To replace a door, refer to Lowe's do-it-yourself for a step by step guide. Replacement is not very difficult. To replace just the door, tools and material required are: a new door, hammer, screw driver, tape measure, pencil, combination square, saw horses, clamps, chisel, a door lock installation kit, a drill with bits, circular saw, level, work gloves, dust mask, safety glasses, plane, shims, cardboard, and a utility knife. Before removing the old door, take a few measurements like the widt...

It's never too early to put away money for your child's education. Consider these options before choosing a plan. Watch this video to learn how to get started with a college savings plan.

Digidesign has transitioned all of their plug-in software copy protection from floppy drive based key disks to copy protection authorizations that reside on the iLok technology provide by PACE. The following is some information about iLok technology.

On Android, you can connect your PayPal account to Google Pay so that you can use that as a payment option when checking out with Google's digital wallet platform. It even works across Google services like the Play Store, Gmail, YouTube, and the Google Store. If you have an iPhone, you can also use PayPal via Google Pay, but what you can do is limited.
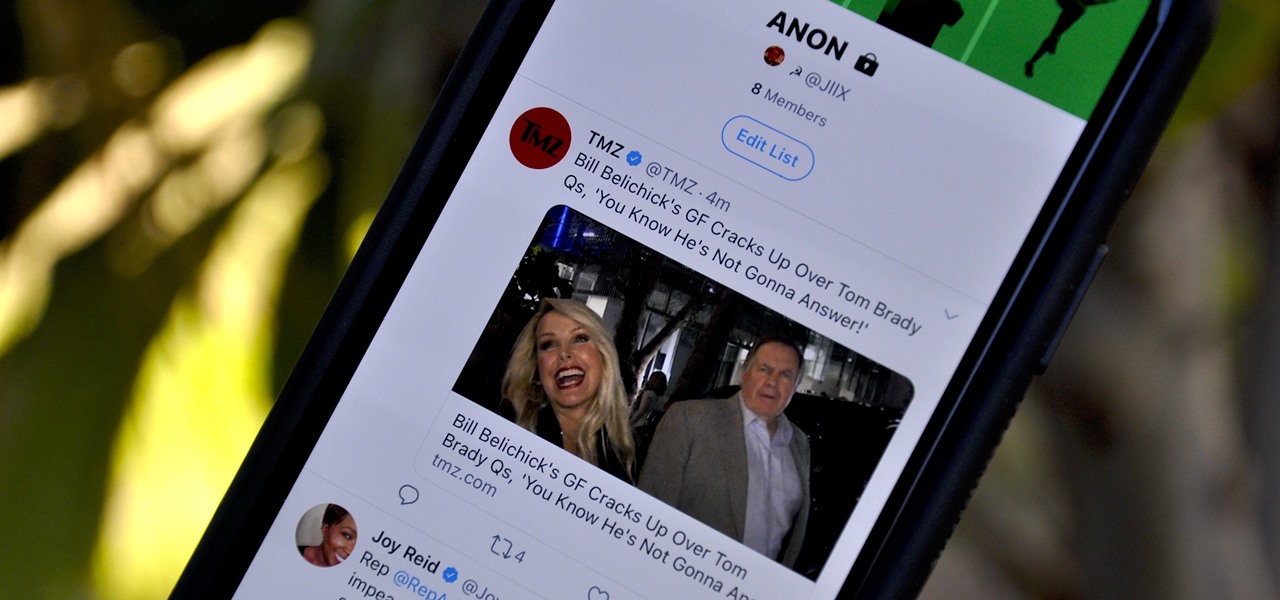
Following someone on Twitter is an investment. You virtually agree to have their opinions, tirades, and hot takes spewed across your timeline. It can get annoying real quick if they're known to post controversial comments periodically. However, there are other ways to stay updated on someone's tweets without you having to hit the follow button and go all in.

We've all seen the login pages that allow you to log in to third-party accounts using your credentials from Facebook, Google, or Twitter. It saves you the trouble of creating another account and remembering more passwords — but it can also become a privacy and security issue, which is why Apple created the "Sign in with Apple" feature for iOS 13.

