"Facebook is a social utility that connects people with friends and others who work, study and live around them. People use Facebook to keep up with friends, to share links, to share photos and videos of themselves and their friends, and to learn more about the people they meet." -- Facebook

Learn how to clean a cassette player. Cassette players may be outdated, but if you've still got tapes, you're going to want to keep them in good condition.
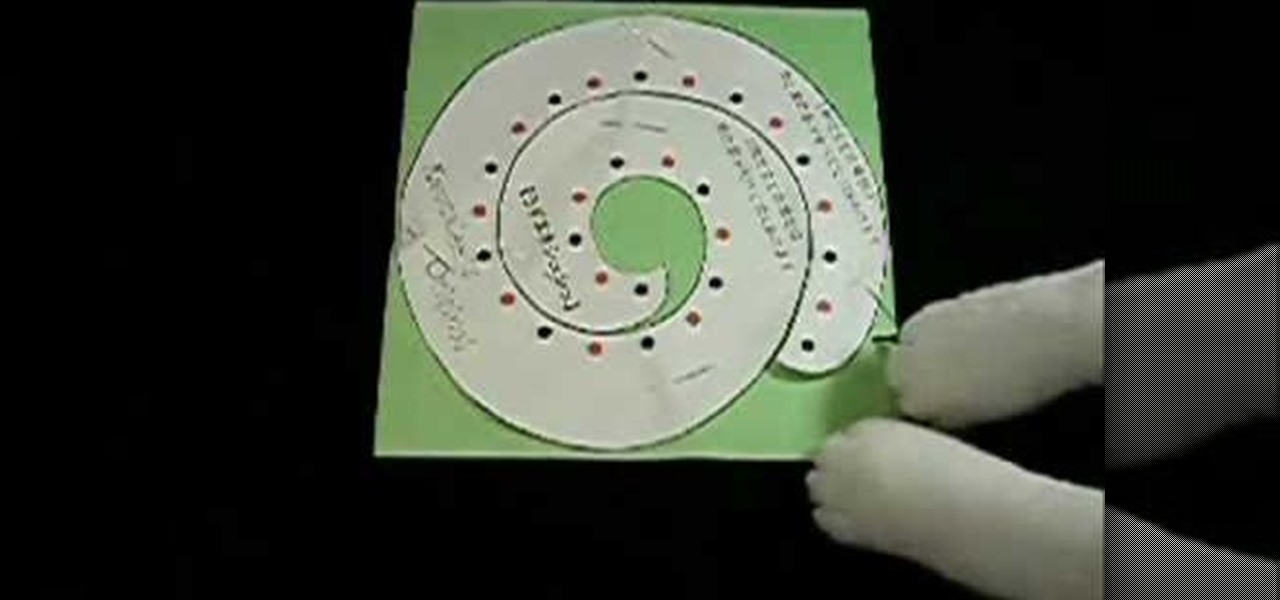
The hair scrunchie in this how-to video is so easy to make, even a cat can do it. You will need a felt fabric square of 20 by 20 cm, an elastic string of 30cm, a cutting punch, a hammer, marking pins, scissors, two big beads, and a cutting mat. Watch this video sewing tutorial and learn how to make a spiral shaped hair scrunchie.

While scrunchies might not be that common a hair accessory anymore, you can make one of your own by following the steps in this how-to video. You will need two satin fabric pieces of 50cm, a sewing machine, sewing thread, a pair of scissors, marking pins, as well as brown and black satin fabrics. It's so easy to make, even a cat can do it. Check out this video sewing tutorial and learn how to make a frilly hair scrunchie.

Embroider away with the layered lace technique! Add embroidered petals to your flowers and wings to your butterflies with a new technique called layered lace. After embroidering the separate pieces, layer them together for a fantastic three-dimensional effect! Layered lace is a wonderful embroidery technique for pins, barrettes, napkin rings, and more. Enjoy this instructional video.

