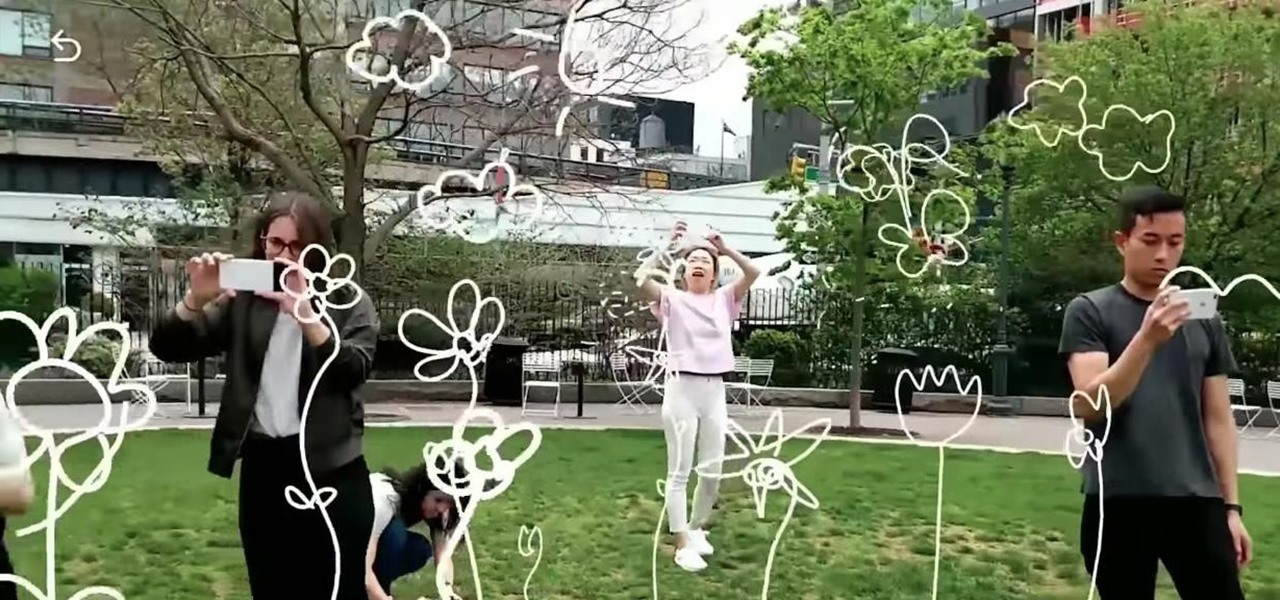A concussion is the most common type of brain injury, often occurring in bike and car accidents or during sports. Many people think that you have to lose consciousness to have a concussion but that is indeed not the case. A concussion occurs any time you have some type of trauma to the head. That can be jostling of the head where the brain is basically just hitting the inside of the skull or it can actually be where you hit your head or somebody that falls and they fall and hit their head. Ki...

Restorative yoga combines physical therapy with yoga to help bring activity back to the body. Learn restorative yoga poses from an instructor in this free yoga video series.

Increase flexibility through stretching exercises with the help of a workout partner. Discover how to stretch the back, shoulder, butt and neck muscles using partner resistance in this free fitness video series from a professional physical trainer.

This is the basic prayer that should be meant from your heart and soul, and not just saying the words from your physical tongue. A true redeeming confession to the lord Jesus Christ, asking Him to come into your heart as your personal lord and savior, asking Him to forgive you of all of your sins, rejecting all evil from continuing to be involved in your life, and rejecting this world's ways, and listening and following God's rules and directions.

Learn how to do mountain climber exercises. Presented by Real Jock Gay Fitness Health & Life. Benefits

Getting angry makes you look weak, especially in an argument. Defuse your temper with these helpful tips.

Drinking too much is bad for your health and your wallet. Here are a few simple strategies for cutting back and keeping it in moderation.