If you're concerned about someone accessing your OneDrive files, you may want to upgrade your protection by enabling fingerprint or Face ID unlocking. Your sensitive information deserves to be protected, and now you can do so easily. Worry no longer — if you need to let someone else use your phone, with a password-protected OneDrive, sneaky file grabbers will be out of luck.

Fireworks are the best part about the Fourth of July and other celebrations, but they can easily cause accidental injuries. It's both safer and more fun to set them off remotely, so we'll hack some standard fireworks with nichrome wire, a relay, and an Arduino to ignite remotely over Wi-Fi using any smartphone or computer.

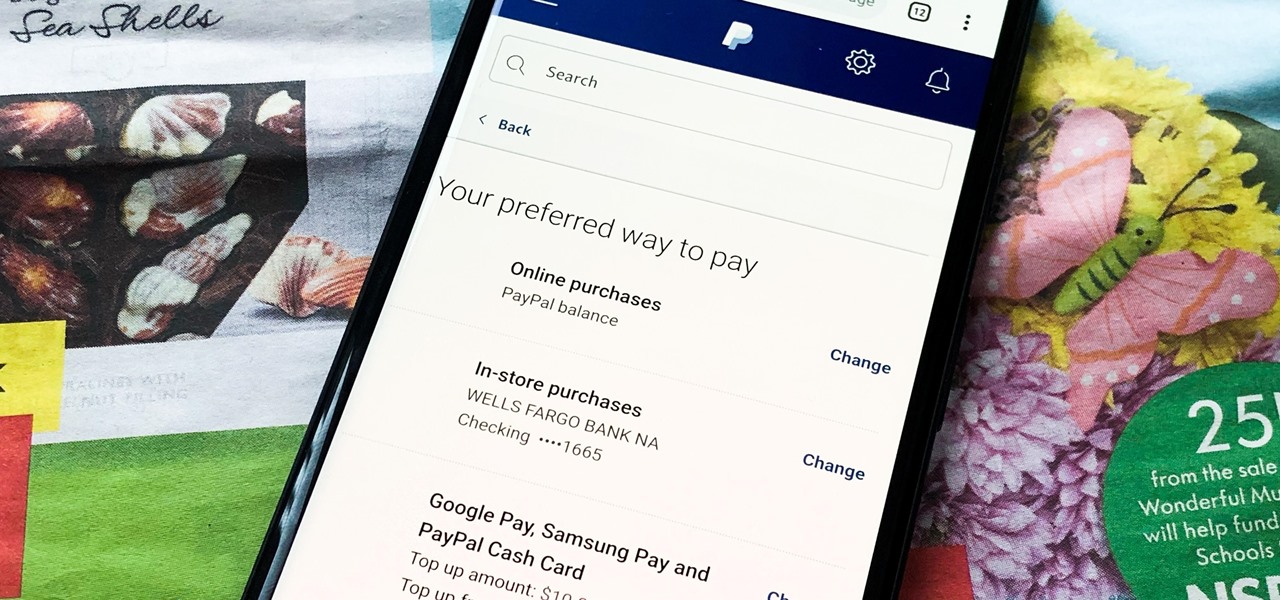
Making a purchase through PayPal is great because you have the option to pay using your account balance, a bank account, debit card, credit card, rewards balance, or even PayPal's own credit product. You need to pick one to be your preferred payment method for each in-stores and online but, unfortunately, changing these preferences can get a bit tricky on your iPhone or Android phone.

If you've ever received an email from a sketchy address purporting to be Uber, asking you to sign in with your credentials, you might be a phishing target. Hackers use a fake login page from real-looking domains to trick you into giving up your account information, and while it's been an issue in the past, Uber is making it more difficult on cyber thieves with the addition of two-step verification.

Unless you want to make your TikTok account totally private, anyone that uses the app — with or without an account — can view your profile and all the videos of you performing new dance moves, singing along to popular songs, and recreating your favorite TV show scenes. Even worse — they can download those videos.

