
News: Meta's Latest Mixed Reality Headset Sets a High Bar
Microsoft enjoyed a few months in the spotlight after releasing the developer version of the very first mixed reality (MR) headset, but now we're starting to see the competition jump in.


Microsoft enjoyed a few months in the spotlight after releasing the developer version of the very first mixed reality (MR) headset, but now we're starting to see the competition jump in.

There are a million (okay, slight exaggeration) ways to peel an egg, and countless numbers of tips, tricks, and hacks that are supposed to make that deviled egg appetizer you agreed to make for the party an absolute snap. More often than not, though, experiences vary... and pock-marked, greyish-yolked boiled eggs find their way into your collection whether you like it or not.

Coffee is a topic that everyone has a strong opinion about, especially when it comes to brewing the perfect cup. Even if you buy the best beans and grind them yourself, chances are you're skipping one necessary step to make sure your coffee tastes the best it can: cleaning your coffeemaker the right way.

Camping in the rain sucks. It's not enough to deal with your clothes and tent being soaked—it makes starting a fire nearly impossible if you're not carrying waterproof matches. You can buy them pretty much anywhere that sells camping gear, but if you've got regular matches and a candle at home, they're just as easy to make yourself..

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Shark jumps Steampunk, experts unsure of the meaning. Cape Town -- In an unprecedented move today, a Shark have jumped a steampunk couple as they were attempting to work on their hobby steamboat.

UPDATE (February 26, 2014) Yesterday, the U.S. House of Representatives passed H.R. 1123 with a 295-114 vote decision. The ruling repeals the 2012 Library of Congress (LOC) decision that limited the ability to legally "unlock" your smartphone (see below).

You may or may not care about this, but sometimes it physically upsets me when I see gears stuck together haphazardly, with no concern for whether their teeth interlock. I mean, what do you do with non-interlocking gears?
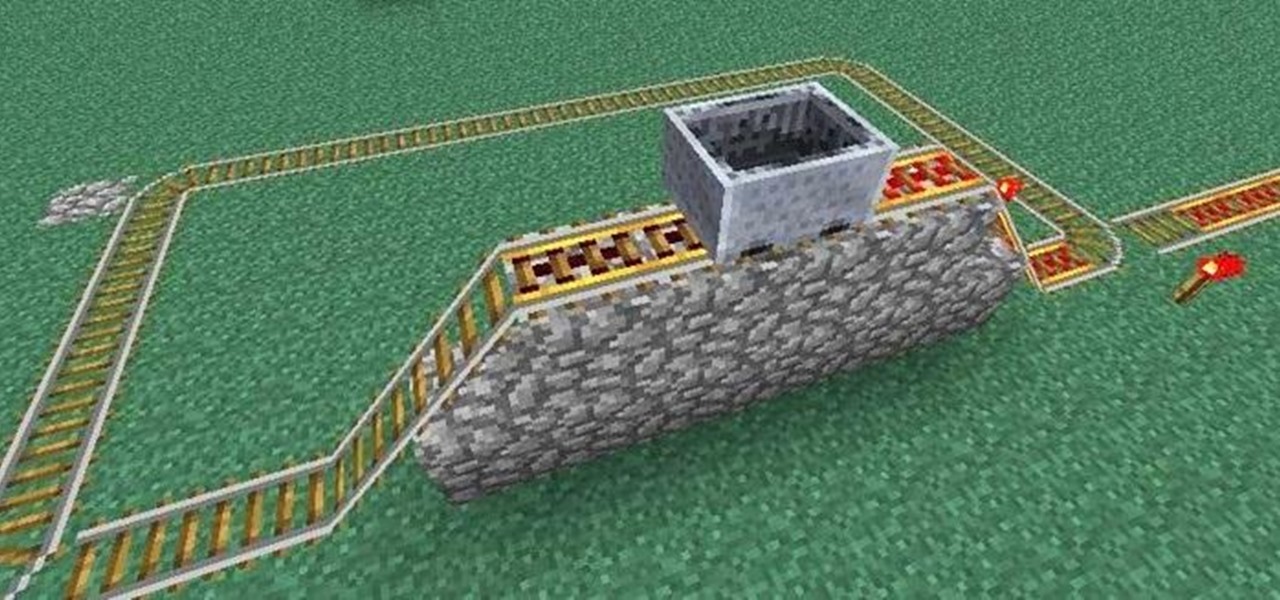
What's nice about Minecraft 1.3 is that it makes minecart stations so simple. Before, you needed redstone and buttons and powered rails in order to make a good minecart station. Now you hardly need anything at all! That said, if you want to be snazzy, all of the minecart stations we covered in this earlier article are still completely functional. You may also want to check out this article on how to make empty minecarts come back to you, if you want some extra bells and whistles.

Everybody should have plants in their home. Not only do they give off oxygen, but they add a whole new level of decor and awesomeness to an otherwise drab room. So naturally, if you want to improve a room, just display a few plants.