Research shows that color can have a powerful effect on our emotions. Start harnessing that power today. Watch this video to learn how to improve your life with chromotherapy.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

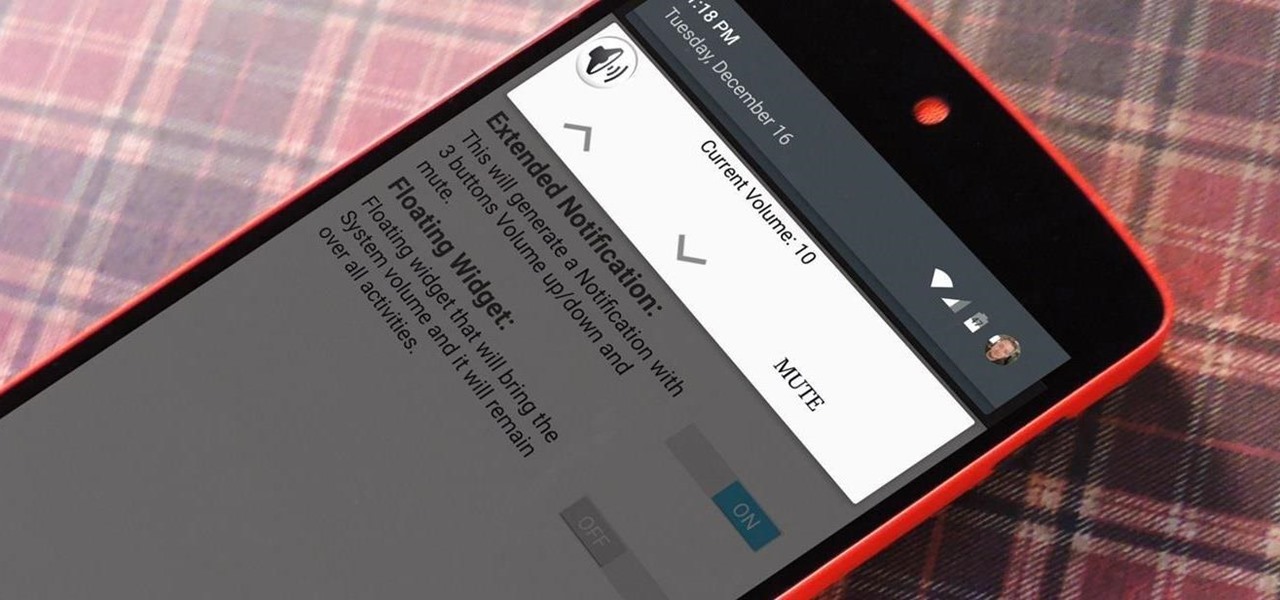
For many of us, our work phone and our personal phone are one and the same. Just any old phone isn't going to cut it when you need to meet a deadline — a phone with built-in features that make it easier to get things done is almost a must.

Pain is, for the most part, unavoidable when you stub your toe, break your arm, or cut your finger open. It's instantaneous and, in some cases, long-lasting, but it only feels as bad as you want it to. Yes, that's right—that pain is all in your head.

Ever think you could lose weight from eating MORE food? Well, if you love to nosh, Volumetrics is the right diet plan for you. Volumetrics is based on the density of food, and how it will be absorbed into your body. If you think this might be right for you, give it a try! Good luck!

Digital artist Beeple's $69 million NFT art auction at Christie's has a second act called Wenew, and includes attempting to open the digital art floodgates to mainstream collectors and artists alike by using physical goods.

There're plenty of great ways to get traffic, especially this off-site optimization technique using classified ads to point website traffic back into your site itself.

On April 26, 2019, Sinemia posted a note on its website stating it has ceased all operations in the United States. It's not known if it continues to work in other countries or if US users will be getting any refunds, particularly, for annual subscribers.

The Super Bowl of bicycle racing, the Tour de France, added augmented reality to its TV broadcast this year.

If you aren't convinced that mobile augmented reality apps need occlusion (or you don't know what the word even means), you really need to watch the latest video from AR cloud startup 6D.ai.

We have some bad news for BlackBerry fans: It looks like the upcoming KeyOne flagship won't be shipped in April after all.

We've all walked into a restaurant with the best of intentions only to order something absurd, like a cheese-injected burger topped with bacon on a brioche bun. It's delicious for the few minutes it takes to eat the thing, and then you're left with a bellyful of regret and an inability to directly look at the numbers on your scale. Turns out that getting yourself to make healthy choices isn't as hard as one might think.

One of the biggest advancements in the new iPhone XS, XS Max, and XR is the dual SIM functionality that will let you use two cellular networks at once. Like Sinatra, however, Apple is known to do things its own way, so their dual SIM setup is a bit different than you might think.