Almost every phone comes with biometric security of some sort these days, but the same can't be said of Windows computers. While fingerprint scanners are becoming increasingly common with laptops and desktops, they're nowhere near ubiquitous. Thankfully, your phone's scanner can be used as a sort-of remote authentication point for your PC.

Media subscriptions are all the rage these days. Between Netflix, Apple Music, HBO Now, and countless more, your TV, movie, and music options have never been better. Unfortunately, all these choices weigh heavily on your wallet. So, when there's an opportunity to snag not just Spotify but Hulu and Showtime as well, all for just a tad bit over five dollars a month, how could you turn that down?

Recently, a user on Reddit complained that their Snapchat account had been temporarily banned because Snapchat noticed the user's account was going through a third-party service. In reality, the account in question was running on a jailbroken iPhone, and it was far from the first to be banned by the messaging app.

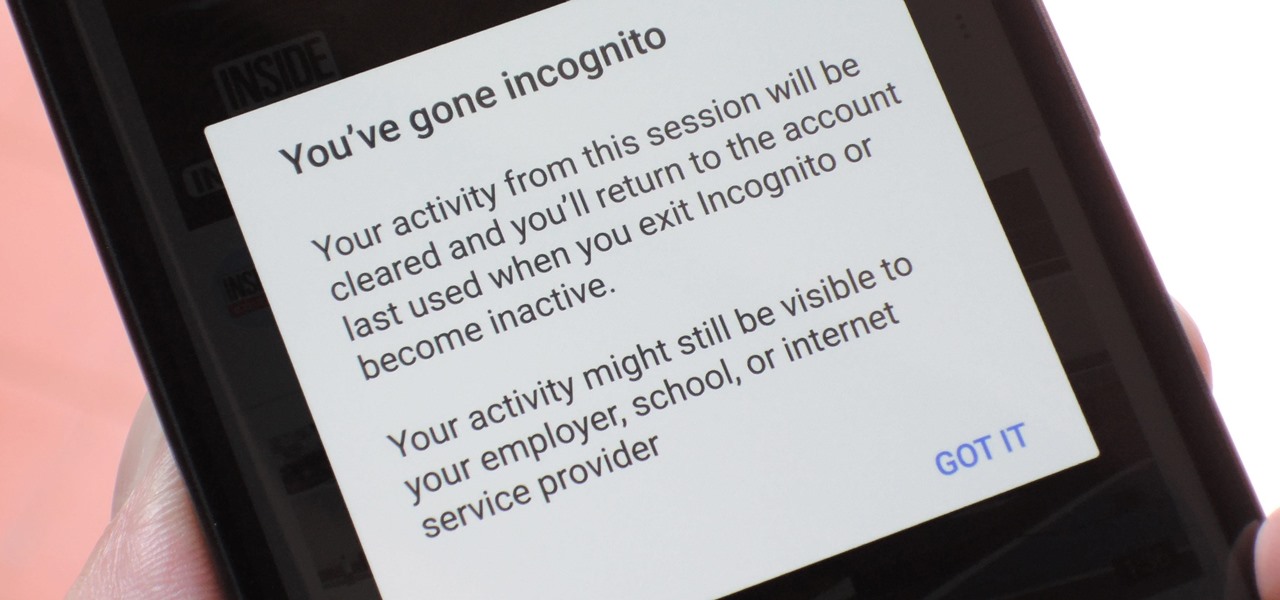
Incognito Mode is a privacy feature that was popularized by Google Chrome, and it recently made its way to GBoard. Now it's coming to the YouTube app to help make your video watching experience truly private.

If you want to automate tasks with your smartphone, IFTTT is a great app. It does a tremendous job of helping you find applets or creating your own from scratch, so it's easy to connect your favorite online services and make them react to each other. With all this personal information, though, you should ensure that your data is secure by enabling two-step verification.

