Although next week will mark the late David Bowie's 72nd birthday, his fans and admirers are the ones receiving a gift in the form of an augmented reality app that explores the artist's career

Location-based gaming pioneer Niantic has been preparing its flavor of AR cloud, the Niantic Real World Platform, to bring more realistic and interactive augmented reality experiences to mobile apps. And now the company is looking for a few good developers to help execute its vision on the platform.

Magic Leap continues to launch new AR apps on its fledging app store before the door closes on 2018, and this time the app is a sequel from a veteran VR developer and early Magic Leap development partner.
Keeping track of your physical activities can be difficult, especially if you have a hectic lifestyle with responsibilities to constantly stay on top of. Thankfully, Samsung Health is there to help you log your workout routines, leaving you with one less thing to keep track of as you go about your busy day.

This year's holiday shopping season is shaping up to be fertile ground for augmented reality to show its worth, as both Walmart and Target have crafted immersive experiences designed to engage shoppers in the coming weeks.

When computers have vision but people don't, why not have the former help the latter? That's the gist behind the Cognitive Augmented Reality Assistant (CARA), a new HoloLens app developed by the California Institute of Technology.

If you've grown bored of day-to-day hacking and need a new toy to experiment with, we've compiled a list of gadgets to help you take password cracking and wireless hacking to the next level. If you're not a white hat or pentester yourself but have one to shop for, whether for a birthday, Christmas present, or other gift-giving reason, these also make great gift ideas.

Amid the opulent and historic confines of Paris, Microsoft is now hosting an exhibit at a local museum that brings a historic map of a Normandy tourist destination to life in augmented reality.

Augmented reality content makers often position the technology as a new storytelling medium. And who loves stories more than children?

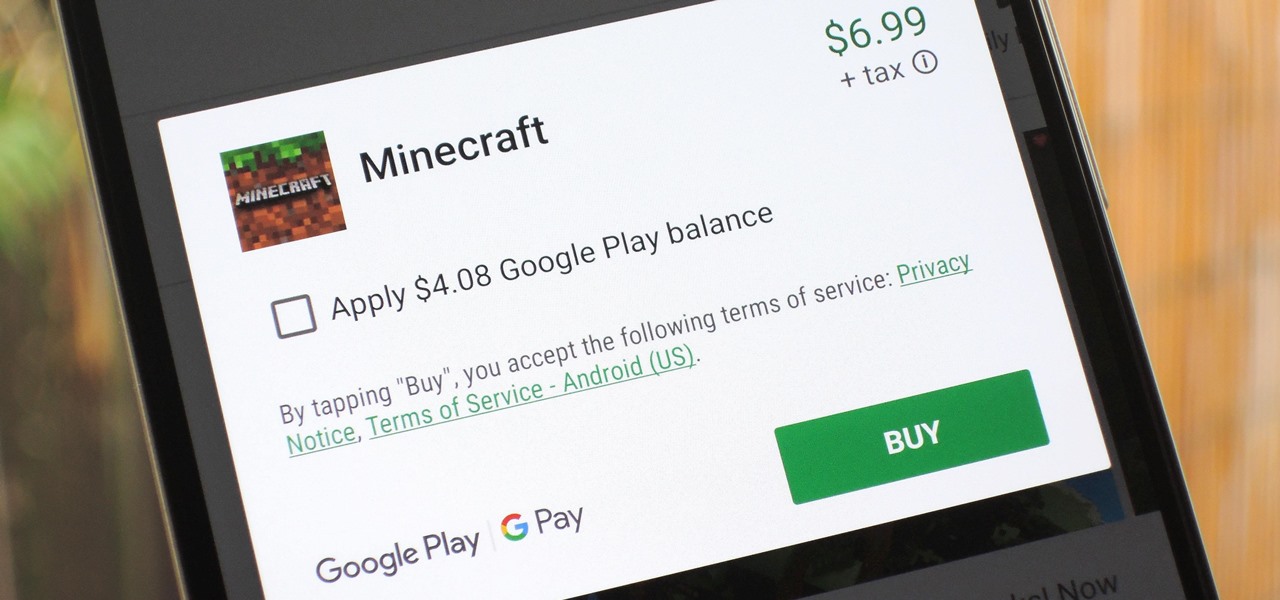
The iTunes App Store makes it easy to buy an app or game on someone else's behalf, and it's a great way to send an iPhone user a thoughtful gift. The Google Play Store doesn't have such functionality, but there are still a few workarounds to accomplish the same goal: gifting an app to an Android user.

If you're hungry for pizza and ordering from Domino's in Australia, you can now see what your pie will look like in augmented reality before placing your order.

Less than three weeks after Rovio Entertainment announced the game, the augmented reality adaptation of Angry Birds is now available for the Magic Leap One.

Traditional media institution The New York Times continues to break new ground in its augmented reality news coverage, this time with a 3D volumetric capture of model Ashley Graham.

When BlackBerry first announced the KEY2 back in June, the biggest gripe we heard was about the price. It was reasonable criticism, as BlackBerry was asking a lot of its consumers at $650. Knowing this, BlackBerry went back, made some downgrades, and cut the price, creating the KEY2 LE.

