Watch as iblogtutorials teaches you how to speed up your Windows XP and Vista shutdown times. To speed up your Windows shutdown time, do the following: Go to Start and select Run. Type in "regedit". Click the triangle next to "HKEY_LOCAL_MACHINE" and then click "SYSTEM" current control set. Click the Control folder. Wait to kill service timeout. Change the Value data to 0.2 seconds. Restart your computer and from now on your shutdown time will be much faster.

In this tutorial, we learn how to check if someone has blocked you on an IM program. To do this, go to Yahoo messenger, because it allows you to add yourself and block yourself. If someone has suddenly showed up as offline on your list and you want to check if they blocked you, visit the website, Yahoo Block Checker. Once you get to this site, type in the screen name for the person under "yahoo id" and you will be able to see if their real status is online or not. You can do this for MSN, AIM...

To watch TV on your PC you need a TV tuner. You have two choices. There are usb sticks and pci cards. The pci is an internal circuit board that goes inside your computer. The pci card is very easy to install. Literally just open the computer and pop it into an available pci slot. Then you will need to install the software that came with the usb stick or pci card. Next attach an antenna to the pci card or usb stick connector. You can scan for channels, save favorite programs, and setup recordi...

Where is the coolant level sensor and how to fix or replace it on a Mercury Sable?? The coolant sensor is located in the coolant reservoir bottle. It cannot be serviced, you can only replace the reservoir. However, if just the sensor is bad, you can also try unplugging the sensor at the coolant reservoir bottle. Unscrew the two screws holding the reservoir bottle in place. With the bottle loose, tilt the bottle slightly toward you until you see wiring coming out of the reservoir bottle, that ...
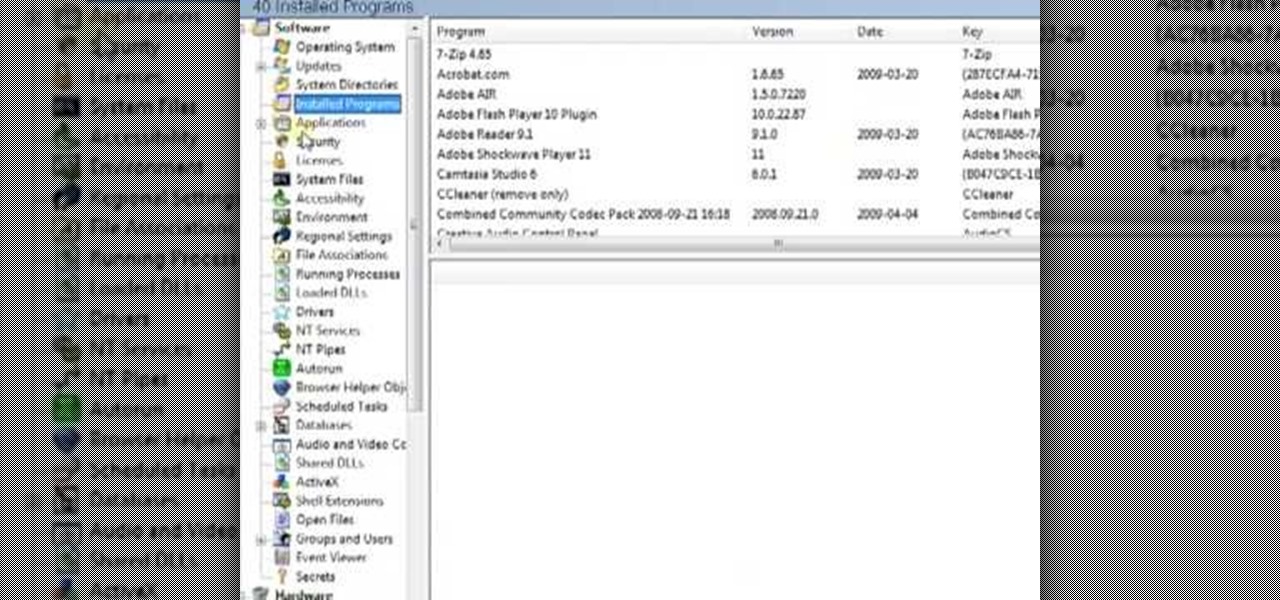
In this video the ClearTechInfo tutor shows how to learn about your computer hardware, software, and network information using a free program called 'System Information for Windows' (S.I.W.). By using this software, you will be able to answer all sorts of questions about your computer like which processor you are using, the amount of RAM, the OS version, the service pack, and all the other numerous specifications of your computer. He shows how to download the standalone version of the S.I.W. ...

