slowly while opening the multiple programs, and for checking mails. The following steps easy to get faster the computer.

A quick video showing how to get free music online. May take a couple minutes per song. To prove quality I used the song i download in the video as background music. "I Wish" by Skee-Lo

New to the Ubuntu Linux distribution (or one of its derivatives) and looking for a way to start programs automatically when you boot up your machine? Take heart: This video tutorial will show you how to accomplish just that using your system preferences. Take a look!

New to OpenSceneGraph and not quite sure where to begin? If so, you're in luck. This tutorial will walk you, step-by-step, through the creation of your very first OpenSceneGraph program for the Mac OS X platform.

Don't let a bunch of programs run in the background and hog your Palm Treo's resources! Watch this electronics tutorial video to learn how to close them out. This how-to video makes maximizing your Palm Treo 750's power easy.

Watch this software tutorial video to learn how to quickly unzip archived files using the program WinZip. WinZip makes unzipping and unarchiving archived files quick and easy, and this how-to video provides helpful tips on how to use the program.

This computer programming tutorial screencast teaches programming tips and tricks on Ruby on Rails. This Ruby on Rails how to video covers basic string manipulation.

To avoid sports-related injuries, it is essential to warm-up before a race or a game or even before a training or practice session. Watch this video tutorial to learn how to warm up before running by doing side steps from Gilbert's Gazelle training program. This how-to video is a must watch for all track and field athletes.

Check out this video screencast tutorial to help beginner iPhone programmers get started. This tutorial shows how to draw "Hello World!" text on the screen of the iPhone in Mac OSX with the help of Objective C (ObjC) in Xcode for Cocoa programming on your Mac OS.

Learn how to apply for a Google Books Partner Program account, which allows you to submit your content for display on Google Book Search.

A VB.Net 2008 tutorial on how to make a program that can count cards in a blackjack game.

A tutorial on how to unroll and append elements to an array when programming in Java.

Learn to program If & Switch Statements in Java. This tutorial uses Java 1.6 with NetBeans 5.5.1 beta

Delphi controls have an owner and parent property, find out what the difference is and how to use them when programming in Delphi.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to detect motion from dual input the Wiimote using GlovePie. You'll be able to connect two Wiimotes to your PC.

In this tutorial you will see how to use Jimmy's speed math program that he wrote in Flash. A download to the program is included. This is a GREAT way to help your kids or students (or maybe adults?) get better at math.

Microsoft Excel is one of the most powerful programs for modern businesses. By allowing you to manage, sort, and analyze large collections of data, Excel provides an essential service for any company interested in using the power of data science to its advantage.

Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

They're finally here. Apple revealed the brand new iPhone 11, 11 Pro, and 11 Pro Max on Sept. 10, and despite the questionable names, these are the best iPhone models money can buy. If you're looking to get your hands on one of these devices as soon as possible, there are few important dates you need to know.

With $100 million in grant funding already available to developers via its MegaGrants program, Epic Games is sweetening the pot with some gear for Magic Leap developers.

On April 26, 2019, Sinemia posted a note on its website stating it has ceased all operations in the United States. It's not known if it continues to work in other countries or if US users will be getting any refunds, particularly, for annual subscribers.

Format strings are a handy way for programmers to whip up a string from several variables. They are designed to save the programmer time and allow their code to look much cleaner. Unbeknownst to some programmers, format strings can also be used by an attacker to compromise their entire program. In this guide, we are going to look at just how we can use a format string to exploit a running program.

Being able to write your own hacking tools is what separates the script kiddies from the legendary hackers. While this can take many forms, one of the most coveted skills in hacking is the ability to dig through the binary files of a program and identify vulnerabilities at the lowest level. This is referred to as binary exploitation, and today we're going to check out a tool known as Protostar.

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

The status of Uber's driverless program remains a big unknown amid the company's recent woes, but a reported multibillion-dollar shot in the arm by Japanese tech giant Softbank could change all that.

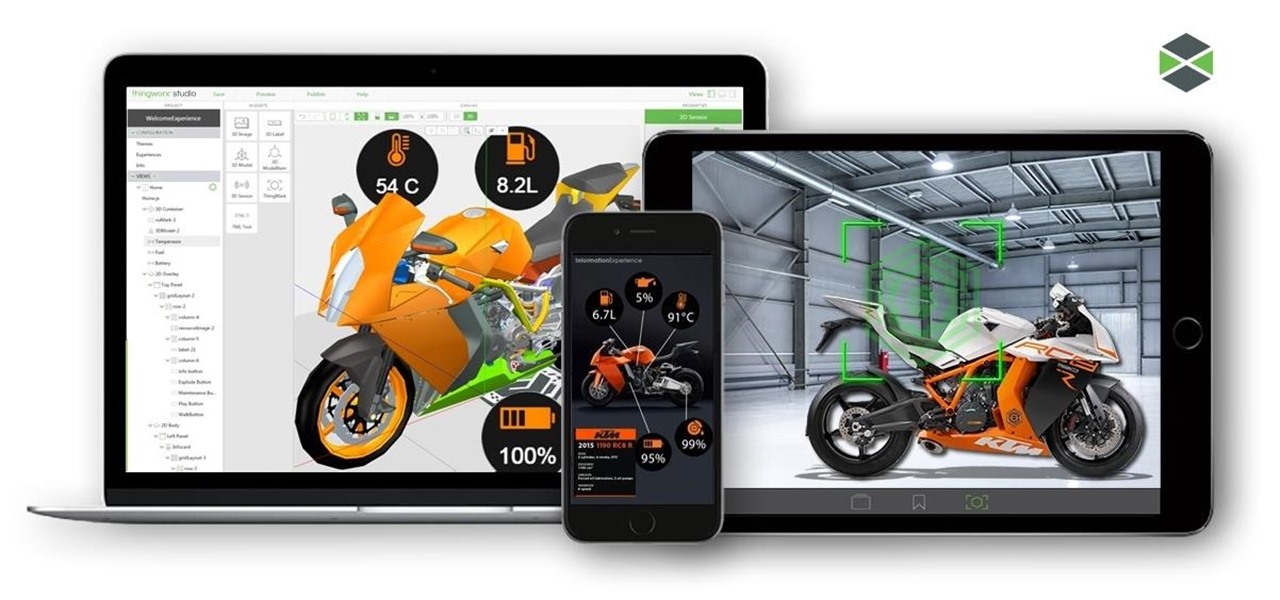
For companies wary of the temperature, PTC just made it easier for them to dip their toes in the waters of augmented reality.

