Hello, everyone. Stealth is a large part of any successful hack; if we don't get noticed, we're much less likely to be caught. In these next few articles, we'll be building a shell based on keeping us hidden from a firewall. There are many ways to stay hidden from a firewall, but we'll only be incorporating a couple into our shell. This article will outline and explain these evasion concepts and techniques.

Hello ladies and gentlemen, PySec here coming at you with another informative(hopefully) article for you all. In the last tutorial, we finally finished our discussion about IP Addressing and I intentionally didn't mention a really important concept with which IP Addressing wouldn't be feasible without it. What I'm talking about is how our network device gets the IP Address in order to communicate with other devices on the network/Internet. There are many different ways for that to be accompli...

Whether you're anxious to tune into this Sunday's Super Bowl 50 to see Cam Newton and the Carolina Panthers take on Peyton Manning and the Denver Broncos, or to see if you win some money on your silly prop bet, or just want to tune in for the commercials, there are a handful of ways to catch the Big Game without an antenna or cable/satellite subscription. When & Where

Unless you're in law enforcement, you won't usually have a flashlight on hand for those rare moments when you need to sift through the dark. However, it is very likely that you will have your phone on you, so you'll have fast access to a bright light with just a few easy taps.

Since Android is an open source operating system, that means anyone with a little know-how can download, view, and even alter its underlying code base. Manufacturers do it all the time, which is how we end up with skins like TouchWiz and Sense. But when Android's awesome third-party development community gets their hands on this code, we end up with custom ROMs like LineageOS and MIUI.

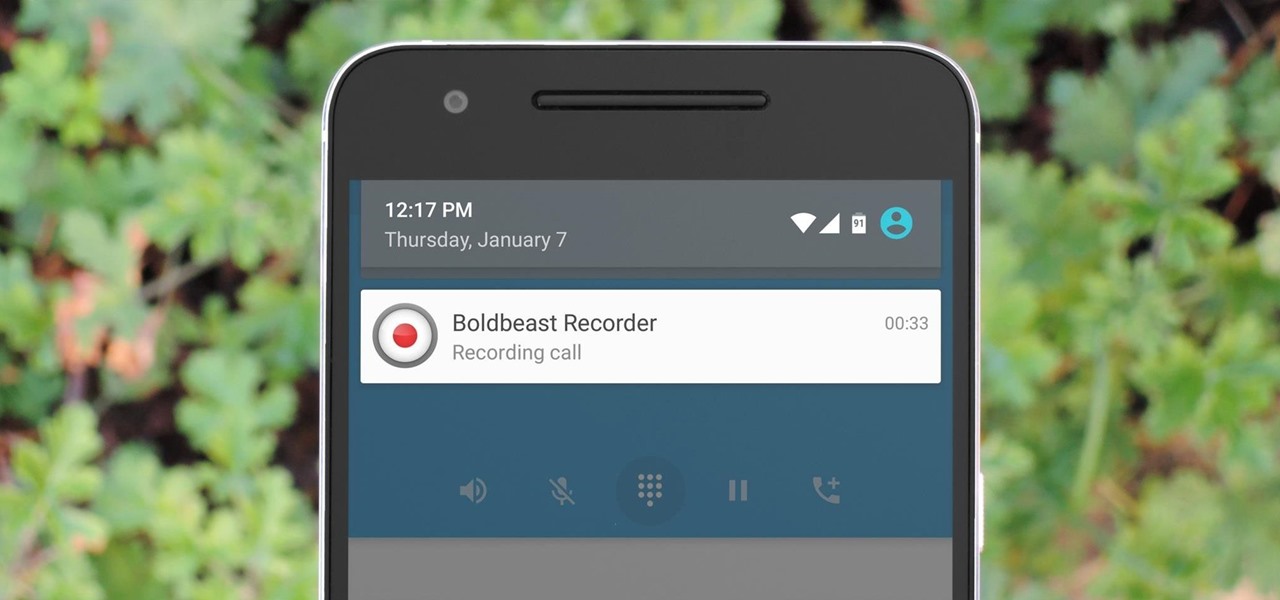
There are plenty of legitimate reasons that you might want to record a phone conversation. Let's say you operate a business and take orders over the phone, and you don't want to miss an item. Or perhaps you need to jot down some notes from a recent conference call, and things were just happening too quickly in real time.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

Hello World ! Well, welcome in my post. This will be in series, and this is first part. Throughout the series, I will share my research and findings with you. And that will be on topic, Encryption Is Not Enough. We will see, how Encryption is broken & what countermeasures should be implemented to secure it. Let's begin, Why do we encrypt ?