Learn how to set up the Internet for T-Mobile on an iPhone clone. First you need to create a GPRS data account and a WAP profile for T mobile to bring up the service icon. Then click the data account button, then the GPRS button, then chose the correct account for you, change the APN to Link (all lower case). Before you finish this process make sure the user name and password fields are blank.

FAST is an expedited travel program for commercial truck drivers that travel between the US and Canada. FAST cards are available to citizens or permanent residents of Canada or the US. The FAST program is viewed as a privilege by both Canada and the US. You can be denied for the FAST program if you do not have a clean driving record and a clean record with the Canadian Border Services and The US Customs and Border Protection. Things such as being caught with undeclared items and having a crim...

Want to switch your Blackberry Curve's service? Here might be your chance. In this tutorial, learn how to unlock (or jailbreak) your Blackberry Curve in just a few steps, listed below (from Killer Number X):

Ever wonder what those black bars across your business letters are for? Together, those 65 black bars are called the Intelligent Mail Barcode (or, "IMB"). First announced in 2003, the IMB came into use in 2006 for United States mail and served as a way to increase the amount of information carried on letters and mail flats, expanding the tracking capabilities for mail carriers. Your IMB is divided into four parts: Ascender (A), Full (F), Tracker (T), and the Descender (D). This video teaches ...

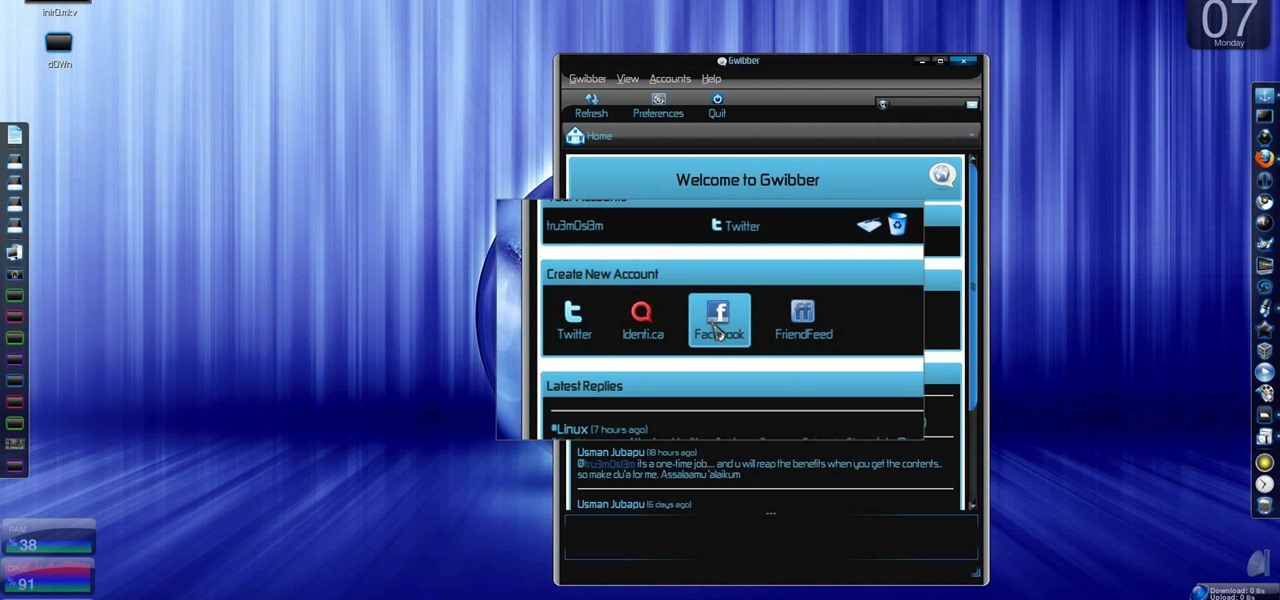
Twitter has consumed the world, so make sure you're up to date on your Tweets. One way to do that is with Gwibber 2.0 on Ubuntu Linux, the computer operating system that could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to retrieve unlimited tweets with Gwibber 2.0 on Ubuntu Linux.

