Even if you're a good cook, sometimes home-cooked food just doesn't taste the same as it does in a restaurant. Of course, there are some utensils and appliances in a professional kitchen that the average person doesn't have access to, but it's not just about the tools.

Despite some of the biggest players in tech still lagging in terms of offering smartglasses options, there are nevertheless a number of smartglasses makers, including North and Vuzix, with consumer-grade smartglasses on the market right now.

The pictures we upload online are something we tend to think of as self-expression, but these very images can carry code to steal our passwords and data. Profile pictures, avatars, and image galleries are used all over the internet. While all images carry digital picture data — and many also carry metadata regarding camera or photo edits — it's far less expected that an image might actually be hiding malicious code.

Greetings my fellow hackers.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.

It has been a long while since I last came here to write an article. Graduate school keeps you busy. After I looked over what I had written previously, I decided that I should introduce another fun topic from cryptography. In this case, steganography.

The world of Lego is timeless primarily because everyone, regardless of age or background, can build a wide variety of amazing things with the simple component blocks from the classic toymaker.

You may be familiar with image-based or audio-based steganography, the art of hiding messages or code inside of pictures, but that's not the only way to conceal secret communications. With zero-width characters, we can use text-based steganography to stash hidden information inside of plain text, and we can even figure out who's leaking documents online.

If you're using a mobile device, it's a pretty safe bet that your apps are sending lots of information back and forth from their servers. To make sure there is no inappropriate data collection going on, it's worth setting up a web proxy to spy on this traffic, so you know exactly which apps are "phoning home" and when.

Kali Linux is the obvious first choice of an operating system for most new hackers, coming bundled with a curated collection of tools organized into easy-to-navigate menus and a live boot option that is very newbie-friendly. But Kali isn't the only distribution targeted at pentesters, and many exciting alternatives may better fit your use-case. We've already covered BlackArch Linux, now it's time to talk about Parrot Security OS.

In the aftermath of the unindicted police killings of Michael Brown and Eric Garner, we've been told that the system worked as intended. When our legal system's outcome is at conflict with what a majority of Americans believe is just, it's clear that some changes are needed. But what specifically needs to change? And what can an average citizen with a moral and just cause do to prevent these kinds of tragedies from repeating themselves again and again?

Like theme music, I always feel that I need more fog in my life. Fog can be useful for many reasons—warding off smaller siblings from your bedroom, keeping curious hands out of your cupboard, and tricking your friends into thinking there's something horribly wrong with their vehicle. So, today we'll be making a very simple fog machine for small scale applications.

In less than a month, WWDC, Apple's Worldwide Developers Conference, will reveal the company's plans for the upcoming iOS 18 and iPadOS 18 software updates. But we already know what accessibility features will be hitting iPhones and iPads later this year, and many of them will be helpful to everyone, not just users with accessibility issues.

Apple's iMessage is one of the main reasons to use an iPhone, and there's a lot you can do in chats without being overly complicated. But there's one issue that continues to drive people nuts, and that's the blue typing bubble indicator with the moving ellipsis (•••). Can you stop it? Not officially, but there are workarounds.

If you have Snap Spectacles 3, the dual camera-equipped sunglasses capable of capturing 3D photos and video, by now you've likely jazzed up the videos you've captured on the wearable with Lenses via Snapchat.

Penetration testing, or pentesting, is the process of probing a network or system by simulating an attack, which is used to find vulnerabilities that could be exploited by a malicious actor. The main goal of a pentest is to identify security holes and weaknesses so that the organization being tested can fix any potential issues. In a professional penetration test, there are six phases you should know.

On April 26, 2019, Sinemia posted a note on its website stating it has ceased all operations in the United States. It's not known if it continues to work in other countries or if US users will be getting any refunds, particularly, for annual subscribers.

You can mod every aspect of your phone's software with root, but if you want to make changes at the hardware level, you'll need a custom kernel. If you've looked into custom kernels before, one name undoubtedly kept coming up: ElementalX. It's easily the best custom kernel out there, and the reason for that is its awesome developer, flar2, aka Aaron Segaert.

Many lazy cooks skip rinsing off their grains before they cook 'em, but that's a big mistake for a few reasons. Some grains have coatings on them that need to be rinsed off to cook properly and taste good.

Thought I would cross-post a piece I did a while ago.

When you enable Low Power Mode on your iPhone, it's not always clear what measures it's taking to reduce battery drain and conserve power. Changes to energy-hungry features you use daily may be immediately noticeable, but some things you frequently use may be disabled or reduced without any apparent indicators.

