PowerShell Empire is a post-exploitation framework for computers and servers running Microsoft Windows, Windows Server operating systems, or both. In these tutorials, we will be exploring everything from how to install Powershell Empire to how to snoop around a target's computer without the antivirus software knowing about it. If we are lucky, we might even be able to obtain domain administrator credentials and own the whole network.

Hello all! In this tutorial, I'd like to show you one way of getting root on OS X. Check out this GitHub page for a recent privilege escalation exploit that was recently discovered. I've tested it and it works on both OS X 10.9 Mavericks and OS X 10.10 Yosemite, but appears to have been patched with OS X 10.11 El Capitan. If you check out the file main.m you can see where most of the magic is happening. This source code can very easily be changed to make it do more than just the system("/bin/...

Spoofed phone calls originate from one source that's disguising its phone number as a different one, and you probably get these calls all the time. Maybe they're numbers from your local area code or for prominent businesses, but the callers are just hijacking those digits to fool you into picking up. Turns out, making a spoofed call is something anybody can do — even you.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

Privilege escalation is the technique used to exploit certain flaws to obtain elevated permissions relative to the current user. There are a vast number of methods out there to go from user to root on Linux, and keeping track of them all can be difficult. This is where automation comes into play, and a privilege escalation script called Linux Smart Enumeration is one to take advantage of.

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

Secure Shell is one of the most common network protocols, typically used to manage remote machines through an encrypted connection. However, SSH is prone to password brute-forcing. Key-based authentication is much more secure, and private keys can even be encrypted for additional security. But even that isn't bulletproof since SSH private key passwords can be cracked using John the Ripper.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

The internet has undoubtedly changed the way we work and communicate. With technological advances, more and more people can collaborate on the web from anywhere in the world. But this remote-friendly environment inherently brings security risks, and hackers are always finding ways to exploit systems for other uses.

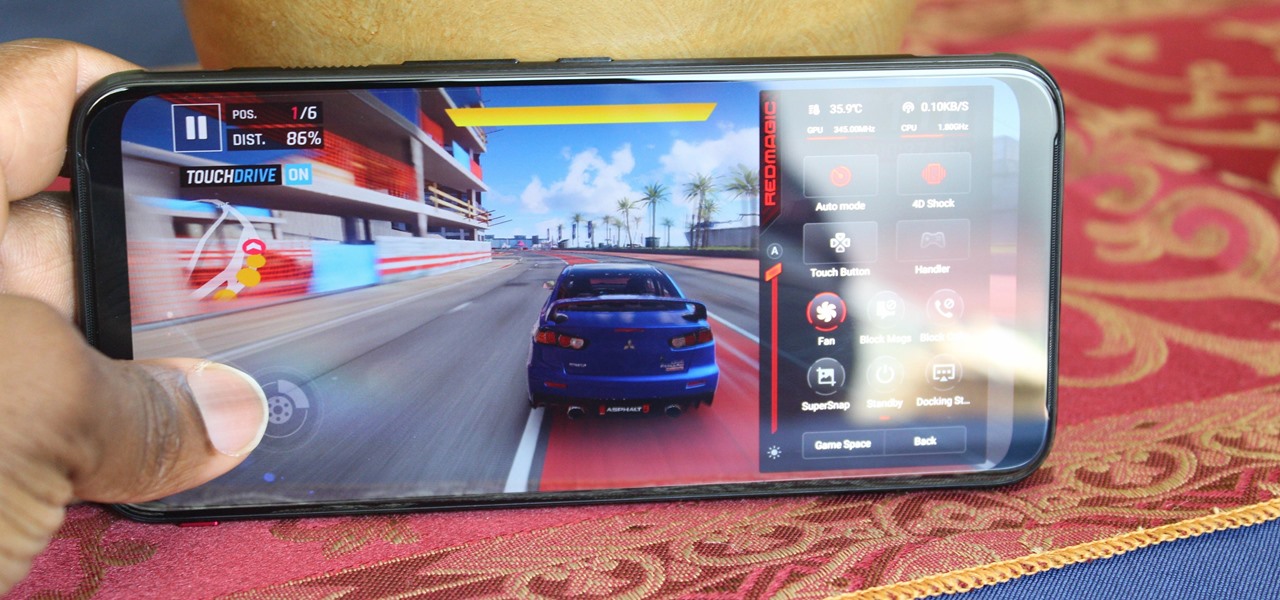
Mobile gaming has exploded in recent years, with experts predicting 2.4 billion global mobile players by the end of 2019. It already accounts for 47% of the worldwide gaming market, besting console and PC. No wonder we've seen the rise of gaming smartphones, a class of phones that specialize in mobile gaming.