Before you sell or give away an old iPhone, Find My iPhone, which works in conjunction with Activation Lock (Apple's anti-theft system) needs to be deactivated from your iCloud account. This also applies if you've lost your passcode and are locked out of the device, if you're restoring to a previous iTunes backup, or just want to remove it from your list of iCloud devices.

Smartphones have been a hot button issue around school campuses for several years now—some schools allow them, others confiscate them on sight. But the fact of the matter is, when used correctly, a smartphone can be just as much of a learning tool as a textbook or school-issued laptop.

Hello fellow Null-Byters! This is my first post so please be respectful and constructed criticism is much appreciated. I am no professional, however I believe that it is important to understand technologies before you go poking at them and trying to break them, I therefore decided to make this series. In this "tutorial" we are going to setup a web server with php and mysql. I will be doing this with a raspberry pi because a pi is quite versatile.

Today's smartphones and tablets offer a great way for children to learn through interactive sight, sound, and touch, but they can also provide hours of genuine fun. If you have a spare tablet laying around—or at least a nice, durable case—the only thing you need to get your child started in this world of fun and learning is a handful of good apps.

Of course, if it were a perfect form of currency, it would have become the standard by now. But it hasn't. Wanna know why? The story begins with the advent of agriculture, when humans had settled down under groups as units called villages, over 10,000 years ago.

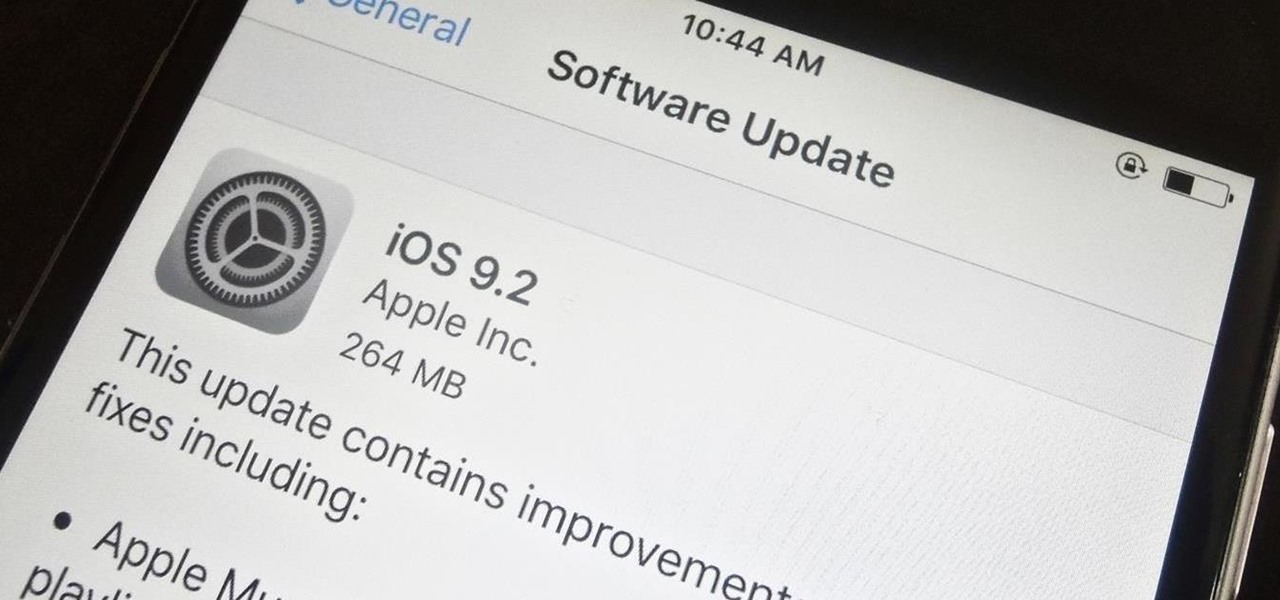
We're near the end of a productive year for Apple, one that introduced a new Apple TV, the iPad Mini 4 (in conjunction with the Apple Pen), the iPad Pro, and the iPhone 6S and 6S Plus, as well as iOS 9. Now, the second major update to iOS 9—version 9.2—has just been released to the public.