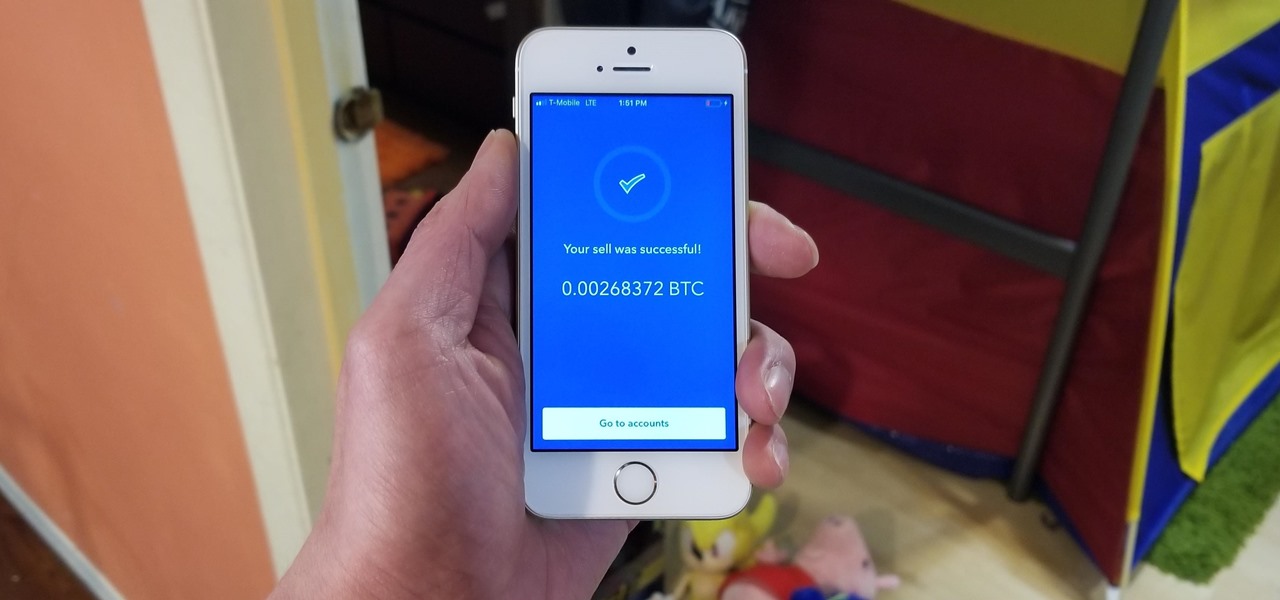
Coinbase has become the most popular mobile wallet app due in large part to its user-friendliness. The app takes the hassle out of buying and selling Bitcoin (BTC), Bitcoin Cash (BCH), Ethereum (ETH), and Litecoin (LTC), letting Android and iPhone users alike trade their favorite cryptocurrency in a few easy steps.

It's really easy to binge-watch episode after episode, and that's exactly what Netflix wants us to do. Before you can even think twice, the next video is playing and you're stuck wallowing in the abyss of unintentionally marathon-viewing your new favorite TV show, and there's nothing you can do. Except there is something you can do — and it's as simple as disabling one little feature.

It's safe to say most of us know the dangers of online security. We know there are people trying to steal our most sensitive information, and we try our best to prevent that theft. But new research is showing what we're doing might not be enough, as the sensors in our phones may be telling hackers everything they want to know.

Google seems to be growing tired of the way links appear in its Search results page, because they're currently experimenting with a color change (that's already causing lots of controversy).