Taking photos is great, but what about being able to share them with the world wide web? There are countless of image hosting options out there to get your photos on the internet, but imgur is probably one of the simplest and easy image uploading sites out there.

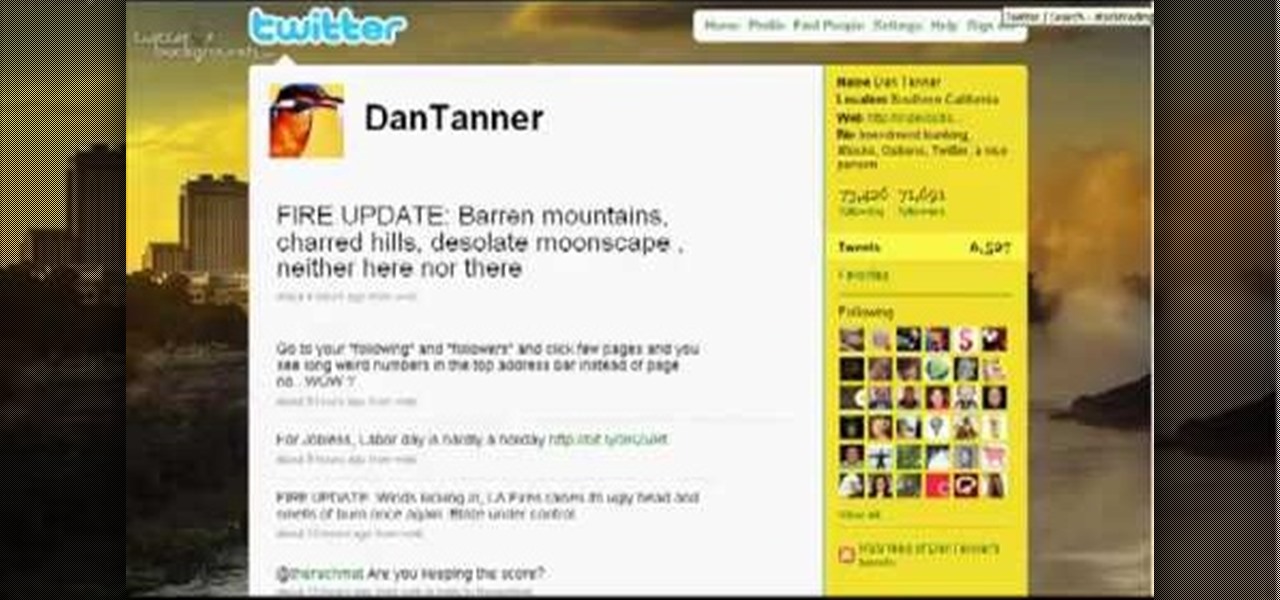
Are you a Tweeter? One of those Twitter maniacs? Or are you just starting out with free social networking service? This video tutorial will help you Tweets by showing you how to find and get more followers on Twitter.

New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install UbuntuOne on Ubuntu Linux.

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to secure remote desktop.

