It's a controversial headline, I know, but bear with me and I'll explain in due course. Disclaimer: I was once a child, and I played lots of video games. I didn't look anything like this child.

Our attention spans have vastly shortened thanks to the Internet and our subsequent procurement of information from it at a rapid pace. It's tough to pay attention to something for a good amount of time, unless it's ridiculously interesting and stimulating. It's gotten so bad for me that I keep checking my phone every ten minutes—I even did it during a midnight showing of The Dark Knight Rises.
Yes, boys. It’s true. It’s here. IT’S FOR REAL!! I am here to provide a list of things that boys should do (meaning they don’t do these things very often, probably why us girls think it’s adorable when they do) when they are pursuing one of us lovely ladies. There is a lot more to making her fall for you than you think, and yes, it’s the little things. The opened doors, the little touches, the tiny encouragements. Those are the things that matter. So here we go...

Offensive pictures, depressing tweets, political statuses, and just plain old dumb comments are only a few of the reasons why people unfriend or unfollow others on social media sites. Sometimes it's just social spring cleaning, other times there's no reason at all.

People take their Black Friday shopping seriously. Some of them are even willing to fight over it. Every year the stories get crazier and crazier, and someone always gets hurt (or even killed).

Notes: My guides are setup like old Lego instruction booklets; picture intense/text lacking. Just remember you're building from the ground up, each step is a layer to go onto the previous layer.

Thermal cooking saves energy costs and preparation time, so why not try out this delicious recipe using a thermal cooker? You'll learn how to make a fruit cake inside a thermal portable cooker, which could get you addicted. Give it a try, see if you're a thermal cooker.

The best way to keep rats out is by making it difficult and unappealing for them to come inside. Keep your house clean and free of anything that a rat might want to eat. Rats can fit through very small opening so go on the defensive and keep rats where they belong.

There's a world of hidden features on your iPhone just waiting to be explored, and one of them is hiding in plain sight right in front of you. You likely see it multiple times a day after performing a routine action without ever thinking twice about what else it can do, and you're not the only one.

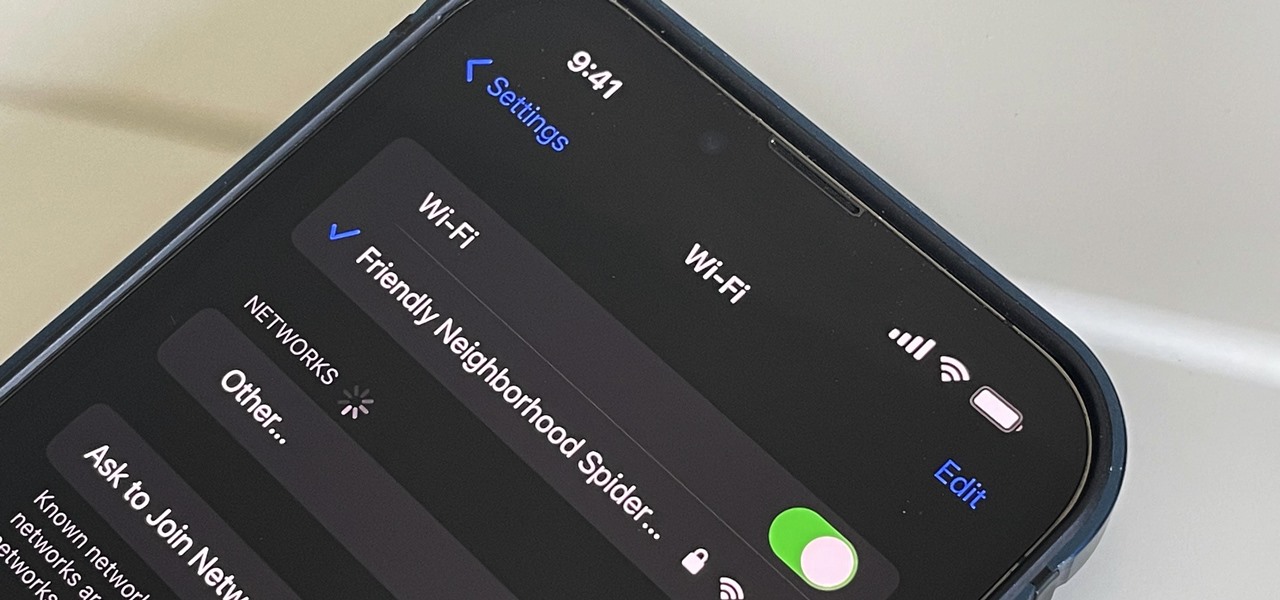
For years, Android has provided easy ways to view all the Wi-Fi networks you connected to in the past, and you can even see the saved passwords in plain text. With iOS 16, Apple finally gave us a similar way to view saved Wi-Fi hotspots, copy their passwords, and remove old ones without being near their access points.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

