Smartphones are almost always connected to the internet, so it stands to reason that they can be hacked remotely. Or perhaps a jealous boyfriend or girlfriend got hold of your device physically, in which case they could've potentially installed a keystroke logger, a virus, or any other type of tracking app to spy on you.

As our lives grow busier, we get secluded in our indoor activities, consuming all types of fatty junk food and what not. Obesity is a very obvious yet unfortunate outcome of our unhealthy living standards. With it comes the predictable rush towards efforts to lose weight. Consequently, we have designed hundreds if not thousands of ways to lose fat and grow slimmer. To ease out your choice of ways, here is a list of the best ways to lose stomach fat. Step 1: Don't Eat Sugar

Mobile payment systems have been around for almost 5 years now, starting with Google Wallet. But when Apple got into the game last year with their new Apple Pay service, things really started to take off. Around this time, Samsung responded by acquiring an up-and-coming mobile payments company that owned the rights to an incredibly innovative technology called Magnetic Secure Transmission (MST).

When most people think of "gaming computers," they're probably thinking of Windows-based PCs. They offer a huge variety of devices with better equipped software and hardware for a cheaper price, and there are more available games than there are for OS X-based systems.

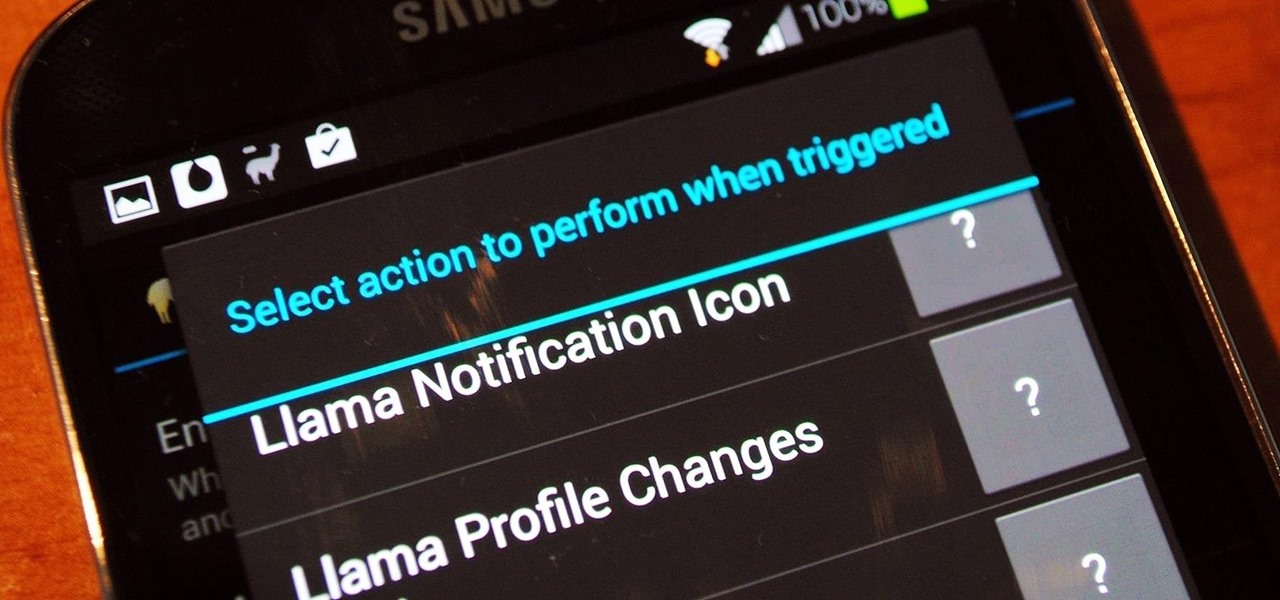
Welcome back, my novice hackers! Previously in my "Spy on Anyone" series, we used our hacking skills to turn a target's computer system into a bug to record conversations and found and downloaded confidential documents on someone's computer. In this tutorial, I will show you how to spy on somebody's Internet traffic.

NOTICE: Ciuffy will be answering questions related to my articles on my behalf as I am very busy. Hope You Have Fun !!!

No one wants to appear stupid. Whether you rely on lengthy, complicated vocabulary to show your smarts, or enjoy highlighting your speedy mental math skills, everyone prefers emphasizing intelligence over hiding it.

While most of us don't think twice about dragging a pattern or using Touch ID to open our phones, or entering a password in for our email and bank accounts, these features are there to protect some of our most private information. Only problem is, they don't do a good job of it.