When you have some form of lock screen security enabled, Android makes sure that you don't have to fumble around to enter your pattern, PIN, or password before you can call 911 in an emergency. It does this by adding an "Emergency Call" button to the bottom of the screen—but as handy as this may sound, most of the time it's more trouble than it's worth.

Social engineering is a pretty important item in a hacker's toolkit. In Mr robot there was a time, we saw Elliot using social engineering to gain access to his therapist's boyfriend's email and bank accounts by calling him and pretending to be someone from his bank, then Elliot asked him for some info that were really useful to gain access to his account, the target believed to be someone from the bank and gave him the info Elliot was looking for. But How Is It in the Real World?

Hi I am a new member of null byte(although I am reading this website from the beginning) and this is going to be my first post.

Screenshots are an indispensable tool when it comes to relaying information about what's currently showing on your monitor. Whether you need help troubleshooting an issue or you just want to save and share a protected image, screenshots are often your best bet.

Microsoft's Windows 10 has proven to be a solid release by Microsoft, with faster adoption rates than its predecessor builds. The seamless integration of cloud services and tweaks both major and minor make using Windows easier than ever now. And it's almost enough to forget you ever used Windows Vista... almost.

Of all the new features in Android 6.0 Marshmallow, an automatic battery-saving function called "Doze" might just be the most interesting. What it all boils down to is that if you set your phone down on a flat surface, the device uses internal sensors to detect that it's motionless and not in use, then responds by drastically scaling back battery-sucking services until the next time you pick your phone up.

Greetings dear null byters, today we start a new series, we will start to attack users using social networking that are popular such as Facebook, Skype, and much more, and in part 1 of the series will engage users of Skype.