Computer vision company Blippar has already dabbled with outdoor AR navigation, but now it wants to make it easier for people to make their way through indoor spaces with augmented reality.

Luxury automaker Mercedes-Benz has joined the growing list of automakers adopting augmented reality to provide an assist to its manufacturing operations, in this case, via the Microsoft HoloLens.

The long and slow road toward the actual release of the Magic Leap One appears to be accelerating, with a couple of new demonstrations of how the system works revealed in this week's creator's portal updates along with the company's developer documentation.

If you're not impressed with the current crop of AR content, and you're worried this may put a damper on the industry's growth, these stories should give you cause for some optimism.

Location-based gaming pioneer Niantic has offered a preview of its augmented reality cloud platform that could change the immersive content game yet again.

If you cover a particular area in tech long enough, you develop certain pet peeves, and one of mine happens to be devices that attempt to keep us wed to the Google Glass style of augmented reality. And while I remain mostly uninterested in such devices, one of these products recently earned my admiration and might work for you, too, under the right circumstances. It's called the Golden-i Infinity.

The availability of space for filming immersive content has just gotten bigger with the launch of Innovation Studios by Sony Pictures Entertainment.

With the announcement of ARKit 2.0 at WWDC 2018, Apple is bringing some powerful new capabilities to mobile augmented reality apps this fall.

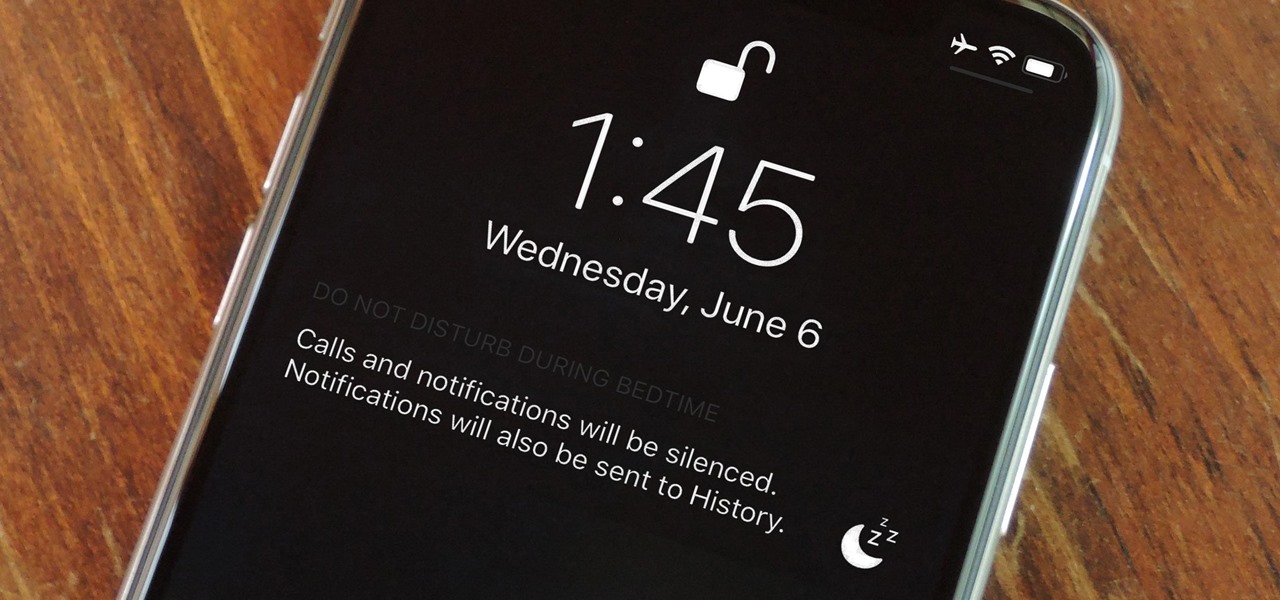
Let's say you wake up in the middle of the night and check your phone to see the time. As soon as you do, you're greeted by a wall of notifications on your lock screen. You just wanted to know how much longer you could sleep, but now your mind's racing after seeing all of the messages you need to deal with. Thankfully, iOS 12's new Bedtime Mode has a solution for this problem.

There are currently 27 available Animoji to choose from in iOS 13, but you're not limited to Apple's animated emoji characters — you can make your own. They're called Memoji, an available feature since iOS 12, and they're highly customizable.

As expected, Apple revealed today at the WWDC keynote that ARKit 2.0 will support multiplayer gaming support and persistent content, which will arrive this fall with iOS 12.

A convincing domain name is critical to the success of any phishing attack. With a single Python script, it's possible to find hundreds of available phishing domains and even identify phishing websites deployed by other hackers for purposes such as stealing user credentials.

After more than a year and a half of silence, the rumors have morphed into reality: Microsoft has finally released an update for the HoloLens. And with that update comes a collection of new features that hint at big plans for the HoloLens this year.

Before the Sept. 2017 event held by Apple, we thought the new iPhone X would come in three different colors. While only a Space Gray and Silver option made it to the Nov. 2017 release, the missing third hue may finally be on its way, if the latest rumors are to be believed. If you can't wait for the new Blush Gold color, here's when and how you can expect to get your hands on one.