One of the most exciting things as an ethical hacker, in my opinion, is catching a reverse shell. But often, these shells are limited, lacking the full power and functionality of a proper terminal. Certain things don't work in these environments, and they can be troublesome to work with. Luckily, with a few commands, we can upgrade to a fully interactive shell with all the bells and whistles.

While photography usually gets all the love, our phones have gotten really good at capturing video. Think about it — when was the last time you needed a camcorder for a vacation? With mobile cameras getting better each year, we're now at a point where smartphones can be used for pro-level videography.

There's a lot of misinformation about VPN services, and it stems from the fact that not all of them are created equal. Some focus on privacy, others on security, and a few VPNs are seemingly even purpose-built for the polar opposite: data collection. We made this guide to help clear the air on some of these issues while objectively ranking the best of the best.

Rooting. As an Android user, I'm sure you've heard the word once or twice. According to Kaspersky, 7.6% of all Android users root — but for the 92.4% who don't, we wanted to talk to you.

After a long hiatus, we shall once again emerge from the shadowy depths of the internet to build an exploit. This time, we'll be looking at how to defeat a non-executable stack by using the ret2libc technique — a lean, mean, and brilliant way of exploiting a stack overflow vulnerability.

A PirateBox creates a network that allows users to communicate wirelessly, connecting smartphones and laptops even when surrounding infrastructure has been disabled on purpose or destroyed in a disaster. Using a Raspberry Pi, we will make a wireless offline server that hosts files and a chat room as an educational database, a discreet local chat room, or a dead-drop file server.

The private automobile has been an intrinsic part of our lives for around a hundred years. But over the last decade, car sharing has gained a very small but growing part of the mobility market. The more recent rise of companies like Uber and Lyft is witness to a more dramatic shift in mobility and car ownership. Private vehicle ownership to a transportation-as-a-service model has already started, and high capability SAE Level 4 vehicles will complete this trend.

No more carrying around heavy laptops and thousands of Linux Live CDs and USBs to always be ready for pentesting on the fly!

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

The latest software update for iPhone has a few new features you should know about, including an enhanced security feature to protect your Apple ID account from phishing and other attacks. Keep reading to see everything new that's included with iOS 16.3 for iPhone.

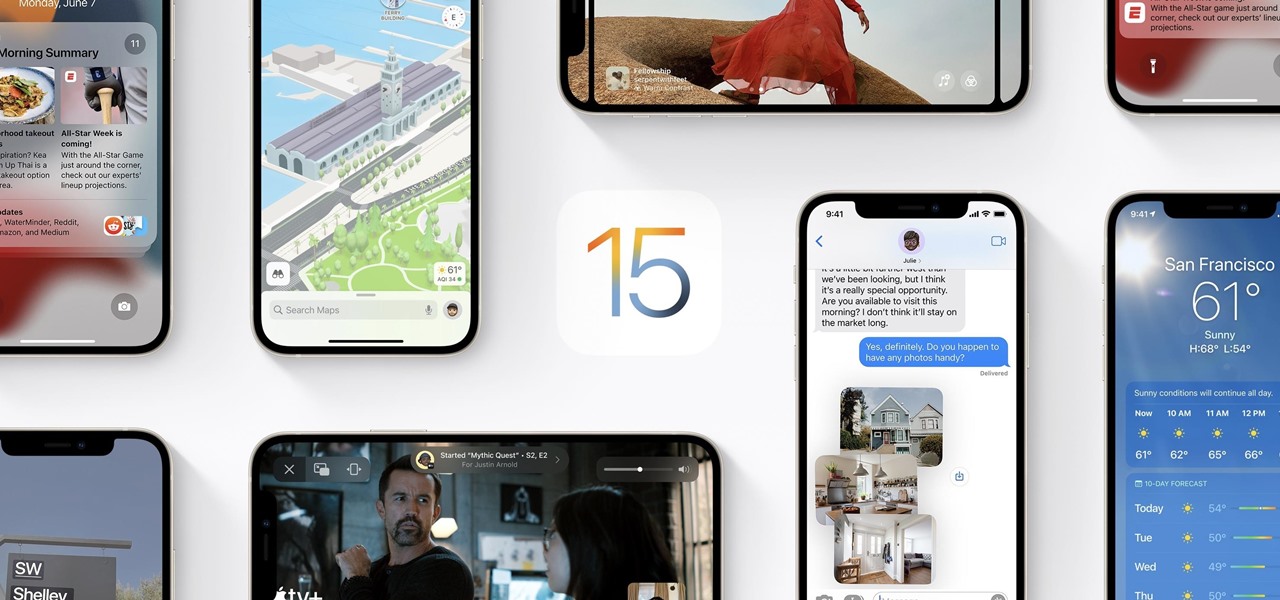
Apple released the second beta for iOS 15 on Thursday, June 24. The update includes FaceTime's "SharePlay" feature for the first time, a new Maps icon, updates to Focus mode, in addition to many other changes and bug fixes.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