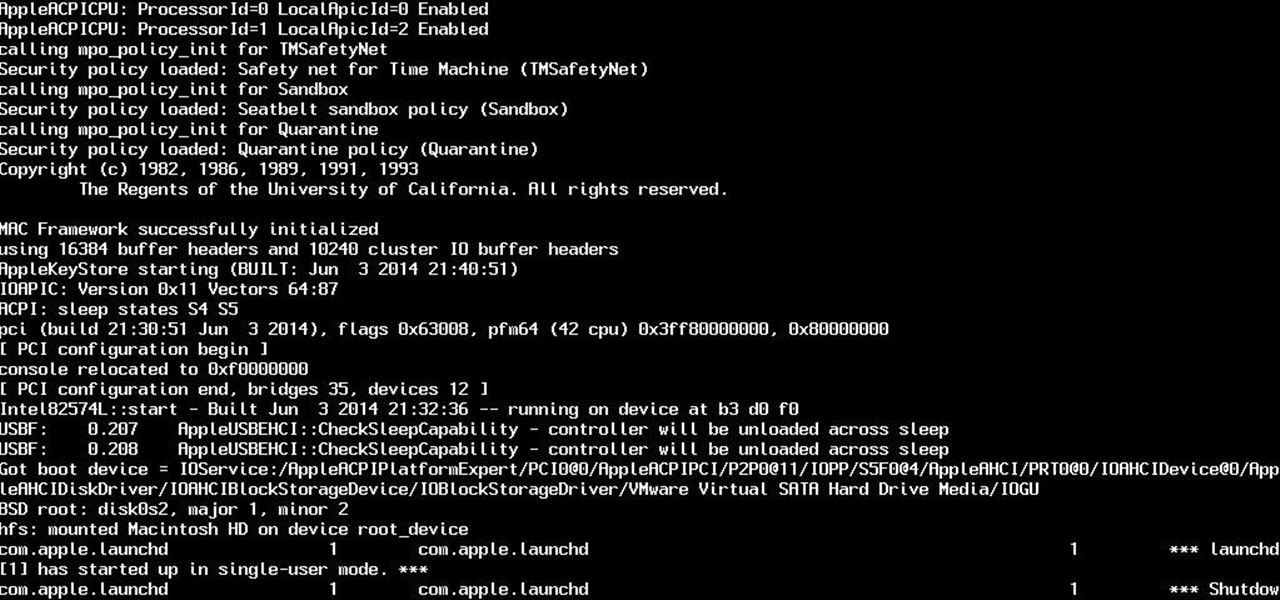
So yeah. Its AugustFackYou and I felt like posting today and being an active member of the community. After reading this please tell me if you have any comments on what I can do better or if this method is bad. Anyway today I will be showing you how to get root on a mac. I managed to become an administrator at my school with this and one other method.

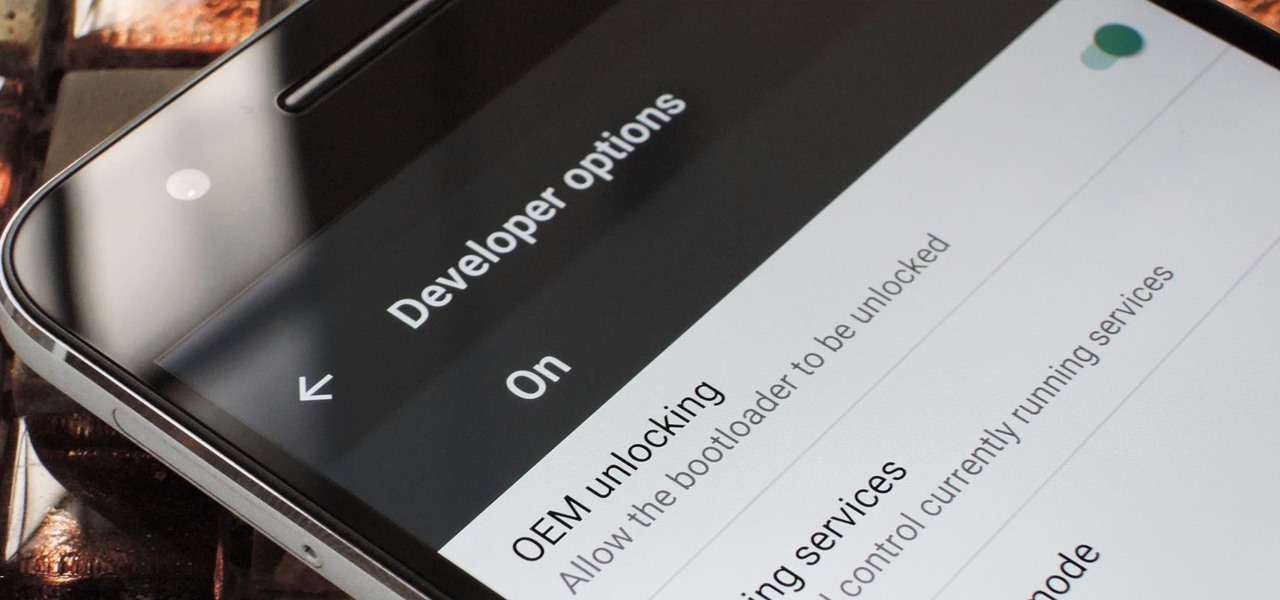
If you've ever rooted an Android device in the past or installed a custom recovery, you're surely familiar with the term "unlocked bootloader." But if all of this sounds like gibberish to you, some major changes in Android have made it to where you should definitely get familiar with the concepts.