Bring the glamour of old Hollywood back with this 1950's makeup look. Learn how to apply pin-up 1950s style makeup with this tutorial. The following products were used in this video: Rimmel concealer, Avon bronzer, Clinique eyeshadows, Smashbox eyeliner black, Rimmel mascara, and Loreal Art Visage in "Carmen." With this how to video and you will be able to create a 1950's style makeup look.

If you're new to Ubuntu Linux and, for whatever reason, not so very keen on Ubuntu's default email client, Evolution, then you might like to try Mozilla Thunderbird. In this tutorial, you'll how learn how to go about setting up an email account in Thunderbird. Take a look.

This video jewelry-making tutorial shows a quick and easy way to wrap the end of a pin or wire into a loop. Used this technique to make pendants, earrings, or bracelet ends. Watch this instructional video, learn how to bend a jewelry loop.

Learn to form a loop for making jewelry from this video tutorial. You will need a head pin or wire and pliers. Watch this video jewelry-making tutorial and see how easy it is to make a simple loop.

At last! You can learn how to make your hair into a pinup girl look with this tutorial video. This video will have your hair looking like a Sexy Betty Page in no time.

Soaking thread in salt and water will allow a flame to rise up it without burning through it, allowing a pin to hang at the end without falling. Nice calm music as well.

The two main types of swings for a horse drawn carriage are the solid bar swivelling on a central pin and the flexible rope type that moves on a system of pulleys.

Make an Eddie Earthworm doll. Yes, you will need cloth and pins. A sewing machine is helpful. Part 1 of 3 - How to Make an Eddie Earthworm doll.

Mary Claire has bangs and knows how to use them. In this segment she shows four different approaches to dealing with bangs.

This tutorial teaches you how to modify delrin balls using a pin vice and 1mm drill bits. The end result is a really nice set of eyes that you can insert in your clay puppet for animation.

Benny from askbenny.cn teaches some Mandarin Chinese words and phrases to use when opening a bank account.

If you're in the process of rebuilding a motor, and have gotten your old pistons cleaned (or bought new ones) it's time to install the rod pins into the connecting rods to connect with the pistons. This video shows you how it's done then they will measure the pistons to determine the final bore size of the cylinder walls before they are honed.

This is a small video documentary explaining how to wear hijab and hijab pins. Modern fashion hijabs have been used. Video provided by Muslimbase.com.

Your TikTok videos might be interesting, creative, fun, and appealing, but that doesn't necessarily mean you want the entire world to see them. While you're fine with strangers watching your videos, you may not want your close friends, family, and coworkers to see the kinds of mischief you're up to.

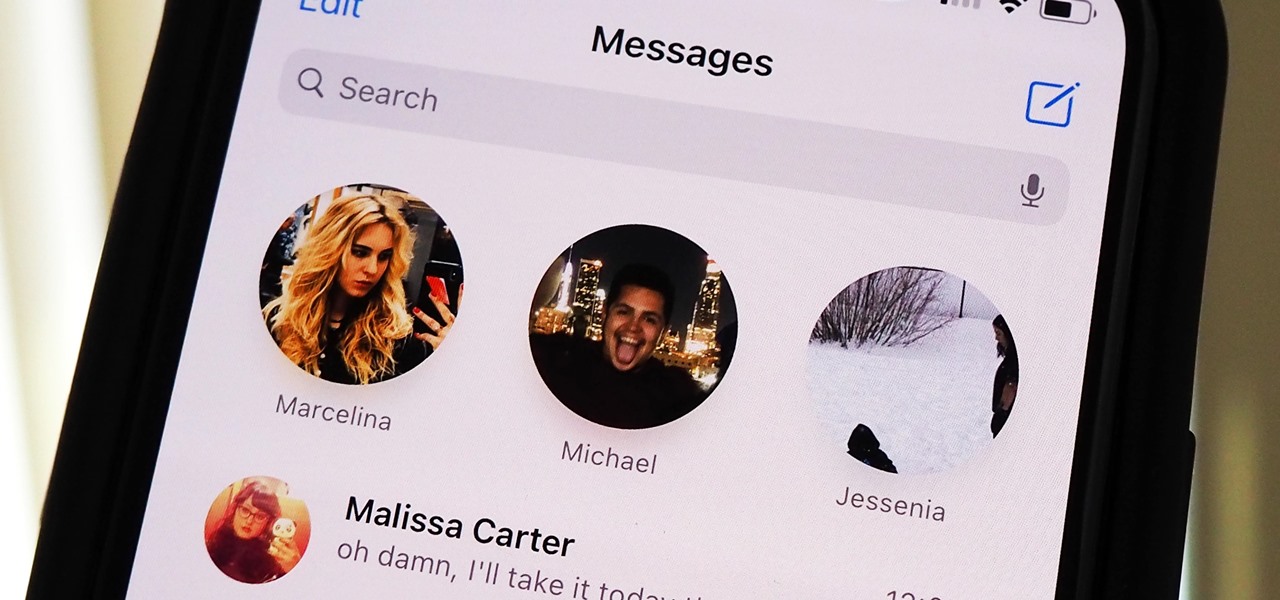
Apple is making it easier to keep track of your most important conversations in Messages. Thanks to iOS 14, you can now pin threads to the top of the app, making text messages and iMessages easier to access than ever before. Even if there aren't any recent messages, you can place the focus on the conversations you want.