Body fat is important to understand when you are dieting. It is good to track your body fat, so that you are not as reliant on the scale. The numbers on your scale are not always accurate. Muscle weighs more than fat and if you are exercising more than usual your physique will get better but your weight may rise. Knowing the difference between fat and muscle will keep you from getting discouraged and hindering your workout. This tutorial will show you how to measure fat for success. Measure a...

When you train, don't just aim to grow big, but rather aim to be functional once you've reached your greatest physique. Weight training isn't only applicable to bodybuilding; it helps you achieve the physique you have always wanted. In the video below, Team Powertec athlete Ian Lauer shares a few tips on triceps training using the Powertec Workbench Multisystem.

One of the key tasks of a nurse is being able to take blood samples, and the only way to get good at the procedure is by practice. Knowing the steps to drawing blood (to go to the lab) is key to both yours and your patient's safety. This interactive video module will help familiarize you with the phlebotomy medical procedure, but is not meant to be your sole method of instruction— always ask for supervision in performing a procedure if you've never done one before, or have little experience.

Six feet long and always hungry, the Humboldt squid, aka the "red devil", is one of the most dangerous yet intelligent predators of the deep. This incredible squid has 3 hearts, keen eye sight, a giant brain, 2 lightning fast tentacles, 8 grasping arms and razor sharp teeth. The red devil squid come out at dusk. They come up from 2300 feet to 200 feet. Obtain information abut the Humboldt squid (red devil).

Earlier we've looked at starting off in Survival mode, plus simple combat. Now we look at a more refreshing aspect of Minecraft: Food!

This video will show you something neat you can do with some easy to obtain acid, and it is a great science project. Have fun with acid.
Leaked documents from the 1966 Bilderberg Group conference exclusively obtained by Infowars betray how even as far back as five decades ago U.S. Senators were being indoctrinated with the belief that “nationalism is dangerous” by Bilderberg elitists, in addition to top union heads scheming behind their members’ backs with titans of capitalism and industry.
On Sunday U.S. Secretary of Defense Leon Panetta said the United States is “ready from a military perspective’’ to attack Iran under the guise of preventing it from obtaining nuclear weapons.

The 'It's Good!' achievement and trophy available on the Xbox 360 and PS3 versions of Rage is obtained while driving the ATV in the game. You will need to jump through 3 different posts located at the Ark Emergence site, the Bash TV station, and the Northern Watch tower. This video tutorial will show you where to find all of them.

Crafter Dawn Huntington shows how to make felted baby bibs. Materials needed are 8 1/2-by-14-inch sheet of freezer paper, felt, ink-jet printer, small binder clips, snaps and a templet which can be obtained from the article part of this video. Make baby bibs.

Ever need to separate out your tea and water? Learn how to easy obtain this goal using a simple technique. Water can be separated from tea if you follow these steps. Separate tea and water.