Find out how everything in a chemistry lab works, from pipettes to burners to recrystallization to storage. You'll get precise instructions on how to work and perform certain scientific duties in the chem lab, whether it's chemical or just ordinary high school science.

For anyone who lives in a space that may frown upon making holes in the walls, or for anyone who may not want to take on such a task, there's a simple alternative to hanging curtains or drapes. And the answer is brilliantly simple.

While there's an art to surviving the all-nighter, there's also an art to staying awake throughout the day when you're operating on little to no sleep. In 1964, the record for sleep deprivation was set by 17-year-old Randy Gardner, who stayed awake for an incredible 264 hours and 12 minutes. Now while we're not out to challenge Randy for his title, we can certainly look to him for inspiration in beating back our own fatigue.

Peter Fiduccia from Field and Stream explains how to use the tending grunt sequence when hunting deer. The tending grunt is a grunt made by a buck when following a doe. The grunt is made in order to let the doe know that he wants to breed. The key to making the call is to be soft. Bucks don't make this call with aggression or loudly. The first step is to take the call and cup your hand around the end. Blow gently into the call. For more resonance in the call, grab the call with both hands at ...

Safari has a convenient "Find" feature to search for specific words and phrases in a webpage, and Apple Books has a similar feature for e-books and PDFs. But those do nothing for you when searching text in the real world. Hardcover and paperback books are still very much a thing, as well as paper-based documents, and finding what you need is as simple as pointing your iPhone's camera at the page.
In the lead up to the Magic Leap One launch, Magic Leap has been coy about what the actual field of view (FoV) is for its first commercial product.

Now that we've had a chance to jump into the Lumin SDK documentation at Magic Leap's Creator Portal, we now have much more detail about how the device will function and utilize software than any single piece of content released by Magic Leap to date.

JavaScript is one of the most common languages used on the web. It can automate and animate website components, manage website content, and carry out many other useful functions from within a webpage. The scripting language also has many functions which can be used for malicious purposes, including stealing a user's cookies containing passwords and other information.

Every year, football fans get excited about the next crop of blue chip prospects joining their teams, from five-star high school recruits graduating to college to first-round rookies drafted into the NFL.

While IKEA is collaborating with Apple for its ARKit furniture app, Marxent is ready to help the rest of the interior decorating and home improvement crowd with their apps.

An older man dies of Zika. A younger man who cares for him catches Zika — but doctors cannot pinpoint how the disease was transmitted. While proximity to the patient is sufficient explanation for the rest of us, for microbe hunters, it is a medical mystery. Why? Zika is not known to transmit from person-to-person casually.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

Peach trees and other related plants are susceptible to the devastation caused by fire blight, a contagious bacterial disease. Once contracted, infected trees have to be burned to contain the disease and prevent spread to nearby trees. Increasing resistance to antibiotic treatment has sent scientists in search of alternative ways to deal with the bacteria and prevent its catastrophic damage.

A vulnerability in the design of LiDAR components in driverless cars is far worse than anything we've seen yet outside of the CAN bus sphere — with a potentially deadly consequence if exploited.
I currently am and have always been what one might call a PC/Android guy. Many that know me well would likely even go so far as to say I am anti-Apple. About an hour after seeing the ARKit demo during the day-one keynote at WWDC, I became the owner of a brand new Mac.

The Massachusetts Department of Public Health (DPH) issued a health alert for a Boston mumps outbreak, on Monday, June 5th, to healthcare providers and local boards of health. There have been 12 reported cases of mumps during the recent outbreak. The affected residents' symptoms occurred between March 24th and May 31st, and 10 of the 12 had symptoms after May 9th. There have been 35 confirmed cases of mumps in 2017 in Massachusetts, and "nearly 300" suspected cases in the continuing outbreak.

We fight cancer in a variety of ways, but no matter whether drugs, biologics, or our immune cells are part of the battle, they can do a better job fighting back cancer if we can help them find the tumors.

By looking for the mechanism that allows influenza A to invade lung cells, scientists also discovered a treatment that might block the virus from taking hold there.

BlackBerry has formally announced the arrival of its flagship, the KeyOne, during Mobile World Congress 2017 in Barcelona. The all-Android KeyOne looks distinctly BlackBerry, with its 4.5" screen and physical QWERTY keyboard. Here's the lowdown on this elegant handset that hearkens back to BlackBerry's heyday, which had previously been known by its code name, the BlackBerry Mercury. Aluminum Unibody with Physical Keyboard

Whether you are vegan, lactose-intolerant, or cooking for someone who is, standing before the non-dairy milk shelf in the grocery store can be daunting. Instead of playing it safe with the two most common milk alternatives—soy and almond—perhaps you should explore a few other choices that tend to be overlooked.

Managing hard drives in Linux is crucial to understanding your system and its operation as well as understanding the system you are exploiting or conducting a forensic analysis on. Linux has numerous commands that can provide us with information, control, and management of hard drives, and in this tutorial, we will examine a number of the most important ones.

I was a vegetarian from age 6 until age 23. When I started eating meat again for the first time in 17 years, most people I knew (including me) expected me to be pretty conservative about it: chicken breasts, hot dogs, and all the other "basic" meats that everyone loves.