While augmented reality is a means for presenting news to their audiences to some media outlets, Bloomberg is interested in how the technology can improve the way journalists work.

Don't Miss: The Difference Between Virtual, Augmented, & Mixed Reality

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Depression can come with physical symptoms - such as poor sleeping habits or aching joints. The theory explained in this video is that there is a relationship between the physical symptoms of an overactive immune system and depression. By supplementing a diet with Vitamin D and UV light, and thereby altering one's immune system, one can allieviate the symptoms of depression.

A dislocated shoulder results when the head of the humerus pops out of the socket joint. This is not a gradual event, but rather a sudden even where the shoulder moves out of its normal location. Learn how to treat a dislocated shoulder and stay fit in this sports medicine how to video.

The staff at Next Reality News is legitimately excited about the prospects that Google's ARCore could bring not only to smartphones and tablets running Android, but also to Android-based hardware such as smartglasses.

If you've ever taken apart an electronic device that uses physical buttons, you already know why these types of input methods are destined to fail. The rubberized contacts used in physical press-and-release buttons like those of a gamepad or keyboard are incredibly frail and can easily wear out over time.

Apple finally unveiled the iPhone 14, 14 Plus, 14 Pro, and 14 Pro Max, and there are a lot of improvements that'll make you want to trade in your current iPhone stat. But I wouldn't be so quick to upgrade because there's one "feature" that will make many of you rethink getting a new iPhone 14 series model.

Unwanted advertising is everywhere. Annoying pop-up ads, overly loud late night commercials, spam...it never ends. And before spam, there was junk mail. Junk mail is even worse because unlike TV commercials and internet ads, it's physical. You can't just delete or ignore it—and it's an awful waste of paper. So what can you do about it?

Every time you make a call or send a text, you're giving the recipient your phone number. This can be quite the security vulnerability, opening yourself up to scammers, spammers, and the feds. In this how-to, we'll look at what a burner phone is, why you might want one, and how to get started using a free second phone number on your regular smartphone.

In the case of Apple Watch v. Fitbit, the winner comes down to the judge at hand. Apple currently offers two smartwatches — the Series 5 and the Series 3 — while Fitbit offers three models — the Fitbit Versa 2, Fitbit Ionic, and Fitbit Versa Lite. Whatever your assumptions about these devices are, throw them out the window, as each has something unique to bring to the table.

In a previous guide, I demonstrated how to extract images from a security camera over Wi-Fi using Wireshark, provided you know the password. If you don't know the password, you can always get physical with the Hak5 Plunder Bug. Using this small LAN tap, we can intercept traffic like images from a Wi-Fi or IP security camera if we can get physical access to the Ethernet cable carrying the data.

It appears that the new AR app from LEGO is inching closer to release.

Just as the Transformers animated TV series of the '80s were basically half-hour commercials for toys, a new Transformers AR app for iOS similarly functions as a promotion for the latest installment in the film franchise.

Welcome back, rookie hackers! We recently began an exploration of ways to hack using the Bluetooth protocol. As you know, Bluetooth is a protocol that connects near field devices such as headsets, speakers, and keyboards. Its minimum range is a 10-meter radius (~33 feet) and maximum is at 100 meters (~328 feet).

Everyone wants to have a pretty young thing on their arm, but not everyone can get it. To secure perfect trophy wife of your dreams, you need to meet a few criteria. Check out this tutorial and learn the do's and don'ts of dating younger ladies.

Millions of travelers pass through airports each day without understanding how powerful and insecure a boarding pass can be. Anyone can scan the boarding pass barcode with a mobile app, allowing access to frequent-flyer accounts and even a passenger's temporary airline account. In this guide, we will explore how hackers scan and decode the information contained in a boarding pass barcode and why.

It's that time of year again. The world's largest electronics companies are sending representatives to the annual Mobile World Congress event in Barcelona, and for gadget lovers like us, that means we'll get our first look at some of this year's biggest upcoming flagship smartphones.

In the arms race between ARKit and ARCore, Google scored a big win with the announcement of its Cloud Anchors shared AR experiences platform at Google I/O on Tuesday.

The rumor train for Samsung's upcoming flagship phone is now running on full steam, and some of its cargo (or lack thereof) might not be warmly welcomed by many when it finally pulls into the station.