Playlists are more than just a list of songs that you enjoy listening to while in traffic or hosting a party—they're stories that illustrate who you are or your frame of mind at a certain point in your life.

I'm back. School's an ass. On my quest for knowledge, which started approximately 3 years ago, I can upon an interesting little artifact. It is called the Arduino.

If you ever need to make calls and/or send texts to the U.S. or Canada from abroad, or even just receive them from those locations, there's an easy way to do so without breaking the bank. In fact, it's free, and all you need is a smartphone, computer, and some free tools.

It might be difficult to admit, but a lot of us are probably guilty of lurking on Instagram profiles, whether it be an ex you've been keeping tabs on or someone cute you literally just met.

This is second post in my series of posts for finding hacked accounts online. Please do read the part 1 of the post at http://null-byte.wonderhowto.com/how-to/find-hacked-accounts-online-part-1-0164611/

If you want to watch a movie on Netflix with a friend, family member, or significant other, but can't meet up in the same living room, the next best thing is doing it remotely from the comfort of your own homes.

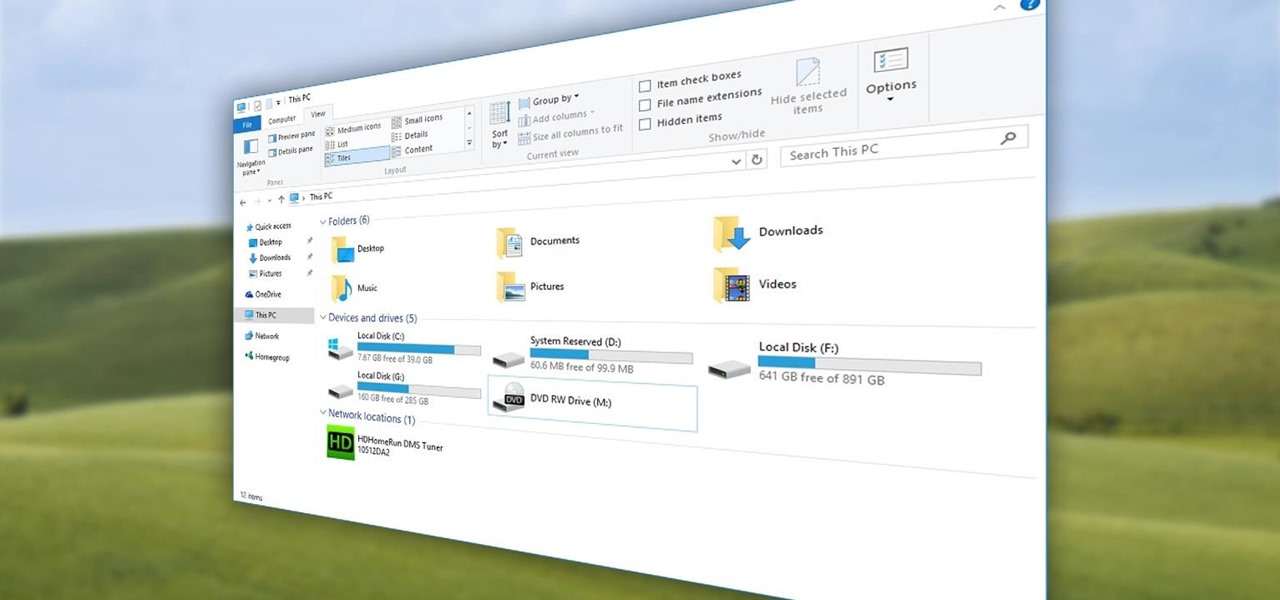
Quite a few things have changed with Windows 10, but one of the more central features that has received a makeover is the old Windows Explorer program, which has been renamed to File Explorer in this version.

