
How To: Troubleshooting a door check link
Here, Rich Pin demonstrates how to troubleshoot the door check link by working on the Saturn S series. Typical example is the popping sound you hear when you open and close the door.


Here, Rich Pin demonstrates how to troubleshoot the door check link by working on the Saturn S series. Typical example is the popping sound you hear when you open and close the door.

What's better than homemade corn tortillas? Follow these simple steps for homemade corn tortillas that will make your guests shout "Ole!"

Clueless when it comes to styling those unruly bangs of yours? Face fringes are cute and fashionable but need extra attention to keep them looking fresh. In this video, learn how to style those bangs easily and with style.

Not sure what to be next Halloween? A princess is a classic choice. Whether you’re making a costume for your little girl, or want to feel like royalty yourself, a princess costume is always in style.

Superman is one of the greatest and most known superheroes out there. Developed by DC Comics, Superman has seen the world… as in comics, television, newspaper strips, video games, movies, radio serials, etc. See how to make a Superman costume in this video from GiannyL.

What's better than a biscuit hot from the oven? Make a batch tonight with this easy recipe. You Will Need

Make a splash at your next masquerade party with this purr-fect black cat costume. You Will Need

Your sewing machine needs bobbin thread to create overlock stitches, so keep your machine going by learning to fill your bobbin.

Turn your home or patio into an incandescent flower garden with plain holiday lights and egg cartons.

Why justify the cost of buying a corsage from your local florist? Make an affordable corsage yourself that reflects your personal style.

In Asia and the Middle East, paste made from the henna plant has been used for centuries to make beautiful temporary tattoos. Make it at home following these easy steps.

In Judaism, men customarily cover their heads with a skullcap as a sign of humility before God, though it is not mandated by law. In Hebrew, it is called a kippah; in Yiddish, a yarmulke. In Europe, the custom dates to the end of the 16th century. Learn how to wear a kippah (yarmulke) with this Howcast guide.

Try these simple fixes to salvage your specs. Learn how to fix your eyeglasses with this helpful guide.

This is no schoolmarm style. You'll instantly look chic with a messy bun. You Will Need:

Learn how to do power stability ball lower back extension with pelvic thrusts. Presented by Real Jock Gay Fitness Health & Life.

We all know Google keeps a history of everything we do on our phones unless we say otherwise. However, you might not realize just how detailed it is until you check it for yourself — even the actions you do in each app are tracked by default.

You can block artists no matter where you are in Spotify's mobile app for Android or iOS, but it's not as easy when you want to hide songs from playing. Disliking tracks is possible here and there, but not everywhere, and that's a serious problem if you keep hearing songs you hate.
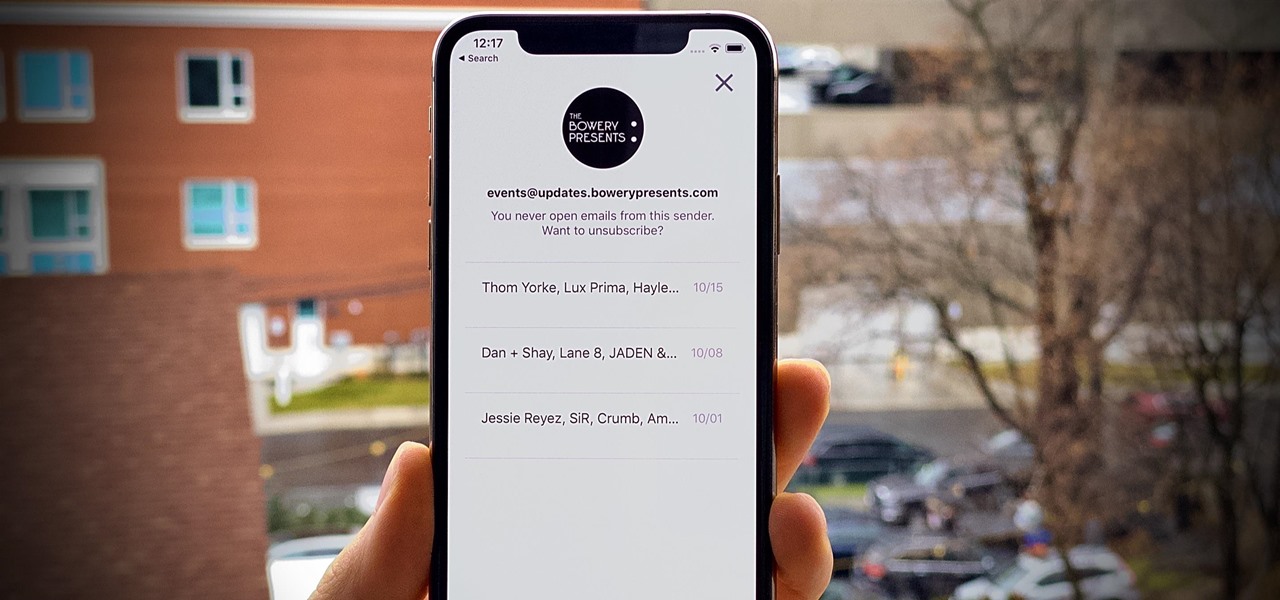
Edison Mail's big 1.17.0 (iOS) and 1.12.0 (Android) updates introduce a new, powerful Assistant to the mix. Aside from the fresh calendar integration and extensive customizability, you'll probably be most interested in the Assistant's unsubscribe feature. It helps to locate and cut down on your inbox's ever-growing jungle of spam. Here's how it works.