When it comes to cybersecurity, one layer isn't enough. A complex password (or one created with a password manager) does a good job of protecting your data, but it can still be cracked. Two-factor authentication strengthens this by adding a second layer of security, giving you even more protection against online threats.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

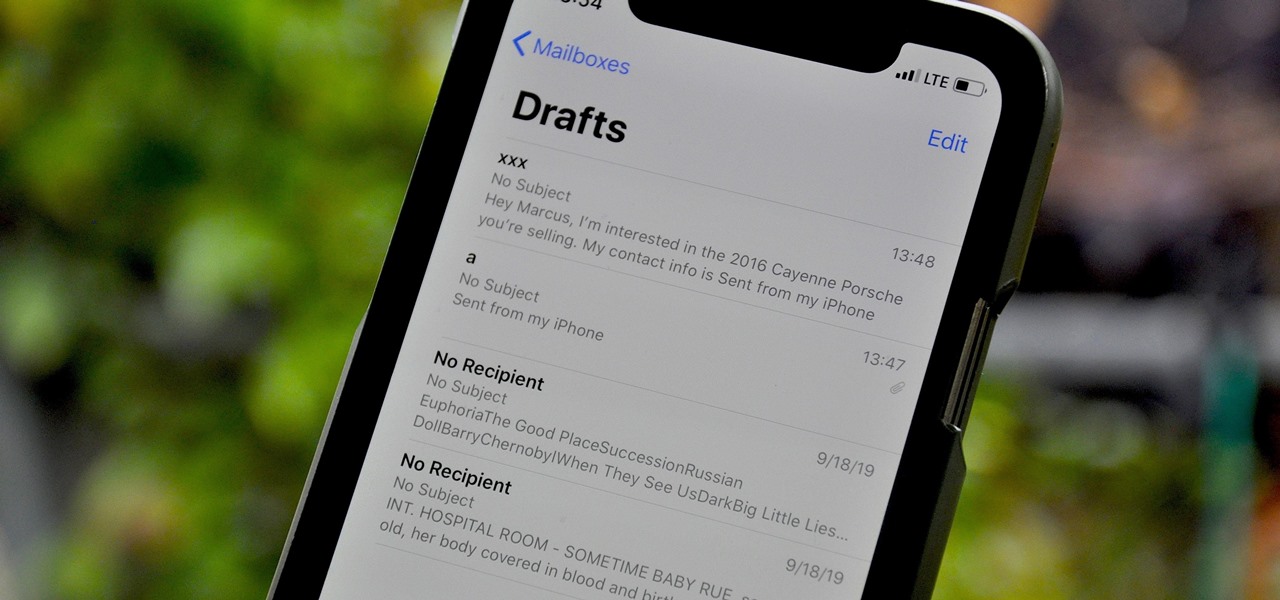
All of your partially written, unsent emails live in your "Drafts" folders, in limbo until the day they are sent off or deleted. In Apple's Mail for iPhone, you can access all drafts from all accounts in a combined "All Drafts" folder from the app's main Mailboxes list — but only if you added it manually. But there's an even better way to access all of your drafts in Apple Mail in iOS; it's just not obvious.

