Zacuto Universal Baseplate V3, includes 12-inch rods and works with all cameras. Zacuto's Universal Baseplate allows mounting accessories off the front and the back of the rods. Our new version 3 Universal Baseplate is 22% lighter then Version 1 or 2. The baseplate measurements (excluding rods) are 7 x 4 x 1 ½

Do you like chess? How about Japanese chess? Aren't there different chess variants in Japan though? Maybe, but this specific chess variant is called Shogi. The chess-like game Shogi is won by capturing the king, just like chess, but defeat is conceded at mate, or when mate becomes unavoidable.

Watch this knitting instructional video on spacing and marking buttonholes for knitting projects. This knitting demonstration uses the swatch of a right sweater front to show an easy way to mark the placement of buttonholes on your knitted material. Lily Chin attributes the method to Carol Anderson of Cottage Creations. You wil be working the button bands from the right side, from the bottom up, so you'll be marking the placement of the bottom of each buttonhole. If this was a boy's or man's ...

Whether you're heading to a frat party, out for Halloween or just looking for a cool way to tie your towel at the beach - this video is here to help! Learn how to tie a toga, the ancient Greek way of dressing, and be ready for whatever costume situation may arise with a quick and cheap outfit!

Summer is just around the corner and those jeans that seemed perfect for winter aren't looking so hot. Put those jeans to use, and make your very own jean skirt. Grab a pair of scissors and a sewing machine and get started.
Have you ever wanted to go into another user's account on your computer but had trouble finding the energy to log out, then log out, only to log back into your own account? Well, here's your solution: XNest will let you log in to another user's account from your account in a virtual way. It's very simple to set up and may just help you with your virtual account crisis!

You shouldn't have to labor for hours on end to achieve great hair. And if you have to wake up early for school or work it's even more important that you don't lose your precious ZZZs just to make sure that French braid is perfectly plaited and pinned up.

In order to face paint flowers and butterflies, you will need the following: metallic white, pin, a sponge, a paintbrush, green paint, glitter, yellow paint, purple paint, and blue paint.

In order to replace a inner tie rod on a Ford Explorer, you will need to loosen the jam nut first. Remove the pin and the nut, next. Loosen the outer tie rod. Count the rotations as you remove it. Remove the bellows boot. The inner clamp is not removable. You have to damage it to remove it. You will need an inner tie rod tool. Use your inner tie rod tool and adapter. Spin it. Compare the old and new part to make sure that you have the right one. Now, reinstall the rod. Align the vent tube wit...

Expand your cheesecake horizons by making white chocolate cheesecake the next time your in the mood for a rich and decadent dessert! In this video, learn from Sue McMahon, cookery editor at Woman's Weekly magazine, how to make a delicious white chocolate cheesecake. This cheesecake takes a total time of four hours and thirty minutes to make and you will need the following ingredients:

Have a new app that you want to pin to your home screen on your Android enabled mobile device? Slapping the application on the home screen is simple on any Android phone. Best Buy has answers. The Best Buy Mobile team explains how simple it is to add apps to your home screen on an Android cell phone.

This video is showing how to create frilled layers on a cake. First you need one mini cake, rolling pin, one knife, one cocktail stick, rolling board, icing sugar, glue or water, and gumpaste to do this. First you have to roll out the gumpaste to very thin layer. Next cut it out round with the frill cutter. Next take a cocktail stick and then create wavy effect to the gumpaste. Sprinkle some icing sugar on the board to use it fast. Next cut the gumpaste. Next take the mini cake and apply some...

HP TouchSmart PC is a powerful computer with various features. You can use you PC to connect to other hardware devices like printer, scanner etc. A hardware device might not even work with you computer because the connecting cables might not match. So if you want a printer to connect to your computer you will need a USB connector. If your printer has a normal pin connector, you cannot work with it directly. In this case the other option is to print wireless, provided your printer supports it....

John Gallagher explains the process of making herbal lozenges in which need slippery elm bark powder and licorice root slices both which sooth the irritation of the throat. You need half a cup of water and two tablespoons of honey along with a small bowl and a dough roller. To cut the dough get a bottle cap and store them in a small metal container. Boil half a cup of water and put licorice according to the number of lozenge required and simmer it on a low flame for 10 minutes. Take 2 tablesp...

The person in this video is teaching us how to make toys with the help of polymer clay. As you can see the video you can say that the person there is a girl. This lady is teaching to make a teapot to her daughter. Her hand is focusing the camera. First she makes a little ball with the help of polymer clay. Then she made few lines on that ball and press that ball slightly on the top. Then she takes another piece of clay and presses it but that one is too small. Then she use another on quit big...