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

Twitter's official iOS app is adequate if you're not much of a tweeter, but if you are, there's a lot of useful features that are missing. Luckily, there are plenty of free Twitter clients available that you can use on your iPhone. These third-party apps have features such as customizable interfaces, post scheduling, and different browser options for opening links, to name just a few.
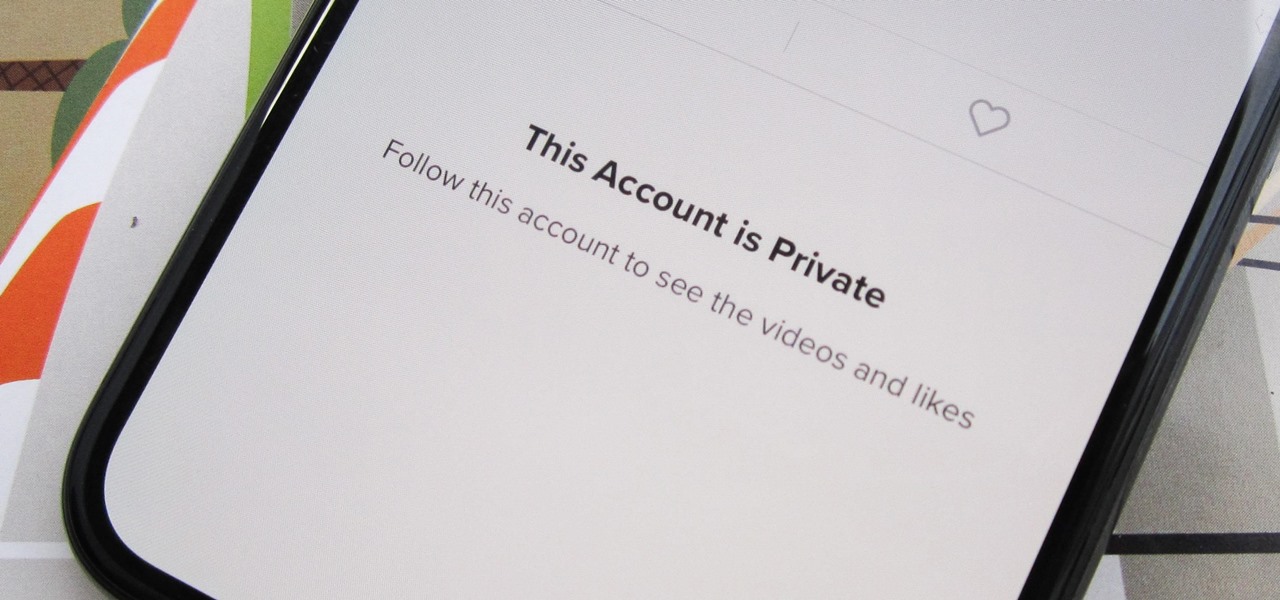
Can you trust every user you come across on TikTok? The answer to that may depend on how use the service, but the real question is — can you trust every user that sees your content? Not everyone on TikTok is someone you want viewing or interacting with your content, and there's a way to prevent them from doing so.

