When playing word association with Star Trek, the first thing to come to mind with regards to augmented reality is likely Holodeck, not The Game, an obscure episode from season five of Star Trek: The Next Generation.
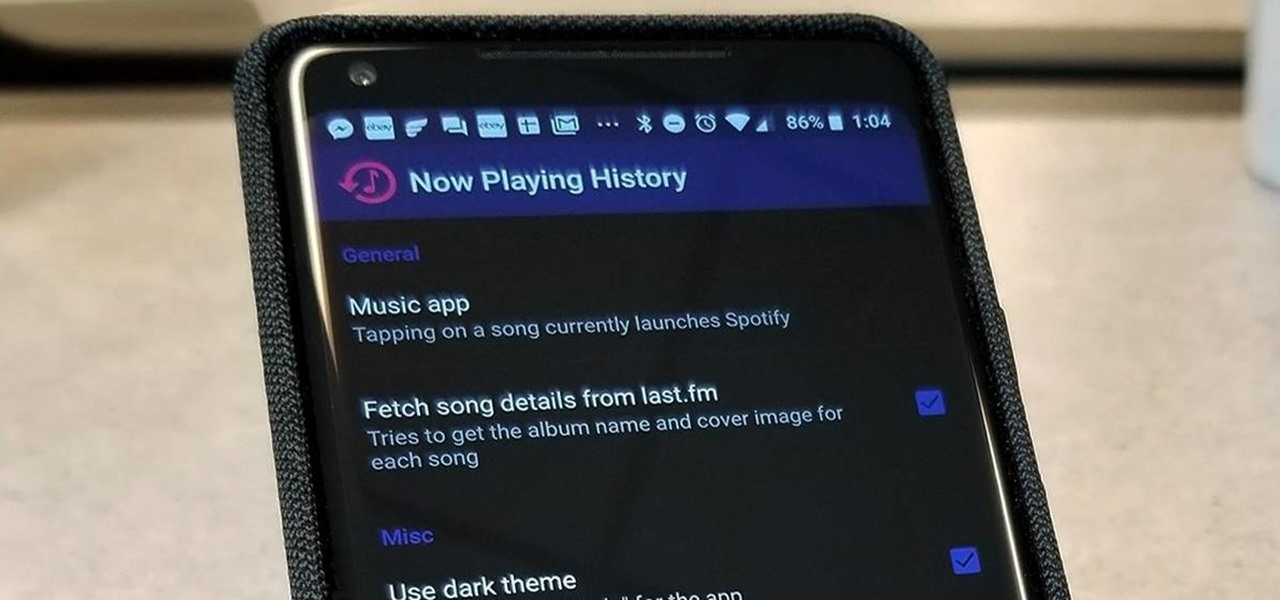
The Pixel 2 has a number of new unique features. One of the most interesting is the Now Playing option to identify songs you hear on a daily basis. Now Playing displays the artist and title of songs playing in the background of your day and shows this information on the lock screen. While this functionality is incredibly useful, the song history is not saved anywhere on your phone.

Augmented reality developer Blippar has created a new visual positioning service based on computer vision that is two times more accurate than GPS in urban locales.

Uber has lost market share to Lyft, its main competitor. Uber's US market share dropped from 84% to 77% between January and the end of May this year, and the ride-sharing company has continued to run into legal, public-image, and internal trouble. Lyft, on the other hand, has been growing.

The list of HoloLens applications continues to grow as more companies discover ways to enhance their operations using augmented reality. Air New Zealand is the latest to show interest in the technology, demonstrating their vision for AR in a new concept video.

Apple staff will be put through their paces now that the company's "Automated System" for driverless cars is in motion.

Every party has a pooper, and that's why you're reading this article. We don't mean to be a downer on such a fun day as 4/20, but it's important to make sure you know about the source of your pot, especially if you're one of the 2,299,016 people who use medical marijuana in the US.

Google's Pixel smartphone is striking up some heated competition between phone makers HTC, LG, TCL, and Coolpad, as the Pixel 3 gets ready to release in 2018. Yep, you heard that right—not the Pixel, not the Pixel 2, but the Pixel 3—which shows that Google is really committed to the future of its new flagship line.