This do it yourself centerpiece is brought to you by A-Bnc parties and more. This starts of by making the bow, shown by painting a dowel and letting it dry. Then glue the 'frogs' at the ends of the dowel and glue fishing line to both frogs and trim to fit. Next take a polystyrene cut out of a violin and seal it. This helps paint stick to the surface of the cut out. The violin is painted brown to replicate an actual violin. Using black paint you detail the 'f' holes and allow to dry before pro...

Sieve flour with half a teaspoon of salt. Mix with three-fourth cup of water gradually and knead to make a smooth dough. Cover with a damp cloth and sit aside for fifteen minutes.

*Iris is out there to demonstrate how to use the flat iron to get the waves in your hair *She is going to show how to get the Hollywood style waves in your hair.

Kate Hemmings on The Crafts Channel shows that covering a cake isn't as tricky as you may think. You will need a type of icing that rolls out, such as fondant icing. Ideally, you will want to have fondant icing with glycerine, and so the Pettinice brand is excellent in this case. If you use this icing, you will not encounter problems with cracking of the icing when you try to shape it over the cake.

If you're record player doesn't work anymore, but it still turns, then this is the perfect solution for you. The video show you how to make a cone record player. It's also a neat trick for playing your records with out a record player, instead of a regular phonograph needle.

With protests springing up across America, there's a chance you may have your first interaction with law enforcement. Many demonstrators will have their phones in-hand to film the action, which, sadly, could prompt an officer to demand the device and any self-incriminating data it may contain. Before this happens, you should know there are tools at your disposal to protect your data in such situations.

With Avatar, Facebook's personalized stickers for use on its social and messaging platforms, those who aren't on Facebook or have otherwise dumped the social network may feel left out.

Imagine a scenario where you're nowhere near your iPhone, but it's on loud, and you really need to silence it. An alarm may be blaring, notifications could be spitting out sounds left and right, and calls may be ringing. Things can get annoying real quick for whoever's around it. Plus, all that attention makes it easy for someone to find and possibly steal your iPhone. Luckily, you can quiet it down.

When the Steam Link app was first introduced in 2018, I was impressed. As long as you were on the same network as your PC, you could play your Steam games on your phone. But now, it's even more impressive. By enabling a few extra settings, you can play your Steam library on mobile data anywhere in the world.

Open TikTok, and you might find yourself spending hours watching video after video. While each video is usually pretty short, it's highly possible to binge-watch hundreds at a time. It's even more fun to create your own. But as a parent, you may not want your children falling into this same trap, and it's easy to limit how much time they spend watching TikTok videos on their iPhone.

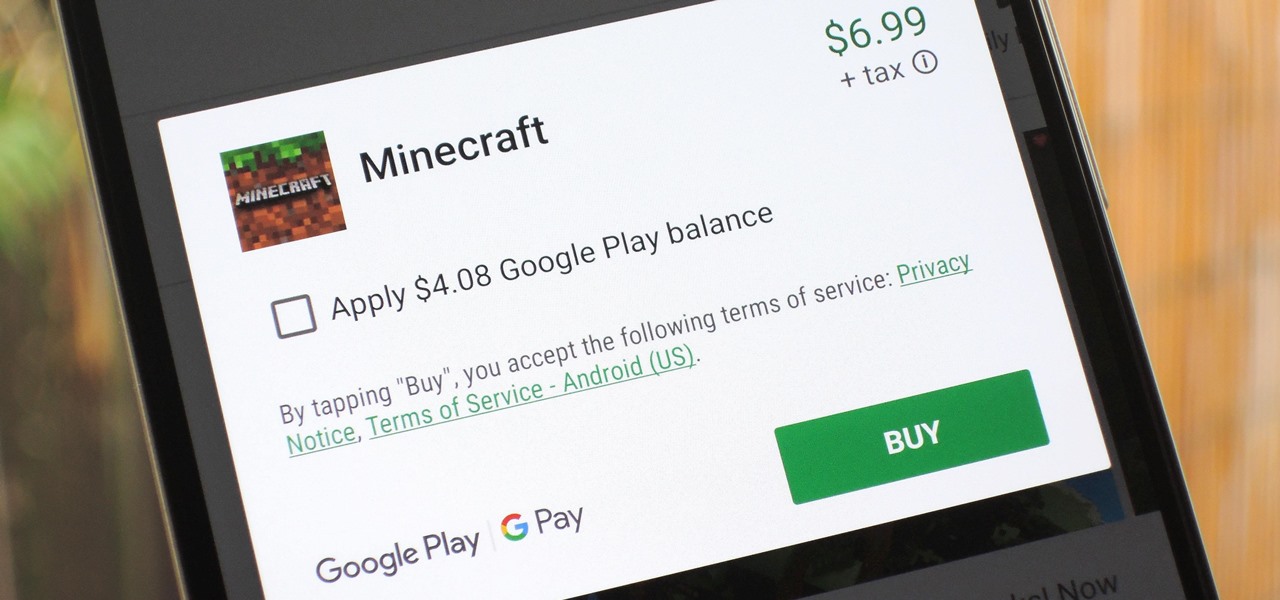
The iTunes App Store makes it easy to buy an app or game on someone else's behalf, and it's a great way to send an iPhone user a thoughtful gift. The Google Play Store doesn't have such functionality, but there are still a few workarounds to accomplish the same goal: gifting an app to an Android user.