Our attention spans have vastly shortened thanks to the Internet and our subsequent procurement of information from it at a rapid pace. It's tough to pay attention to something for a good amount of time, unless it's ridiculously interesting and stimulating. It's gotten so bad for me that I keep checking my phone every ten minutes—I even did it during a midnight showing of The Dark Knight Rises.
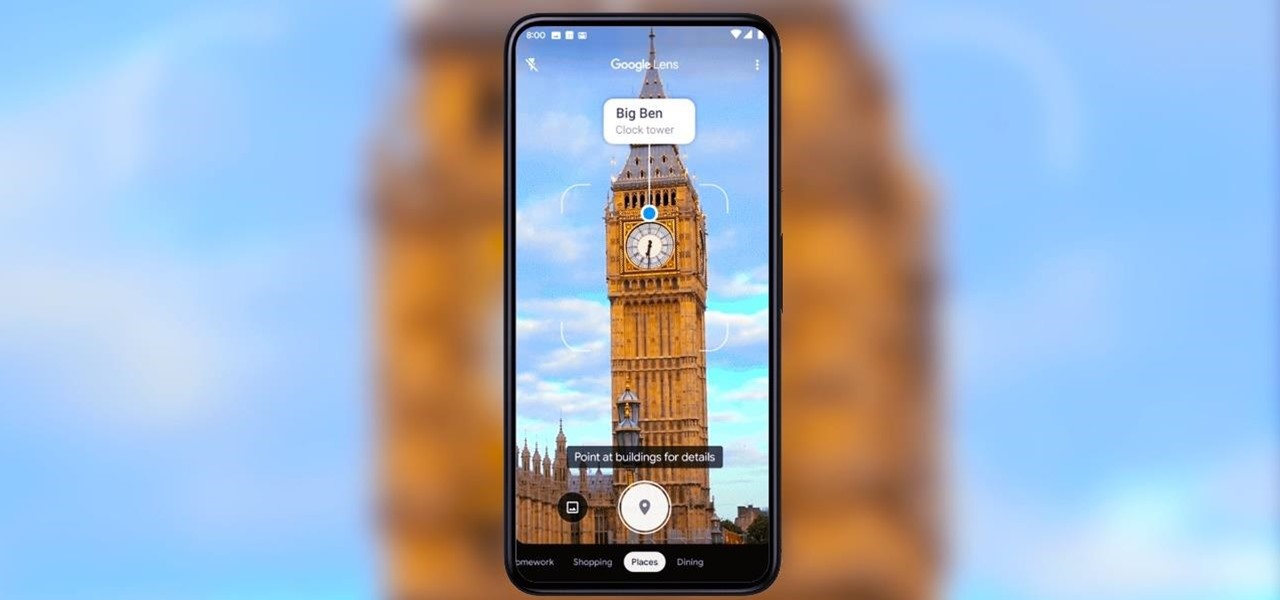
This week, Apple unveiled its own version of Google Lens in the form of Live Text. In response, Google just hit back with a new feature for its visual search tool called Places, a new search category that can recognize landmarks and return information on them within the camera view, which Apple touted as a capability of Live Text during its WWDC keynote.

Regardless of whether you're an aspiring or established coding pro, knowing just one or two programming languages and platforms is no longer sufficient if you want to be truly competitive in an increasingly popular and lucrative field. But before you spend an excessive amount of time mastering six new platforms, do yourself a favor and master Linux.

For some of us, winter puts the brakes on apps like Pokémon GO since smartphone screens usually only respond to bare fingers. Nobody wants to be that guy who caught frostbite chasing a Sneasel. When you use normal gloves, the display's sensor simple doesn't activate, so that doesn't help any. Fortunately, several options for touchscreen-friendly capacitive gloves are on the market to help you through this last blast of winter.

We're nearly done getting our Mac set up for hacking. If you haven't checked out previous tutorials, I'd recommend you do so first before diving right into this one.

I've never had a problem with veggies—we've always been the best of friends—but I do have a lot of other people in my life that have been less than enamored with this basic food group in the past. Some cite the bitter flavor associated with veggies like Brussels sprouts, while others dislike the various consistencies that come with boiling or steaming vegetables such as broccoli or eggplant.

Since I first announced the new Null Byte recognition for excellence a few weeks ago, several of you have written me asking, "How can I study for this certification exam, and what material will be covered on the exam?" Now I have an answer for you. The White Hat Hacker Associate (CWA) will cover 14 domains or areas. Everything you need to know is here on Null Byte. There will be no questions that are not covered here on this site, guaranteed.

Welcome back, my greenhorn hackers! As hackers, we often take for granted that nearly all of our hacking tools and operating system are free and open source. I think it's important to examine a bit of background on how we arrived at this intriguing juncture in the history of computer software. After all, we pay for nearly all of our other software (Microsoft, Adobe, etc.) and nearly everything else we use in life, so how is it that Linux and all our hacking tools are free?