Following the surprise release of Magic Leap's SDK on Monday, March 19, Unity, Unreal Engine, and Mozilla followed up by announcing official partnerships with the company.

Google and Samsung are the biggest players in the Android world. Despite a rocky launch, Google's Pixel 2 XL became one of the premier Android devices of 2017, headlined by fast performance and a pure version of Android. Still, many users prefer Samsung's offerings, and their Galaxy S9+ is poised to be the phone to beat in terms of specs.

In any business, there are a number of questions companies must answer in order to get customers to buy a product or service. The same holds true for companies selling augmented reality headsets.

It's easy to have your password stolen. Important people like executives, government workers, journalists, and activists face sophisticated phishing attacks to compromise their online accounts, often targeting Google account credentials. To reduce this risk, Google created the Advanced Protection Program, which uses U2F security keys to control account access and make stolen passwords worthless.

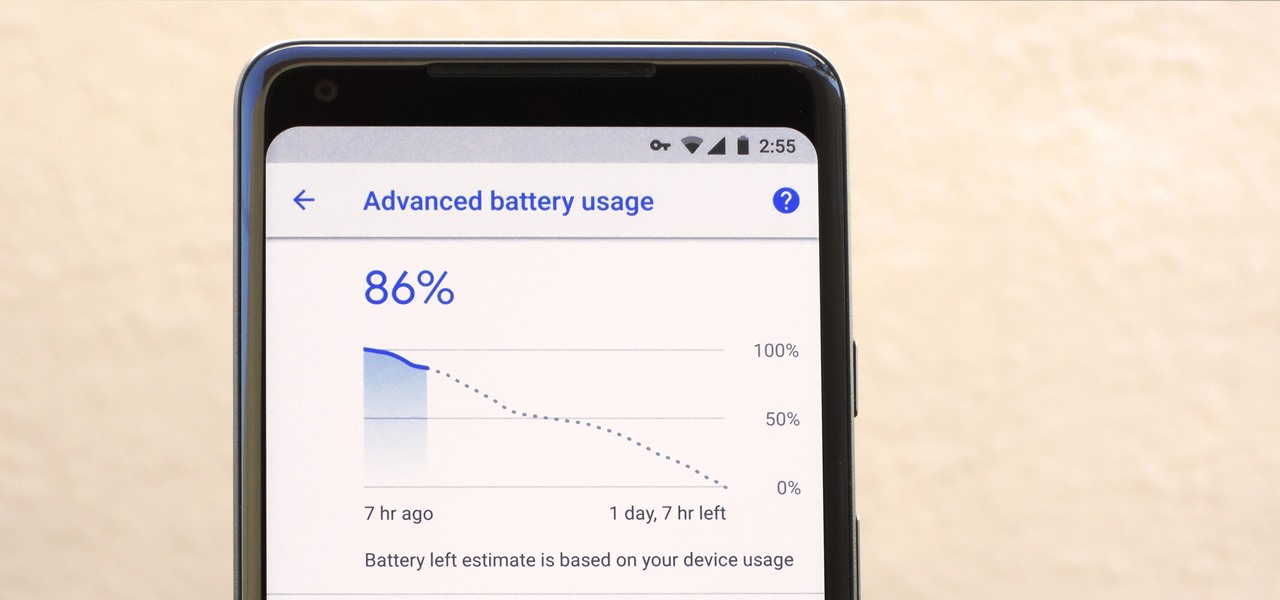
After Apple's recent fiasco, it's now common knowledge that smartphone batteries degrade over time. But aside from causing terrible battery life, a degraded battery can also trick your phone's software into thinking the device has more juice left than it actually does.

Stop me if you've heard this one before: scan an image with your iPhone's camera and augmented reality content shows up.

There's no doubt Kali has established itself as the most popular penetration distribution available. However, just because it's the fan favorite of beginners and security researchers doesn't make it right for everyone. Manjaro Linux is a beginner-friendly Arch-based distribution which can be easily weaponized with the Black Arch expansion, creating a friendlier first-time Arch experience.

On Monday, toy maker Merge virtually blasted its way into CES 2018 with a new tech-meets-toys innovation in the form of an augmented reality gun controller for use with smartphone-powered first-person shooter apps.

It finally happened. Magic Leap has given the world its first glimpse at its debut device, the Magic Leap One Creator Edition.

If you used Touch ID on an iPhone before, all you had to do to install apps and games from the App Store was rest your fingertip on the Home button. On the iPhone X, there's Face ID instead, and Apple has included on-screen instructions to help everyone adjust to the lack of Home button. Still, those instructions may not be working for you, but the solution is as simple as a misinterpretation.

Now that the holiday season has officially kicked off, Office Depot has updated its popular Elf Yourself app with a few new augmented reality options.

There's a new macOS vulnerability that hackers within physical reach of your computer can use to gain root access to your system and accounts. Just by using "root" as the username and a blank password on a privilege escalation prompt, someone can install malware on your computer, access hidden files, reset your passwords, and more. Root access gives them the ability to do anything they want.