Help yourself win that must-have item with these tips. You Will Need: a computer with internet access, money, & patience. Create an account. Browse the categories to familiarize yourself with the site, especially if you don’t have a specific item in mind. If you know what you want, start searching by using broad terms and synonyms to yield the most results. Add quotes around your search terms or qualifiers, such as a specific color or size, to narrow the field. You can also post on the “Want ...

Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer. In this video tutorial, you'll learn how to use the new CSS, or Cascading Style Sheet, management tools in Visual Studio 2008 in the service of enhancing an existing stylesh...

Insects can be a big nuisance while you are hiking. Different parts of the country and different parts of the world have different kinds of stinging, nasty, biting insects. Preventing insect bites is easy with these tips. Get advice on backpacking, hiking, and the great outdoors in this how-to video.

Hiking is easy with these tips. Get advice on backpacking, hiking, and the great outdoors in this video tutorial. Take action: pace yourself, don't take too many long breaks, maintain good posture, keep a light spring in your step, and bring plenty of food and water. John Flaherty, the instructor of this how-to video from Live Strong, has a great love for the outdoors. In 2003, John and his wife started Central Coast Outdoors in northern California. His company provides hiking, kayaking, and ...

Packing for a hiking trip is easy with these tips. Get advice on backpacking, hiking, and the great outdoors in this video tutorial. Take Action: pack heavy items at the bottom, bring extra water, and include a first-aid kit in your pack. John Flaherty, the instructor in this how-to video, has a great love for the outdoors. In 2003, John and his wife started Central Coast Outdoors in northern California. His company provides hiking, kayaking, and biking services for those wanting to be closer...

Breaking-in hiking boots can be a pain. Get tips and advice on backpacking, hiking, and the great outdoors in this video tutorial. Take action: use more time to break in bigger boots, wear boots around the house first, and avoid long hikes. John Flaherty, the instructor in this how-to video from Live Strong, has a great love for the outdoors. In 2003, John and his wife started Central Coast Outdoors in northern California. His company provides hiking, kayaking, and biking services for those w...

Picking hiking gear is easy with these tips. Get advice on backpacking, hiking, and the great outdoors in this video tutorial. Take action: purchase a quality backpack with a good hip belt, bring some sort of shelter, bring plenty of food and water, and pack clothing for appropriate weather. John Flaherty, the instructor in this how-to video from Live Strong, has a great love for the outdoors. In 2003, John and his wife started Central Coast Outdoors in northern California. His company provid...