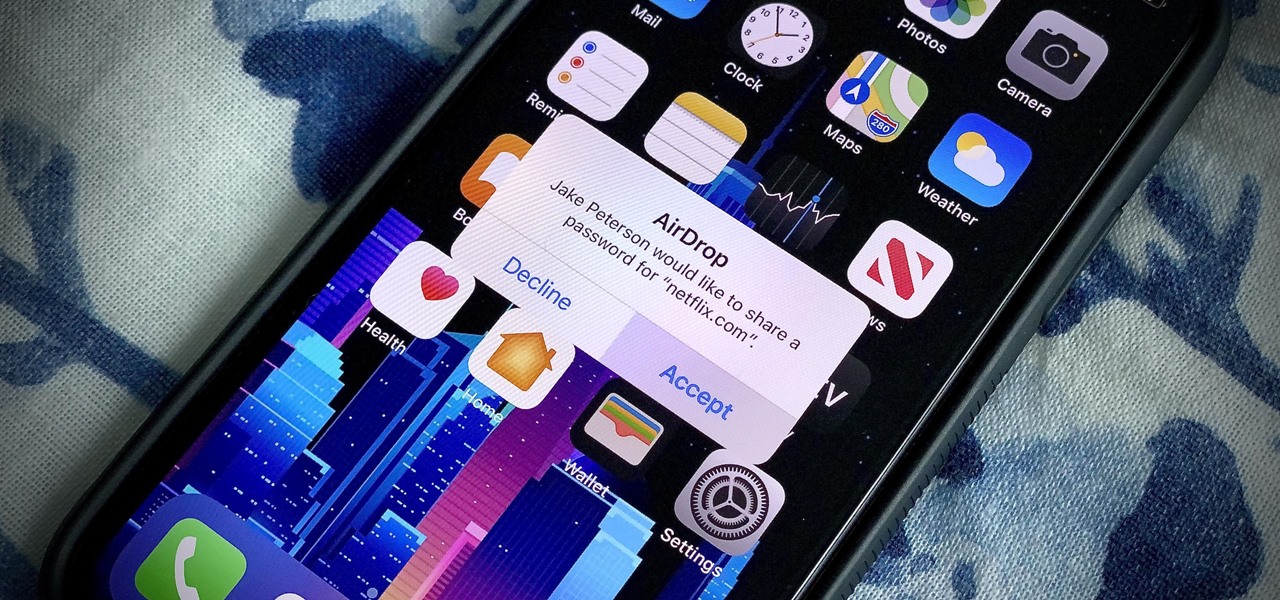
In iOS 11, Apple made it easier for you to share passwords with friends. Back then, it was just Wi-Fi passwords, which made sense. "What's the Wi-Fi?" gets old after a while. But now, whether you're running iOS 12 or 13, you can share any password you want with any iPhone around, all with one of iOS' best features: AirDrop.