Apple's new iPhone XR, XS, and XS Max are sure to be hits this year. Of course, that means plenty of hungry customers are looking to sign up for a model once preorders begin on Friday, Sept. 14, for the XS models, and Oct. 19 for the XR. Luckily, there are preemptive actions you can take right now to avoid waiting outside an Apple Store overnight or getting kicked out of the preorder queue online.

Excessive cell phone use was issue that Apple decided to tackle with iOS 12. Starting with the iPhone's 2018 update, a new "Screen Time" feature give you the ability to set App Limits to encourage more balanced usage, and there's another setting that gives you control over when certain apps can be accessed.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

We're nearly there — Apple released the seventh iOS 12 beta to developers Monday, August 13. While not totally unexpected, beta testers understand the struggle of predicting the next update, as Apple has switched haphazardly between two-week, one-week, and irregular release schedules for both the developer and public betas.

Apple released the third beta of iOS 12 for developers on Tuesday, July 3. The update comes exactly two weeks after the release of the second developer beta, which introduced a variety of fixes as well as new issues, and just one week after the release of the public beta. Public beta testers received this iOS 12 update on Thursday, July 5, labeled as public beta 2.

Since the San Bernardino shooting in 2014, Apple's been engaged in a game of cat and mouse with law enforcement. Authorities want access to evidence on criminals' iPhones, but Apple wants to protect all of its customers' personal data equally. The latest installment in this saga has Apple outright disabling the Lightning port.

Google Calendar is a cornerstone of the Google Suite, perhaps second only to Gmail itself. Whereas email is constantly plagued by phishing attacks, as of yet, the calendar is a relatively untapped social engineering attack vector. But it's relatively easy for an attacker to inject a meeting or event into a target's Google Calendar and use it to exploit them.

While there are a variety of privacy-focused search engines available like StartPage and DuckDuckGo, nothing can offer the complete trust offered by creating one's own search engine. For complete trust and security, Searx can be used as free metasearch engine which can be hosted locally and index results from over 70 different search engines.

There are a number of options and hidden menus within Android that provide users more control over their device. With this control, you can better manage how your phone operates. We came up with a list of tips and shortcuts that, when used, will slowly put you on a path to becoming an Android power user.

Prior to Apple's earnings report on Thursday, the storm clouds were gathering as Wall Street prepared for bad news in the wake of reports of slower iPhone sales. But it turns out that those fears were mostly unwarranted. Apple managed to increase iPhone revenue during the December quarter, despite selling slightly fewer phones.

You know Moana's a rock-solid pick for Halloween this year. The question is, how far will you go to become Moana? Are you going to just slap on a cream skirt and a red bandeau? Or do you want to go all out and end up with the finished product like YouTuber Gladzy Kei did?