If you use Apple's email services and the "From:" field in your iPhone's Mail app is cluttered with @Mac.com, @Me.com, and @iCloud.com variations of the same address — along with third-party accounts — there's an easy way to declutter things and hide the addresses you don't use anymore.

Hearthstone, Blizzard's online card game, combines strategy with a fun spin on the World of Warcraft lore to create a unique experience. With the latest expansion (The Witchwood) on the horizon, you'll want to make sure your collection is ready for when the set drops in April. Fortunately, you can get free packs on iPhone or Android to help prepare.
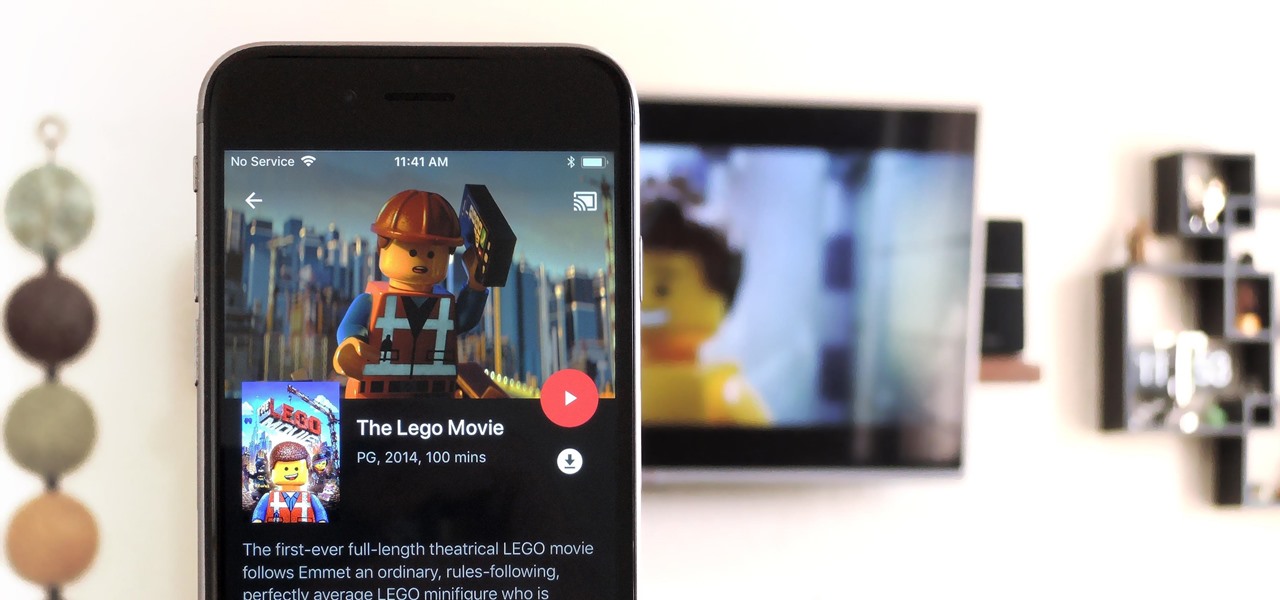
Google announced a partnership with Movies Anywhere that allows you to connect your iTunes, Amazon, and Vudu movie library with Google Play Movies. In other words, movies you purchase from any of these online retailers will be available for playback in the Google Play Movies app after a little setup.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

Zently — the mobile app for renters — is taking on Venmo with its newest feature. Traditionally used to automate rent payments, deliver rent checks for free, and communicate with your landlord, it now allows you to connect to your bank account and split bills with housemates. Following the addition of Zelle to several major banks apps — to allow users to transfer money to their contacts — the battle of the mobile payment apps is getting increasingly fierce. With this new update, Zently is als...