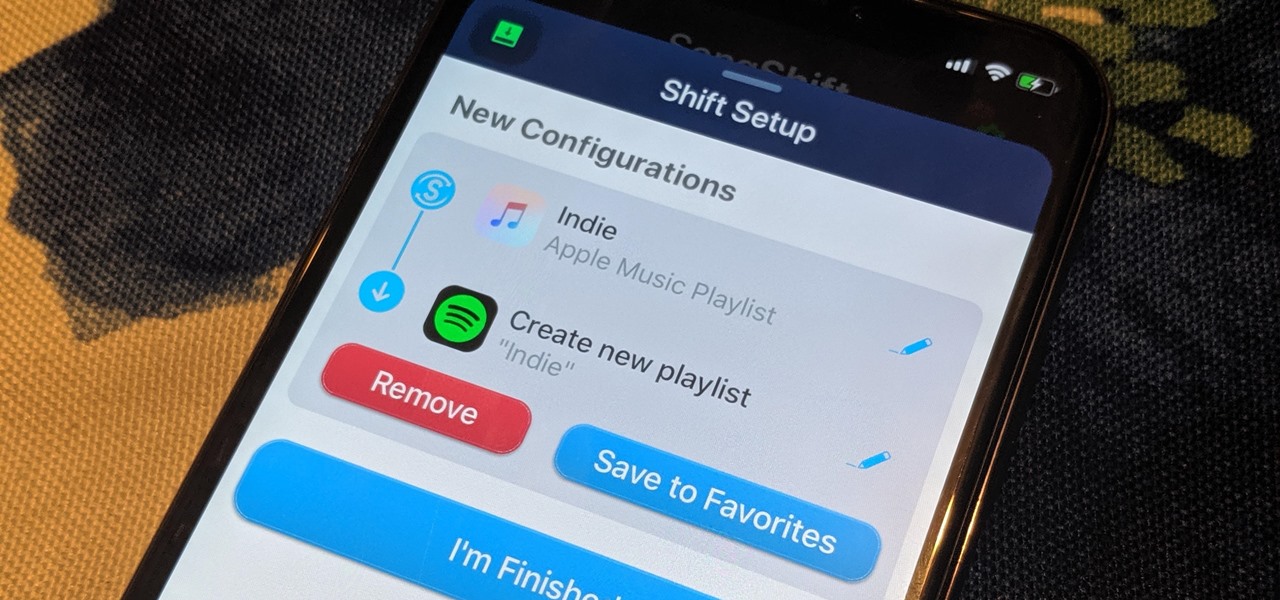
Switching from one popular music streaming service to another shouldn't have to be a hassle, but it is if you want to transfer all your favorite music over. No popular service offers a built-in feature to export or import playlists, so if you want to move your favorite Apple Music playlists over to Spotify, you'll have to use a third-party service.

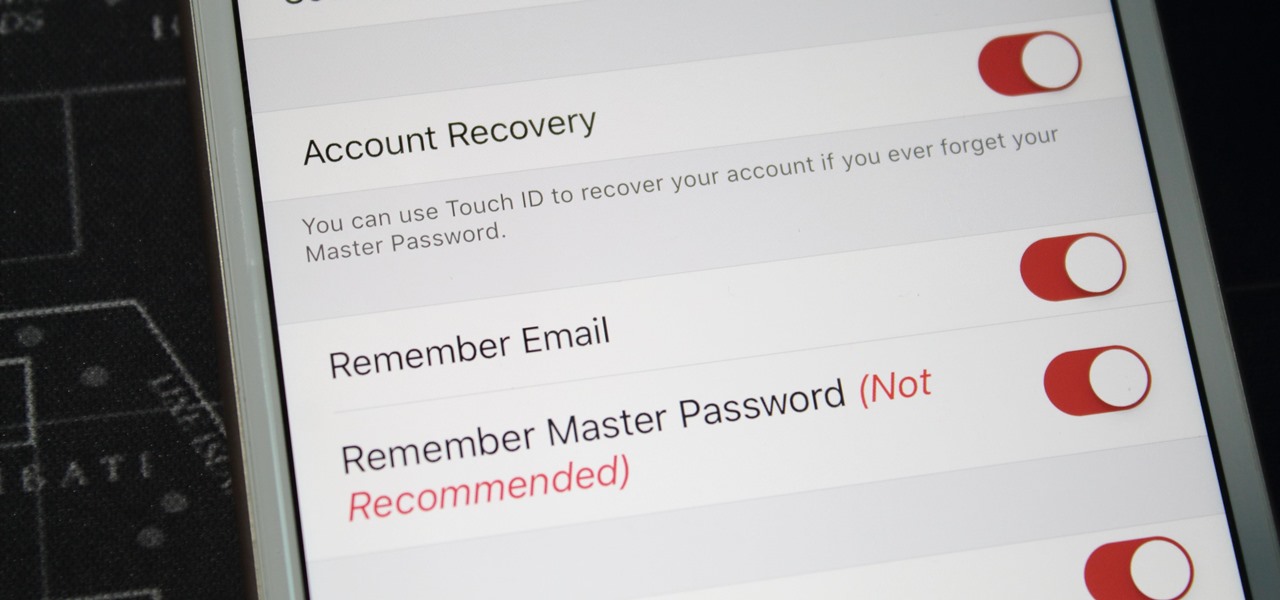
With any password manager, the only password you need to remember is the master password that locks the vault from both hackers and the company. This makes the master password very important. But what happens if you forget this password? Well, LastPass has you covered.