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

Body fat is important to understand when you are dieting. It is good to track your body fat, so that you are not as reliant on the scale. The numbers on your scale are not always accurate. Muscle weighs more than fat and if you are exercising more than usual your physique will get better but your weight may rise. Knowing the difference between fat and muscle will keep you from getting discouraged and hindering your workout. This tutorial will show you how to measure fat for success. Measure a...

When you train, don't just aim to grow big, but rather aim to be functional once you've reached your greatest physique. Weight training isn't only applicable to bodybuilding; it helps you achieve the physique you have always wanted. In the video below, Team Powertec athlete Ian Lauer shares a few tips on triceps training using the Powertec Workbench Multisystem.

If it takes a village to raise a child, you can imagine what it takes to raise a village! In brief: a whole lot! Thanks to the folks behind the Open Source Ecology movement, however, starting your own self-sufficient community has never been easier! Taking free software as a model, the group is working on what they call the Global Village Construction Set—"a fully integrated [and freely reproducible] set of machines for creating a self-sufficient modern life from the resources of a small amou...

Fill half a cup with water or slightly more than half a cup since some water will evaporate on boiling. Pour this water in a steel vessel.

PostSharp is an free, open-source and extensible platform for enhancement of .NET assemblies, that is: PostSharp transforms assemblies after compilation. Pretty abstract, isn't it? Not so much. It has great applications. PostSharp Laos, a Lightweight Aspect-Oriented Solution, provides aspect-oriented programming (AOP) to .NET Developers without the learning curve. This tutorial presents an introduction to the PostSharp programming language, one that's more than sufficient to get you started. ...

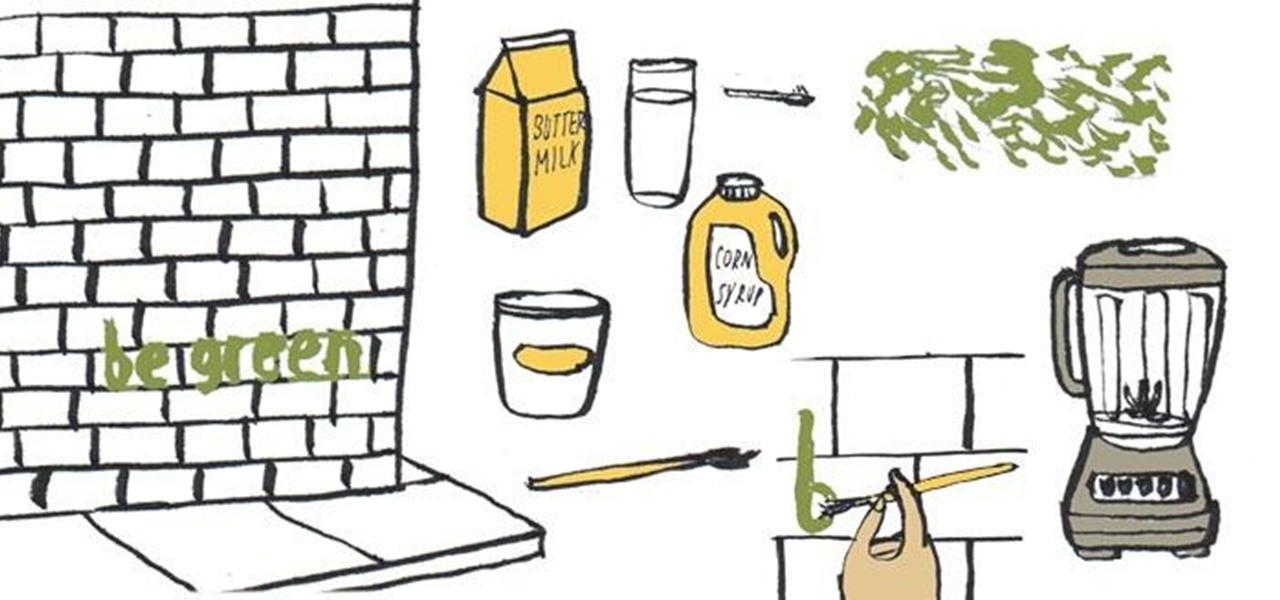
Feeling the need to creatively express yourself in a public space? Make an artistic statement with some DIY moss graffiti using moss, buttermilk, beer, a paintbrush, and some imagination.

This video tutorial will show you the process of drawing blood from rats through the saphenous vein and by cardiac puncture.