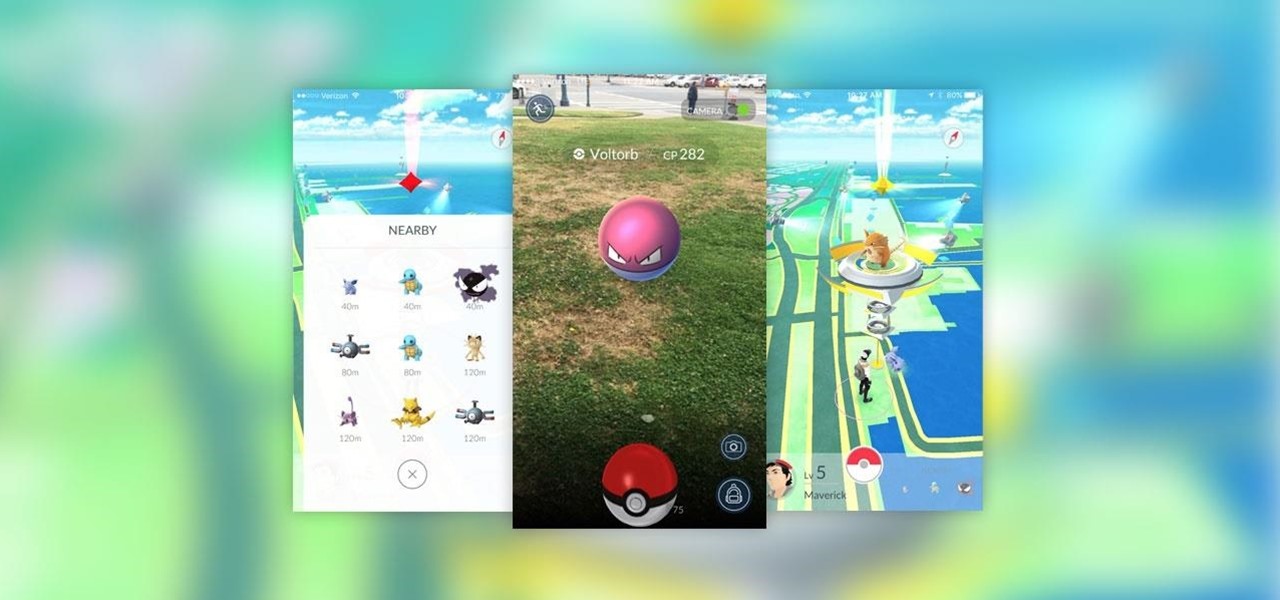
Pokémon Go takes the popular franchise and brings it into the real world through augmented reality, allowing us to play the game while exploring our physical environments at the same time. It doesn't just put pocket monsters into a more realistic context, but it changes the game in some major ways that may delight some players... and upset others.

In Minecraft 1.9 New Command Blocks can be used to make elevators. You types different commands to achieve controlling the elevator for movement you like. This tutorial tells in Minecraft 1.9 how to use command blocks to make elevator. Lets just have a look at it!

Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.

Rooting is a great way to unleash your device's full potential, but not everyone's comfortable with it. Rooting can void a warranty, cause issues with certain apps, and the process itself can be tricky for older devices. Alas, most of the great apps or mods out there require root access, like the ability to utilize a built-in KitKat feature known as Immersive Mode.

If you work at a large office or have a multi-story home, you're probably familiar with Wi-Fi range extenders. Since one hotspot isn't always enough to cover an entire area, Wi-Fi repeaters are generally set up in larger areas to capture and rebroadcast the original signal.

If mainstream media has taught us anything, it's that being beautiful can get you ahead in life. The notion isn't necessarily correct, but it's what the general consensus accepts and it seems to hold quite a bit of weight (no pun intended) in the western world.

I collect straight razors from the Victorian era and then add some steampunk style. Step 1: Remove the Old Scales

If you're a Breaking Bad junkie who can't wait for the next episode, satisfy your craving with a little at-home chemistry and make some blue DIY smash-glow crystals! No, this is not Walter White's so-called "Big Sky" or even the subpar cringe-worthy product of his competitors. It's not even the same kind of crystals, otherwise you wouldn't be reading this. This is totally legal, even kid-friendly if you play it safe, though it actually requires more safety precautions than the potassium nitra...

Earlier this week, Spiderlabs' vulnerability researcher Jonathan Claudius discovered a key in Windows 7 and 8 registries that makes it easy for anyone with physical or remote access to a computer get a hold of the user's password hints. When the "UserPasswordHint" key is read, the hints are displayed as a code that looks encrypted, but Claudius noticed a pattern of zeroes that could be easily translated back to plain text with a decoder he made in Ruby. He added this functionality to the Meta...