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

If you're a Mac user with an Android phone, some apps on your computer aren't very useful, such as Messages, which is meant to work and sync with iOS devices. But now, thanks to MDRS, LLC, using the Messages app on your Mac with an Android phone is now possible and easily achievable. Plus, we've got 50 promo codes to give away for a free year of service!

While we now know that iCloud was not exploited by hackers to steal private celebrity photos, Apple did admit that guessed (aka brute-forced) passwords and/or iCloud security questions were to blame for the breach.

People who know that I am a professional hacker often ask me what they can do to make their computers and personal information safe from people like me. The answer, of course, is that nothing will make you completely safe, but there are a number of measures any computer user can take to reduce the chances of being a victim of a hacker.
Believe it or not, but people are actually texting less than they did before, and that's all thanks to Facebook Messenger, Snapchat, WhatsApp, and other split-second communication services. However, one communication method that is still going strong—and dominating—is email.
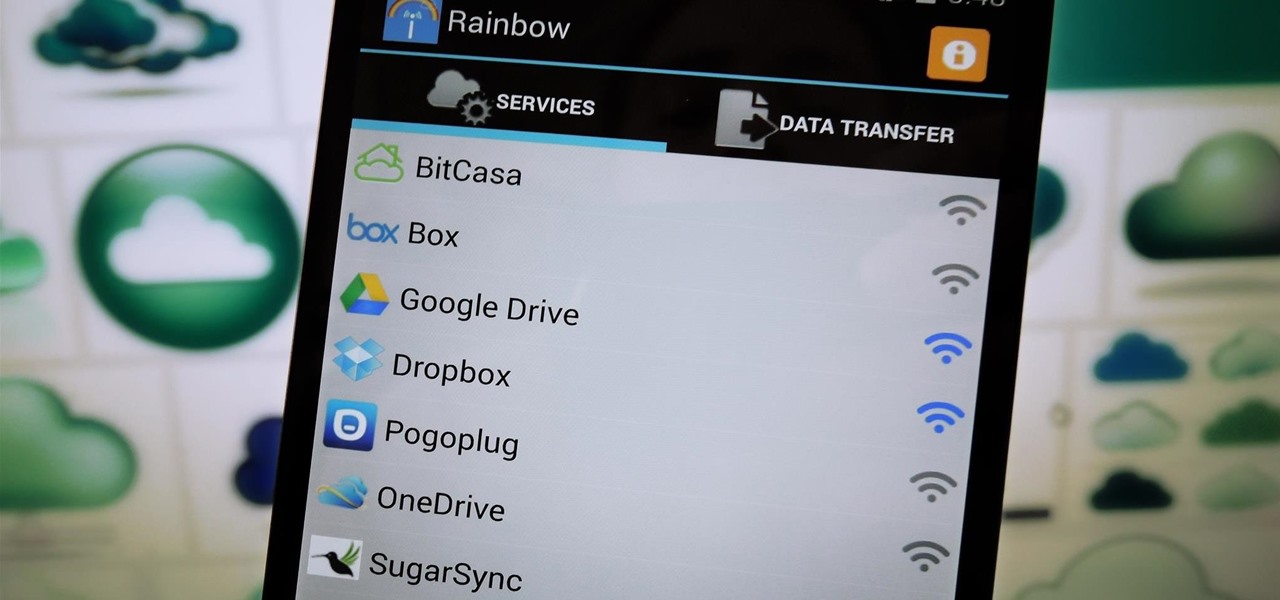
With limited storage options available on the Nexus 5, cloud storage can definitely come in handy. But sometimes, with the seemingly endless options of cloud services for us to choose from, our online data can get a bit disorganized.

Greetings. This how-to on hacking Windows 7/8/10 etc. admin account passwords using Windows Magnifier is focused on adding, changing, or deleting an admin level account on a Windows 7/8/10 etc.

It was just released a few days, but Facebook Paper has already taken the world by storm. CNET said it was a better way to use Facebook. TIME said it's the future of Facebook. The Verge called it the best Facebook app ever. There's one problem, though...