Router gateways are responsible for protecting every aspect of a network's configuration. With unfettered access to these privileged configurations, an attacker on a compromised Wi-Fi network can perform a wide variety of advanced attacks.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

The gym can be pretty distracting. With the slamming of weights and pieces of equipment, loud music blasting through the speakers, and plain old grunting, it can be challenging to focus on your workout. However, with your just your phone, you can not only eliminate these distractions but make the most of your time there.

As Android bug bounty hunters and penetration testers, we need a properly configured environment to work in when testing exploits and looking for vulnerabilities. This could mean a virtual Android operating system or a dedicated network for capturing requests and performing man-in-the-middle attacks.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

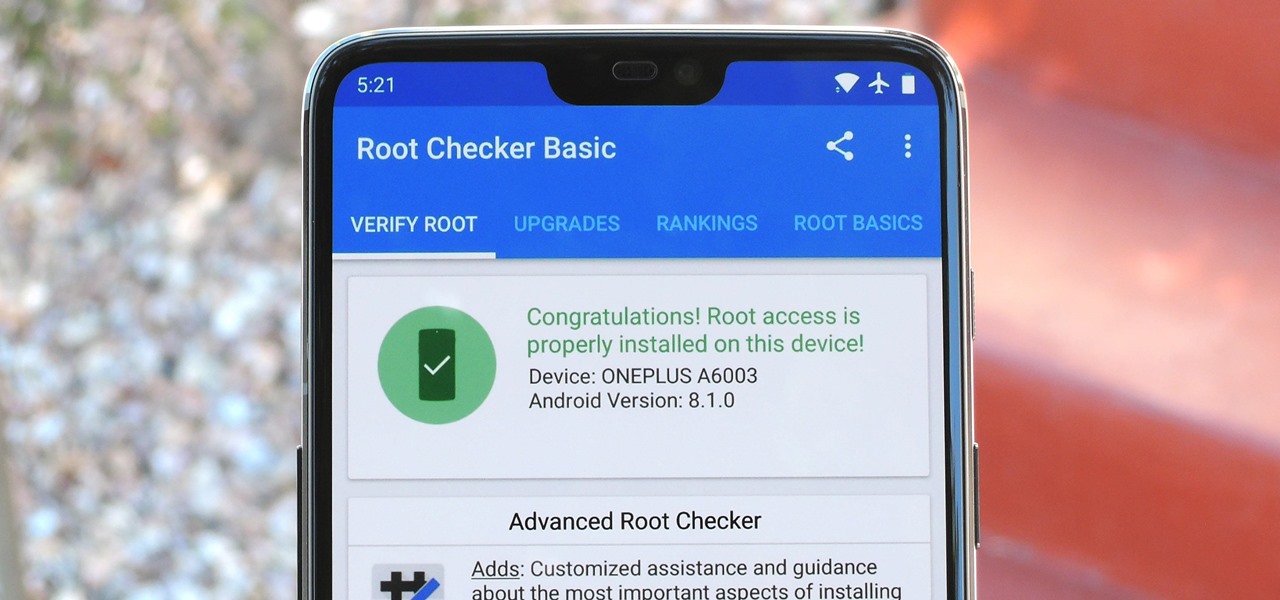
Year in and year out, OnePlus flagships top our list of the best phones for rooting. Why? Primarily because rooting does not void your warranty, and OnePlus goes out of their way to make the whole process as easy as possible.

The easiest way around a security policy is to find users who don't follow it. The Have I Been Pwned database identifies accounts with information breached by major third parties like Yahoo and LinkedIn. With Maltego, hackers can locate breached accounts created using company email addresses, potentially giving attackers access to a company account if the employee reuses a compromised password.

According to Google at their 2018 I/O conference, Google Assistant is now available on over 500 million devices. Now that the assistant is available on iPhones as well, Google has to give iOS users a reason to switch to its assistant over the built-in Siri. Today, Google has eight more reasons for users to do so.