In the summer of 1976, 4,000 American Legionnaires descended upon the Bellevue-Stratford Hotel in Philadelphia, Pennsylvania, for a four-day convention. Several days later, many of the attendees experienced symptoms of severe pneumonia. By the beginning of August, 22 people had died. The Centers for Disease Control and Prevention (CDC) estimate that about 180 people were sickened and 29 people died before this mysterious outbreak burnt out.

Remember that feeling when you first took your smartphone out of the box, powered it on, then proceeded to futz around with it for the rest of the day non-stop? If you've owned your device for more than a year, chances are, that scenario is a distant memory by this point.

If you want to make some money from catching bugs and are sick of pentesting Facebook, Google, and Microsoft's products, Uber may be your new favorite playground.

Researchers have discovered a "severe vulnerability" that allows attackers to use eBay to distribute malware, and the online auction company has no plans to fix the problem.

How's it goin'? In this tutorial, we will learn about the security issues of the popen and system functions. I've seen a few people attempting to run command line utilities or whatever it is they require with calls to these two functions but may not know the security implications which come along with it. I will show you using an example from the wargame IO Smash The Stack.

In many programs on Linux, you'll come across programs which allow you to specify additional arguments instead of just simply running the program by itself. If you've used the Kali distribution, I'm more than certain you'll have come across these with the command line tools, else if you have been following these tutorials, we have already come across three tools which also use the same technique, i.e. gcc, gdb and wc. How do we do this with C? Let's find out.

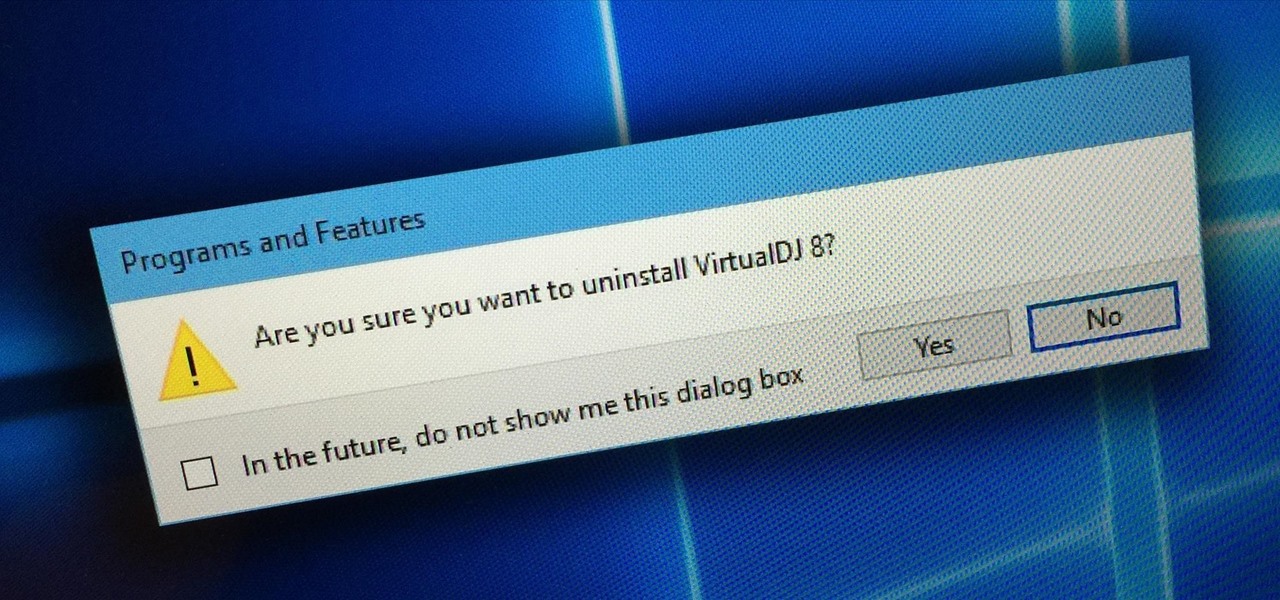
Uninstalling programs in Windows is not the nicest procedure. Some programs bundle a nice uninstaller with them which helps to ease the process. Other programs, mainly those that utilize the Windows Installer technology, begin the uninstall process right away. This can potentially be problematic for users who are trigger-happy with the mouse.