As great as the Internet is, it is not without its dangers. Hackers at any time may be breaking into your online accounts and compromising your sensitive information. Last year, hackers broke into Facebook, Gmail, and Twitter and made off with 2 million stolen passwords.

We all know that it's important to drink water regularly throughout the day. After all, it has so many benefits, including flushing toxins out of the body and maintaining kidney health and good bowel movements. Turns out that's only part of the story. While being properly hydrated is key to maintaining overall health, it's also a big component of maintaining and even increasing cognitive ability. Plus, drinking enough water regularly can help you lose weight, if you know when to drink it and ...

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

From amateurs to professionals, DSLR cameras are the standard weapon of choice for most photographers. If you own one, then you probably know how expensive of a hobby photography can be. A good starter camera can run between $400 and $500. Then there are accessories like tripods, lenses, filters, and memory cards that can slowly empty out your wallet.

Automation is everywhere in our daily lives. Faucets and hand dryers that turn on for you when they detect your presence. Automated teller machines to handle your bank account. Timed sprinklers to water your lawn every morning. DVRs to record your favorite TV shows when you're not home.

When you're using vacuum power, moving water, or compressing air, it's more than likely being done with some sort of pump. I'll be needing a pump for some of my future projects, so in this tutorial, I'll be showing you how to make your own customizable PVC hand pump that will let you do all three.

Deep in the crevasses of the Songshan mountain range, an Indian dhyana master established the first Shaolin Monastery in 477 AD, seeking to spread the relatively new teachings of Buddha at the time. This monastery then bred the Shaolin monks, who are now popular for their incredible feats with Chinese martial arts, particularly with Shaolin Kung Fu.

There's something special about Laika Inc.'s Paranorman... Hey! Did you love Coraline? Are you interested at all in stop-motion animation? Well, watch this feature on Laika Inc.’s new film, Paranorman.

There are lots of people who want to stay anonymous online, and lots of reasons they want to do this. Staying anonymous on the internet isn't easy, and it's probably possible to trace almost anyone with enough time and resources. A lot of people think that they're completely secure with just one method of cover. For example, a lot of people thought anyone using the Tor network was nearly untraceable, but then things like this often cast doubt on just how secure these networks are. Unless you ...

The Paris-based technology conference Viva Technology, which hosted the likes of Apple's Tim Cook and Facebook's Mark Zuckerberg, is now over.

The experience of actually using the HoloLens 2 can be difficult to describe to anyone who hasn't had a chance to directly interact with the device in person and be blown away by its immersive capabilities.

The COVID-19 pandemic has increased the demand for virtual and remote collaboration, and Microsoft has a solution that may serve as the catalyst for more such apps for augmented and virtual reality in the near future.

The past year has revealed a gaping hole of opportunity in the world of business called virtual meetings. Some existing players like Zoom hopped on that opportunity, while others like Skype seemed stuck on the sidelines, and Google Meet just managed to catch up in time to snag some of the shift in remote work.

You won't have to ask Santa for holiday-themed augmented reality experiences, because practically any social and shopping app that offers AR effects has them available now.

When learning Wi-Fi hacking, picking a compatible Wi-Fi network adapter is the first step to learning to crack Wi-Fi passwords.

As government officials scramble to contain the new coronavirus outbreak with bans on large gatherings, travel restrictions, and school closures, the rest of us have to worry about how we're going to safely purchase water, toilet paper, groceries, and other household goods during the global COVID-19 pandemic.

When Facebook launched its first hardware products last year, the Portal and Portal+ smart displays, the company mostly touted its video-calling features as it faced off against Amazon and its Echo Show.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

With a tiny computer, hackers can see every website you visit, exploit services on the network, and break into your Wi-Fi router's gateway to manipulate sensitive settings. These attacks can be performed from anywhere once the attacker's computer has been connected to the router via a network implant.

Here at Next Reality, our typical approach to all things augmented reality involves vision combined with remote control, either via a handheld device, gaze control, or hand/finger tracking.

Setting up a new Android phone can be a pain. Although Google has some automated features, it does not restore everything. When it comes to transferring certain types of data like files and SMS logs, it's even trickier. By following our steps, you can be sure that you all your data will follow you to your new device.

Security-minded users can reduce the risk of phishing by enabling Advanced Protection on important Google accounts, requiring a U2F security token to log in. Using these keys isn't intuitive on most popular smartphone platforms, and you can find yourself locked out if you don't plan ahead. You'll need to learn and practice using U2F keys on your device before enabling this layer of security.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

In October of 2017, Mathy Vanhoef released "Key Reinstallation Attacks: Forcing Nonce Reuse in WPA2." This paper demonstrates a way to decrypt traffic on practically any WPA2 network, the most commonly used form of wireless security (seeing as all other forms of Wi-Fi encryption have already been broken). Practically all of the network-connected devices we use will need to be updated in some way in order to protect against this vulnerability, each of them in a different way.