Unlike on Android, you can't easily hide your iPhone apps. Sure, you can nestle them away in folders labeled "junk," but they're supposed to be omni-present somewhere on your home screen. That is, until one day they're just ... gone. The fact that some of your apps disappeared only makes it more frustrating because there's no logical reason why they should have, right?

Identifying vulnerable devices and services on a target router can be difficult without leaving logs and other traces of an active attacker on the network. However, there is a way to covertly decrypt and view Wi-Fi activity without ever connecting to the wireless network.

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

While there aren't as many ways to customize your iPhone like there is on Android, there are still a lot of apps out there that can help streamline and enhance your experience beyond Apple's own default options — and we've hand-picked over 100 essentials.

Blowing dust and fungal spores are creating a public health problem that could be just a slice of what's to come with climate change.

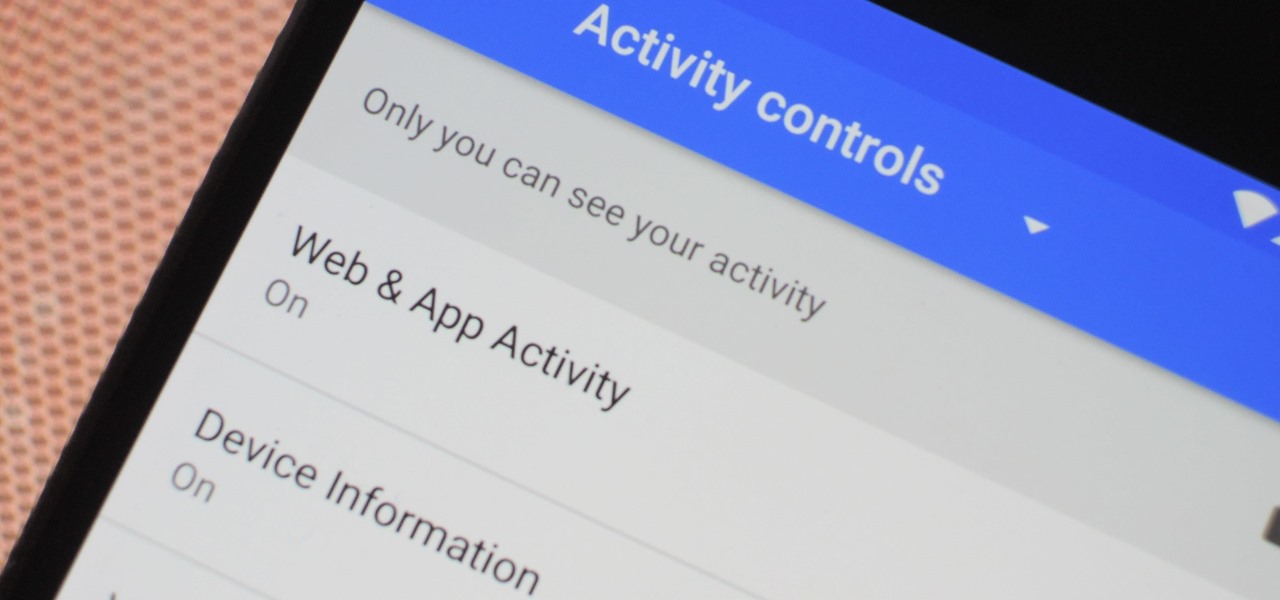
The Google Assistant is an incredibly useful tool that's now available for both Android and iOS. You can use plain English to send voice commands that range from turning off your smart lights to answering almost any question — but many of these features won't work properly if you have certain Google activity controls disabled.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