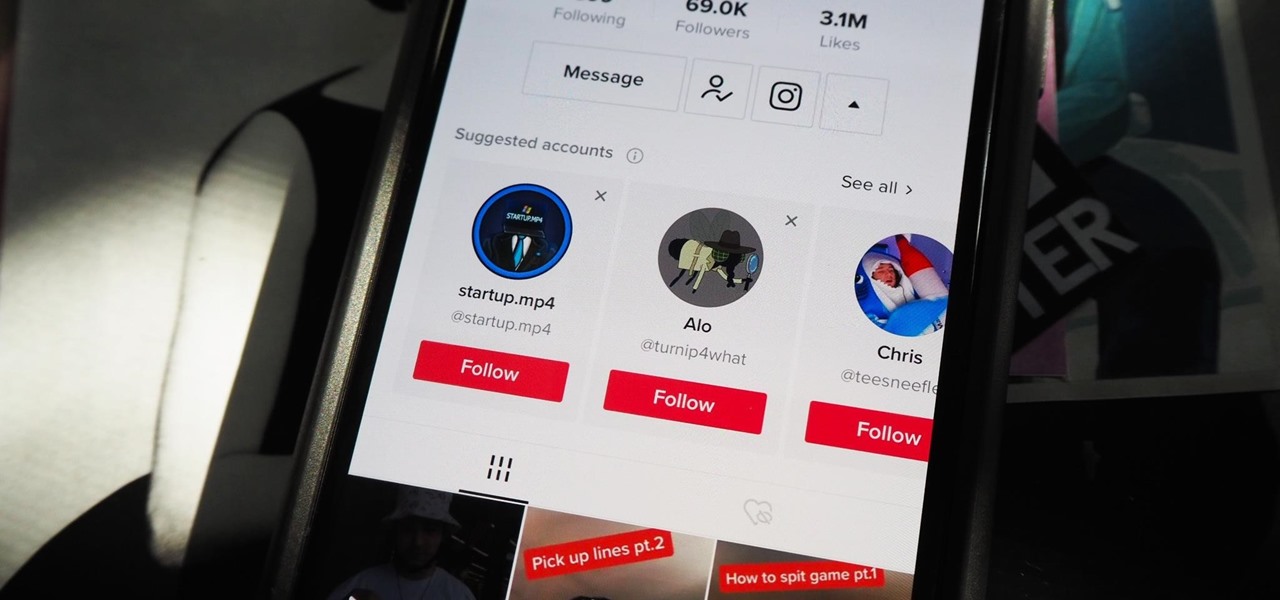
Unless you're completely new to Instagram, it's likely that you've linked your account with a third-party service at some point and forgotten about it. Those services still have access to data such as your media and profile information, so it's important that you not only know how to find these "authorized" apps, but that you know how to revoke their permissions.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

What you see when you open the Play Store is completely dependent on your country settings. Search results and top charts are specific to each region and there are lots of popular apps and games that simply won't show up unless your Play Store country matches up.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.

The share menu is a vital part of Android that lets you send data between between apps. Many of your favorite apps support the feature, including the new Direct Share sub-menu, which can lead to a messy share menu. However, there are a number of tools to clean up this clutter, three of which don't require root.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

As with most social media platforms, Instagram can be a double-edged sword. On one hand, it's a great way to share and express yourself — but on the other, it can be just as effective at compromising your privacy. Thankfully, there are a few things you can do to protect yourself.