In the following video, I demonstrate how to create a device capable of charging the body of anyone who wears it with static electricity, allowing a powerful shock to be discharged into anything that is touched. This grants the wearer the ability to do some pretty amazing things, some of which are shown in the first segment of the video.

In this video, Jeff Cavalier demonstrates how the viewer can obtain six pack abs in just twelve weeks while training at home. He begins by explaining that he will show the viewer five separate work outs techniques. The first exercise is called a X-man crunch. To complete this exercise you must lay on your back, with your body in an "X" shape. You then tighten your stomach muscles and bring your legs and your arms together towards the middle. The second exercise is called Heels to the Heavens....

Need a new iPhone app? Check out Comets and Craters, a new iPhone tower defense strategy game. These ten video tutorials cover all of the gameplay troubles you may have. Steve explains the features and gameplay to help you get the most out of playing Comets and Craters on your Apple iPhone. For those more seasoned Tower Defense players, the video's also provide some insight regarding scoring, upgrades, plus Tower and Enemy capabilities.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

If you've read any health news in the past year or so, you've probably been bombarded with headlines announcing that frequent sitters face certain death, even when you're just relaxing and watching TV at home.

A pyramid is a three-dimensional figure with a polygonal base and a vertex. The base can be a triangle, quadrilateral, pentagon, hexagon, or other type of polygon.

This video shows you how to easily divide proper fractions. In the first step, you have to calculate how many times does the denominator fit into the numerator. You need to divide the numerator by the denominator. If the denominator does not fit into the numerator, you have to write 0, followed with a point, at the top of the calculation ("0."). Next, you add a 0 next to the numerator (multiply it by 10). Now, you have to calculate how many times does the denominator fit into the numerator ag...

For all the benefits 5G brings to cellular data, it isn't without weaknesses, the biggest being privacy. Yes, the latest standard comes with breakneck downloads speeds up to 4.3 Gbps, but at what cost? Like with all things on the internet, 5G devices open opportunities for both good and bad actors.

As the demand for realistic volumetric video for AR experiences begins to grow (along with the available facilities and services for capturing it), researchers at Google have figured out how to improve upon the format.

The legal drama surrounding Chinese startup Nreal and Magic Leap continues, and now we finally have an update.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

The long guarded veil of mystery surrounding Magic Leap for years was finally lifted last year when the company revealed its Magic Leap One device.

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

After building its business on virtual reality, Jaunt is leaving the technology behind to focus on building tools for creating augmented reality content.

One of the first steps in reconnaissance is determining the open ports on a system. Nmap is widely considered the undisputed king of port scanning, but certain situations call for different tools. Metasploit makes it easy to conduct port scanning from directly inside the framework, and we'll show you three types of port scans: TCP, SYN, and XMAS.

After gaining access to a root account, the next order of business is using that power to do something more significant. If the user passwords on the system can be obtained and cracked, an attacker can use them to pivot to other machines if the login is the same across systems. There are two tried-and-true password cracking tools that can accomplish this: John the Ripper and Hashcat.

Users of Epson's smartglasses can now tell their devices to "talk to the hand" when it comes to passwords and authentication.

While Instagram users can attach links to images, they can only do so in stories, and only if they meet the special requirements that most users cannot obtain. Snapchat, on the other hand, lets anyone add a link, and it can be done in regular snaps and in your story. This feature has only been around since July 2017, so you may have missed it and not even realized it was a possibility.

While playing Fortnite Battle Royale, you may have noticed a few players wearing different outfits or using fancy dance moves. These are cosmetic items that can only be obtained by unlocking them. However, unlocking items in Fortnite is a little different than many free-to-play games.

Business cards are a great way to keep tabs on the contacts we network with. So why shouldn't our smartphones make them even more useful? Enter Google Lens, which will help you save, search, and expand on the contact information found on all of the business cards you've collected.

The Pixel 2's camera is one of the best you'll find on an Android phone. Among its standout features is the incredible Portrait Mode, which Google accomplished with some impressive software processing. Thanks to a few clever developers, you can now enjoy the Pixel 2's Portrait Mode on your Galaxy S8 or Galaxy Note 8.

Thanks to Metaverse, it has never been this easy to create your own AR game.