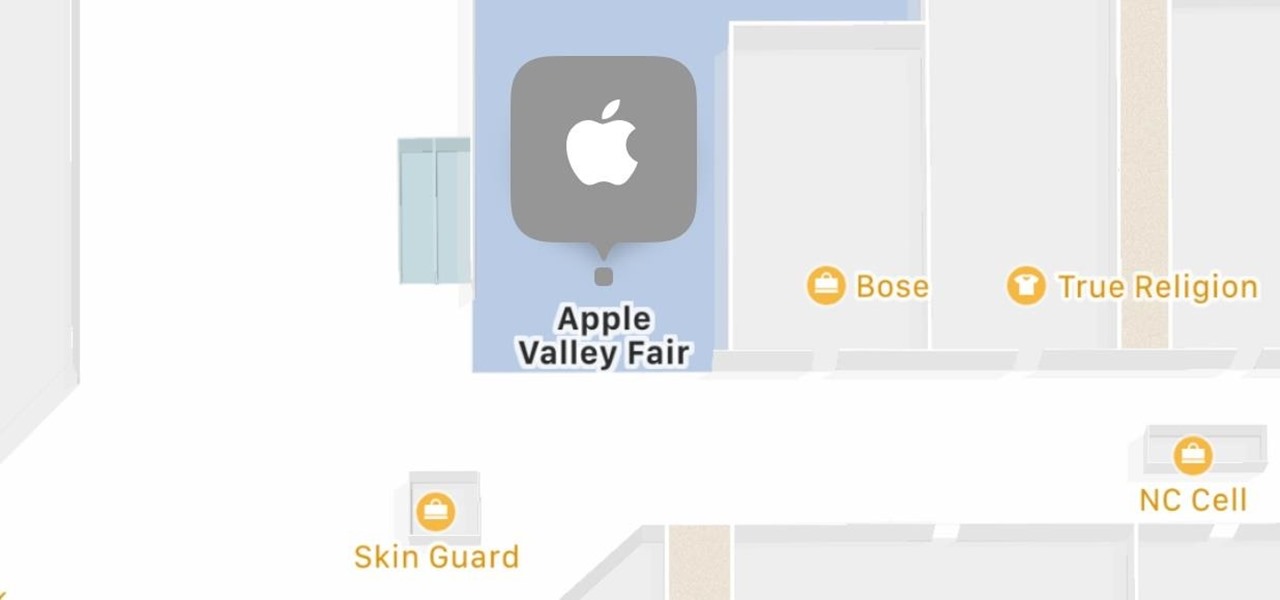
Apple has some great features aimed at making the lives of globetrotters and mall aficionados significantly easier, such as having detailed floor plans for airports and shopping centers in its native Maps app. With this feature available in Apple Maps, you no longer need to rely on publicly posted maps and directions that are often hard to understand.

Hear me out. No, really. Before you sharpen your pitchforks and give me anecdotal evidence of your Chinese restaurant syndrome, I think you need to know a few things about monosodium glutamate. First of all, it's a naturally-occurring chemical compound that can be found in anything from tomatoes to cheese, and is used in all kinds of foods from KFC to breakfast sandwiches. So spare me the comments on MSG and Chinese food—you probably eat MSG on a daily basis without even knowing it. (And also...

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.

I truly don't understand why anyone would pay $10.99 for a case of carbonated water just to feel like a Midwest mom on a diet. Every time I talk about LaCroix, pronounced La-CROY (rhymes with enjoy), it's like I take all the money I spent on my French major and light it on fire.

Thanks to the Edge variants, Samsung's Galaxy S phones are just a few millimeters off in body size when compared to the Note series, and just 0.2 inches smaller when it comes to displays. Now that the two flagship models are almost identical in size—with matching curved displays—there's really only one thing that separates the Note7 from the Galaxy S7 Edge: The S Pen.

The yogis of the internet have started a wonderful food trend that has everyone wanting to eat healthy—gorgeous buddha bowls. Okay, so maybe not everyone, but a lot of people are definitely entranced by these beautiful, multicolored meals.

My husband's and my daily schedules are constantly changing. Frankly, it's complete chaos sometimes, so I can't plan to have elaborate dinners on the table at six o'clock every day. And by the time we actually get to eating in the evening, we've become so hungry that our moods have taken a nosedive.

A carefully constructed frittata is one of the culinary world's perfect wonders. It's inexpensive to create, can be made with all sorts of leftovers, and is outstanding to eat for breakfast, lunch, or dinner. However, frittatas can go downhill fast and come out spongy, tasteless, dry, and over-done.

When we were kids, snacks on-the-go or in our lunch box were often Kellogg's Nutri-Grain cereal bars. There were flavors like strawberry, blueberry, and our beloved apple-cinnamon.

Pokémon GO made waves as the first augmented reality game to gain popular adoption. In fact, it was so popular that it only took a few days to uncover some the benefits and serious issues with combining physical and digital worlds.

If you spend a lot of time reading about food, chances are you've heard about bone broth. It's all the rage these days, from high profile chefs like Marco Canora building menus around it, to celebrities like Salma Hayek using it as self-prescribed beauty regimens.

When alcohol tastes bad, there's little you can do to save it—or so you think. While it might seem easier to toss your entire bottle of old, opened wine, or to give up and drink crappy vodka anyway, there are creative ways to turn a spoiled or just plain bad boozy beverage into one you actually want to drink.