We all know about PRISM. The Surveillance Program allowing the U.S Government to access private user information. Such as, Google Searches, Tweets, Facebook Posts, Private Images, and other private user data. "Hiding" yourself can be very difficult, but it is possible. I'm here to show you How to Become Anonymous & Browse the Internet Safely.

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

The SATs are a very valuable college entrance test and could determine if you're accepted or denied to your favorite university. So, once you've learned to ace the SATs and have already taken your test, get your scores as soon as they're out! Don't sit in dreaded anticipation— go to College Board and get your SAT test results now!

A flaw in WPS, or WiFi Protected Setup, known about for over a year by TNS, was finally exploited with proof of concept code. Both TNS, the discoverers of the exploit and Stefan at .braindump have created their respective "reaver" and "wpscrack" programs to exploit the WPS vulnerability. From this exploit, the WPA password can be recovered almost instantly in plain-text once the attack on the access point WPS is initiated, which normally takes 2-10 hours (depending on which program you use).

This video tutorial will show you how to setup your YouTube account in order to enable you to play videos automatically in high quality when available. It only takes a few seconds to setup. It is a very simple process that takes us through the settings and options to enable your default viewing of videos.
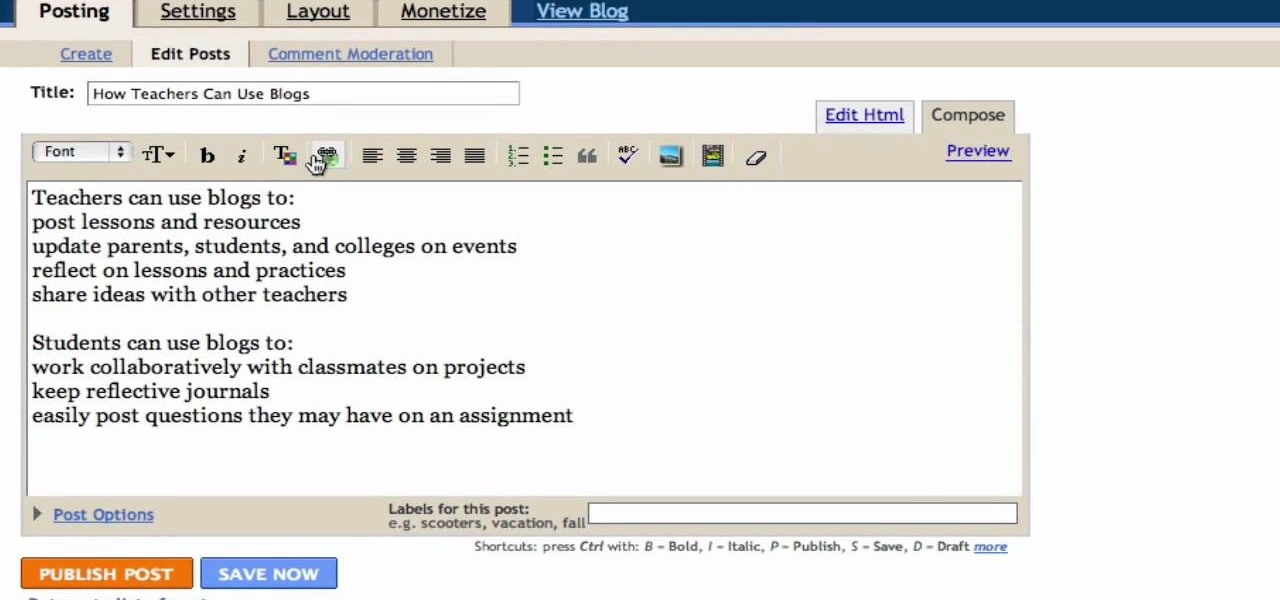
In this Computers & Programming video tutorial you will learn how to create a new account, add and edit in Blogger. First go to Blogger. On the home page click on ‘create a blog’. You will be taken to the account setting up page. Feed in all the details including our email. Then open your email and click on the confirmation link. You will then be taken to your dashboard or your home page. On this page you can click on ‘new post’ button and start writing your blog. When you do this a word proc...