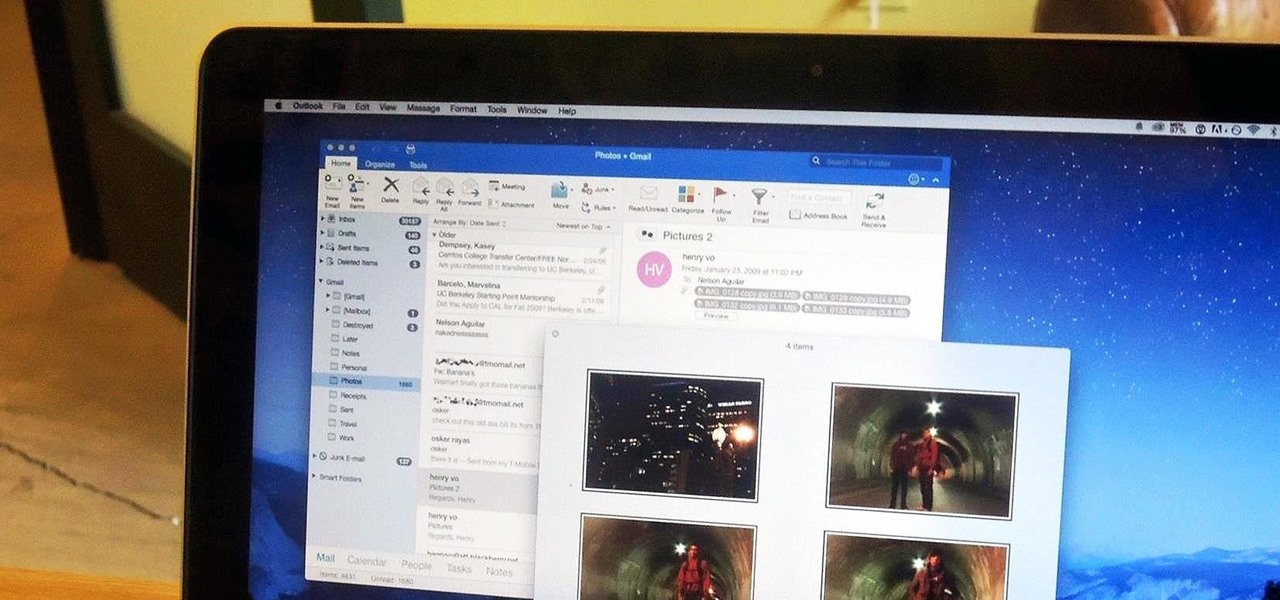
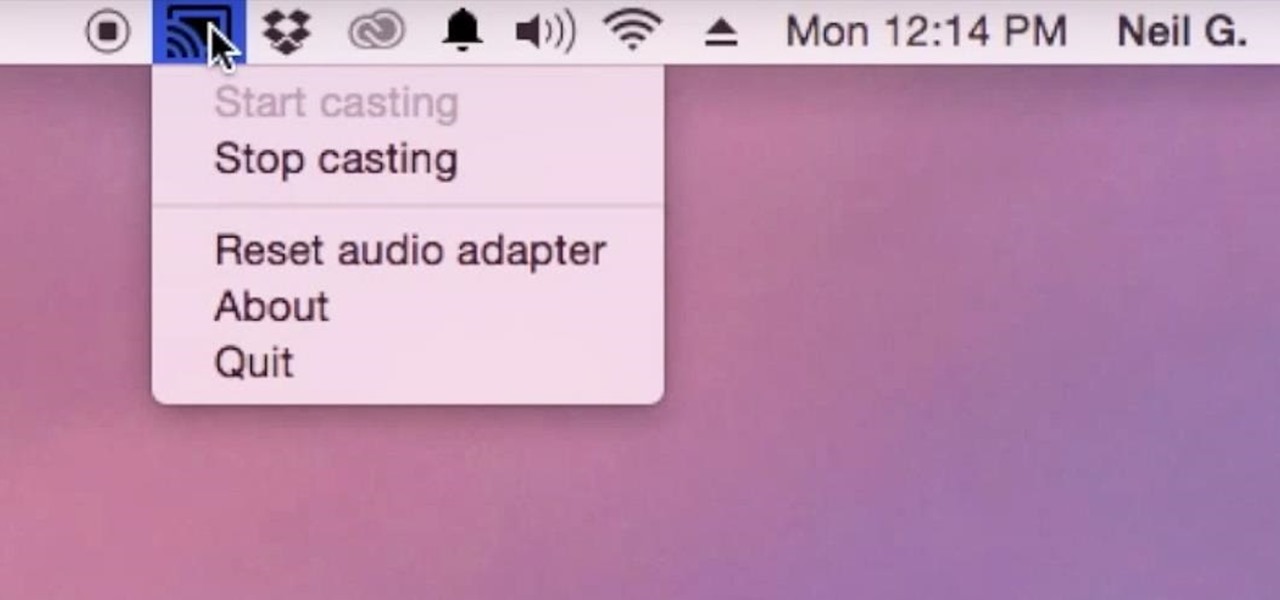
Google just announced a new and improved Chromecast at an event in San Francisco this morning, and debuted a new "Chromecast Audio" for streaming music directly to any speaker. I'm sure you rushed off to the Google Store to buy one of these promising and powerful devices, but while you wait on the new one to come in the mail, your old Chromecast just got a lot more functional by way of a simple app update.

Slowly but surely, Microsoft seems to be steering Windows in the direction of Google's Android. First, they released Windows 10 as a free upgrade, mainly because they wanted to cash in on the revenue that they hoped would come when more users had access to the Windows Store. Then, they included tons of tracking "features" to help populate Bing with targeted ads, which has always been Google's primary method for monetizing Android.

Welcome learners, lets us proceed further with the information we already have. In this post we will explore more about finding hacked accounts online. We will look into how to find juicy info in pastes which are deleted on Pastebin.

After my hard drive crashed recently, I lost everything. Old college essays, half-written stories, short films, and most importantly, all of the photos that I had saved from the past five years... all gone.