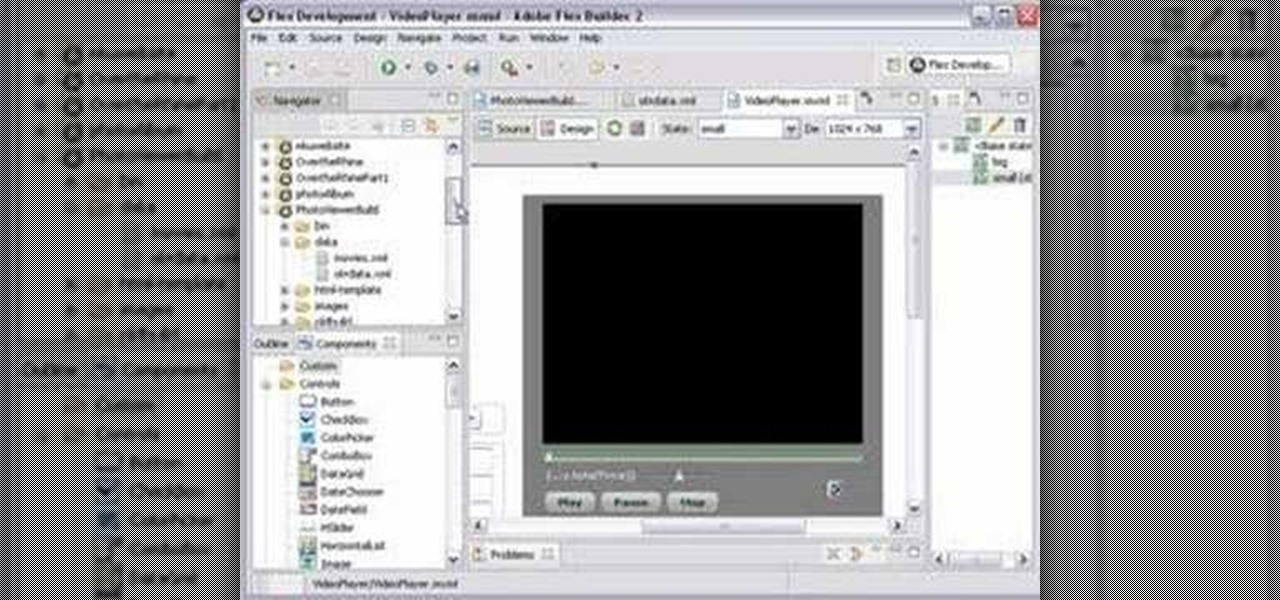
This is a simple Adobe Flex Photo Viewer. It uses a number of techniques that are not found in any one place in the literature - data shorting, tile repeater, xml http services, inline mxml actionscripting, click on double functions, use of CDATA Tags, tooltip, glow and fade effects - all done in less than 100 lines of code (once you take out the blank lines). This was created by Mike Lively Director of Instructional Design at Northern Kentucky University for the Over The Rhine project.

Stop guessing if you need to take your RV into a service center, answers are here in this tutorial video. Learn how to maintain the water heater on your RV.

Zune is a digital media players and services sold by Microsoft. It includes portable media players, client software, and the Zune Marketplace Internet music and video store. If you hate the Apple iPods, you probably have one of these MP3 players.

With a few simple steps, you can change your motor oil yourself -- no need for an expensive mechanic to do it for you.

Are you serious about becoming a bonafide hacker? Then you simply must learn how to hack SSL passwords using ARP poisoning. ARP poisoning, also known as ARP spoofing, involves attacking an ethernet wireless network by looking at the data frames on a LAN (local area network). Resultingly, you can sniff plaintext passwords, SSL passwords, and even manufacture denial-of-service attacks.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

Twelve years ago Google launched its Cloud Platform, and the world has never been the same. This suite of cloud computing services has changed how modern businesses operate. Whether you use it for data storage, management tools, computing, or machine learning, the Google Cloud Platform is essential.

It's not hard to let the new SARS-CoV-2 strain of coronavirus put pressure on our minds. Fear of catching COVID-19 is never far from the topic of conversation. But it doesn't have to be that way. If you're struggling with anxiety, stress, depression, or any negative emotions due to the virus's effect on our lives right now, you might find some solace in meditation.

A virtual private network is a necessary part of your arsenal if you're insistent on surfing the web privately and securely on your iPhone. The App Store is littered with hundreds of different VPN services that encrypt traffic and mask your IP address, but what they all have in common are connectivity issues.