If you have some photos, videos, and documents that you want to keep completely hidden and encrypted on your Android device, Andrognito is the app you need. We showcased this app in the past, but since then, CODEX has rebuilt it from the ground up with new and improved features.

These days, that pocket-sized computer we call a smartphone is home to your entire digital life. But with the onset of mobile payments and online banking, the line between your virtual world and the physical realm is becoming increasingly blurred.

The options for finding random or specific music to listen to are vast. Spotify is excellent for streaming popular music and new releases, while SoundCloud provides a healthy dose of user-generated remixes and originals. And then there's YouTube for everything else.

Hello Elite Hackers! Welcome to my 3rd Post, which explains how to hack any account like G-mail, Facebook, etc.

With all of the productivity tweaks and usability enhancements that we cover here at Gadget Hacks, it's nice when we come across a unique and noteworthy app that's simply about having fun.

Google's Chrome Remote Desktop, which allows for remote access to your personal computer from your smartphone, has been out for almost a year now. Sadly, it's only been available for Android devices—until now. So, if you got an iPhone (or other iOS device), you can now access and control your computer directly from your smartphone or tablet just like with Android.

Spotify is how I listen to almost all of my music; I use it on my way to work, while I workout, and even while I'm in the shower. And more often than not, I use my Spotify account on various devices including my MacBook, iPhone, and LG G3. In order to make listening to music across multiple devices even more convenient, Spotify released “Spotify Connect” earlier this month.

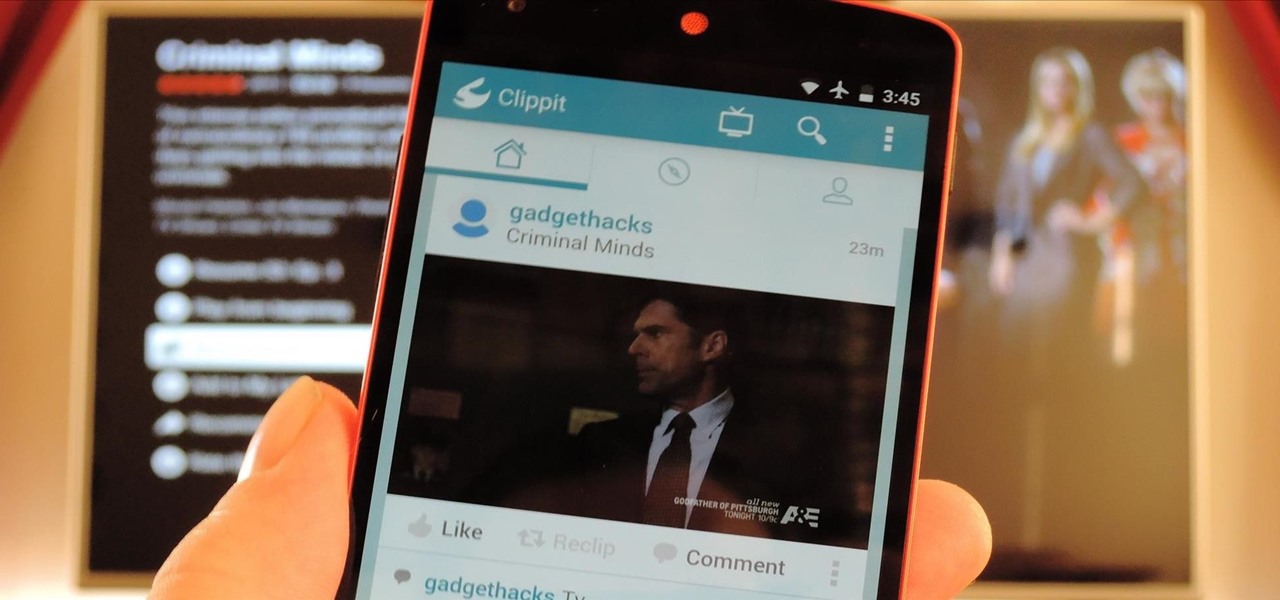
Social media is constantly evolving, and as a result, we're now capable of sharing much more than we were even just a few years ago. Television, on the other hand, continues to hold strong as one of America's favorite pastimes.