With so much money on the line, it's no surprise that cryptocurrency exchanges are prime targets for cybercriminals. Because of this, the importance of keeping your personal account as secure as possible cannot be overstated. Binance is one step ahead in this regard, as it requires you to enable two-factor authentication to keep your bitcoins and alt-coins safe.

Equifax reported on Sept. 7 that it discovered a breach on July 29 which affects roughly half of Americans, many of whom don't realize they have dealings with the company. Hackers got away with social security numbers, addresses, and driver's license numbers, foreshadowing a "nuclear explosion of identity theft." Let's explore what really happened and what you and those around you can do to protect yourselves.

Gmail has been the email standard for quite some time now, and for good reason: it's a free service provided by one of the largest tech companies in the world that offers users an amazing feature set to manage, send, and keep track of all their important emails.

Hello Everyone! I wanted to share a free and open source note taking tool that I've been using for quite some time now.

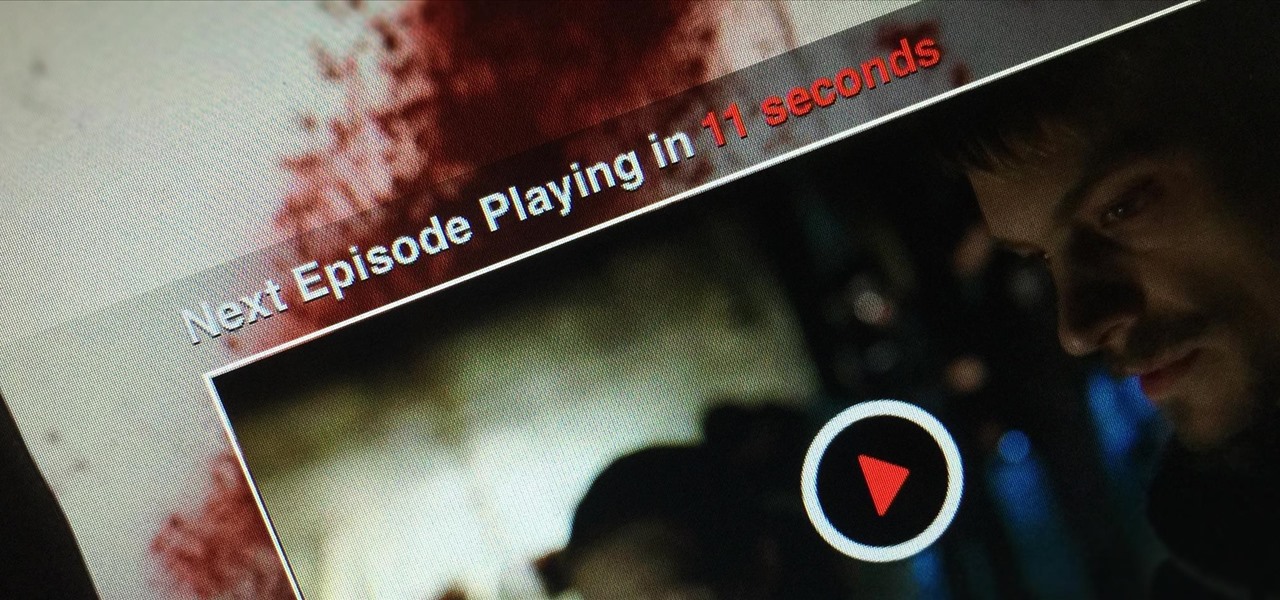
Netflix is an enabler. It creates a joy around binge-watching and couch potato-ness, and the major contributor to this epidemic is its built-in "Post-Play" feature.

This video will show you how to protect others from accessing saved password on Google Chrome. Saving account passwords in browsers are useful for time saving as well as threatening for malicious activity. This is dangerous for security. So you must protect your accounts detail from others to secure your browsing. Watch the video and follow all the steps carefully.

How to make a cute Macrame Butterflies. This butterfly can be used as: necklace, pendant, earrings, bracelet, keyring, keychain, bobby pins, hairdo or hair ornament, etc..