Initially reluctant to port Firefox over to iOS, Mozilla has finally released the first public preview of their famed web browser. While this is great news for all Firefox users, the bad news is that the browser is currently available for download only in New Zealand.

Welcome back, my novice hackers! This new series on Bluetooth hacking was inspired by a recent episode of Mr. Robot (my favorite TV show). In episode 6, Eliot hacked the bluetooth keyboard of the police office in order to hack the prison and release his nemesis, Vera. This is just one of the many hacks we will explore in the series.

Everyone's favorite Android modding tool is finally available for the Galaxy S6 and S6 Edge. Thanks to some hard work by Wanam and a few other developers, we can now install the Xposed Framework on Samsung's latest mid-sized flagship phones.

Although I know it will never happen due to Apple and Google's tempestuous relationship, I sometimes wish I could cast iTunes or Apple Music from my Mac to Google's Chromecast. When you don't have speakers to blast your music, the television is a great alternative to amplify your music.

Welcome back, my novice hackers! Episode 6 of Mr. Robot has come and gone and, as usual, it did not disappoint. Once again, our hero, Elliot, has used his extraordinary intellect and hacking skills to awe and inspire us.

There are many apps and features on your iPhone that you may never use, and therefore don't need. A great illustration of this is the Apple Watch app. You might have no interest in ever getting an expensive smartwatch, yet you're stuck with the Apple Watch app on your home screen.

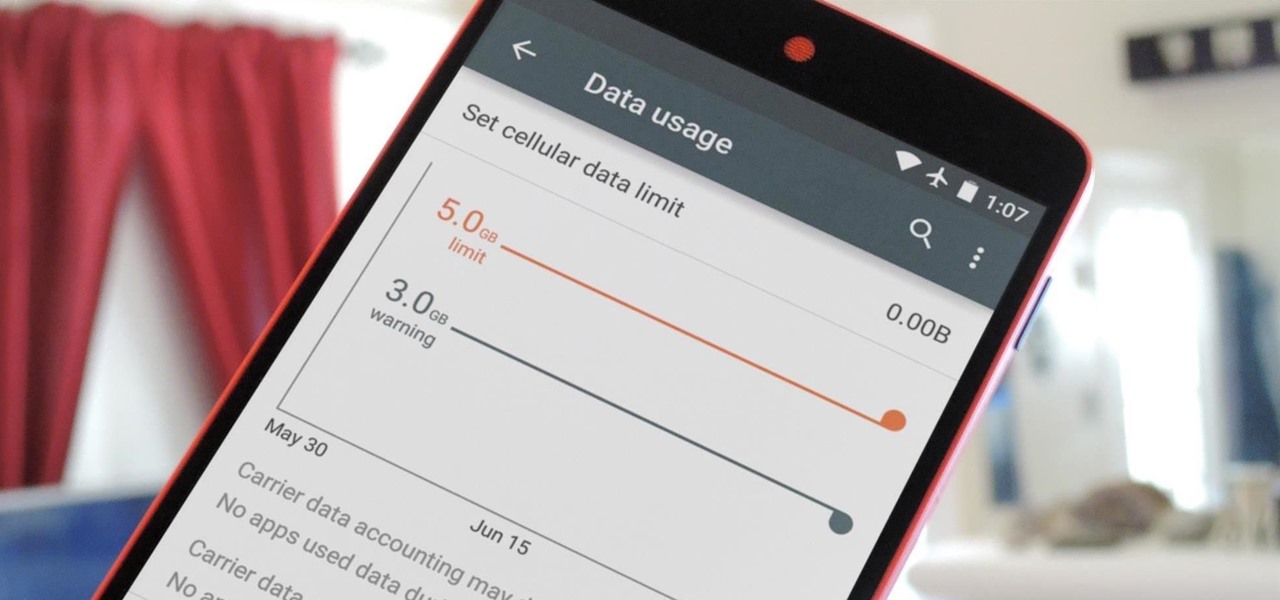
Ever watched Netflix on your phone only to realize an hour later that you forgot to turn Wi-Fi on? That's a whole lot of data used.
Hello, Hackers/Viewers! My name is nullf0x, and I have 4 years of experience as a hacker. You might see everyday that one of your friends or acquaintances get a new virus in their computer. You might think, How cool would it be if I made a virus? or How cool would I be if i could remove viruses from others computers for money or free?