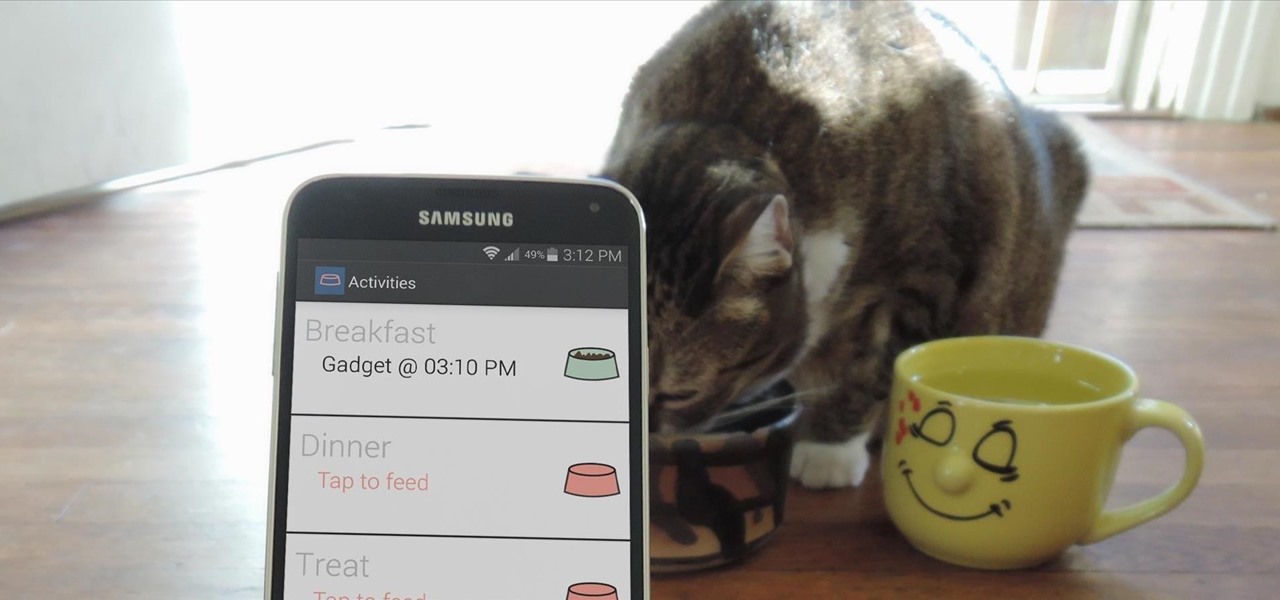
Pets are one of the biggest sources of joy in life, but keeping track of their daily activities can easily become a chore. When you have a roommate or spouse that also likes to feed the cat or walk the dog, miscommunication can lead to double-feeding or an under-exercised pet.

I think it's safe to assume that most of us appreciate a little privacy and security when it comes to our mobile devices, which is exactly why we have lock screens that require unique passwords, patterns, or PINs. Although someone can discretely peer over your shoulder to see what your password is, it's much more difficult for them to duplicate your face to unlock the device.

The interwebs is a great source of information, but sometimes said information is not always legit. That can be frustrating when it comes to making fun food, costumes, and arts and crafts for Halloween, like this bowl of "bloody" gummy worms.