Now we're getting to the kids who actually know what's going on. You're more likely to get enthusiasm and dare I say focus from grade school and middle school kids. Here's the lowdown:

CNA skills may vary from state to state. Depending on your state of residence, the skills section of the CNA certification exam will consist of three to five randomly chosen skills.

Competition and cooperation are two modes of interaction that engage us throughout our lives. West LA Seido Karate recognizes the need for being skillful at both. We channel the cooperative instinct in the dojo in a variety of ways, ritual courtesy being the most visible. We also give our competitive nature its due. In weekly sparring classes and periodic tournaments throughout the year, the West LA Seido program provides the eligible student with sufficient opportunities to “test” her or him...

Nasty weather is bad enough when you drive, but if you ride your bike to school or work, it's really not a pleasant way to start the day. And if getting soaked isn't sufficient, a wet commute means your bike chain is going to be caked with mud and all kinds of other gross stuff.

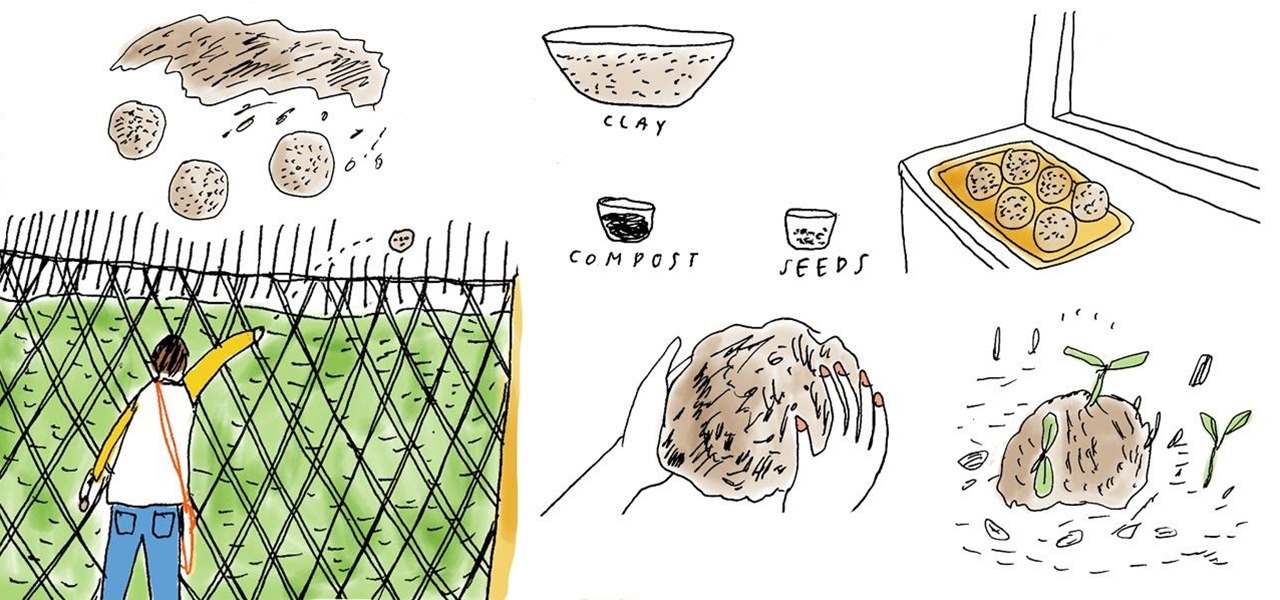
Build up your arm strength and beautify your local community in a single stroke by dropping homemade seed bombs in and around your neighborhood. A guerrilla gardening technique anyone can participate in, seed bombing is a fun and effective way to add tiny oases of wildflowers and healthy green plants in vacant lots and other overlooked and neglected parcels of land.

Eat your heart out, Joey Chestnut. There's a new super-speed-eater in town, and she means business. 45-year-old Hatsuyo Sugawara downed an incredible number of 399 bowls of soba noodles in just ten minutes at the annual All-Japan Wanko Soba Eating Championship this past Sunday. The noodle queen calls herself a food fighter, and has been coined "the witch".

If you love playing those WarCraft and StarCraft strategy games on your PC, chances are you've also heard of a game called League of Legends.

Here's a delicious Byte of information for you. A proof of concept program on Linux was coded to exploit a known bug in how the Linux Kernel (versions 2.6.39+) handles permissions for the

TCP/IP Client / Server Application Hello! Today's blog post will be about coding a very rudimentary Client and Server application duo, which will communicate by using TCP Sockets.