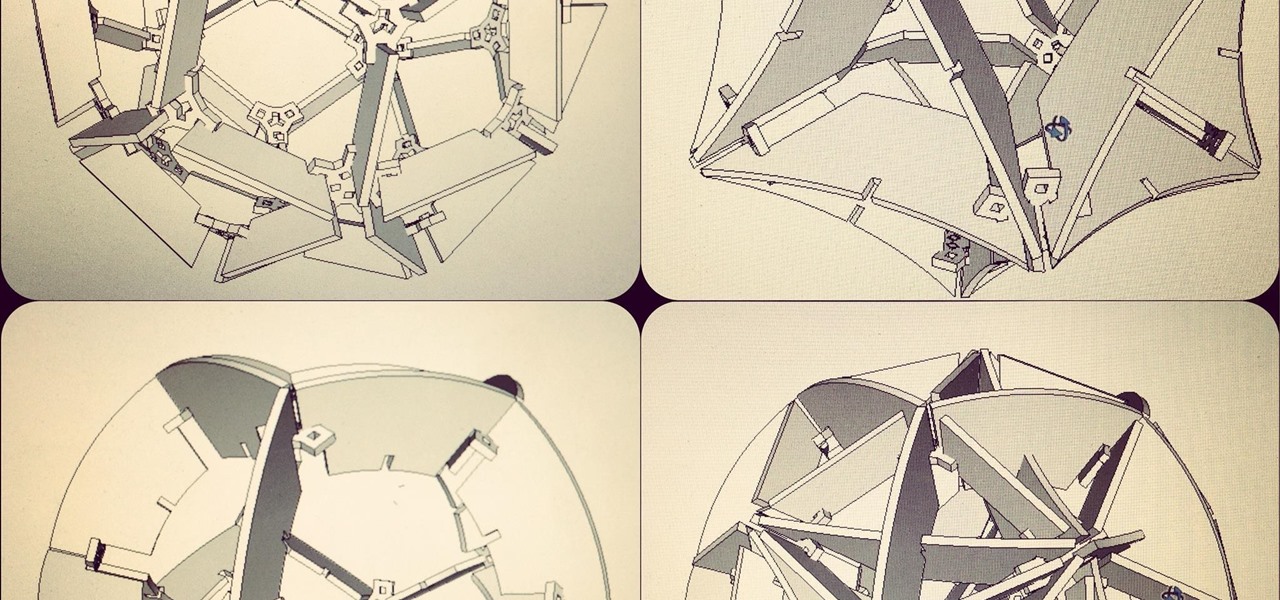
These drawings were made with Google SketchUp. There is a dodecahedral model, icosahedral model, and a third I don't know the name of, made of rhombic faces obtained by connecting vertices of the other two. The final image is all three models together. I'll use a ShopBot CNC router to cut out the pieces this week.

In this video tutorial, CreativeCOW contributing editor, Nelson Fernandes demonstrates a method to obtain a quick and dirty mask using the find edges effect combined with the auto-trace feature.

Give a vintage look to your footage similar to that obtained from LOMO Cameras. Originally LOMO cameras are still cameras that are used for causal cheap photography. But the photographs obtained from such cameras have a unique look to it. In this tutorial you will learn to digitally manipulate cross-processed LOMO effect and add it to your video footage.

Many communities obtain their drinking water from underground sources called aquifers. If a surface water source, such as a river, is not available, water companies will drill wells into the soil and rock to a water source below. Some homes have their own private wells and must tap into the same ground water sources. In this video tutorial, you'll what aquifers are, how they work, why they are important and, of course, how to build your own model! Build your own aquifer.

Need to know how to use your Texas Instruments graphing calculator for your college math or statistics class? You're in luck... watch this video tutorial to see how to use ANOVA with a TI-83 graphing calculator. What is ANOVA? One-way Analysis of Variance.
Back in Backtrack5 there was a nice GUI addon for the aircrack suite called feedingbottle. I liked it because it simplified easy tasks like fake auth with a click of a button. I was hunting for sources and it seems that all I could find was an ubuntu deb package from 2013. It was a little tricky installing it on a 64-bit system so I thought I would write a quick how to. Feedingbottle is an x86 package so you must install the corresponding libraries. If they are missing you will get a "bash:.....

If you're a frequenter of Null Byte, I bet you have at least some interest in information security. Furthermore, you have a hobby that if applied in certain ways, will get you arrested. I've received quite a few messages from the community here about federal cybercrime law and how it applies to them, so I decided to get together with my lawyer to come up with some answers.