When we are building programs that communicate over a network, how can we keep our data private? The last thing we want is some other lousy hacker sniffing our packets, so how do we stop them? The easy answer: encryption. However, this is a very wide-ranging answer. Today we're going to look specifically at how to encrypt data in Python with dynamically generated encryption keys using what is known as the Diffie-Hellman key exchange.

Walsh, a new community under construction on 7,200 acres of former ranch land near Fort Worth, Texas, will one day contain 15,000 homes.

The Galaxy S8 has finally touched down, and it's an absolutely gorgeous device. Samsung's brand new flagship comes jam-packed with new features — some refined, and some that aren't. Luckily, we've compiled some major features to help you get started as quickly as possible so you can go about the rest of your day and show off your shiny new S8 to friends and coworkers.

For years, smartphone makers have been caught up in a megapixel spec race to prove that their camera is better than the next guy's. But we've finally come to a point where even the lower-end camera phones are packing more megapixels than they need, so it's getting harder to differentiate camera hardware.

I've been an Android user almost as long as the operating system has existed, so when I received my first iPhone in April, I felt like I was in a foreign land. Sure, it runs most of the apps I'm used to, and the phone itself feels about the same in my hand as any similarly-sized device, but everything else is just different.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.

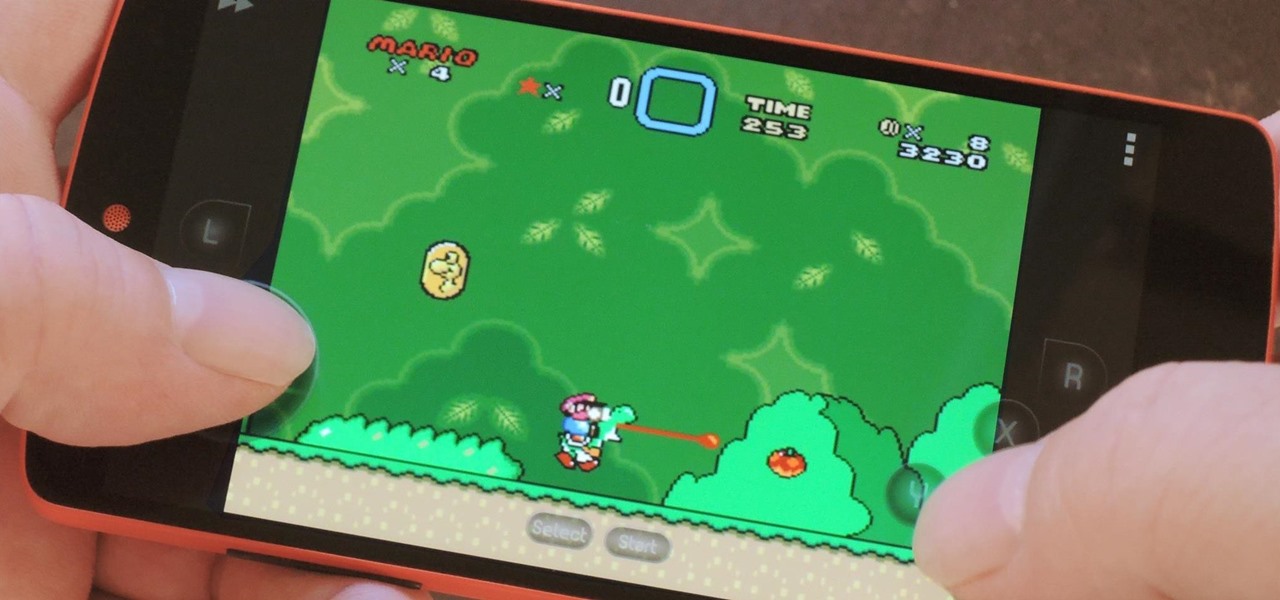
Smartphone games are getting pretty good these days, but they still can't beat the retro appeal of a good emulator. I mean, who wouldn't want to have their all-time favorite console and arcade games tucked neatly in their front pocket? Classics ranging from Super Mario Bros. to Pokémon can all be played at a silky-smooth frame rate on today's devices if you can just find a good emulator to run them on.

The ability to make a meal for yourself used to be one of those life skills you had to learn or otherwise you would starve, but the rise of convenience foods, takeout, and other aspects of modern living have made it entirely possible to be a grown person and not know what to do in the kitchen.