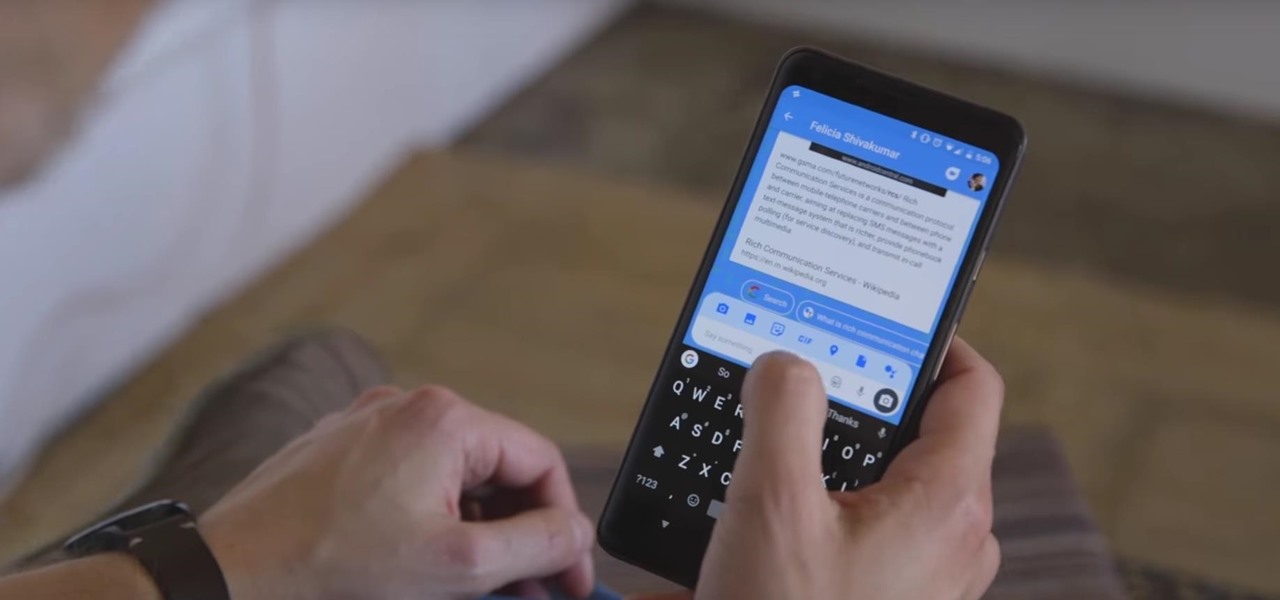
In November 2016, the RCS Universal Profile (Rich Communications Services) was introduced. The technology takes text messaging to the 21st century, emulating many of the features found in IM apps like WhatsApp and iMessage, but working through your phone number like regular SMS or MMS. The only thing is, your carrier needs to support RCS-UP to use the feature. Thankfully, the list is growing.

You may not have thought of dorks as powerful, but with the right dorks, you can hack devices just by Googling the password to log in. Because Google is fantastic at indexing everything connected to the internet, it's possible to find files that are exposed accidentally and contain critical information for anyone to see.

After reviewing the international plans for major US wireless carriers, it became obvious they're all pretty bad. Your data is heavily restricted, requiring a daily fee which can cost an extra $100+ on a seven-day vacation. That's when I learned about Google Fi, and how for most travelers, it's the best option.

There have been concerns with how much personal information Google tracks and all the things they know about us. Of course, that's what makes Google services so useful, they can use that information to cater to each of us individually. So yes, it serves a purpose, but it's not great for personal data security.

When you can't reach your iPhone or don't have it on you, how do you get help from emergency services? Unless you have one of those life-alert mobile triggers, someone nearby, or some amazing telepathy skills, hope might be the only answer — unless you wear an Apple Watch, that is.

When you don't want somebody you're calling to know the real phone number associated with your iPhone, whether it's for privacy reasons, to avoid being called back, or to prevent being ignored, there are multiple things you can do to block it on their caller ID.

Nmap is possibly the most widely used security scanner of its kind, in part because of its appearances in films such as The Matrix Reloaded and Live Free or Die Hard. Still, most of Nmap's best features are under-appreciated by hackers and pentesters, one of which will improve one's abilities to quickly identify exploits and vulnerabilities when scanning servers.

Threats to your privacy and security are everywhere, so protecting your data should be the highest priority for anyone with a smartphone. However, one threat many people overlook is the company who supplies the operating system your Android phone runs — Google.

Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The result is RCS Universal Profile, or simply Chat, and it's finally catching on.

If you somehow forgot the pattern, PIN, or password that locks your Android device, you might think you're out of luck and are destined to be locked out forever. These security methods are hard to crack by design, but in many cases, it's not entirely impossible to break into a locked device.