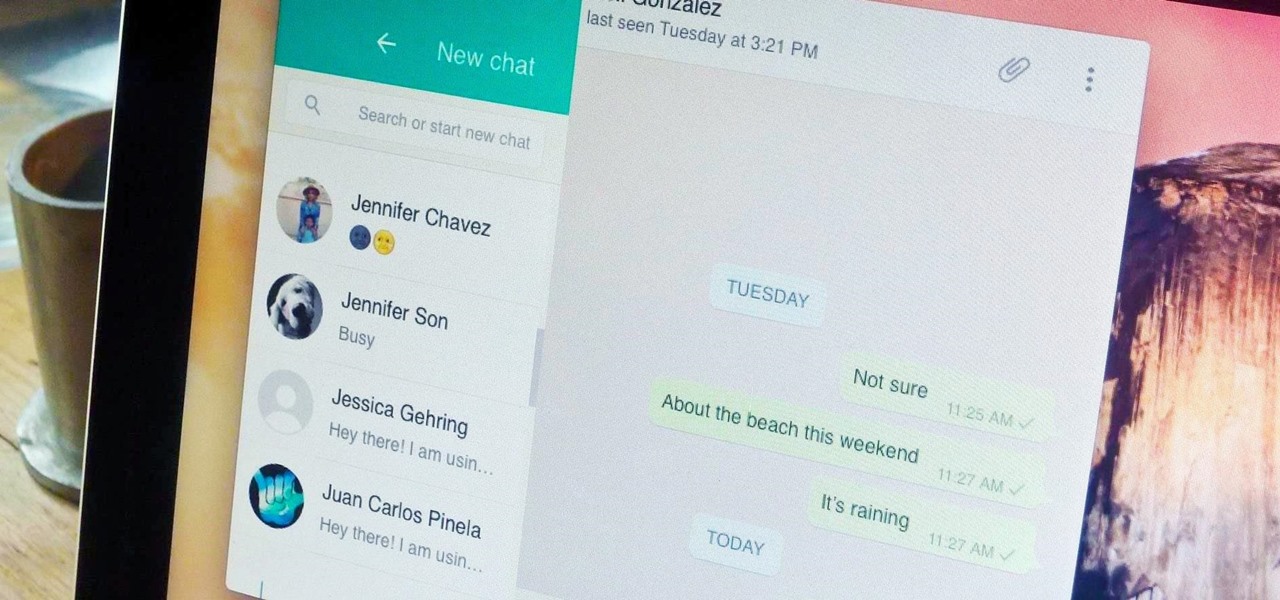
Boasting over 800 million users a month, WhatsApp has quickly become one of the most popular messaging services available today. Thanks to its low price, ease of use, lack of ads, cross-platform functionality, and great features, its popularity is well-deserved.

I'm an Android fan through and through, but occasionally, I see a feature or two on iOS that makes me a bit jealous. This was the case when I first discovered the useful functionality that lets you scroll to the top of a page by simply tapping the status bar on an iPhone.

Hi nullbytes! I've been recently reading the whole Linux Basics for the Aspiring Hacker series and felt like it was missing some stuff I know, so I felt like sharing it with anyone who might find it useful too.

Your Apple Watch is a fantastic tool that can help you perform daily tasks on your iPhone. Notifications get filtered through it, you can respond to messages on it, and you can even use Apple Pay to purchase goods and services. Your Apple Watch is also a valuable asset when it comes to finding your lost iPhone, too.

The Apple Watch is finally here! We'll have loads of guides and videos for you guys to check out in the following week and beyond, but we thought it'd be best to start off showing you how to set up and pair that brand new beautiful Apple Watch of yours to your iPhone.

Google Play Music is an awesome app—even if you don't subscribe to their $9.99/month All Access service, you can still use it to store and stream up to 50,000 of your own songs for free. Add to that the fact that it's a pre-installed app on most Android devices, and there aren't many reasons not to be using Play Music.