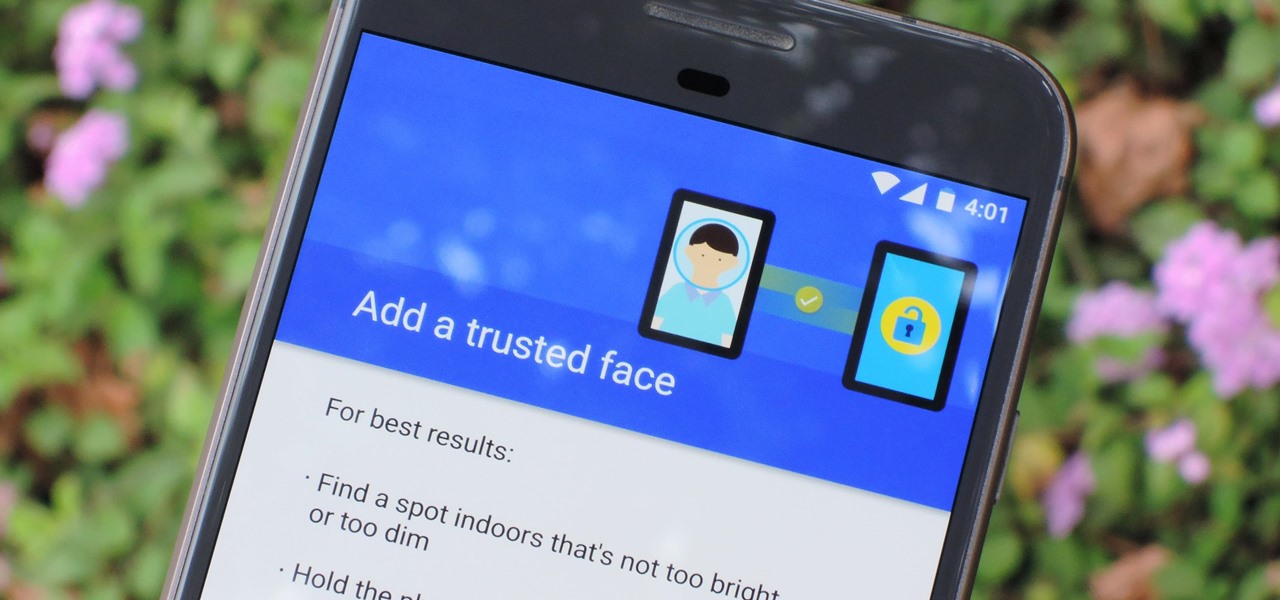
The iPhone X has a new unlocking mechanism called Face ID, which replaces the old Touch ID system since the phone no longer has a fingerprint sensor. The way it works is simple — you just look at the phone, it recognizes your face, then the system unlocks — so Apple deserves the praise they're getting for it. But did you know you can get almost this exact same feature on any Android device right now?

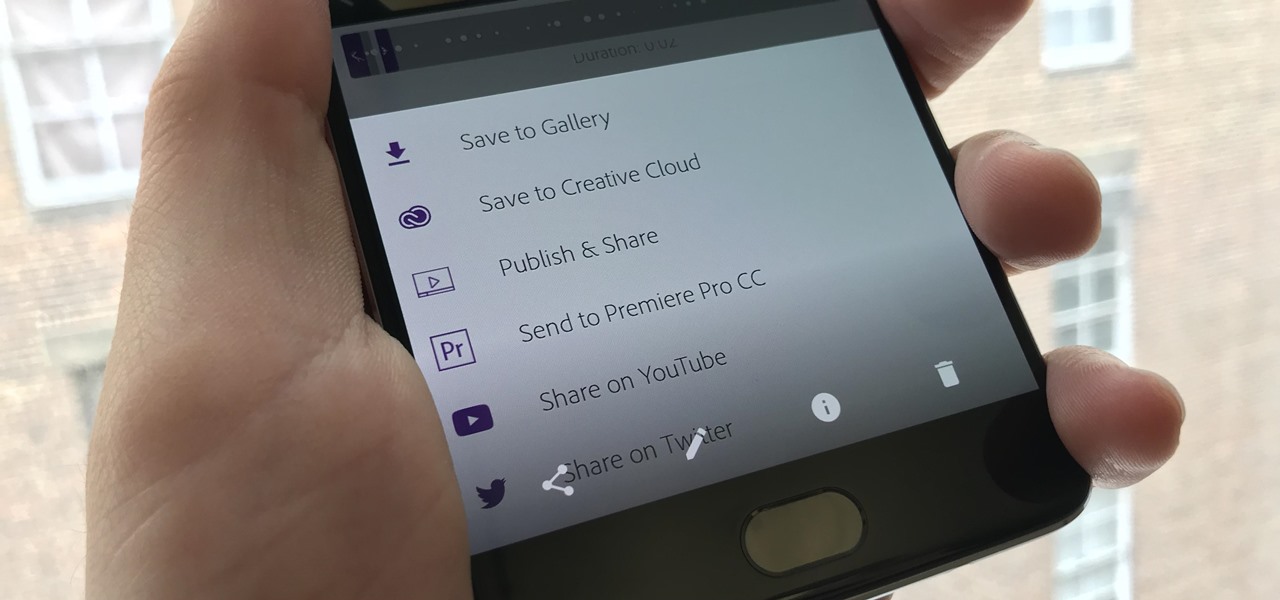
If you've taken the time to edit a video on your iPhone or Android phone, you probably have a purpose for it. Maybe you want to share it to YouTube in hopes of making the next viral sensation. Maybe you just want to save the video to your phone to show off to friends and family when you can.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.